Recommended Practice for Use and Procedures for Inspection
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Evaluation of Open Source Operating Systems for Safety-Critical Applications Master’S Thesis in Embedded Electronic System Design
Evaluation of open source operating systems for safety-critical applications Master’s thesis in Embedded Electronic System Design Petter Sainio Berntsson Department of Computer Science and Engineering CHALMERS UNIVERSITY OF TECHNOLOGY UNIVERSITY OF GOTHENBURG Gothenburg, Sweden 2017 MASTER’S THESIS 2017 Evaluation of open source operating systems for Safety-critical applications Petter Sainio Berntsson Department of Computer Science and Engineering Chalmers University of Technology University of Gothenburg Gothenburg, Sweden 2017 Evaluation of open source operating systems for safety-critical applications Petter Sainio Berntsson © Petter Sainio Berntsson, 2017 Examiner: Per Larsson-Edefors Chalmers University of Technology Department of Computer Science and Engineering Academic supervisor: Jan Jonsson Chalmers University of Technology Department of Computer Science and Engineering Industrial supervisors: Lars Strandén RISE Research Institutes of Sweden Dependable Systems Fredrik Warg RISE Research Institutes of Sweden Dependable Systems Master’s Thesis 2017 Department of Computer Science and Engineering Chalmers University of Technology University of Gothenburg SE-412 96 Gothenburg Telephone +46(0) 31 772 1000 Abstract Today many embedded applications will have to handle multitasking with real-time time constraints and the solution for handling multitasking is to use a real-time operating system for scheduling and managing the real-time tasks. There are many different open source real-time operating systems available and the use of open source software for safety-critical applications is considered highly interesting by industries such as medical, aerospace and automotive as it enables a shorter time to market and lower development costs. If one would like to use open source software in a safety-critical context one would have to provide evidence that the software being used fulfills the requirement put forth by the industry specific standard for functional safety, such as the ISO 26262 standard for the automotive industry. -
Relevant Norms and Standards
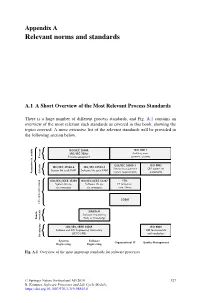
Appendix A Relevant norms and standards A.1 A Short Overview of the Most Relevant Process Standards There is a huge number of different process standards, and Fig. A.1 contains an overview of the most relevant such standards as covered in this book, showing the topics covered. A more extensive list of the relevant standards will be provided in the following section below. ISO/IEC 15504, ISO 19011 ISO/IEC 330xx Auditing man- agement systems Process Process assessment ISO/IEC 20000-1 ISO 9001 ISO/IEC 15504-6 ISO/IEC 15504-5 Service management QM system re- System life cycle PAM Software life cycle PAM Assessments, audits Criteria system requirements quirements ISO/IEC/IEEE 15288 ISO/IEC/IEEE 12207 ITIL System life cy- Software life cy- IT Infrastruc- cle processes cle processes ture Library COBIT Life cycle processes SWEBoK Software engineering Funda- Body of Knowledge mentals ISO/IEC/IEEE 24765 ISO 9000 Systems and SW Engineering Vocabulary QM fundamentals (SEVOCAB) and vocabulary Vocabulary Systems Software Organzational IT Quality Management Engineering Engineering Fig. A.1 Overview of the most important standards for software processes © Springer Nature Switzerland AG 2018 327 R. Kneuper, Software Processes and Life Cycle Models, https://doi.org/10.1007/978-3-319-98845-0 328 A Relevant norms and standards A.2 ISO and IEC Standards The International Organization for Standardization (ISO) is the main international standard-setting organisation, working with representatives from many national standard-setting organisations. Standards referring to electrical, electronic and re- lated technologies, including software, are often published jointly with its sister organisation, the International Electrotechnical Commission (IEC), but IEC also publishes a number of standards on their own. -

IEC 61508 Standard for Functional Safety of Electrical/Electronic/Programmable Electronic Safety-Related Systems
IEC 61508 Overview Report A Summary of the IEC 61508 Standard for Functional Safety of Electrical/Electronic/Programmable Electronic Safety-Related Systems exida Sellersville, PA 18960, USA +1-215-453-1720 © exida IEC 61508 Overview Report, Version 2.0, January 2, 2006 Page 1 of 29 1 Overall Document Summary IEC 61508 is an international standard for the “functional safety” of electrical, electronic, and programmable electronic equipment. This standard started in the mid 1980s when the International Electrotechnical Committee Advisory Committee of Safety (IEC ACOS) set up a task force to consider standardization issues raised by the use of programmable electronic systems (PES). At that time, many regulatory bodies forbade the use of any software-based equipment in safety critical applications. Work began within IEC SC65A/Working Group 10 on a standard for PES used in safety-related systems. This group merged with Working Group 9 where a standard on software safety was in progress. The combined group treated safety as a system issue. The total IEC 61508 standard is divided into seven parts. Part 1: General requirements (required for compliance); Part 2: Requirements for electrical/electronic/programmable electronic safety-related systems (required for compliance); Part 3: Software requirements (required for compliance); Part 4: Definitions and abbreviations (supporting information) Part 5: Examples of methods for the determination of safety integrity levels (supporting information) Part 6: Guidelines on the application of parts 2 and 3 (supporting information) Part 7: Overview of techniques and measures (supporting information). Parts 1, 3, 4, and 5 were approved in 1998. Parts 2, 6, and 7 were approved in February 2000. -

D1.5 Impact on Standards and Open Initiatives - First Analysis
Ref. Ares(2020)1266005 - 28/02/2020 D1.5 Impact on standards and open initiatives - First analysis Version 1.0 Document Information Contract Number 825473 Project Website https://elastic-project.eu/ Contractual Deadline M15, Feb 2020 Dissemination Level CO Nature R Author(s) Thales R&T Contributor(s) BSC, ISEP, SIX, THALIT Reviewer(s) SIX, BSC Keywords Railway Safety Standards, Open Initiatives, Impact Notices: The ELASTIC project has received funding from the European Union’s Horizon 2020 research and innovation programme under the grant agreement Nº 825473. © 2019 ELASTIC. A Software Architecture for Extreme-ScaLe Big-Data AnalyticS in Fog CompuTing ECosystems. All rights reserved. D1.5 Impact on standards and open initiatives - First analysis Version 1.0 Change Log Version Author Description of Change V0.1 TRT Initial Draft Contribution on the analysis of OpenFog V0.2 BSC Initiative V0.2 TRT Contribution 61508 std, Railway std V0.3 SIX DMTF V0.4 ISEP FIWARE V0.5 BSC OpenFog V0.6 THALIT Contribution 61508 std, Railway std V0.7 TRT Final version, including revision V0.8 SIX Internal review V1.0 BSC Final adjustments. Version released to EC. 2 D1.5 Impact on standards and open initiatives - First analysis Version 1.0 Table of contents Change Log ...................................................................................... 2 1. Executive Summary ....................................................................... 5 2. Introduction ............................................................................... 6 2.1 Purpose -

CIP Safety Protocol Training Session 0: Overview of Functional Safety and Safety Networks
CIP Safety Protocol Training Session 0: Overview of Functional Safety and Safety Networks Virtual Training Courses Before We Begin • Introductions • All attendees are automatically muted with no video connection as a default. • Please use the Q&A to ask questions, not the chat. We will address questions as they come in. • At the end if there is time, we will take questions verbally from the attendees. We will advise if and when there is time for you to “raise your hand” if you have a question. • Please complete the 4 question post session survey. The survey will launch when you close out of the webinar. PUB00303R6, CIP Safety Protocol Training, © 2021 ODVA 2 Overview of Functional Safety Standards Jim Grosskreuz Rockwell Automation Evolution of Factory Safety In early factories, workers were encouraged to act in unsafe ways to meet production goals. Industry 2.0 and 3.0 gave us increased focus improved safety by focusing on human factors and developing best practices. Industry 4.0 requires flexibility, ease of use, human-machine collaboration, and interoperability between vendors. PUB00303R6, CIP Safety Protocol Training, © 2021 ODVA 4 Machinery Builder & Operator Responsibilities • European Union – Machinery Directive • Prescriptive approach to machinery safety • Mandates risk assessments and safe machines • United States – OSHA • Less prescriptive approach to machinery safety • Introduces fines for violations – Litigious Culture • OEMs and System Integrators aren’t protected from litigation • Elsewhere – Mixed legal and cultural environments -

Programming Languages — Guidance to Avoiding Vulnerabilities in Programming Languages – Part 1: Language Independent Guidance
Baseline Edition – 3 TR 24772-1 ISO/IEC JTC 1/SC 22/WG23 N0826 Posted Date: 28 August 2018 ISO/IEC TR 24772-1 Edition 1 ISO/IEC JTC 1/SC 22/WG 23 Secretariat: ANSI Information Technology — Programming languages — Guidance to avoiding vulnerabilities in Programming languages – Part 1: Language indePendent guidance Élément introductif — Élément principal — Partie n: Titre de la partie Warning This document is not an ISO International Standard. It is distributed for review and comment. It is subject to change without notice and may not be referred to as an International Standard. ReciPients of this draft are invited to submit, with their comments, notification of any relevant Patent rights of which they are aware and to Provide suPPorting documentation. Document tyPe: International standard Document subtyPe: if aPPlicable Document stage: (10) develoPment stage Document language: E © ISO/IEC 2013 – All rights reserved i WG 23/N 0751 CopyrigHt notice This ISO document is a working draft or committee draft and is coPyright-protected by ISO. While the reProduction of working drafts or committee drafts in any form for use by ParticiPants in the ISO standards develoPment Process is Permitted without Prior Permission from ISO, neither this document nor any extract from it may be reproduced, stored or transmitted in any form for any other PurPose without Prior written Permission from ISO. Requests for Permission to reProduce this document for the PurPose of selling it should be addressed as shown below or to ISO’s member body in the country of the requester: ISO copyright office Case postale 56, CH-1211 Geneva 20 Tel. -

Reduce Medical Device Compliance Costs with Best Practices
Reduce Medical Device Compliance Costs with Best Practices [email protected] 1 Agenda • Medical Software Certification – How new is Critical Software Certification? – What do we need to do? – What Best Practises will help us achieve Certification? • Questions & Answers 2 CRITICAL SOFTWARE CERTIFICATION HOW NEW IS IT? 3 Where is certification enforced? Whenever the cost of failure is very high Risk of death or injury High cost of repair High cost of product recall What software needs to be certified? Aircraft Trains Medical Devices Nuclear Power Cars Industrial Plants Stations 4 Leading Safety Critical Standards Avionics DO-178B (First published 1992) / DO-178C Industrial IEC 61508 (First published 1998) Railway CENELEC EN 50128 (First published 2001) Nuclear IEC 61513 (First published 2001) Automotive ISO/DIS 26262 (Draft) Medical IEC 62304 (First published 2006) Process IEC 61511 (First published 2003) So, the experience of other sectors is invaluable to the medical device (and automotive) industries. IEC 62304 AND RELATED IEC 61508 DERIVATIVES 6 Safety Integrity Levels IEC 61508 (Industrial) SIL Level 1 to 4 ISO/DIS 26262 (Automotive) ASIL A to ASIL D IEC 62304 (Medical) Class A to Class C CENELEC EN 50128 (Railway) SIL Level 0 to SIL Level 4 DO-178B / DO-178C (Avionics) Level E to Level A So, nothing new here either! Functional Safety Assessment Classes A –C in IEC 62304 are based on the principle of IEC 61508’s SIL levels ... Safety Integrity Level Minimum Level of Independence 1 2 3 4 Independent Person HR HR NR NR Independent -

Implementing IEC 61508:2010 with the LDRA Tool Suite®
Technical White Paper Software Technology Implementing IEC 61508:2010 with the LDRA tool suite® Working with the programmable electronic components sector to achieve functional safety www.ldra.com © LDRA Ltd. This document is property of LDRA Ltd. Its contents cannot be reproduced, disclosed or utilised without company approval. LDRA Ltd 1 Implementing IEC 61508:2010 with the LDRA tool suite® Contents Introduction 3 Safety Integrity Levels 3 The software development lifecycle 4 IEC 61508:2010-3 Section 7.2: “Software safety requirements specification” 5 Bi-directional traceability 6 Static analysis and bi-directional traceability 7 IEC 61508:2010-3 Section 7.3: “Validation plan for software aspects of system safety” 8 IEC 61508:2010-3 Section 7.4.3: “Requirements for software architecture design” 8 IEC 61508:2010-3 Section 7.4.4: “Requirements for support tools, including programming languages” 10 IEC 61508:2010-3 Section 7.4.5: “Requirements for detailed design and development – software system design” 11 IEC 61508:2010-3 Section 7.4.6: “Requirements for code implementation” 12 IEC 61508:2010-3 Section 7.4.7: “Requirements for software module testing” and Section 7.4.8: “Requirements for software integration testing” 12 IEC 61508:2010-3 Section 7.5: “Programmable electronics integration (hardware and software)” 14 IEC 61508:2010-3 Section 7.4.6: “Requirements for code implementation” 16 IEC 61508:2010-3 Section 7.7: “Software aspects of system safety validation” 16 IEC 61508:2010-3 Section 7.8: “Software modification” 16 The connected -

Model-Based Design for IEC 62304 Medical Devices
Using Model-Based Design in an IEC 62304-Compliant Software Development Process David Hoadley, Ph.D.1 1 The MathWorks, Inc., Novi, MI, USA [email protected] 1 Introduction IEC 62304 [1] is an international standard (hereafter referred to as the Standard) that specifies software development life cycle processes to improve the safety of medical devices. It defines a series of activities and tasks that are required for medical device software engineering. We will discuss how MathWorks tools for Model-Based Design, which have been used to create high-integrity software [2-4], can be used to create control system and signal processing software in a manner compliant with the Standard. 2 Software development processes 2.1 Software design and implementation In addition to representing functional behavior, Simulink® can be used to segregate a software design into major structural components, indicate their external properties, and demonstrate the relationship among the components. One application would be to separate risk control measures into a Simulink subsystem or referenced model to more intuitively track them and potentially lower the software safety class for other parts of the software architecture. Simulink Verification and Validation™ provides a facility called the Requirements Management Interface that establishes navigable links between textual requirements and components of models. Software in safety class C (the greatest potential for harm) of the Standard requires a documented, verified detailed design for each software unit. The Simulink model or subsystem that represents each unit can be an important part of this detailed design. Additional software standards such as MAAB [5], DO-178B [6], IEC 61508 [7] and MISRA-C® [8], can facilitate validation of the unit design. -

Please Read Our IO-Link Safety Policy
IO-Link Safety Policy The concept of IO-Link safety has been designed and developed according to international standards such as IEC 61508, IEC 61784-3, and ISO 13849 and approved by competent assessment bodies. In order to prevent and protect the manufacturers and vendors of FS-Masters and FS- Devices from possibly misleading understandings or wrong expectations and negligence actions regarding safety-related developments and applications the following shall be observed and explained in each training, seminar, workshop and consultancy. Rules: • Any non-safety-related device automatically will not be applicable for safety- related applications just by using fieldbus or IO-Link communication and a safety communication layer such as in IO-Link safety. The safety technology part of a safety device shall be approved for a Safety Integrity Level (SIL) or Performance Level (PL) suitable for the intended safety functions. The IO-Link safety part shall be implemented and approved for the same SIL/PL or better. • In order to enable a product for safety-related applications, appropriate development processes according to safety standards shall be observed (see IEC 61508, IEC 62061, ISO 13849) and an assessment from a competent assessment body or authorized manufacturer department shall be achieved. • The manufacturer/vendor of a safety product is responsible for the correct implementation of the safety communication layer technology, the correctness and completeness of the product documentation and information. • Supplemental safety-related information to the published "IO-Link safety" specification shall be observed for implementation, test and assessment if applicable. Normally, this information is provided by the working group as response to a change request (CR) within the CR-database that is in state "implementation" and approved by an assessment body. -

Chapter 11 Software Quality
CHAPTER 11 SOFTWARE QUALITY Dolores Wallace* and Larry Reeker National Institute of Standards and Technology Gaithersburg, Maryland 20899 USA {Dolores.Wallace, Larry.Reeker}@NIST.gov *Dolores Wallace has retired from NIST (but is still available via her NIST e-mail address at the time of publication.) Table of Contents Another major topic of this KA is just trying to answer the question “What is software quality?” this is not a simple 1. Introduction and Definition of the Software Quality question, as was concluded by David Garvin [Gar84, Knowledge Area ......................................................... 1 Hya96]. Though we will not go into the complexities that 2. Breakdown of Topics for Software Quality................ 2 he studied, we will present a view for the working software 3. Breakdown Rationale................................................ 12 engineer. 4. Matrix of Topics vs. Reference material................... 13 The discussion of the purpose and planning of SQA and V&V is a bridge between the discussion of quality and the 5. Recommended References for Software Quality...... 16 activities and techniques discussion for SQA and V&V, but it is also an important activity in itself. In the planning process, the activities are designed to be fitted to the 1. INTRODUCTION AND DEFINITION OF THE SOFTWARE product and its purposes, including the quality attributes in QUALITY KNOWLEDGE AREA the requirements. This chapter deals with software quality considerations that Because determining quality of both the final product and transcend the life cycle processes. Of course, software intermediate products requires measurement, the topic of quality is a ubiquitous concern in software engineering, so measurement is relevant to the other parts of this KA. -

An Introduction to Functional Safety and IEC 61508
An introduction to Functional Safety and IEC 61508 Application Note AN9025 Contents Page 1 INTRODUCTION . 1 2 FUNCTIONAL SAFETY . 1 2.1 Aspects of safety . 1 2.2 Glossary of terms . 1 3 OVERVIEW OF IEC 61508 . 2 3.1 Origins of IEC 61508 . 2 3.2 The physical form of the standard . 2 3.3 Scope of the standard . 2 3.4 The standard's rationale . 3 3.5 The overall safety lifecycle . 3 3.6 Risk and its analysis and reduction . 4 3.7 Safety requirements and safety functions . 5 3.8 Safety integrity levels . 5 3.9 Safety assessment . 6 3.10 Principles not covered by the standard . 6 4 SOME RELATED STANDARDS . 6 4.1 DIN 19250 . 7 4.2 S84 . 7 4.3 IEC 61511 . 7 5 THE TOLERABILITY OF RISK . 7 6 HOW IEC 61508 IS APPLIED . 8 6.1 Introduction . 8 6.2 Installation . 8 6.3 Safety function . 9 6.4 System test . 11 6.5 Calculating PFDavg . 11 6.6 Operational reliability . 11 6.7 Conclusion . 11 7 UNDERSTANDING AND USING IEC 61508 APPROVALS . 11 7.1 What IEC 61508 certificates should tell you . 11 7.2 Calculating the average probability of failure on demand . 12 8 SOURCES OF INFORMATION . 13 © 2002 MTL Instruments Group plc. All rights reserved. Material may only be copied from this publication on the understanding that the source of the material is acknowledged explicitly. AN9025-3 Mar 2002 AN9025-3 March 2002 1 INTRODUCTION 2.2 Glossary of terms The definitions given in this glossary of terms are direct quotations Instrumented safety systems are not new.