Frame Relay Networks
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Strategic Use of the Internet and E-Commerce: Cisco Systems
Journal of Strategic Information Systems 11 (2002) 5±29 www.elsevier.com/locate/jsis Strategic use of the Internet and e-commerce: Cisco Systems Kenneth L. Kraemer*, Jason Dedrick Graduate School of Management and Center for Research on Information Technology and Organizations, University of California, Irvine, 3200 Berkeley Place, Irvine, CA 92697-4650, USA Accepted 3October 2001 Abstract Information systems are strategic to the extent that they support a ®rm's business strategy. Cisco Systems has used the Internet and its own information systems to support its strategy in several ways: (1) to create a business ecology around its technology standards; (2) to coordinate a virtual organiza- tion that allows it to concentrate on product innovation while outsourcing other functions; (3) to showcase its own use of the Internet as a marketing tool. Cisco's strategy and execution enabled it to dominate key networking standards and sustain high growth rates throughout the 1990s. In late 2000, however, Cisco's market collapsed and the company was left with billions of dollars in unsold inventory, calling into question the ability of its information systems to help it anticipate and respond effectively to a decline in demand. q 2002 Elsevier Science B.V. All rights reserved. Keywords: Internet; e-commerce; Cisco Systems; Virtual Organization; Business Ecology 1. Introduction Information systems are strategic to the extent that they are used to support or enable different elements of a ®rm's business strategy (Porter and Millar, 1985). Cisco Systems, the world's largest networking equipment company, has used the Internet, electronic commerce (e-commerce), and information systems as part of its broad strategy of estab- lishing a dominant technology standard in the Internet era. -

Medium Access Control Layer
Telematics Chapter 5: Medium Access Control Sublayer User Server watching with video Beispielbildvideo clip clips Application Layer Application Layer Presentation Layer Presentation Layer Session Layer Session Layer Transport Layer Transport Layer Network Layer Network Layer Network Layer Univ.-Prof. Dr.-Ing. Jochen H. Schiller Data Link Layer Data Link Layer Data Link Layer Computer Systems and Telematics (CST) Physical Layer Physical Layer Physical Layer Institute of Computer Science Freie Universität Berlin http://cst.mi.fu-berlin.de Contents ● Design Issues ● Metropolitan Area Networks ● Network Topologies (MAN) ● The Channel Allocation Problem ● Wide Area Networks (WAN) ● Multiple Access Protocols ● Frame Relay (historical) ● Ethernet ● ATM ● IEEE 802.2 – Logical Link Control ● SDH ● Token Bus (historical) ● Network Infrastructure ● Token Ring (historical) ● Virtual LANs ● Fiber Distributed Data Interface ● Structured Cabling Univ.-Prof. Dr.-Ing. Jochen H. Schiller ▪ cst.mi.fu-berlin.de ▪ Telematics ▪ Chapter 5: Medium Access Control Sublayer 5.2 Design Issues Univ.-Prof. Dr.-Ing. Jochen H. Schiller ▪ cst.mi.fu-berlin.de ▪ Telematics ▪ Chapter 5: Medium Access Control Sublayer 5.3 Design Issues ● Two kinds of connections in networks ● Point-to-point connections OSI Reference Model ● Broadcast (Multi-access channel, Application Layer Random access channel) Presentation Layer ● In a network with broadcast Session Layer connections ● Who gets the channel? Transport Layer Network Layer ● Protocols used to determine who gets next access to the channel Data Link Layer ● Medium Access Control (MAC) sublayer Physical Layer Univ.-Prof. Dr.-Ing. Jochen H. Schiller ▪ cst.mi.fu-berlin.de ▪ Telematics ▪ Chapter 5: Medium Access Control Sublayer 5.4 Network Types for the Local Range ● LLC layer: uniform interface and same frame format to upper layers ● MAC layer: defines medium access .. -

The Great Telecom Meltdown for a Listing of Recent Titles in the Artech House Telecommunications Library, Turn to the Back of This Book
The Great Telecom Meltdown For a listing of recent titles in the Artech House Telecommunications Library, turn to the back of this book. The Great Telecom Meltdown Fred R. Goldstein a r techhouse. com Library of Congress Cataloging-in-Publication Data A catalog record for this book is available from the U.S. Library of Congress. British Library Cataloguing in Publication Data Goldstein, Fred R. The great telecom meltdown.—(Artech House telecommunications Library) 1. Telecommunication—History 2. Telecommunciation—Technological innovations— History 3. Telecommunication—Finance—History I. Title 384’.09 ISBN 1-58053-939-4 Cover design by Leslie Genser © 2005 ARTECH HOUSE, INC. 685 Canton Street Norwood, MA 02062 All rights reserved. Printed and bound in the United States of America. No part of this book may be reproduced or utilized in any form or by any means, electronic or mechanical, including photocopying, recording, or by any information storage and retrieval system, without permission in writing from the publisher. All terms mentioned in this book that are known to be trademarks or service marks have been appropriately capitalized. Artech House cannot attest to the accuracy of this information. Use of a term in this book should not be regarded as affecting the validity of any trademark or service mark. International Standard Book Number: 1-58053-939-4 10987654321 Contents ix Hybrid Fiber-Coax (HFC) Gave Cable Providers an Advantage on “Triple Play” 122 RBOCs Took the Threat Seriously 123 Hybrid Fiber-Coax Is Developed 123 Cable Modems -

PDF Version of DM3530-005
CHAPTER 6 – PART 5 Encryption Security Standards 1 BACKGROUND All USDA agencies and staff offices need to transmit Sensitive But Unclassified (SBU) over open networks. In using IT to continuously improve mission performance, the USDA is becoming more interconnected to open networks and other emergent global networks. The openness of these networks enables malicious cyber attacks against sensitive USDA assets and increases the potential risk to sensitive information. This risk is compounded through the use of the Internet and other non-secure mediums such as Wireless Local Area Network technology, Microwave, and Radio technologies. This technology includes utilizing Laptops and Personal Electronic Devices (such as cellular telephones, pagers and hand held computers) to communicate and process USDA information from any location. Encryption methods can protect sensitive information during storage and transmission. They provide important functionality to reduce the risk of intentional and accidental compromise and alteration of data. Encryption algorithms use a mechanism called a key, which is used to render the information unreadable during transmission. While the information is encrypted it is mathematically protected against disclosure because it is cannot be read by some one who does not have a corresponding key to decrypt the information. Encryption methods serve as part of the USDA defense-in-depth strategy and provide reasonable protection of sensitive information at a comparatively low cost. The primary factor that must be considered when determining if encryption is required is data sensitivity. Data sensitivity is a measure of the importance and nature of the information processed, stored, and transmitted by an IT system to the organization’s mission and day-to-day operations. -
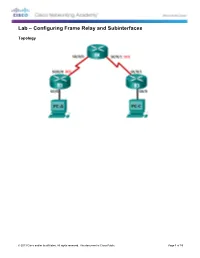
Lab – Configuring Frame Relay and Subinterfaces
Lab – Configuring Frame Relay and Subinterfaces Topology © 2013 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 19 Lab – Configuring Frame Relay and Subinterfaces Addressing Table Device Interface IPv4 and IPv6 Address Default Gateway 192.168.1.1/24 2001:DB8:ACAD:A::1/64 R1 G0/0 FE80::1 link-local N/A 10.1.1.1/30 2001:DB8:ACAD:B::1/64 S0/0/0 (DCE) FE80::1 link-local N/A FR S0/0/0 N/A N/A S0/0/1 (DCE) N/A N/A 192.168.3.1/24 2001:DB8:ACAD:C::3/64 R3 G0/0 FE80::3 link-local N/A 10.1.1.2/30 2001:DB8:ACAD:B::3/64 S0/0/1 FE80::3 link-local N/A 192.168.1.3/24 192.168.1.1 PC-A NIC 2001:DB8:ACAD:A::A/64 FE80::1 192.168.3.3/24 192.168.3.1 PC-C NIC 2001:DB8:ACAD:C::C/64 FE80::3 Objectives Part 1: Build the Network and Configure Basic Device Settings Part 2: Configure a Frame Relay Switch Part 3: Configure Basic Frame Relay Part 4: Troubleshoot Frame Relay Part 5: Configure a Frame Relay Subinterface Background / Scenario Frame Relay is a high-performance WAN protocol that operates at the physical and data link layers of the OSI reference model. Unlike leased lines, Frame Relay requires only a single access circuit to the Frame Relay provider to communicate with multiple sites that are connected to the same provider. -

High-Level Data Link Control
ELEC3030 (EL336) Computer Networks S Chen High-Level Data Link Control • This class of data link layer protocols includes High-level Data Link Control (HDLC), Link Access Procedure Balanced (LAPB) for X.25, Link Access Procedure for D-channel (LAPD) for ISDN, and Logic Link Control (LLC) for FDDI • The frame format is: Flag Address Control Data FCS Flag Note that address and control bits 8 8 8 variable 16 8 can be extended to 16 bits, so bit position 12 3 4 5 6 7 8 N(S)=send sequence number N(R)=receive sequence number that sequence number is 7-bit Information: 0 N(S) P/F N(R) S=supervisory function bits P/F • Frame flag: 01111110, so bit Supervisory: 1 0 S N(R) M=unumbered function bits stuffing is used Unumbered: 1 1 M P/F M P/F=poll/final bit • Address: For multipoint operation, it is used to identify the terminal that transmits or receives the frame and, in point-to-point link, it is used to distinguish Commands from Responses (2nd bit for C/R: 0/1). The address is now extended to 16 bits (1st bit indicates long/short 16/8 bits) • Checksum: FCS contains the remainder of a 16-bit CRC calculation of the frame. It may be extended to 32 bits, using a 32-bit CRC • Control: Three types of frames, I, S and U frames. The old protocol uses a sliding window with 3-bit sequence number and the maximum window size is N = 7. The control field is now extended to 16 bits with 7-bit sequence number 60 ELEC3030 (EL336) Computer Networks S Chen HDLC (continue) • I-frames: carry user data. -

Lab Implementation of Ipv6 in Enterprise Network Using Cisco Packet Tracer
Turkish Journal of Computer and Mathematics Education Vol.12 No.10 (2021), 6564 – 6580 Research Article Lab Implementation of IPv6 in Enterprise Network Using Cisco Packet Tracer Mohammad Ali Sadata, Priyanka Meelb a,b Department of Information Technology, Delhi Technological University, India a [email protected], b [email protected] Article History: Received: 11 January 2021; Revised: 12 February 2021; Accepted: 27 March 2021; Published online: 28 April 2021 Abstract: As technology is growing fast, using technologies is also increasing because the previous technologies cannot support the new requirements. In this case, every company is trying to implement newly released technologies. As IPv4 was introduced, it has been used for a long time in networking. But now, the limitations of IPv4 are too much, such as address limitation, subnet-ting with complex structure, inefficient NAT employment. This is why IPv4 is not considered to be used anymore. Because of IPv4 problems, the IPv6 protocol is designed and developed to overcome IPv4 limitations. The efficiency of IPv6 is more in packet processing, and routing pro-vides a simple network configuration and improves the QoS by decreasing latency in the time of the data packet transformation. As IPv6 has many features and new supported services. With the emergence of IPv6, any enterprise companies are interested in implementing IPv6 in the enterprise network. An enterprise network includes protocols, virtual and physical networks that connect all systems and users on a LAN, and all applications in the cloud and data center. The main purpose of this research is to implement ipv6in the enterprise network. -

How to Configure Frame Relay Over a DS3 Interface Between Two Rapier 24I Switches
How to configure Frame Relay over a DS3 interface between two Rapier 24i switches Introduction This document provides a basic configuration example for configuring Frame Relay over a DS3 interface between two Rapier 24i switches. Frame Relay Frame Relay is a network service, defined by ITU-T (formerly CCITT), ANSI and vendor standards, to which switches may connect in order to communicate with one another and exchange data. Connections can be made via synchronous lines, DS3 lines, ISDN calls or G.703 TDM (Time Division Multiplexing) links. A Frame Relay network provides Data Link Connections (DLCs) between the switches connected to the network. These DLCs are set up by the Frame Relay network administration. One DLC is reserved for the communication of management information between the routers and the Frame Relay network, in a dialogue called the Local Management Interface (LMI). Frame Relay itself exists purely as a way for frames to get from one switch to another in an efficient manner. Frames sent to the network must contain the Data Link Connection Identifier (DLCI) of the DLC to use to deliver the frame. Except for LMI frames, the rest of the content of the frame is determined by the switch-to-switch communication and is not used by the network. In order for switches to transport multiple protocols across a single DLC the data being transmitted must be encapsulated to allow the remote switch to identify the type of network protocol packet contained in the frame. A common standard for carrying multiple protocols over Frame Relay is specified by the IETF in RFC 1294. -

Frame Relay Vs. IP Vpns
Contents: The Case for Frame Relay The Case for IP VPNs Conclusion Frame Relay vs. IP VPNs 2002 02089 9/02 Contents: Table of Contents Introduction 2 Definition of Terms 2 “Virtual” Privacy and 3 the Value of Shared Networks The Three Definitions 3 or Distinctions of VPN The Case for Frame Relay 4 The Case for IP Virtual Private Networks 6 Conclusion 8 1 02089 9/02 Introduction: Introduction Definition of Terms Welcome to one in a series of white papers The following definitions will be used in this brought to you by Sprint. We believe it is white paper: important to inform you on issues in the industry and to keep you updated on our VPN — Virtual Private Network is a private current endeavors. communications network that uses a shared network as its Wide Area Network (WAN) A major challenge in today’s data transport backbone, thereby offering the appearance market is that businesses wanting to and functionality of a dedicated private implement a Virtual Private Network (VPN) network at a reduced price. are faced with a dizzying array of options and have few guidelines from which to make IP VPN — An IP Security (IPSec)-based VPN an educated decision. The sheer breadth of that uses encryption and authentication to available VPN offerings can be overwhelming, offer the appearance and functionality of a especially for those unfamiliar with the relative private data network over a shared IP network merits and capabilities of all the alternatives. such as the Internet. In this paper, IP VPN will be discussed in terms of both Sprint CPE- To answer this challenge, Sprint has based IP VPNs and Network-based IP VPNs. -

VPN Tech Brief MM
A DETAILED ANALYSIS OF FR-VPNs vs. IP-VPNs VPNs Frame Relay A Comparison of IP-VPN and Frame Relay Services Description Secure Transmissions carriers may constitute a strong value proposi- tion for price-sensitive customers willing to Say “VPN” and most people think Internet Today, one way IP-VPNS are being deployed is give up SLA and security, a consideration that technology. Generically defined, a Virtual through ISPs who are building IP tunnels “traditional” carriers will not underestimate. Private Network (VPN) is a means of through their backbones as special, secure With the potential threat of new entrants, transmitting digital information over a shared paths for customers’ traffic. However, users carriers will have a strong incentive to protect public network infrastructure in which secure trust frame relay Permanent Virtual Circuits their installed base and resulting revenue. and reliable connectivity, management and (PVCs) to provide adequate security for most The ISP/carrier consolidation will also push addressing is equivalent virtually to that of a applications without having to create tunnels the service providers to rationalize and posi- private network. and use encryption as default. PVCs inherent- tion their own offerings within their product Despite the recent excitement about ly provide a “tunnel” of sorts in that the line so as to minimize cannibalization effects. IP-VPNs, Layer 2 VPNs have been available network operator (within the company or since the mid to late 1980s as VPDNs. Current service provider) establishes the DLCIs managed frame relay services run mission- associated with a different access device. In Flexibility and Any-to-Any critical applications and provide secure, stable addition, packets with corrupted addressing predictable and highly manageable solutions. -
Medium Access Control Sublayer
Telematics Chapter 5: Medium Access Control Sublayer User Server watching with video Beispielbildvideo clip clips Application Layer Application Layer Presentation Layer Presentation Layer Session Layer Session Layer Transport Layer Transport Layer Network Layer Network Layer Network Layer Prof. Dr. Mesut Güneş Data Link Layer Data Link Layer Data Link Layer Computer Systems and Telematics (CST) Physical Layer Physical Layer Physical Layer Distributed, embedded Systems Institute of Computer Science Freie Universität Berlin http://cst.mi.fu-berlin.de Contents ● Design Issues ● Metropolitan Area Networks ● Network Topologies (()MAN) ● The Channel Allocation Problem ● Wide Area Networks (WAN) ● Multiple Access Protocols ● Frame Relay ● Ethernet ● ATM ● IEEE 802.2 – Logical Link Control ● SDH ● Token Bus ● Network Infrastructure ● Token Ring ● Virtual LANs ● Fiber Distributed Data Interface ● Structured Cabling Prof. Dr. Mesut Güneş ▪ cst.mi.fu-berlin.de ▪ Telematics ▪ Chapter 5: Medium Access Control Sublayer 5.2 Design Issues Prof. Dr. Mesut Güneş ▪ cst.mi.fu-berlin.de ▪ Telematics ▪ Chapter 5: Medium Access Control Sublayer 5.3 Design Issues ● Two kinds of connections in networks ● Point-to-point connections OSI Reference Model ● Broadcast (Multi-access channel, Application Layer Random access channel) Presentation Layer ● In a network with broadcast Session Layer connections ● Who gets the channel? Transport Layer Network Layer ● PtProtoco ls use dtdtd to determ ine w ho gets next access to the channel Data Link Layer ● Medium Access Control (()MAC) sublay er Phy sical Laye r Prof. Dr. Mesut Güneş ▪ cst.mi.fu-berlin.de ▪ Telematics ▪ Chapter 5: Medium Access Control Sublayer 5.4 Network Types for the Local Rang e ● LLC layer: uniform interface and same frame format to upper layers ● MAC layer: defines medium access - LLC IEEE 802.2 Logical Link Control .. -

Wide-Area Networking Overview
Wide-Area Networking Overview Last Updated: October 6, 2011 Cisco IOS software provides a range of wide-area networking capabilities to fit almost every network environment need. Cisco offers cell relay via the Switched Multimegabit Data Service (SMDS), circuit switching via ISDN, packet switching via Frame Relay, and the benefits of both circuit and packet switching via Asynchronous Transfer Mode (ATM). LAN emulation (LANE) provides connectivity between ATM and other LAN types. The Cisco IOS Wide-Area Networking Configuration Guide presents a set of general guidelines for configuring the following software components: This module gives a high-level description of each technology. For specific configuration information, see the appropriate module. • Finding Feature Information, page 1 • Frame Relay, page 1 • Switched Multimegabit Data Service, page 4 • Link Access Procedure - Balanced and X.25, page 5 • Layer 2 Virtual Private Network, page 6 • Wide Area Application Services, page 7 Finding Feature Information Your software release may not support all the features documented in this module. For the latest feature information and caveats, see the release notes for your platform and software release. To find information about the features documented in this module, and to see a list of the releases in which each feature is supported, see the Feature Information Table at the end of this document. Use Cisco Feature Navigator to find information about platform support and Cisco software image support. To access Cisco Feature Navigator, go to www.cisco.com/go/cfn. An account on Cisco.com is not required. Frame Relay The Cisco Frame Relay implementation currently supports routing on IP, DECnet, AppleTalk, XNS, Novell IPX, CLNS, Banyan VINES, and transparent bridging.