Comprehensive Analysis of Dynamic Routing Protocols in Computer Networks Priya Asher Department of Electronics and Telecommunication, K
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

A Comprehensive Study of Routing Protocols Performance with Topological Changes in the Networks Mohsin Masood Mohamed Abuhelala Prof
A comprehensive study of Routing Protocols Performance with Topological Changes in the Networks Mohsin Masood Mohamed Abuhelala Prof. Ivan Glesk Electronics & Electrical Electronics & Electrical Electronics & Electrical Engineering Department Engineering Department Engineering Department University of Strathclyde University of Strathclyde University of Strathclyde Glasgow, Scotland, UK Glasgow, Scotland, UK Glasgow, Scotland, UK mohsin.masood mohamed.abuhelala ivan.glesk @strath.ac.uk @strath.ac.uk @strath.ac.uk ABSTRACT different topologies and compare routing protocols, but no In the modern communication networks, where increasing work has been considered about the changing user demands and advance applications become a functionality of these routing protocols with the topology challenging task for handling user traffic. Routing with real-time network limitations. such as topological protocols have got a significant role not only to route user change, network congestions, and so on. Hence without data across the network but also to reduce congestion with considering the topology with different network scenarios less complexity. Dynamic routing protocols such as one cannot fully understand and make right comparison OSPF, RIP and EIGRP were introduced to handle among any routing protocols. different networks with various traffic environments. Each This paper will give a comprehensive literature review of of these protocols has its own routing process which each routing protocol. Such as how each protocol (OSPF, makes it different and versatile from the other. The paper RIP or EIGRP) does convergence activity with any change will focus on presenting the routing process of each in the network. Two experiments are conducted that are protocol and will compare its performance with the other. -

Configuring Static Routing
Configuring Static Routing This chapter contains the following sections: • Finding Feature Information, on page 1 • Information About Static Routing, on page 1 • Licensing Requirements for Static Routing, on page 4 • Prerequisites for Static Routing, on page 4 • Guidelines and Limitations for Static Routing, on page 4 • Default Settings for Static Routing Parameters, on page 4 • Configuring Static Routing, on page 4 • Verifying the Static Routing Configuration, on page 10 • Related Documents for Static Routing, on page 10 • Feature History for Static Routing, on page 10 Finding Feature Information Your software release might not support all the features documented in this module. For the latest caveats and feature information, see the Bug Search Tool at https://tools.cisco.com/bugsearch/ and the release notes for your software release. To find information about the features documented in this module, and to see a list of the releases in which each feature is supported, see the "New and Changed Information"chapter or the Feature History table in this chapter. Information About Static Routing Routers forward packets using either route information from route table entries that you manually configure or the route information that is calculated using dynamic routing algorithms. Static routes, which define explicit paths between two routers, cannot be automatically updated; you must manually reconfigure static routes when network changes occur. Static routes use less bandwidth than dynamic routes. No CPU cycles are used to calculate and analyze routing updates. You can supplement dynamic routes with static routes where appropriate. You can redistribute static routes into dynamic routing algorithms but you cannot redistribute routing information calculated by dynamic routing algorithms into the static routing table. -

Dynamic Routing: Routing Information Protocol
CS 356: Computer Network Architectures Lecture 12: Dynamic Routing: Routing Information Protocol Chap. 3.3.1, 3.3.2 Xiaowei Yang [email protected] Today • ICMP applications • Dynamic Routing – Routing Information Protocol ICMP applications • Ping – ping www.duke.edu • Traceroute – traceroute nytimes.com • MTU discovery Ping: Echo Request and Reply ICMP ECHO REQUEST Host Host or or Router router ICMP ECHO REPLY Type Code Checksum (= 8 or 0) (=0) identifier sequence number 32-bit sender timestamp Optional data • Pings are handled directly by the kernel • Each Ping is translated into an ICMP Echo Request • The Pinged host responds with an ICMP Echo Reply 4 Traceroute • xwy@linux20$ traceroute -n 18.26.0.1 – traceroute to 18.26.0.1 (18.26.0.1), 30 hops max, 60 byte packets – 1 152.3.141.250 4.968 ms 4.990 ms 5.058 ms – 2 152.3.234.195 1.479 ms 1.549 ms 1.615 ms – 3 152.3.234.196 1.157 ms 1.171 ms 1.238 ms – 4 128.109.70.13 1.905 ms 1.885 ms 1.943 ms – 5 128.109.70.138 4.011 ms 3.993 ms 4.045 ms – 6 128.109.70.102 10.551 ms 10.118 ms 10.079 ms – 7 18.3.3.1 28.715 ms 28.691 ms 28.619 ms – 8 18.168.0.23 27.945 ms 28.028 ms 28.080 ms – 9 18.4.7.65 28.037 ms 27.969 ms 27.966 ms – 10 128.30.0.246 27.941 ms * * Traceroute algorithm • Sends out three UDP packets with TTL=1,2,…,n, destined to a high port • Routers on the path send ICMP Time exceeded message with their IP addresses until n reaches the destination distance • Destination replies with port unreachable ICMP messages Path MTU discovery algorithm • Send packets with DF bit set • If receive an ICMP error message, reduce the packet size Today • ICMP applications • Dynamic Routing – Routing Information Protocol Dynamic Routing • There are two parts related to IP packet handling: 1. -

Routing As a Service
Routing as a Service Karthik Lakshminarayanan Ion Stoica Scott Shenker Jennifer Rexford University of California, Berkeley Princeton University Abstract configuration, making it difficult to offer meaningful service- level agreements (SLAs) to customers or to identify the AS In Internet routing, there is a fundamental tussle between the responsible for end-to-end performance problems. end users who want control over the end-to-end paths and the An ISP's customers, such as end users, enterprise net- Autonomous Systems (ASes) who want control over the flow works, and smaller ISPs, have even less control over the se- of traffic through their infrastructure. To resolve this tussle lection of end-to-end paths. By connecting to more than one and offer flexible routing control across multiple routing do- ISPs, an enterprise can select from multiple paths [2]; how- mains, we argue that customized route computation should ever, the customer controls only the first hop for outbound be offered as a service by third-party providers. Outsourcing traffic and has (at best) crude influence on incoming traffic. specialized route computation allows different path-selection Yet, some customers need more control over the end-to-end mechanisms to coexist, and evolve over time. path, or at least its properties, to satisfy performance and pol- icy goals. For example, a customer might not want his Web 1 Introduction traffic forwarded through an AS that filters packets based on Interdomain routing has long been based on three pillars: their contents. Alternatively, a customer might need to discard traffic from certain sources to block denial-of-service attacks • Local control: ASes have complete control over routing or protect access to a server storing sensitive data. -

Routing Basics
CHAPTER 5 Chapter Goals • Learn the basics of routing protocols. • Learn the differences between link-state and distance vector routing protocols. • Learn about the metrics used by routing protocols to determine path selection. • Learn the basics of how data travels from end stations through intermediate stations and on to the destination end station. • Understand the difference between routed protocols and routing protocols. Routing Basics This chapter introduces the underlying concepts widely used in routing protocols. Topics summarized here include routing protocol components and algorithms. In addition, the role of routing protocols is briefly contrasted with the role of routed or network protocols. Subsequent chapters in Part VII, “Routing Protocols,” address specific routing protocols in more detail, while the network protocols that use routing protocols are discussed in Part VI, “Network Protocols.” What Is Routing? Routing is the act of moving information across an internetwork from a source to a destination. Along the way, at least one intermediate node typically is encountered. Routing is often contrasted with bridging, which might seem to accomplish precisely the same thing to the casual observer. The primary difference between the two is that bridging occurs at Layer 2 (the link layer) of the OSI reference model, whereas routing occurs at Layer 3 (the network layer). This distinction provides routing and bridging with different information to use in the process of moving information from source to destination, so the two functions accomplish their tasks in different ways. The topic of routing has been covered in computer science literature for more than two decades, but routing achieved commercial popularity as late as the mid-1980s. -

Routing Tables
Routing Tables A routing table is a grouping of information stored on a networked computer or network router that includes a list of routes to various network destinations. The data is normally stored in a database table and in more advanced configurations includes performance metrics associated with the routes stored in the table. Additional information stored in the table will include the network topology closest to the router. Although a routing table is routinely updated by network routing protocols, static entries can be made through manual action on the part of a network administrator. How Does a Routing Table Work? Routing tables work similar to how the post office delivers mail. When a network node on the Internet or a local network needs to send information to another node, it first requires a general idea of where to send the information. If the destination node or address is not connected directly to the network node, then the information has to be sent via other network nodes. In order to save resources, most local area network nodes will not maintain a complex routing table. Instead, they will send IP packets of information to a local network gateway. The gateway maintains the primary routing table for the network and will send the data packet to the desired location. In order to maintain a record of how to route information, the gateway will use a routing table that keeps track of the appropriate destination for outgoing data packets. All routing tables maintain routing table lists for the reachable destinations from the router’s location. -

Advanced Routing – Cisco (4 Cr.) Course Description
NVCC COLLEGE-WIDE COURSE CONTENT SUMMARY ITN 250 - Advanced Routing – Cisco (4 cr.) Course Description ITN 250 - Includes instruction focusing on the characteristics of various Routing protocols used in the TCP/IP networking environment, static routing, OSPF, IGRP, EIGRP, IS-IS, BGP, advanced IP addressing, and security. Course content also examines various strategies for optimizing network routing performance. Lecture 4 hours per week. Recommended Pre-requisites Student should: be a Cisco Certified Network Associate (CCNA), or, have successfully completed ITN157 WAN Technologies – Cisco, or have successfully completed TEL251 Internetworking 4, or, have successfully completed CCNA Semester 4 training at a Cisco Network Academy, or, have instructor’s permission. Course Objectives Upon completion of this course, the student will be able to: Selecting and configuring scalable IP addresses Configure the RIP version 2 routing protocol Configure the EIGRP routing protocol Configure Open Shortest Path First protocol in a multi-area environment Configure the IS-IS routing protocol Develop route filtering and policy routing Configure route redistribution Describe the Border Gateway Protocol (BGP) Configure and troubleshoot the BGP routing protocol Course Content Overview of Scalable Internetworks Advanced IP Addressing Management Routing Overview Routing Information Protocol Version 2 EIGRP OSPF IS-IS Route Optimization BGP Student Learning Outcomes Selecting and configuring scalable IP addresses Understand the issues of IP address -

Introduction to Wifi Networking
Introduction to WiFi Networking Marco Zennaro Ermanno Pietrosemoli Goals The goal of this lecture is to introduce: ‣ 802.11 family of radio protocols ‣ 802.11 radio channels ‣ Wireless network topologies ‣ WiFi modes of operation ‣ Strategies for routing network traffic 2 ISM / UNII bands Most commercial wireless devices (mobile phones, television, radio, etc.) use licensed radio frequencies. Large organizations pay licensing fees for the right to use those radio frequencies. WiFi uses unlicensed spectrum. License fees are not usually required to operate WiFi equipment. The Industrial, Scientific and Medical (ISM) bands allow for unlicensed use of 2.4-2.5 GHz, 5.8 GHz, and many other (non-WiFi) frequencies. 3 802.11 family 4 802.11 family 5 Wireless networking protocols The 802.11 family of radio protocols are commonly referred to as WiFi. • 802.11a supports up to 54 Mbps using the 5 GHz unlicensed bands. • 802.11b supports up to 11 Mbps using the 2.4 GHz unlicensed band. • 802.11g supports up to 54 Mbps using the 2.4 GHz unlicensed band. • 802.11n supports up to 600 Mbps using the 2.4 GHz and 5 GHz unlicensed bands. • 802.16 (WiMAX) is not 802.11 WiFi! It is a completely different technology that uses a variety of licensed and unlicensed frequencies. 6 Compatibility of standards AP 802.11a 802.11b 802.11g 802.11n 802.16 Yes C 802.11a Yes @5GHz L Yes Yes 802.11b Yes I (slower) @2.4GHz Yes Yes E 802.11g Yes (slower) @2.4GHz N Yes Yes Yes 802.11n Yes T @5GHz @2.4GHz @2.4GHz 802.16 Yes 7 IEEE 802.11 AC Improved performance by means of: • Two or up to 8 Spatial streams (MIMO) • Higher order modulation types (up to 256 QAM) • Wider Channels bandwidth (up to 160 MHz) 8 IEEE 802.11 AC: MIMO 9 IEEE 802.11 AC, 256 constellation 1 0 Data rates Note that the “data rates” quoted in the WiFi specifications refer to the raw radio symbol rate, not the actual TCP/IP throughput rate. -

Chapter 4 Dynamic Routing
CHAPTER 4 DYNAMIC ROUTING In this chapter we cover the basic principles of dynamic routing algorithms that form the basis of the experiments in Lab 4. The chapter has six sections. Each section covers material that you need to run the lab exercises. The first section gives an overview of dynamic routing protocols and discusses the differences between the two major classes of routing algorithms: intra domain and inter domain. Sections 2, 3, 4, and 5 give an overview of the most common routing algorithms such , RIP, OSPF, BGP and IGRP. Section 6 presents the commands used to configure the hosts and the routers for dynamic routing. TABLE OF CONTENT 1 ROUTING PROTOCOLS ........................................................................................................................ 3 1.1 AUTONOMOUS SYSTEMS (AS)............................................................................................................ 3 1.2 INTRADOMAIN ROUTING VERSUS INTERDOMAIN ROUTING ............................................................... 4 1.3 DYNAMIC ROUTING ............................................................................................................................ 4 1.3.1 Distance Vector Algorithm ........................................................................................................... 4 2 RIP ............................................................................................................................................................... 5 3 OSPF........................................................................................................................................................... -

Reinforcement Learning for Routing in Communication Networks
Reinforcement Learning for Routing in Communication Networks Walter H. Andrag Thesis presented in partial fulfilment of the requirements for the degree of Master of Science at the University of Stellenbosch Supervisor: Prof Christian W. Omlin April 2003 Stellenbosch University http://scholar.sun.ac.za Declaration I, the undersigned, hereby declare that the work contained in this thesis is my own original work and has not previously in its entirety or in part been submitted at any university for a degree. Signature: Date: .~ Stellenbosch University http://scholar.sun.ac.za Abstract Routing policies for packet-switched communication networks must be able to adapt to changing traffic patterns and topologies. We study the feasibility of implementing an adaptive routing policy using the Q-Learning algorithm which learns sequences of actions from delayed rewards. The Q-Routing algorithm adapts a network's routing policy based on local information alone and converges toward an optimal solution. We demonstrate that Q-Routing is a viable alternative to other adaptive routing methods such as Bellman-Ford. We also study variations of Q-Routing designed to better explore possible routes and to take into consideration limited buffer size and optimize multiple objectives. 11 Stellenbosch University http://scholar.sun.ac.za Opsomming Die roetering in kommunikasienetwerke moet kan aanpas by veranderings in netwerk- topologie en verkeersverspreidings. Ons bestudeer die bruikbaarheid van 'n aanpasbare roeteringsalgoritme gebaseer op die "Q-Learning"-algoritme wat dit moontlik maak om 'n reeks besluite te kan neem gebaseer op vertraagde vergoedings. Die roeteringsalgo- ritme gebruik slegs nabygelee inligting om roeteringsbesluite te maak en konvergeer na 'n optimale oplossing. -

RIP: Routing Information Protocol a Routing Protocol Based on the Distance-Vector Algorithm
Laboratory 6 RIP: Routing Information Protocol A Routing Protocol Based on the Distance-Vector Algorithm Objective The objective of this lab is to configure and analyze the performance of the Routing Information Protocol (RIP) model. Overview A router in the network needs to be able to look at a packet’s destination address and then determine which of the output ports is the best choice to get the packet to that address. The router makes this decision by consulting a forwarding table. The fundamental problem of routing is: How do routers acquire the information in their forwarding tables? Routing algorithms are required to build the routing tables and hence forwarding tables. The basic problem of routing is to find the lowest-cost path between any two nodes, where the cost of a path equals the sum of the costs of all the edges that make up the path. Routing is achieved in most practical networks by running routing protocols among the nodes. The protocols provide a distributed, dynamic way to solve the problem of finding the lowest-cost path in the presence of link and node failures and changing edge costs. One of the main classes of routing algorithms is the distance-vector algorithm. Each node constructs a vector containing the distances (costs) to all other nodes and distributes that vector to its immediate neighbors. RIP is the canonical example of a routing protocol built on the distance-vector algorithm. Routers running RIP send their advertisements regularly (e.g., every 30 seconds). A router also sends an update message whenever a triggered update from another router causes it to change its routing table. -
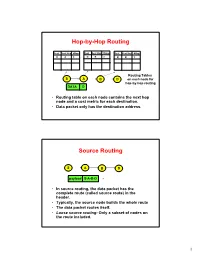
Hop-By-Hop Routing Source Routing
Hop-by-Hop Routing Dest. Next Hop #Hops Dest. Next Hop #Hops Dest. Next Hop #Hops D A 3 D B 2 D D 1 Routing Tables S A B D on each node for hop-by-hop routing DATA D • Routing table on each node contains the next hop node and a cost metric for each destination. • Data packet only has the destination address. Source Routing S A B D payload S-A-B-D • In source routing, the data packet has the complete route (called source route) in the header. • Typically, the source node builds the whole route • The data packet routes itself. • Loose source routing: Only a subset of nodes on the route included. 1 Static vs. Dynamic Routing • Static routing has fixed routes, set up by network administrators, for example. • Dynamic routing is network state- dependent. Routes may change dynamically depending on the “state” of the network. • State = link costs. Switch traffic from highly loaded links to less loaded links. Distributed, Dynamic Routing Protocols • Distributed because in a dynamic network, no single, centralized node “knows” the whole “state” of the network. • Dynamic because routing must respond to “state” changes in the network for efficiency. • Two class of protocols: Link State and Distance Vector. 2 Link State Protocol • Each node “floods” the network with link state packets (LSP) describing the cost of its own (outgoing) links. – Link cost metric = typically delay for traversing the link. – Every other node in the network gets the LSPs via the flooding mechanism. • Each node maintains a LSP database of all LSPs it received.