Securing Debian HOWTO
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

The Elinks Manual the Elinks Manual Table of Contents Preface
The ELinks Manual The ELinks Manual Table of Contents Preface.......................................................................................................................................................ix 1. Getting ELinks up and running...........................................................................................................1 1.1. Building and Installing ELinks...................................................................................................1 1.2. Requirements..............................................................................................................................1 1.3. Recommended Libraries and Programs......................................................................................1 1.4. Further reading............................................................................................................................2 1.5. Tips to obtain a very small static elinks binary...........................................................................2 1.6. ECMAScript support?!...............................................................................................................4 1.6.1. Ok, so how to get the ECMAScript support working?...................................................4 1.6.2. The ECMAScript support is buggy! Shall I blame Mozilla people?..............................6 1.6.3. Now, I would still like NJS or a new JS engine from scratch. .....................................6 1.7. Feature configuration file (features.conf).............................................................................7 -

On Trends in Low-Level Exploitation
On trends in low-level exploitation Christian W. Otterstad Department of Informatics, University of Bergen Abstract Low-level computer exploitation and its mitigation counterpart has accumulated some noteworthy history. Presently, especially in academia, it features a plethora of mitigation techniques and also various possible modes of attack. It has seen numerous developments building upon basic methods for both sides and certain trends have emerged. This paper is primarily an overview paper, focusing especially on x86 GNU/Linux. The basic reasons inherent for allowing low-level exploitability are identified and explained to provide background knowledge. The paper furthermore describes the history, present state of the art and future developments that are topical and appear to be important in the field. Several attack and defense techniques have overlapping notions with not always obvious differences. Herein the notion of the bar being raised for both exploits and mitigation methods is examined and extrapolated upon based on the known relevant present state and history. The difference between academia and the industry is discussed especially where it relates to application of new mitigation techniques. Based on this examination some patterns and trends are identified and a conjecture for the likely future development of both is presented and justified. This paper was presented at the NIK-2016 conference; see http://www.nik.no/. 1 Introduction and earlier related work In 1972 the paper “Computer Security Technology Planning Study” was published [1]. Since then, research surrounding the main ideas in this paper has grown to become a ma- ture and complex field in its own right. There are many different exploitation techniques and mitigation techniques. -

Detecting Exploit Code Execution in Loadable Kernel Modules
Detecting Exploit Code Execution in Loadable Kernel Modules HaizhiXu WenliangDu SteveJ.Chapin Systems Assurance Institute Syracuse University 3-114 CST, 111 College Place, Syracuse, NY 13210, USA g fhxu02, wedu, chapin @syr.edu Abstract and pointer checks can lead to kernel-level exploits, which can jeopardize the integrity of the running kernel. Inside the In current extensible monolithic operating systems, load- kernel, exploitcode has the privilegeto interceptsystem ser- able kernel modules (LKM) have unrestricted access to vice routines, to modify interrupt handlers, and to overwrite all portions of kernel memory and I/O space. As a result, kernel data. In such cases, the behavior of the entire sys- kernel-module exploitation can jeopardize the integrity of tem may become suspect. the entire system. In this paper, we analyze the threat that Kernel-level protection is different from user space pro- comes from the implicit trust relationship between the oper- tection. Not every application-level protection mechanism ating system kernel and loadable kernel modules. We then can be applied directly to kernel code, because privileges present a specification-directed access monitoring tool— of the kernel environment is different from that of the user HECK, that detects kernel modules for malicious code ex- space. For example, non-executableuser page [21] and non- ecution. Inside the module, HECK prevents code execution executable user stack [29] use virtual memory mapping sup- on the kernel stack and the data sections; on the bound- port for pages and segments, but inside the kernel, a page ary, HECK restricts the module’s access to only those kernel or segment fault can lead to kernel panic. -

MX Linux Benutzerhandbuch V
MX Linux Benutzerhandbuch v. 20210327 manual AT mxlinux DOT org MX Linux Webseite MX Linux deutschsprachiges Forum Strg-F = Dieses Handbuch durchsuchen Pos1 / Home = Zum Anfang des Dokuments Translation: Sigi Vranšak – SpinBit Informatik Schaan, 27.03.2021 Tools: LibreOffice 7.0.4, deepl.com Rückmeldungen zu diesem deutschsprachigen Handbuch bitte an: [email protected] OpenPGP 51F0D5C53CF46E29 Titel des englischen Originals: MX Linux Users Manual v. 20200801 Inhalt 1 Einleitung.........................................................................................................................................7 1.1 Über MX Linux..........................................................................................................................7 1.2 Über dieses Handbuch.............................................................................................................7 1.3 Systemanforderungen..............................................................................................................8 1.4 Unterstützung und «Lebensdauer» (EOL, End Of Life)...........................................................8 1.5 Fehler, Probleme und Anfragen, Anträge.................................................................................9 1.6 Migration, Upgrade (Aktualisierung nächste Hauptversion)..................................................10 1.7 Unsere Standpunkte...............................................................................................................10 1.7.1 Systemd..........................................................................................................................10 -

The Linux Gamers' HOWTO
The Linux Gamers’ HOWTO Peter Jay Salzman Frédéric Delanoy Copyright © 2001, 2002 Peter Jay Salzman Copyright © 2003, 2004 Peter Jay SalzmanFrédéric Delanoy 2004-11-13 v.1.0.6 Abstract The same questions get asked repeatedly on Linux related mailing lists and news groups. Many of them arise because people don’t know as much as they should about how things "work" on Linux, at least, as far as games go. Gaming can be a tough pursuit; it requires knowledge from an incredibly vast range of topics from compilers to libraries to system administration to networking to XFree86 administration ... you get the picture. Every aspect of your computer plays a role in gaming. It’s a demanding topic, but this fact is shadowed by the primary goal of gaming: to have fun and blow off some steam. This document is a stepping stone to get the most common problems resolved and to give people the knowledge to begin thinking intelligently about what is going on with their games. Just as with anything else on Linux, you need to know a little more about what’s going on behind the scenes with your system to be able to keep your games healthy or to diagnose and fix them when they’re not. 1. Administra If you have ideas, corrections or questions relating to this HOWTO, please email me. By receiving feedback on this howto (even if I don’t have the time to answer), you make me feel like I’m doing something useful. In turn, it motivates me to write more and add to this document. -

MX-18.3 Users Manual
MX-18.3 Users Manual v. 20190614 manual AT mxlinux DOT org Ctrl-F = Search this Manual Ctrl+Home = Return to top Table of Contents 1 Introduction................................................................................2 2 Installation..................................................................................8 3 Configuration...........................................................................37 4 Basic use..................................................................................93 5 Software Management...........................................................126 6 Advanced use.........................................................................141 7 Under the hood.......................................................................164 8 Glossary.................................................................................178 1 Introduction 1.1 About MX Linux MX Linux is a cooperative venture between the antiX and former MEPIS communities, using the best tools and talents from each distro and including work and ideas originally created by Warren Woodford. It is a midweight OS designed to combine an elegant and efficient desktop with simple configuration, high stability, solid performance and medium-sized footprint. Relying on the excellent upstream work by Linux and the open-source community, we deploy Xfce 4.12 as Desktop Environment on top of a Debian Stable base, drawing from the core antiX system. Ongoing backports and outside additions to our Repos serve to keep components current with developments. -

Pipenightdreams Osgcal-Doc Mumudvb Mpg123-Alsa Tbb
pipenightdreams osgcal-doc mumudvb mpg123-alsa tbb-examples libgammu4-dbg gcc-4.1-doc snort-rules-default davical cutmp3 libevolution5.0-cil aspell-am python-gobject-doc openoffice.org-l10n-mn libc6-xen xserver-xorg trophy-data t38modem pioneers-console libnb-platform10-java libgtkglext1-ruby libboost-wave1.39-dev drgenius bfbtester libchromexvmcpro1 isdnutils-xtools ubuntuone-client openoffice.org2-math openoffice.org-l10n-lt lsb-cxx-ia32 kdeartwork-emoticons-kde4 wmpuzzle trafshow python-plplot lx-gdb link-monitor-applet libscm-dev liblog-agent-logger-perl libccrtp-doc libclass-throwable-perl kde-i18n-csb jack-jconv hamradio-menus coinor-libvol-doc msx-emulator bitbake nabi language-pack-gnome-zh libpaperg popularity-contest xracer-tools xfont-nexus opendrim-lmp-baseserver libvorbisfile-ruby liblinebreak-doc libgfcui-2.0-0c2a-dbg libblacs-mpi-dev dict-freedict-spa-eng blender-ogrexml aspell-da x11-apps openoffice.org-l10n-lv openoffice.org-l10n-nl pnmtopng libodbcinstq1 libhsqldb-java-doc libmono-addins-gui0.2-cil sg3-utils linux-backports-modules-alsa-2.6.31-19-generic yorick-yeti-gsl python-pymssql plasma-widget-cpuload mcpp gpsim-lcd cl-csv libhtml-clean-perl asterisk-dbg apt-dater-dbg libgnome-mag1-dev language-pack-gnome-yo python-crypto svn-autoreleasedeb sugar-terminal-activity mii-diag maria-doc libplexus-component-api-java-doc libhugs-hgl-bundled libchipcard-libgwenhywfar47-plugins libghc6-random-dev freefem3d ezmlm cakephp-scripts aspell-ar ara-byte not+sparc openoffice.org-l10n-nn linux-backports-modules-karmic-generic-pae -
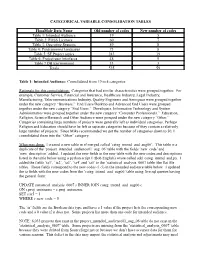
Categorical Variable Consolidation Tables
CATEGORICAL VARIABLE CONSOLIDATION TABLES FlossMole Data Name Old number of codes New number of codes Table 1: Intended Audience 19 5 Table 2: FOSS Licenses 60 7 Table 3: Operating Systems 59 8 Table 4: Programming languages 73 8 Table 5: SF Project topics 243 19 Table 6: Project user interfaces 48 9 Table 7 DB Environment 33 3 Totals 535 59 Table 1: Intended Audience: Consolidated from 19 to 4 categories Rationale for this consolidation: Categories that had similar characteristics were grouped together. For example, Customer Service, Financial and Insurance, Healthcare Industry, Legal Industry, Manufacturing, Telecommunications Industry, Quality Engineers and Aerospace were grouped together under the new category “Business.” End Users/Desktop and Advanced End Users were grouped together under the new category “End Users.” Developers, Information Technology and System Administrators were grouped together under the new category “Computer Professionals.” Education, Religion, Science/Research and Other Audience were grouped under the new category “Other.” Categories containing large numbers of projects were generally left as individual categories. Perhaps Religion and Education should have be left as separate categories because of they contain a relatively large number of projects. Since Mike recommended we get the number of categories down to 50, I consolidated them into the “Other” category. What was done: I created a new table in sf merged called ‘categ_intend_aud_aug06’. This table is a duplicate of the ‘project_intended_audience01_aug_06’ table with the fields ‘new_code’ and ‘new_description’ added. I updated the new fields in the new table with the new codes and descriptions listed in the table below using a python script I (Bob English) wrote called add_categ_intend_aud.py. -

Securing Debian Manual
Securing Debian Manual Javier Fernández-Sanguino Peña <[email protected]> 2.6 10 octubre 2002Wed, 18 Sep 2002 14:09:35 +0200 Abstract This document describes the process of securing and hardening the default Debian installation. It covers some of the common tasks to set up a secure network environment using Debian GNU/Linux. It also gives additional information on the security tools available as well as the work done by the Debian security team. Copyright Notice Copyright © 2002 Javier Fernández-Sanguino Peña Copyright © 2001 Alexander Reelsen, Javier Fernández-Sanguino Peña Copyright © 2000 Alexander Reelsen Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation License, Version 1.1 (http://www.fsf.org/copyleft/fdl. html) or any later version published by the Free Software Foundation. It is distributed in the hope that it will be useful, but WITHOUT ANY WARRANTY. i Contents 1 Introduction 1 1.1 Download the manual .................................. 1 1.2 Organizational Notes/Feedback ............................ 2 1.3 Prior knowledge ...................................... 2 1.4 Things that need to be written (FIXME/TODO) .................... 2 1.5 Changelog/History .................................... 5 1.5.1 Version 2.6 (september 2002) .......................... 5 1.5.2 Version 2.5 (september 2002) .......................... 5 1.5.3 Version 2.5 (august 2002) ............................ 5 1.5.4 Version 2.4 ..................................... 9 1.5.5 Version 2.3 ..................................... 9 1.5.6 Version 2.3 ..................................... 9 1.5.7 Version 2.2 ..................................... 10 1.5.8 Version 2.1 ..................................... 10 1.5.9 Version 2.0 ..................................... 10 1.5.10 Version 1.99 ................................... -

Integrity Checking for Process Hardening
Integrity Checking For Process Hardening by Kyung-suk Lhee B.A. Korea University, 1991 Graduate Diploma, Griffith University, 1993 M.A. Boston University, 1995 DISSERTATION Submitted in partial fulfillment of the requirements for the degree of Doctor of Philosophy in Computer and Information Science in the Graduate School of Syracuse University May 2005 Advisor: Professor Steve J. Chapin Abstract Computer intrusions can occur in various ways. Many of them occur by exploiting program flaws and system configuration errors. Existing solutions that detects specific kinds of flaws are substantially different from each other, so aggregate use of them may be incompatible and require substantial changes in the current system and computing practice. Intrusion detection systems may not be the answer either, because they are inherently inaccurate and susceptible to false positives/negatives. This dissertation presents a taxonomy of security flaws that classifies program vulnerabilities into finite number of error categories, and presents a security mechanism that can produce accurate solutions for many of these error categories in a modular fashion. To be accurate, a solution should closely match the characteristic of the target error category. To ensure this, we focus only on error categories whose characteristics can be defined in terms of a violation of process integrity. The thesis of this work is that the proposed approach produces accurate solutions for many error categories. To prove the accuracy of produced solutions, we define the process integrity checking approach and analyze its properties. To prove that this approach can cover many error categories, we develop a classification of program security flaws and find error characteristics (in terms of a process integrity) from many of these categories. -

Secure Programming for Linux HOWTO Secure Programming for Linux HOWTO
Secure Programming for Linux HOWTO Secure Programming for Linux HOWTO Table of Contents Secure Programming for Linux HOWTO........................................................................................................1 David A. Wheeler, dwheeler@dwheeler.com.........................................................................................1 1.Introduction...........................................................................................................................................1 2.Background...........................................................................................................................................1 3.Summary of Linux Security Features...................................................................................................1 4.Validate All Input.................................................................................................................................1 5.Avoid Buffer Overflow.........................................................................................................................2 6.Structure Program Internals and Approach...........................................................................................2 7.Carefully Call Out to Other Resources.................................................................................................2 8.Send Information Back Judiciously......................................................................................................2 9.Special Topics.......................................................................................................................................2 -

EXPRESSSCOPE Engine 3 User's Guide
EXPRESSSCOPE Engine 3 User’s Guide Scalable Modular Server DX2000 1. Overview 2. Configuring the Server Module 3. Configuring a Management PC 4. Networking 5. Using Remote Management 6. Troubleshooting 20.102.01-120-02 April, 2016 TRADEMARKS AND PATENTS EXPRESSSCOPE is registered trademarks of NEC Corporation. Microsoft, Windows and Windows Vista, Windows Media Player, Windows Server, Internet Explorer are registered trademarks of Microsoft Corporation in the United States and other countries. Firefox is registered trademarks of the Mozilla Foundation. Java is registered trademarks of Oracle and/or its affiliates. Red Hat is registered trademarks of Red Hat, Inc. in the United States and other countries. Active Directory is registered trademarks of Microsoft Corporation in the United States and other countries. NFS is registered trademarks of Sun Microsystems, Inc. in the United States and other countries. (Sun Microsystems is registered trademarks of Oracle and/or its affiliates) Linux is registered trademarks of Mr. Linus Torvalds in the United States and other countries. UNIX is registered trademarks of The Open Group in the United States and other countries. JavaScript is registered trademarks of Oracle and/or its affiliates. OpenLDAP is registered trademarks of the OpenLDAP Foundation. NOTES (1) No part of this manual may be reproduced in any form without the prior written permission of NEC Corporation. (2) The contents of this User’s Guide may be revised without prior notice. (3) The contents of this User's Guide shall not be copied or altered without the prior written permission of NEC Corporation. (4) All efforts have been made to ensure the accuracy of all information in this User's Guide.