App Server Focus:Best Practices for Writing EJB
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Oracle Database Licensing Information, 11G Release 2 (11.2) E10594-26
Oracle® Database Licensing Information 11g Release 2 (11.2) E10594-26 July 2012 Oracle Database Licensing Information, 11g Release 2 (11.2) E10594-26 Copyright © 2004, 2012, Oracle and/or its affiliates. All rights reserved. Contributor: Manmeet Ahluwalia, Penny Avril, Charlie Berger, Michelle Bird, Carolyn Bruse, Rich Buchheim, Sandra Cheevers, Leo Cloutier, Bud Endress, Prabhaker Gongloor, Kevin Jernigan, Anil Khilani, Mughees Minhas, Trish McGonigle, Dennis MacNeil, Paul Narth, Anu Natarajan, Paul Needham, Martin Pena, Jill Robinson, Mark Townsend This software and related documentation are provided under a license agreement containing restrictions on use and disclosure and are protected by intellectual property laws. Except as expressly permitted in your license agreement or allowed by law, you may not use, copy, reproduce, translate, broadcast, modify, license, transmit, distribute, exhibit, perform, publish, or display any part, in any form, or by any means. Reverse engineering, disassembly, or decompilation of this software, unless required by law for interoperability, is prohibited. The information contained herein is subject to change without notice and is not warranted to be error-free. If you find any errors, please report them to us in writing. If this is software or related documentation that is delivered to the U.S. Government or anyone licensing it on behalf of the U.S. Government, the following notice is applicable: U.S. GOVERNMENT END USERS: Oracle programs, including any operating system, integrated software, any programs installed on the hardware, and/or documentation, delivered to U.S. Government end users are "commercial computer software" pursuant to the applicable Federal Acquisition Regulation and agency-specific supplemental regulations. -

Third-Party License Acknowledgments
Symantec Privileged Access Manager Third-Party License Acknowledgments Version 3.4.3 Symantec Privileged Access Manager Third-Party License Acknowledgments Broadcom, the pulse logo, Connecting everything, and Symantec are among the trademarks of Broadcom. Copyright © 2021 Broadcom. All Rights Reserved. The term “Broadcom” refers to Broadcom Inc. and/or its subsidiaries. For more information, please visit www.broadcom.com. Broadcom reserves the right to make changes without further notice to any products or data herein to improve reliability, function, or design. Information furnished by Broadcom is believed to be accurate and reliable. However, Broadcom does not assume any liability arising out of the application or use of this information, nor the application or use of any product or circuit described herein, neither does it convey any license under its patent rights nor the rights of others. 2 Symantec Privileged Access Manager Third-Party License Acknowledgments Contents Activation 1.1.1 ..................................................................................................................................... 7 Adal4j 1.1.2 ............................................................................................................................................ 7 AdoptOpenJDK 1.8.0_282-b08 ............................................................................................................ 7 Aespipe 2.4e aespipe ........................................................................................................................ -
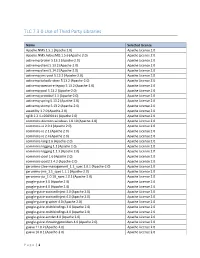
TLC 7.3.0 Use of Third Party Libraries
TLC 7.3.0 Use of Third Party Libraries Name Selected License Apache.NMS 1.5.1 (Apache 2.0) Apache License 2.0 Apache.NMS.ActiveMQ 1.5.6 (Apache 2.0) Apache License 2.0 activemq-broker 5.13.2 (Apache-2.0) Apache License 2.0 activemq-client 5.13.2 (Apache-2.0) Apache License 2.0 activemq-client 5.14.2 (Apache-2.0) Apache License 2.0 activemq-jms-pool 5.13.2 (Apache-2.0) Apache License 2.0 activemq-kahadb-store 5.13.2 (Apache-2.0) Apache License 2.0 activemq-openwire-legacy 5.13.2 (Apache-2.0) Apache License 2.0 activemq-pool 5.13.2 (Apache-2.0) Apache License 2.0 activemq-protobuf 1.1 (Apache-2.0) Apache License 2.0 activemq-spring 5.13.2 (Apache-2.0) Apache License 2.0 activemq-stomp 5.13.2 (Apache-2.0) Apache License 2.0 awaitility 1.7.0 (Apache-2.0) Apache License 2.0 cglib 2.2.1-v20090111 (Apache 2.0) Apache License 2.0 commons-daemon-windows 1.0.10 (Apache-2.0) Apache License 2.0 commons-io 2.0.1 (Apache 2.0) Apache License 2.0 commons-io 2.1 (Apache 2.0) Apache License 2.0 commons-io 2.4 (Apache 2.0) Apache License 2.0 commons-lang 2.6 (Apache-2.0) Apache License 2.0 commons-logging 1.1 (Apache 2.0) Apache License 2.0 commons-logging 1.1.3 (Apache 2.0) Apache License 2.0 commons-pool 1.6 (Apache 2.0) Apache License 2.0 commons-pool2 2.4.2 (Apache-2.0) Apache License 2.0 geronimo-j2ee-management_1.1_spec 1.0.1 (Apache-2.0) Apache License 2.0 geronimo-jms_1.1_spec 1.1.1 (Apache-2.0) Apache License 2.0 geronimo-jta_1.0.1B_spec 1.0.1 (Apache-2.0) Apache License 2.0 google-guice 3.0 (Apache 2.0) Apache License 2.0 google-guice 4.0 (Apache -

MARIMBA PROMOTES SIMON WYNN to CHIEF TECHNOLOGY OFFICER Submitted By: Axicom Monday, 30 April 2001
MARIMBA PROMOTES SIMON WYNN TO CHIEF TECHNOLOGY OFFICER Submitted by: AxiCom Monday, 30 April 2001 Arthur van Hoff to Head Newly-Formed Marimba Advanced Development Laboratory to Promote Technology Innovation Marimba, Inc, a leading provider of systems management solutions built for e-business, today announced the appointment of Simon Wynn to the post of chief technology officer (CTO), reporting directly to Marimba president and CEO, John Olsen. Mr. Wynn assumes the position from Arthur van Hoff, a co-founder of Marimba. Van Hoff, along with senior engineers and fellow co-founders, Sami Shaio and Jonathan Payne, will be part of Marimba's newly-formed Advanced Development Laboratory, and van Hoff will continue to report directly to Olsen. This distinguished team of engineers will focus on technology innovation designed to bring new, leading-edge products to market quickly. Van Hoff, Shaio and Payne are well known as original members of the Sun Microsystems Java team. As CTO, Wynn will be responsible for all technical aspects of Marimba's product vision, including software development, product deployment, strategic planning, new business opportunity assessment, as well as industry standards. "I am pleased to announce the promotion of Simon Wynn to the position of CTO, and we welcome him as a member of our executive team," said Olsen. "This appointment acknowledges Simon's past contributions and reflects his leadership role within the company. Simon has been instrumental in helping to secure Marimba's leadership position in the systems management market." Wynn previously held consecutive positions of director of engineering, engineering manager, and staff software engineer. -

Eeeeett., '1 H-{6'~-H~-4Ttf1ete
~eeeeett., '1 H-{6'~-H~-4ttf1ete ommission Delegation European C ~~;;~ street, NW ~ JANVIER 199 7 '1W&Shin.gton, DO 2 Message de Monsieur E. BRACKENIERS . 3 COMMUNICATIONS . 5 STB INFO ................................................ 7 INFORMATIONS DU CENTRE DE CALCUL ....................... 18 ARTICLES . Translation Centre for the bodies of the European Union ............... 21 . La signature électronique . 22 . SNet - les fondations ........................................ 26 . INTRANET- Application architectures ............................ 27 . INTRANET - Application development tools ........................ 35 . Migration "Nouvelle plate-forme technologique" en site pilote à la DI ...... 44 . D'autres questions/réponses sur le projet 11Next Technological Platform" ..... 46 . New information technologies applied to statistics .................... 49 . SDTvista - vos originaux, nos traductions, des références intéressantes ...... 52 . Chaîne des SIC Outils logistiques ................................ 57· ORGANISATION ........................................... 61 TABLEAUX DE BORD . Budget informatique . 64 . Ressources humaines . 65 . Projets d'infrastructure ....................................... 67 . Formation ................................................ 68 LISTE DES PRODUITS ....................................... 72 COMITES 1 GROUPES DE TRAVAIL ............................ 91 -' CALENDRIER ............................................. 92 ~,---------------------------------------------------------~ lj C.E. 1 Direction Informatique -

Open Source Used in Cisco UCS Director 5.5
Open Source Used In Cisco UCS Director 5.5 Cisco Systems, Inc. www.cisco.com Cisco has more than 200 offices worldwide. Addresses, phone numbers, and fax numbers are listed on the Cisco website at www.cisco.com/go/offices. Text Part Number: 78EE117C99-116574787 Open Source Used In Cisco UCS Director 5.5 1 This document contains licenses and notices for open source software used in this product. With respect to the free/open source software listed in this document, if you have any questions or wish to receive a copy of any source code to which you may be entitled under the applicable free/open source license(s) (such as the GNU Lesser/General Public License), please contact us at [email protected]. In your requests please include the following reference number 78EE117C99-116574787 The product also uses the Linux operating system, Centos Full 6.7. Information on this distribution is available at http://vault.centos.org/6.7/os/Source/SPackages/. The full source code for this distribution, including copyright and license information, is available on request from [email protected]. Mention that you would like the Linux distribution source archive, and quote the following reference number for this distribution: 118610896-116574787. Contents 1.1 activemq-all 5.2.0 1.1.1 Available under license 1.2 Amazon AWS Java SDK 1.1.1 1.2.1 Available under license 1.3 ant 1.9.3 :2build1 1.3.1 Available under license 1.4 aopalliance version 1.0 repackaged as a module 2.3.0-b10 1.4.1 Available under license 1.5 Apache -

Class and Objects in C++ 193–278
OBJECT-ORIENTED PROGRAMMING C++ SIMPLIFIED OBJECT-ORIENTEDOBJECT-ORIENTED PROGRAMMINGPROGRAMMING C++C++ SIMPLIFIEDSIMPLIFIED By HARI MOHAN PANDEY Assistant Professor Computer Engineering Department NMIMS University Mumbai (Maharashtra) UNIVERSITY SCIENCE PRESS !N)MPRINTOF,AXMI0UBLICATIONS0VT,TD "E.'!,U2U ∑ #(%..!)∑ #/#(). ∑ '57!(!4) ∑ (9$%2!"!$ *!,!.$(!2∑ +/,+!4! ∑ ,5#+./7 ∑ -5-"!) ∑ 2!.#() ∑ NEW DELHI ).$)! 53! '(!.!∑ +%.9! OBJECT-ORIENTED PROGRAMMING C++ SIMPLIFIED © by Laxmi Publications (P) Ltd. All rights reserved including those of translation into other languages. In accordance with the Copyright (Amendment) Act, 2012, no part of this publication may be reproduced, stored in a retrieval system, or transmitted in any form or by any means, electronic, mechanical, photocopying, recording or otherwise. Any such act or scanning, uploading, and or electronic sharing of any part of this book without the permission of the publisher constitutes unlawful piracy and theft of the copyright holder’s intellectual property. If you would like to use material from the book (other than for review purposes), prior written permission must be obtained from the publishers. Typeset at ABRO Enterprises, Delhi First Edition: 2015 ISBN 978-93-81159-50-7 Limits of Liability/Disclaimer of Warranty: The publisher and the author make no representation or warranties with respect to the accuracy or completeness of the contents of this work and specifically disclaim all warranties. The advice, strategies, and activities contained herein may not be suitable for every situation. In performing activities adult supervision must be sought. Likewise, common sense and care are essential to the conduct of any and all activities, whether described in this book or otherwise. Neither the publisher nor the author shall be liable or assumes any responsibility for any injuries or damages arising herefrom. -

Internal and External Mechanisms for Extending Programming Languages
Internal and External Mechanisms for Extending Programming Languages Keren Lenz Technion - Computer Science Department - Ph.D. Thesis PHD-2013-03 - 2013 Technion - Computer Science Department - Ph.D. Thesis PHD-2013-03 - 2013 Internal and External Mechanisms for Extending Programming Languages Research Thesis Submitted in partial fulfillment of the requirements for the degree of Doctor of Philosophy Keren Lenz Submitted to the Senate of the Technion — Israel Institute of Technology Kislev 5773 Haifa November 2012 Technion - Computer Science Department - Ph.D. Thesis PHD-2013-03 - 2013 Technion - Computer Science Department - Ph.D. Thesis PHD-2013-03 - 2013 The research thesis was done under the supervision of Prof. Joseph (Yossi) Gil in the Computer Science Department. First and foremost, I would like to express my gratitude to my advisor, Prof. Yossi Gil. He has patiently guided me in my journey as a new researcher, providing me with valuable insights and practical guidance, as well as encouragement. I would like to thank my parents, Hava and Avishay Golz, for years of dedica- tion and devotion and mainly for bestowing me with education as a key principle since early age. Special thanks go to my brother, Omer, for his incredible support and help in parts of this research. Finally, I am indebted to my beloved husband Oron, for standing beside me every step of the way; and to my Children, Amit, Roy and Ido, for making me happy. The generous financial support of the Technion, the Harbor fund, and IBM’s PhD Fellowship program is gratefully acknowledged. Technion - Computer Science Department - Ph.D. Thesis PHD-2013-03 - 2013 Technion - Computer Science Department - Ph.D. -

What Is Javamail?
WHAT IS JAVAMAIL? TM The World’s Leading Java Resource Java COM Volume:4 Issue:10, October1999 Guaranteed Lowest Prices... From the Editor Holy Wars by Sean Rhody pg. 5 Guest Editorial Presenting Java by Ajit Sagar pg. 7 Straight Talking What an ‘L’ of a Month by Alan Williamson pg. 14 Feature: Ian Moraes E-Java JavaMail Palming Java Framework for developing by Ajit Sagar pg. 28 Internet-based e-mail client applications 8 EJB Home Cover Story: Creating Newsfeeds Using Java Applets John Keogh The Business Make the Internet more relevant, and give Advantage of EJB by Jason Westra pg. 58 your customers better—faster—service 18 CORBA Corner Feature: What Is JavaMail? Rachel Gollub What’s Coming By now you might be asking yourself... 32 in CORBA 3? by Jon Siegel pg. 68 Case History: Enterprise Java at Syracuse University Frank Gates IMHO Distributed applications written in Java using the SIS EJB SIS HTML Web EJB Interface Student Browser Application Interface Server Information Server Calls H Server Manager System T t M le SIS Java OOP Means L or App Interface EJB model to build reliable and scalable systems Server 44 J SIS DB C C Interface alls Server Database OODBMS—Not SIS Server Interface Server by Bruce Scott pg. 94 Widget Factory: A Return to Reflection Jim Crafton RETAILERS PLEASE DISPLAY UNTIL DECEMBER 31, 1999 Adding advanced features to the CodeDocument class à la Borland’s CodeInsight 50 SYS-CON Radio: JavaOne Interviews with Grant Wood & Daniel Berg, and Martin Hardee 64 Product Review: SQL 2000 v7.5 Jim Milbery SYS -CON Pervasive -

Reassessing Client/Server Tools and Technologies Lawrence K
Previous 4-04-40 Reassessing Client/Server Tools and Technologies Lawrence K. Cooper John S. Whetstone Payoff Client/server computing has not yet realized its promise of faster applications development, reduced maintenance costs, and enterprise scalability. This article's review of client/server technologies from the perspective of whether they cause developers to focus more on the tool than on the business problem helps IS and business managers appreciate what each technology can and cannot do. Understanding that client/server computing is more a concept than a technology is key to the proper evaluation of the tools and strategies flooding the marketplace. Introduction During the past 10 years, client/server architecture and technologies have been hailed as spelling the demise of the mainframe-centric view of computing. Corporations purchased PC by the truckload and bought myriad development tools, languages, and frameworks for developers and users alike. Products with descriptions such as GUI-builders, front ends, gateways, back ends, middleware, and glue flooded the client/server marketplace. Applications were supposed to be able to be developed faster and maintenance costs were supposed to decrease. Clearly this has not been the case: Client/server computing has proven to be both a boon and a bust. Although it provides more flexibility, it requires more computing resources, faster networks, and higher maintenance. According to a recent Gartner study, client/server computing costs often exceed mainframe-centric computing by up to 70%. Client/server computing also poses an abundance of data security problems. Current technologies are at a middle stage between the rigorous structures of mainframes and the total openness implicit in many of the new architectures. -

Java Bytecode to Native Code Translation: the Caffeine Prototype and Preliminary Results
Java Bytecode to Native Code Translation: The Caffeine Prototype and Preliminary Results Cheng-Hsueh A. Hsieh John C. Gyllenhaal Wen-mei W. Hwu Center for Reliable and High-Performance Computing University of Illinois Urbana-Champaign, IL 61801 ada, gyllen, [email protected] Abstract exists behind efforts to create such a software distribution language. The progress, however, has been very slow due to The Java bytecode language is emerging as a software legal and technical difficulties. distribution standard. With major vendors committed to On the legal side, many software vendors have been porting the Java run-time environment to their platforms, skeptical about the ability of the proposed software distribution programs in Java bytecode are expected to run without languages to protect their intellectual property. In practice, modification on multiple platforms. These first generation run- such concern may have to be addressed empirically after a time environments rely on an interpreter to bridge the gap standard emerges. Although the protection of intellectual between the bytecode instructions and the native hardware. property in software distribution languages is an intriguing This interpreter approach is sufficient for specialized issue, it is not the topic addressed by this paper. For the applications such as Internet browsers where application purpose of our work, we expect Java to be accepted by a performance is often limited by network delays rather than sufficient number of software vendors in the near future to processor speed. It is, however, not sufficient for executing make our work relevant. general applications distributed in Java bytecode. This paper On the technical side, the performance of programs presents our initial prototyping experience with Caffeine, an distributed in a universal software distribution language has optimizing translator from Java bytecode to native machine been a major concern. -

Dr. Douglas Craig Schmidt
Dr. Douglas Craig Schmidt Cornelius Vanderbilt Professor of Engineering [email protected] Department of Electrical Engineering & Computer Science (TEL) 615-294-9573 Vanderbilt University (FAX) 615-343-7440 Nashville, TN 37203 (WEB) www.dre.vanderbilt.edu/∼schmidt/ Educational Background • Ph.D. Computer Science, summer 1994, University of California, Irvine Dissertation: \An Object-Oriented Framework for Experimenting with Alternative Process Archi- tectures for Parallelizing Communication Subsystems." Co-advisors: Dr. Tatsuya Suda and Dr. Richard W. Selby. • M.S. Computer Science, summer 1990, University of California, Irvine, specializing in software engineering. • M.A. Sociology, summer 1986, College of William and Mary, Williamsburg, Virginia Thesis: \A Statistical Analysis of University Resource Allocation Policies." Advisor: Dr. Michael A. Faia. • B.A. Sociology, summer 1984, College of William and Mary, Williamsburg, Virginia. Professional Experience 1. 7/1/18 { present: Associate Provost of Research Development and Technologies Develop cohesive and sustainable information technology (IT) services to advance research and scholarship across Vanderbilt's ten schools and colleges; develop scalable storage and processing solutions by leveraging on-campus and cloud data storage services, as well as creating big data research cores and core-related services; and implement NIST 800-171 compliant IT services. 2. 8/1/18 { present: Co-Director of the Vanderbilt Data Science Institute Facilitate highly innovative research and education initiatives that build on Vanderbilt University's current strengths, promote new collaborations, and establish a cohesive institutional framework that embraces Vanderbilt's diverse campus, while establishing the university as a leader in data science research and education. 3. 2/17 { present: Cornelius Vanderbilt Professor of Engineering Received an endowed chair in recognition of my scholarship, intellect, and leadership in the field of computer science and computer engineering.