Programming in C & Living in Unix
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Application Program Interface Guide
APPLICATION PROGRAM INTERFACE GUIDE VWS-2001, VWS-2002 V WS-2001 V WS-2002 API GUIDE 24/7 TECHNICAL SUPPORT AT 1.877.877.2269 OR VISIT BLACKBOX.COM RemoteRemote Command Command Line Line Status Configure Status Client connected Enabled Monitor Client authorized Settings… Client disconnected Client authorized “C:\Program Files (x86)\Wall Control\wallctl.exe”- Active Server Telnet Command Lin — — — OK Cancel Apply Help NEED HELP? LEAVE THE TECH TO US LIVE 24/7 TABLE OF CONTENTS TECHNICAL SUPPORT 1.877.877.2269 1. INTRODUCTION ............................................................................................................................................................................. 3 1.1 API Programs ................................................................................................................................................................................................................3 1.2 Nomenclature ...............................................................................................................................................................................................................3 2. LAYOUTS ........................................................................................................................................................................................ 4 2.1 Example Usage ............................................................................................................................................................................................................4 -

Managing Projects with GNU Make, Third Edition by Robert Mecklenburg
ManagingProjects with GNU Make Other resources from O’Reilly Related titles Unix in a Nutshell sed and awk Unix Power Tools lex and yacc Essential CVS Learning the bash Shell Version Control with Subversion oreilly.com oreilly.com is more than a complete catalog of O’Reilly books. You’ll also find links to news, events, articles, weblogs, sample chapters, and code examples. oreillynet.com is the essential portal for developers interested in open and emerging technologies, including new platforms, pro- gramming languages, and operating systems. Conferences O’Reilly brings diverse innovators together to nurture the ideas that spark revolutionary industries. We specialize in document- ing the latest tools and systems, translating the innovator’s knowledge into useful skills for those in the trenches. Visit con- ferences.oreilly.com for our upcoming events. Safari Bookshelf (safari.oreilly.com) is the premier online refer- ence library for programmers and IT professionals. Conduct searches across more than 1,000 books. Subscribers can zero in on answers to time-critical questions in a matter of seconds. Read the books on your Bookshelf from cover to cover or sim- ply flip to the page you need. Try it today with a free trial. THIRD EDITION ManagingProjects with GNU Make Robert Mecklenburg Beijing • Cambridge • Farnham • Köln • Sebastopol • Tokyo Managing Projects with GNU Make, Third Edition by Robert Mecklenburg Copyright © 2005, 1991, 1986 O’Reilly Media, Inc. All rights reserved. Printed in the United States of America. Published by O’Reilly Media, Inc., 1005 Gravenstein Highway North, Sebastopol, CA 95472. O’Reilly books may be purchased for educational, business, or sales promotional use. -

Introduction to Linux – Part 1
Introduction to Linux – Part 1 Brett Milash and Wim Cardoen Center for High Performance Computing May 22, 2018 ssh Login or Interactive Node kingspeak.chpc.utah.edu Batch queue system … kp001 kp002 …. kpxxx FastX ● https://www.chpc.utah.edu/documentation/software/fastx2.php ● Remote graphical sessions in much more efficient and effective way than simple X forwarding ● Persistence - can be disconnected from without closing the session, allowing users to resume their sessions from other devices. ● Licensed by CHPC ● Desktop clients exist for windows, mac, and linux ● Web based client option ● Server installed on all CHPC interactive nodes and the frisco nodes. Windows – alternatives to FastX ● Need ssh client - PuTTY ● http://www.chiark.greenend.org.uk/~sgtatham/putty/download.html - XShell ● http://www.netsarang.com/download/down_xsh.html ● For X applications also need X-forwarding tool - Xming (use Mesa version as needed for some apps) ● http://www.straightrunning.com/XmingNotes/ - Make sure X forwarding enabled in your ssh client Linux or Mac Desktop ● Just need to open up a terminal or console ● When running applications with graphical interfaces, use ssh –Y or ssh –X Getting Started - Login ● Download and install FastX if you like (required on windows unless you already have PuTTY or Xshell installed) ● If you have a CHPC account: - ssh [email protected] ● If not get a username and password: - ssh [email protected] Shell Basics q A Shell is a program that is the interface between you and the operating system -

13-DUALOSS-MV Commercial Grade In-Wall Occupancy/Vacancy Sensor
13-DUALOSS-MV Commercial Grade In-Wall Occupancy/Vacancy Sensor APPLICATIONS This Multi-Technology Wall Switch Sensor combine advanced passive infrared (PIR) and ultrasonic technologies into one unit. The combined technologies helps eliminate false triggering even in difficult applications. Selectable operating modes allow the sensor to turn a load on, and hold it on as long as either or both technologies detect occupancy . After no movement is detected for the selected time delay, the lights switch off. A "walk-through" mode can turn lights off after only 3 minutes, if no activity is detected after 30 seconds following an occupancy detection. This sensor also contains a light level sensor. If adequate daylight is present, the sensor holds the load OFF until light levels drop, even if the area is occupied. MODEL #: 13-DUALOSS-MV FEATURES • Integrated PIR and Ultrasonic sensor technology to detect very fine COVERAGE AREA motion and provide accurate motion sensing Top View • Allows to choose triggering when both technologies detect motion or when only PIR detects motion 20' • Less false trigger, fast ON/OFF; commercial grade sensor for closet, garage, hotels, meeting room, work places 10' • Adjustable timeout from 15 seconds to 30 minutes; Walk-Through mode: 3 minutes if no activity after first 30 seconds SPECIFICATIONS 10' • Voltage: 120/277VAC, 50/60Hz • Incandescent: 800W-120VAC, 50/60Hz • Fluorescent: 800VA-120VAC, 1600VA-277VAC, 50/60Hz 20' • Resistive: 800W-120VAC, 50/60Hz • Motor: 1/4 HP-120VAC, 50/60Hz • Adjustment Time Delay: 5 Sec to 30 Mins 5' • Walk-Through Mode: 3-minutes if no activity after 30 sec. -

Unix: Beyond the Basics
Unix: Beyond the Basics BaRC Hot Topics – September, 2018 Bioinformatics and Research Computing Whitehead Institute http://barc.wi.mit.edu/hot_topics/ Logging in to our Unix server • Our main server is called tak4 • Request a tak4 account: http://iona.wi.mit.edu/bio/software/unix/bioinfoaccount.php • Logging in from Windows Ø PuTTY for ssh Ø Xming for graphical display [optional] • Logging in from Mac ØAccess the Terminal: Go è Utilities è Terminal ØXQuartz needed for X-windows for newer OS X. 2 Log in using secure shell ssh –Y user@tak4 PuTTY on Windows Terminal on Macs Command prompt user@tak4 ~$ 3 Hot Topics website: http://barc.wi.mit.edu/education/hot_topics/ • Create a directory for the exercises and use it as your working directory $ cd /nfs/BaRC_training $ mkdir john_doe $ cd john_doe • Copy all files into your working directory $ cp -r /nfs/BaRC_training/UnixII/* . • You should have the files below in your working directory: – foo.txt, sample1.txt, exercise.txt, datasets folder – You can check they’re there with the ‘ls’ command 4 Unix Review: Commands Ø command [arg1 arg2 … ] [input1 input2 … ] $ sort -k2,3nr foo.tab -n or -g: -n is recommended, except for scientific notation or start end a leading '+' -r: reverse order $ cut -f1,5 foo.tab $ cut -f1-5 foo.tab -f: select only these fields -f1,5: select 1st and 5th fields -f1-5: select 1st, 2nd, 3rd, 4th, and 5th fields $ wc -l foo.txt How many lines are in this file? 5 Unix Review: Common Mistakes • Case sensitive cd /nfs/Barc_Public vs cd /nfs/BaRC_Public -bash: cd: /nfs/Barc_Public: -

LAB MANUAL for Computer Network
LAB MANUAL for Computer Network CSE-310 F Computer Network Lab L T P - - 3 Class Work : 25 Marks Exam : 25 MARKS Total : 50 Marks This course provides students with hands on training regarding the design, troubleshooting, modeling and evaluation of computer networks. In this course, students are going to experiment in a real test-bed networking environment, and learn about network design and troubleshooting topics and tools such as: network addressing, Address Resolution Protocol (ARP), basic troubleshooting tools (e.g. ping, ICMP), IP routing (e,g, RIP), route discovery (e.g. traceroute), TCP and UDP, IP fragmentation and many others. Student will also be introduced to the network modeling and simulation, and they will have the opportunity to build some simple networking models using the tool and perform simulations that will help them evaluate their design approaches and expected network performance. S.No Experiment 1 Study of different types of Network cables and Practically implement the cross-wired cable and straight through cable using clamping tool. 2 Study of Network Devices in Detail. 3 Study of network IP. 4 Connect the computers in Local Area Network. 5 Study of basic network command and Network configuration commands. 6 Configure a Network topology using packet tracer software. 7 Configure a Network topology using packet tracer software. 8 Configure a Network using Distance Vector Routing protocol. 9 Configure Network using Link State Vector Routing protocol. Hardware and Software Requirement Hardware Requirement RJ-45 connector, Climping Tool, Twisted pair Cable Software Requirement Command Prompt And Packet Tracer. EXPERIMENT-1 Aim: Study of different types of Network cables and Practically implement the cross-wired cable and straight through cable using clamping tool. -

Install and Run External Command Line Softwares
job monitor and control top: similar to windows task manager (space to refresh, q to exit) w: who is there ps: all running processes, PID, status, type ps -ef | grep yyin bg: move current process to background fg: move current process to foreground jobs: list running and suspended processes kill: kill processes kill pid (could find out using top or ps) 1 sort, cut, uniq, join, paste, sed, grep, awk, wc, diff, comm, cat All types of bioinformatics sequence analyses are essentially text processing. Unix Shell has the above commands that are very useful for processing texts and also allows the output from one command to be passed to another command as input using pipe (“|”). less cosmicRaw.txt | cut -f2,3,4,5,8,13 | awk '$5==22' | cut -f1 | sort -u | wc This makes the processing of files using Shell very convenient and very powerful: you do not need to write output to intermediate files or load all data into the memory. For example, combining different Unix commands for text processing is like passing an item through a manufacturing pipeline when you only care about the final product 2 Hands on example 1: cosmic mutation data - Go to UCSC genome browser website: http://genome.ucsc.edu/ - On the left, find the Downloads link - Click on Human - Click on Annotation database - Ctrl+f and then search “cosmic” - On “cosmic.txt.gz” right-click -> copy link address - Go to the terminal and wget the above link (middle click or Shift+Insert to paste what you copied) - Similarly, download the “cosmicRaw.txt.gz” file - Under your home, create a folder -

PS TEXT EDIT Reference Manual Is Designed to Give You a Complete Is About Overview of TEDIT
Information Management Technology Library PS TEXT EDIT™ Reference Manual Abstract This manual describes PS TEXT EDIT, a multi-screen block mode text editor. It provides a complete overview of the product and instructions for using each command. Part Number 058059 Tandem Computers Incorporated Document History Edition Part Number Product Version OS Version Date First Edition 82550 A00 TEDIT B20 GUARDIAN 90 B20 October 1985 (Preliminary) Second Edition 82550 B00 TEDIT B30 GUARDIAN 90 B30 April 1986 Update 1 82242 TEDIT C00 GUARDIAN 90 C00 November 1987 Third Edition 058059 TEDIT C00 GUARDIAN 90 C00 July 1991 Note The second edition of this manual was reformatted in July 1991; no changes were made to the manual’s content at that time. New editions incorporate any updates issued since the previous edition. Copyright All rights reserved. No part of this document may be reproduced in any form, including photocopying or translation to another language, without the prior written consent of Tandem Computers Incorporated. Copyright 1991 Tandem Computers Incorporated. Contents What This Book Is About xvii Who Should Use This Book xvii How to Use This Book xvii Where to Go for More Information xix What’s New in This Update xx Section 1 Introduction to TEDIT What Is PS TEXT EDIT? 1-1 TEDIT Features 1-1 TEDIT Commands 1-2 Using TEDIT Commands 1-3 Terminals and TEDIT 1-3 Starting TEDIT 1-4 Section 2 TEDIT Topics Overview 2-1 Understanding Syntax 2-2 Note About the Examples in This Book 2-3 BALANCED-EXPRESSION 2-5 CHARACTER 2-9 058059 Tandem Computers -

ANSWERS ΤΟ EVEN-Numbered
8 Answers to Even-numbered Exercises 2.1. WhatExplain the following unexpected are result: two ways you can execute a shell script when you do not have execute permission for the file containing the script? Can you execute a shell script if you do not have read permission for the file containing the script? You can give the name of the file containing the script as an argument to the shell (for example, bash scriptfile or tcsh scriptfile, where scriptfile is the name of the file containing the script). Under bash you can give the following command: $ . scriptfile Under both bash and tcsh you can use this command: $ source scriptfile Because the shell must read the commands from the file containing a shell script before it can execute the commands, you must have read permission for the file to execute a shell script. 4.3. AssumeWhat is the purpose ble? you have made the following assignment: $ person=zach Give the output of each of the following commands. a. echo $person zach b. echo '$person' $person c. echo "$person" zach 1 2 6.5. Assumengs. the /home/zach/grants/biblios and /home/zach/biblios directories exist. Specify Zach’s working directory after he executes each sequence of commands. Explain what happens in each case. a. $ pwd /home/zach/grants $ CDPATH=$(pwd) $ cd $ cd biblios After executing the preceding commands, Zach’s working directory is /home/zach/grants/biblios. When CDPATH is set and the working directory is not specified in CDPATH, cd searches the working directory only after it searches the directories specified by CDPATH. -

Unix for Newbies from Duane A
Content borrowed and updated (with permission) Unix for Newbies from Duane A. Bailey’s guidelines from 2007. Getting help on unix: Some Tips To Make Your UNIX Life More Reasonable man <command-name>!!Get full description of command man -k <keyword>!! ! List command mentioning keyword in title 0. Walk away from the machine. If you’re not making progress, don’t waste time banging your head (literally or Logging in and out of a system: figuratively) against the machine. Save your files, print the buggy output, or logout!!!!Terminate session create a backup and walk away. Find someone to talk to about something else. Your exit!!!!Terminate current “shell” mind will work on the problem while you go get a snack and take a break. ssh <username>@<remote host>!Login securely as username to remote host 1. Read man pages. File Manipulation: Realize that you don’t know everything. Take the time to learn how man pages are emacs <file>!!!Edit a text file (See the emacs cheatsheet) structured and what they can teach you. You find answers to many questions on the mv <old> <new>!!!Move or rename <old> file as <new> file internet, but you learn even more by finding and reading the man pages. Better, rm <file(s)>!!!Delete file(s) from filesystem you learn elegant solutions to questions you didn’t think to ask. cp <orig> <duplicate>!!Copy <orig> to file named <duplicate> sftp <remote host>!!Secure batch file transfers between machines 2. Learn the emacs keystrokes. scp host:<orig> host:<dub>!Securely transfer files between machines It will save you time when you work on a machine whose mouse or arrow keys aren’t cat <file>!!!Display or catenate file contents to screen working, and the keystrokes often work in other editors. -

Functional C
Functional C Pieter Hartel Henk Muller January 3, 1999 i Functional C Pieter Hartel Henk Muller University of Southampton University of Bristol Revision: 6.7 ii To Marijke Pieter To my family and other sources of inspiration Henk Revision: 6.7 c 1995,1996 Pieter Hartel & Henk Muller, all rights reserved. Preface The Computer Science Departments of many universities teach a functional lan- guage as the first programming language. Using a functional language with its high level of abstraction helps to emphasize the principles of programming. Func- tional programming is only one of the paradigms with which a student should be acquainted. Imperative, Concurrent, Object-Oriented, and Logic programming are also important. Depending on the problem to be solved, one of the paradigms will be chosen as the most natural paradigm for that problem. This book is the course material to teach a second paradigm: imperative pro- gramming, using C as the programming language. The book has been written so that it builds on the knowledge that the students have acquired during their first course on functional programming, using SML. The prerequisite of this book is that the principles of programming are already understood; this book does not specifically aim to teach `problem solving' or `programming'. This book aims to: ¡ Familiarise the reader with imperative programming as another way of imple- menting programs. The aim is to preserve the programming style, that is, the programmer thinks functionally while implementing an imperative pro- gram. ¡ Provide understanding of the differences between functional and imperative pro- gramming. Functional programming is a high level activity. -
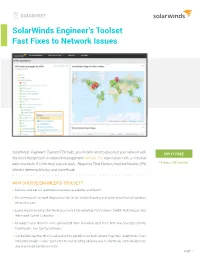
Solarwinds Engineer's Toolset Fast Fixes to Network Issues
DATASHEET SolarWinds Engineer’s Toolset Fast Fixes to Network Issues SolarWinds® Engineer’s Toolset (ETS) helps you monitor and troubleshoot your network with TRY IT FREE the most trusted tools in network management. Version 11.0 now comes with an intuitive web console for 5 of the most popular tools - Response Time Monitor, Interface Monitor, CPU 14 days, full version Monitor, Memory Monitor, and TraceRoute. WHY CHOOSE ENGINEER’S TOOLSET? » Monitor and alert in real time on network availability and health. » Perform robust network diagnostics for faster troubleshooting and quick resolution of complex network issues. » Easily deploy an array of network discovery tools including Port Scanner, Switch Port Mapper, and Advanced Subnet Calculator. » Manage Cisco® devices with specialized tools including Real-time NetFlow Analyzer, Config Downloader, and Config Compare. » Cut troubleshooting time in half and put frequently used tools at your fingertips. SolarWinds Orion integration makes easier and faster troubleshooting allowing you to start tools contextually from any monitored element in Orion. page 1 DATASHEET: SOLARWINDS ENGINEER’S TOOLSET INTUITIVE WEB INTERFACE Response Time Monitor Web access for Response Time Monitor allows you to monitor availability of multiple devices TRY IT FREE in real time and obtain latency and availability information in tabular form. 14 days, full version Memory Monitor Web-based Memory Monitor allows you to monitor memory utilization in real time and enables you to view current memory utilization alongside the total memory available. CPU Monitor Monitor CPU load for multiple devices in real time and set warning and alarm thresholds for each device independently. Interface Monitor The Interface Monitor allows you to view real-time interface statistics for routers and switches simultaneously.