Flex Integration with J2EE
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Ioc Containers in Spring
301AA - Advanced Programming Lecturer: Andrea Corradini [email protected] http://pages.di.unipi.it/corradini/ AP-2018-11: Frameworks and Inversion of Control Frameworks and Inversion of Control • Recap: JavaBeans as Components • Frameworks, Component Frameworks and their features • Frameworks vs IDEs • Inversion of Control and Containers • Frameworks vs Libraries • Decoupling Components • Dependency Injection • IoC Containers in Spring 2 Components: a recap A software component is a unit of composition with contractually specified interfaces and explicit context dependencies only. A software component can be deployed independently and is subject to composition by third party. Clemens Szyperski, ECOOP 1996 • Examples: Java Beans, CLR Assemblies • Contractually specified interfaces: events, methods and properties • Explicit context dependencies: serializable, constructor with no argument • Subject to composition: connection to other beans – Using connection oriented programming (event source and listeners/delegates) 3 Towards Component Frameworks • Software Framework: A collection of common code providing generic functionality that can be selectively overridden or specialized by user code providing specific functionality • Application Framework: A software framework used to implement the standard structure of an application for a specific development environment. • Examples: – GUI Frameworks – Web Frameworks – Concurrency Frameworks 4 Examples of Frameworks Web Application Frameworks GUI Toolkits 5 Examples: General Software Frameworks – .NET – Windows platform. Provides language interoperability – Android SDK – Supports development of apps in Java (but does not use a JVM!) – Cocoa – Apple’s native OO API for macOS. Includes C standard library and the Objective-C runtime. – Eclipse – Cross-platform, easily extensible IDE with plugins 6 Examples: GUI Frameworks • Frameworks for Application with GUI – MFC - Microsoft Foundation Class Library. -

Design Pattern Interview Questions
DDEESSIIGGNN PPAATTTTEERRNN -- IINNTTEERRVVIIEEWW QQUUEESSTTIIOONNSS http://www.tutorialspoint.com/design_pattern/design_pattern_interview_questions.htm Copyright © tutorialspoint.com Dear readers, these Design Pattern Interview Questions have been designed specially to get you acquainted with the nature of questions you may encounter during your interview for the subject of Design Pattern. As per my experience good interviewers hardly plan to ask any particular question during your interview, normally questions start with some basic concept of the subject and later they continue based on further discussion and what you answer: What are Design Patterns? Design patterns represent the best practices used by experienced object-oriented software developers. Design patterns are solutions to general problems that software developers faced during software development. These solutions were obtained by trial and error by numerous software developers over quite a substantial period of time. What is Gang of Four GOF? In 1994, four authors Erich Gamma, Richard Helm, Ralph Johnson and John Vlissides published a book titled Design Patterns - Elements of Reusable Object-Oriented Software which initiated the concept of Design Pattern in Software development. These authors are collectively known as Gang of Four GOF. Name types of Design Patterns? Design patterns can be classified in three categories: Creational, Structural and Behavioral patterns. Creational Patterns - These design patterns provide a way to create objects while hiding the creation logic, rather than instantiating objects directly using new opreator. This gives program more flexibility in deciding which objects need to be created for a given use case. Structural Patterns - These design patterns concern class and object composition. Concept of inheritance is used to compose interfaces and define ways to compose objects to obtain new functionalities. -

Design Pattern
Sitesbay.com A Perfect Place for All Tutorials Resources Java Projects | C | C++ | DS | Interview Questions | JavaScript Core Java | Servlet | JSP | JDBC | Struts | Hibernate | Spring | Java Projects | C | C++ | DS | Interview Questions | Html | CSS | Html5 | JavaScript | Ajax | Angularjs | Basic Programs | C Project | Java Project | Interview Tips | Forums | Java Discussions www.sitesbay.com DESIGN PATTERN By SEKHAR SIR [Thursday, May 29, 2014] Recursive Problem:- If some problem occurs again and again in a particular context then we call it as a Recursive Problem. For example, if an audio player having support with MP2 files gets problem for MP3 files and having support for MP3 gets problem MP4. So it is a recursive problem. In a software application, for example a recursive problem will be transferring the data across layers. Q. Why Design Patterns? Ans:- Design patterns are used for solving recursive problems in a software application design. A design pattern is a description for how to solve a recursive problem. Design patterns are not a technology or a tool or a language or a platform or a framework. Design patterns are effective proven solutions for recursive problems. Q. How many Design Patterns? Ans:- Actually, there is no fixed count of no of design patterns because design patterns is not a package and not in the form of classes. SUN Microsystems constituted a group with four professional with the name of Gang of Four (GOF) to find effective solutions for the recursive problems. According to GOF, they found 23 design patterns as effective solutions for re-occurring problems. GOF divided java design patterns into 4 categories (a) Creational Design Patterns:- (1) Singleton Pattern. -

Dependency Injection with Unity
D EPEN DEPENDENCY INJECTION WITH UNITY Over the years software systems have evolutionarily become more and more patterns & practices D ENCY complex. One of the techniques for dealing with this inherent complexity Proven practices for predictable results of software systems is dependency injection – a design pattern that I allows the removal of hard-coded dependencies and makes it possible to Save time and reduce risk on your NJECT assemble a service by changing dependencies easily, whether at run-time software development projects by or compile-time. It promotes code reuse and loosely-coupled design which incorporating patterns & practices, I leads to more easily maintainable and flexible code. Microsoft’s applied engineering ON guidance that includes both production The guide you are holding in your hands is a primer on using dependency quality source code and documentation. W I injection with Unity – a lightweight extensible dependency injection TH DEPENDENCY INJECTION container built by the Microsoft patterns & practices team. It covers The guidance is designed to help U software development teams: various styles of dependency injection and also additional capabilities N I of Unity container, such as object lifetime management, interception, Make critical design and technology TY and registration by convention. It also discusses the advanced topics of selection decisions by highlighting WITH UNITY enhancing Unity with your custom extensions. the appropriate solution architectures, technologies, and Microsoft products The guide contains plenty of trade-off discussions and tips and tricks for for common scenarios managing your application cross-cutting concerns and making the most out of both dependency injection and Unity. These are accompanied by a Understand the most important Dominic Betts real world example that will help you master the techniques. -

Designpatternsphp Documentation Release 1.0
DesignPatternsPHP Documentation Release 1.0 Dominik Liebler and contributors Jul 18, 2021 Contents 1 Patterns 3 1.1 Creational................................................3 1.1.1 Abstract Factory........................................3 1.1.2 Builder.............................................8 1.1.3 Factory Method......................................... 13 1.1.4 Pool............................................... 18 1.1.5 Prototype............................................ 21 1.1.6 Simple Factory......................................... 24 1.1.7 Singleton............................................ 26 1.1.8 Static Factory.......................................... 28 1.2 Structural................................................. 30 1.2.1 Adapter / Wrapper....................................... 31 1.2.2 Bridge.............................................. 35 1.2.3 Composite............................................ 39 1.2.4 Data Mapper.......................................... 42 1.2.5 Decorator............................................ 46 1.2.6 Dependency Injection...................................... 50 1.2.7 Facade.............................................. 53 1.2.8 Fluent Interface......................................... 56 1.2.9 Flyweight............................................ 59 1.2.10 Proxy.............................................. 62 1.2.11 Registry............................................. 66 1.3 Behavioral................................................ 69 1.3.1 Chain Of Responsibilities................................... -
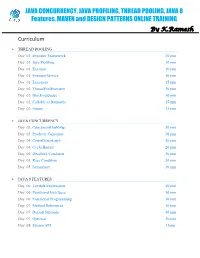
JAVA CONCURRENCY ONLINE TRAINING – Java2aspire
JAVA CONCURRENCY, JAVA PROFILING, THREAD POOLING, JAVA 8 Features, MAVEN and DESIGN PATTERNS ONLINE TRAINING By K.Ramesh Curriculum THREAD POOLING Day 01: Executor Framework 20 min Day 01: Java Profiling 10 min Day 01: Executor 10 min Day 01: ExecutorService 10 min Day 01: Executors 15 min Day 02: ThreadPoolExecutor 20 min Day 02: BlockingQueue 10 min Day 02: Callable vs Runnable 15 min Day 02: Future 15 min JAVA CONCURRENCY Day 03: ConcurrentHashMap 30 min Day 03: Producer Consumer 30 min Day 04: CountDownLatch 20 min Day 04: CyclicBarrier 20 min Day 04: Deadlock Condition 20 min Day 05: Race Condition 30 min Day 05: Semaphore 30 min JAVA 8 FEATURES Day 06: Lambda Expressions 40 min Day 06: Functional Interfaces 10 min Day 06: Functional Programming 10 min Day 07: Method References 10 min Day 07: Default Methods 40 min Day 07: Optional 10 min Day 08: Stream API 1 hour MAVEN Day 09: Project Object Model (POM) 20 min Day 09: Project Description 10 min Day 09: Public Repository 10 min Day 09: Dependency Management 10 min Day 09: Build Configuration 10 min Day 10: Installation 15 min Day 10: Dependency Scope 15 min Day 10: Proprietary Dependencies 15 min Day 10: Project Inheritance 15 min Day 11: Maven life cycle 20 min Day 11: Maven Directory Structure 20 min Day 11: Archetypes 20 min Day 12: Applications 1 hour DESIGN PATTERNS Day 13: Factory Pattern 20 min Day 13: Abstract Factory Pattern 10 min Day 13: Single Pattern 20 min Day 13: Prototype Pattern 10 min Day 14: Composite Pattern 10 min Day 14: Facade Pattern 15 min Day 14: DAO -

POJO in Action.Book
SAMPLE CHAPTER POJOs in Action by Chris Richardson Chapter 1 Copyright 2006 Chris Richardson contents PART 1OVERVIEW OF POJOS AND LIGHTWEIGHT FFFFFFFFFFFFFFFFRAMEWORKS .............................................1 Chapter 1 ■ Developing with POJOs: faster and easier 3 Chapter 2 ■ J2EE design decisions 31 PART 2A SIMPLER, FASTER APPROACH................... 59 Chapter 3 ■ Using the Domain Model pattern 61 Chapter 4 ■ Overview of persisting a domain model 95 Chapter 5 ■ Persisting a domain model with JDO 2.0 149 Chapter 6 ■ Persisting a domain model with Hibernate 3 195 Chapter 7 ■ Encapsulating the business logic with a POJO façade 243 PART 3VARIATIONS ........................................... 287 Chapter 8 ■ Using an exposed domain model 289 Chapter 9 ■ Using the Transaction Script pattern 317 Chapter 10 ■ Implementing POJOs with EJB 3 360 vii viii BRIEF CONTENTS PART 4DEALING WITH DATABASES AND CCCCCCCCCCCCCONCURRENCY .......................................405 Chapter 11 ■ Implementing dynamic paged queries 407 Chapter 12 ■ Database transactions and concurrency 451 Chapter 13 ■ Using offline locking patterns 488 Developing with POJOs: faster and easier This chapter covers ■ Comparing lightweight frameworks and EJBs ■ Simplifying development with POJOs ■ Developing an object-oriented design ■ Making POJOs transactional and persistent 3 4 CHAPTER 1 Developing with POJOs: faster and easier Sometimes you must use a technology for a while in order to appreciate its true value. A few years ago I had to go out of the country on a business trip, and I didn’t want to risk missing episodes of my favorite show. So, rather than continu- ing to struggle with the timer function on my VCR, I bought a TiVo box. At the time I thought it was simply going to be a much more convenient and reliable way to record programs. -

Implementing Domain-Driven Design
www.EBooksWorld.ir Praise for Implementing Domain-Driven Design “With Implementing Domain-Driven Design, Vaughn has made an important con- tribution not only to the literature of the Domain-Driven Design community, but also to the literature of the broader enterprise application architecture field. In key chap- ters on Architecture and Repositories, for example, Vaughn shows how DDD fits with the expanding array of architecture styles and persistence technologies for enterprise applications—including SOA and REST, NoSQL and data grids—that has emerged in the decade since Eric Evans’ seminal book was first published. And, fittingly, Vaughn illuminates the blocking and tackling of DDD—the implementation of entities, value objects, aggregates, services, events, factories, and repositories—with plentiful exam- ples and valuable insights drawn from decades of practical experience. In a word, I would describe this book as thorough. For software developers of all experience levels looking to improve their results, and design and implement domain-driven enterprise applications consistently with the best current state of professional practice, Imple- menting Domain-Driven Design will impart a treasure trove of knowledge hard won within the DDD and enterprise application architecture communities over the last cou- ple decades.” —Randy Stafford, Architect At-Large, Oracle Coherence Product Development “Domain-Driven Design is a powerful set of thinking tools that can have a profound impact on how effective a team can be at building software-intensive systems. The thing is that many developers got lost at times when applying these thinking tools and really needed more concrete guidance. In this book, Vaughn provides the missing links between theory and practice. -

Semantic Description of Services and Service Factories for Ambient Intelligence Rémi Emonet
Semantic Description of Services and Service Factories for Ambient Intelligence Rémi Emonet To cite this version: Rémi Emonet. Semantic Description of Services and Service Factories for Ambient Intelligence. Soft- ware Engineering [cs.SE]. Institut National Polytechnique de Grenoble - INPG, 2009. English. tel- 00450479 HAL Id: tel-00450479 https://tel.archives-ouvertes.fr/tel-00450479 Submitted on 26 Jan 2010 HAL is a multi-disciplinary open access L’archive ouverte pluridisciplinaire HAL, est archive for the deposit and dissemination of sci- destinée au dépôt et à la diffusion de documents entific research documents, whether they are pub- scientifiques de niveau recherche, publiés ou non, lished or not. The documents may come from émanant des établissements d’enseignement et de teaching and research institutions in France or recherche français ou étrangers, des laboratoires abroad, or from public or private research centers. publics ou privés. GRENOBLE INP n◦ attribu´epar la biblioth`eque THESE` pour obtenir le grade de ❉♦❝❡✉ ❉✉ ●♦✉♣❡ ●❡♥♦❜❧❡ ■◆ Sp´ecialit´e: Informatique pr´epar´eeau Laboratoire d’Informatique de Grenoble dans le cadre de l’Ecole´ Doctorale Math´ematiques, Sciences et Technologies de l’Information, Informatique pr´esent´eeet soutenue publiquement par R´emi ❊♠♦♥❡ le 23 septembre 2009 ❉❡❝✐♣✐♦♥ ❙♠❛♥✐✉❡ ❞❡ ❙❡✈✐❝❡ ❡ ❞✬❯✐♥❡ à ❙❡✈✐❝❡ ♣♦✉ ❧✬■♥❡❧❧✐❣❡♥❝❡ ❆♠❜✐❛♥❡ ❙❡♠❛♥✐❝ ❉❡❝✐♣✐♦♥ ♦❢ ❙❡✈✐❝❡ ❛♥❞ ❙❡✈✐❝❡ ❋❛❝♦✐❡ ❢♦ ❆♠❜✐❡♥ ■♥❡❧❧✐❣❡♥❝❡ Directeur de th`ese : James L. ❈♦✇❧❡② Co-directeur de th`ese : Dominique ❱❛✉❢❡②❞❛③ JURY Pr. Marie-Christine Rousset Pr´esident Pr. James L. Crowley Directeur de th`ese Dr. Dominique Vaufreydaz Co-directeur de th`ese Pr. Gregory D. Abowd Rapporteur Pr. David Simplot-Ryl Rapporteur Pr. Michel Riveill Examinateur 2 R´esum´e Ce manuscrit ´etudie l’ad´equation des approches `aservices, ainsi que leur am´elioration, pour l’int´egration dynamique et la r´eutilisation logicielle dans le cadre de l’informatique ambiante. -

Sun Certified Enterprise Architect for Java EE Study Guide / Mark Cade, Humphrey Sheil
Many of the designations used by manufacturers and sellers to distinguish their products are claimed as trademarks. Where those designations appear in this book, and the publisher was aware of a trademark claim, the designations have been printed with initial capital letters or in all capitals. Sun Microsystems, Inc. has intellectual property rights relating to implementations of the technology described in this publication. In particular, and without limitation, these intellectual property rights may include one or more U.S. patents, foreign patents, or pending applications. Sun, Sun Microsystems, the Sun logo, J2ME, J2EE, Java Card, and all Sun and Java based trademarks and logos are trademarks or registered trademarks of Sun Microsystems, Inc., in the United States and other countries. UNIX is a registered trademark in the United States and other countries, exclusively licensed through X/Open Company, Ltd. This publication is provided “as is” without warranty of any kind, either express or implied, including, but not limited to, the implied warranties of merchantability, fitness for a particular purpose, or non-infringement. This publication could include technical inaccuracies or typographical errors. Changes are periodically added to the information herein; these changes will be incorporated in new editions of the publication. Sun Microsystems, Inc. may make improvements and/or changes in the product(s) and/or the program(s) described in this publication at any time. The authors and publisher have taken care in the preparation of this book, but make no expressed or implied warranty of any kind and assume no responsibility for errors or omissions. No liability is assumed for incidental or consequential damages in connection with or arising out of the use of the information or programs contained herein. -

J2EE Architecture and Patterns in Enterprise Systems
J2EE Architecture and Patterns in Enterprise Systems Zhiguo Guo University of Tampere Department of Computer and Information Science Master’s Thesis May 2004 i University of Tampere Department of Computer and Information Science Zhiguo Guo: J2EE Architecture and Patterns in Enterprise Systems Master’s Thesis, 60 pages May 2004 The purpose of this thesis is to illustrate an enterprise project named HUVA, in which Java Platform 2, Enterprise Edition (J2EE) architecture and patterns are applied. This study took a constructive research approach: It starts from the application domain including the initial plan and business model, then moves to the system architecture covering the architecturally significant requirements and the system structure compliant with J2EE architecture, finally ends at the application design elaborated by applying the J2EE patterns at a high level. As a result the architectural and application design satisfied the project needs and requirements; and the HUVA software has been implemented in practice according to the design. Keywords: J2EE, architecture, pattern, enterprise system. ii Acknowledgements I would like to thank Professor Roope Raisamo and Professor Isto Aho from the University of Tampere for being my encouraging, patient and responsible supervisors during the master’s thesis project. I would like to thank Mr. Mika Miettinen from Solteq Oyj and Mr. Timo Westkämper for supporting the technical aspects of this thesis. Finally, I would like to use this opportunity to express huge thanks to my dear wife, Chongliang Tang for always being the invaluable person behind my success. Tampere - Finland, June 1st, 2004 Zhiguo Guo iii Contents 1. Introduction.............................................................................................................1 2. Application domain ...............................................................................................3 2.1. -

How to Reduce Costs of Business Logic Maintenance
How to reduce costs of business logic maintenance Tomas Cerny Michael J. Donahoo Department of Computer Science and Engineering Department of Computer Science, Czech Technical University, Baylor University, Charles Square 13, Prague, Czech Republic Waco, TX, USA Email: [email protected] Email: jeff [email protected] Abstract—Three tier enterprise applications introduce multiple patterns has grown to multiple categories and spread from challenges for software engineers. Although we can divide the analyzes over design to coding. application into three tiers, we still need to design properly each Besides multiple patterns simplifying designers decisions tier internally to achieve multiple design qualities. The middle business tier captures logic in which we associate objects, validate another innovative contribution and complement to the OOP business rules, etc. Often multiple cross-cutting concerns are appeared known aspect oriented programming (AOP) [9]. mixed in the services which results in bloated, highly coupled de- AOP that introduces the idea of cross-cutting concerns in sign with very low cohesion. In this paper we present a case study objects. These concerns then spread through multiple architec- that we develop based on our four year experience with enterprise tural layers and cannot be isolated with the sole use of OOP. application that struggled from multiple weak design decisions. We emphasize multiple aspects that should be decoupled from AOP defines the location where multiple concerns cross as the rest of the services which increase service cohesion and results a pointcut. This pointcut as reached by the program can use in better readability, maintenance, testability, reuse and error- an additional code (separately defined) known as an advice avoidance.