Self-Configuring Safety Networks
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

Accessing PI System Using OPC Unified Architecture
Accessing PI System using OPC Unified Architecture Alisher Maksumov OPC Development Group Lead OSIsoft, Inc. Agenda • What is OPC Unified Architecture? • OPC UA Web Services • Information Modeling • Client and Sever Communication • Exposing PI System • Server and Client Demo • OPC UA Roadmap • Summary What is OPC Unified Architecture? • Next generation of OPC technology – Platform independent • Designed with SOA principles – Extensible, discoverable – Well defined message syntax • Mapped into Web Services – WSDL, XML schema, SOAP – Message exchange over HTTP/HTTPS • Supports enhanced security – Certificates, Encryption, Signature • Adopts Information Modeling concepts – Browsable and discoverable Address Space model – Objects, Nodes, Types, Data Variables, Properties OPC UA Specification • Part 1 – Concepts • Part 2 – Security • Part 3 – Address Space Generic Parts • Part 4 – Services • Part 5 – Information Model • Part 6 – Mappings Mapping to Web Services • Part 7 – Profiles Supported features • Part 8 – Data Access • Part 9 – Alarms and Conditions Parts specific to classic • Part 10 – Programs OPC mapping • Part 11 – Historical Access • Part 12 – Discovery OPC Server discovery • Part 13 – Aggregates OPC UA Web Services • Defined in OPC UA Spec (Parts 4, 6) and OPC UA WSDL • Can be group into service sets: – Discovery Service Set • FindServers, GetEndpoints, RegisterServer – Secure Channel Service Set • OpenSecureChannel, CloseSecureChannel – Session Service Set • Create, Activate, Close Session – Node Management Service Set • Add and -

OPC UA Server App OPC UA Server for Ctrlx CORE
Application Manual OPC UA Server App OPC UA Server for ctrlX CORE R911403778, Edition 03 Copyright © Bosch Rexroth AG 2021 All rights reserved, also regarding any disposal, exploitation, reproduction, editing, distribution, as well as in the event of applications for industrial property rights. Liability The specified data is intended for product description purposes only and shall not be deemed to be a guaranteed characteristic unless expressly stipulated in the contract. All rights are reserved with respect to the content of this documentation and the availability of the product. DOK-XCORE*-OPCUA*SERV*-AP03-EN-P DC-IA/EPI5 (TaDo/MePe) f5f200cddfc773880a347e883d356b4f, 3, en_US OPC UA Server App 3 / 31 Table of contents 1 About this documentation 4 2 Important directions on use 5 2.1 Intended use. 5 2.1.1 Introduction. 5 2.1.2 Areas of use and application . 5 2.2 Unintended use. 6 3 Safety instructions 7 4 Introduction into the OPC Unified Architecture 9 4.1 General information. 9 4.2 Overview on specifications . 9 4.3 Information model . 10 4.4 Service-oriented architecture . 10 5 Rexroth ctrlX OPC UA Server 17 5.1 The ctrlX OPC UA Server in the ctrlX AUTOMATION . 17 5.2 Installation on ctrlX CORE. 17 5.3 Properties. 19 5.4 Configuration . 19 5.4.1 Certificate configuration . 20 6 Related documentation 23 6.1 Overview. 23 6.2 ctrlX AUTOMATION. 23 6.3 ctrlX WORKS. 23 6.4 ctrlX CORE. 24 6.5 ctrlX CORE Apps. 24 7 Service and support 27 8 Index 29 R911403778, Edition 03 Bosch Rexroth AG 4 / 31 OPC UA Server App 1 About this documentation Editions of this documentation Edition Release Notes date 01 2020-06 First edition 02 2021-01 Revision ctrlX CORE version UAS-V-0106 03 2021-04 Revision ctrlX CORE version UAS-V-0108 Bosch Rexroth AG R911403778, Edition 03 OPC UA Server App 5 / 31 Intended use 2 Important directions on use 2.1 Intended use 2.1.1 Introduction Rexroth products are developed and manufactured to the state-of-the-art. -

Comtrol IO-Link to OPC UA
FOR IMMEDIATE RELEASE CONTACT: Jordan DeGidio Marketing Specialist +1 763.957.6000 [email protected] Comtrol Implements OPC-UA connectivity with MultiLink™ on IO-Link Master family MINNEAPOLIS, Minnesota – April 21, 2017 — Comtrol Corporation, a manufacturer of industrial device connectivity products and the official North American IO-Link Competency Center, today announced the availability of OPC-UA support with its MultiLink™ technology on its IO-Link Master family of products. OPC Unified Architecture (OPC-UA) is a machine to machine communication protocol developed for industrial automation. OPC-UA allows customers to communicate with industrial equipment and systems for data connection and control, freely use an open standard, cross-platform, implement service-oriented architecture (SOA) software and utilize robust security. Comtrol’s MultiLink™ technology allows IO-Link Masters to simultaneously provide sensors Process data to PLC platforms, while also sending the sensors ISDU Service and Process data via Modbus TCP or OPC-UA upstream to IIoT/Industry 4.0 Cloud solutions or factory SCADA systems. Comtrol’s IO-Link Masters are available in three industrial Ethernet protocols: EtherNet/IP, Modbus TCP and PROFINET IO, which are all capable of running OPC UA with MultiLink™. “The OPC Foundation is very excited about the great work that Comtrol Corporation has been doing with the OPC UA technology. Their company specializes in quality networking and industrial data communication products, with the addition OPC UA to their portfolio of IO-Link Masters, factory automation users will have a seamless connection from IO-Link sensors and actuators to SCADA/HMI and cloud systems. This will add significant capability allowing seamless interoperability across the multitude of industrial networks and industrial devices says Thomas J Burke, OPC Foundation President & Executive Director. -

Data Exchange in Distributed Mining Systems by OPC Unified Architec- Ture, WLAN and TTE VLF Technology
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by Technische Universität Bergakademie Freiberg: Qucosa REAL TIME MINING - Conference on Innovation on Raw Material Extraction Amsterdam 2017 Data exchange in distributed mining systems by OPC Unified Architec- ture, WLAN and TTE VLF technology. David Horner1, Friedemann Grafe2, Tobias Krichler1, Helmut Mischo1, Thomas Wilsnack2) 1 TU Bergakademie Freiberg 2 IBeWa Consulting ABSTRACT Mining operations rely on effective extraction policies, which base on concerted manage- ment and technical arrangements. In addition to commodities, mining of data is the in- creasingly matter of subject in mining engineering. The Horizon 2020 project – Real-Time- Mining supports the ongoing paradigm shift of pushing mining activities from discontinuous to continuous operation. In this respect, the partners TU Bergakademie Freiberg (TU BAF) and IBeWa Consulting tackle the issue of physical and logical data acquisition in under- ground mining. The first aspect of the project addresses the ‘logical’ provision of data. Mining technology is increasingly interacting among each other and integrated into globally distributed sys- tems. At the same time, the integration of current mining devices and machineries into su- perordinated systems is still complex and costly. This means only a few number of mining operators is capable to integrate their operation technology into a Supervisory Control and Data Acquisition (SCADA) system. TU BAF presents the middleware OPC Unified Archi- tecture, which is a platform independent middleware for data exchange and technology interconnection among distributed systems. By installing a SCADA demonstrator at the research and education mine Reiche Zeche, TU BAF intends to present the technical fea- sibility of a SCADA system basing on OPC UA even for SME mining operations. -

Evaluation of Open Source Operating Systems for Safety-Critical Applications Master’S Thesis in Embedded Electronic System Design
Evaluation of open source operating systems for safety-critical applications Master’s thesis in Embedded Electronic System Design Petter Sainio Berntsson Department of Computer Science and Engineering CHALMERS UNIVERSITY OF TECHNOLOGY UNIVERSITY OF GOTHENBURG Gothenburg, Sweden 2017 MASTER’S THESIS 2017 Evaluation of open source operating systems for Safety-critical applications Petter Sainio Berntsson Department of Computer Science and Engineering Chalmers University of Technology University of Gothenburg Gothenburg, Sweden 2017 Evaluation of open source operating systems for safety-critical applications Petter Sainio Berntsson © Petter Sainio Berntsson, 2017 Examiner: Per Larsson-Edefors Chalmers University of Technology Department of Computer Science and Engineering Academic supervisor: Jan Jonsson Chalmers University of Technology Department of Computer Science and Engineering Industrial supervisors: Lars Strandén RISE Research Institutes of Sweden Dependable Systems Fredrik Warg RISE Research Institutes of Sweden Dependable Systems Master’s Thesis 2017 Department of Computer Science and Engineering Chalmers University of Technology University of Gothenburg SE-412 96 Gothenburg Telephone +46(0) 31 772 1000 Abstract Today many embedded applications will have to handle multitasking with real-time time constraints and the solution for handling multitasking is to use a real-time operating system for scheduling and managing the real-time tasks. There are many different open source real-time operating systems available and the use of open source software for safety-critical applications is considered highly interesting by industries such as medical, aerospace and automotive as it enables a shorter time to market and lower development costs. If one would like to use open source software in a safety-critical context one would have to provide evidence that the software being used fulfills the requirement put forth by the industry specific standard for functional safety, such as the ISO 26262 standard for the automotive industry. -

Combining Automationml and OPC UA
Combining AutomationML and OPC UA Dr.-Ing. Miriam Schleipen © Fraunhofer IOSB 1 Agenda • Motivation • Plug-and-work principles • Goals • Mapping of AutomationML and OPC UA • Access to the AutomationML model in OPC UA • Examples • Conclusion and Outlook © Fraunhofer IOSB 2 Motivation - Changes • Continuous changes of production systems reconfiguration of hardware and software components • Objects to change within a manufacturing enterprise • Products • Technological or logistical processes • Parts of the manufacturing facilities • Software systems • Company’s organization • interoperability and seamless semantic integration necessary © Fraunhofer IOSB 3 Initial situation - ‚Babylon‘ on the shopfloor Visualization / SCADA Production Monitoring & Control ? ? ? ? Ωασχηµοδυ Τροχκενµοδυλ Abc_23-xy_Vors. Τεµπερατυρ Bbc_24-xy_T ist Γεσχηωινδιγκειτ Image sources: MOC Danner, KUKA, MAG, Schunk © Fraunhofer IOSB 4 Plug-and-work • Term definition: • setting up, modification or termination of interoperation between two or more involved parties with minimal effort • Note 1: The interoperability of those involved is assumed. • Note 2: The minimum effort can vary depending on the state of the art. • Note 3: Plug & play and plug & produce are synonyms or similar terms. Source: I4.0 Glossary of the VDI GMA technical committee 7.21 »Industrie 4.0« © Fraunhofer IOSB 5 Unique Datamodels (yesterday-Level 1, today-Level 2, tomorrow-Industrie 4.0) Visualisation/ Evaluation New Application Control Function Knowhow/Meaning Semantic Models („Industry -

Integration of OPC Unified Architecture with Iiot Communication Protocols in an Arrowhead Translator
Integration of OPC Unified Architecture with IIoT Communication Protocols in an Arrowhead Translator Jesper Rönnholm Engineering Physics and Electrical Engineering, master's level 2018 Luleå University of Technology Department of Computer Science, Electrical and Space Engineering Integration of OPC Unified Architecture with IIoT Communication Protocols in an Arrowhead Translator Jesper R¨onnholm Master's thesis Dept. of Computer Science, Electrical and Space Engineering Lule˚aUniversity of Technology Supervisors: Jerker Delsing, Hasan Derhamy 2018 Abstract This thesis details the design of a protocol translator between the industrial-automation protocol OPC UA, and HTTP. The design is based on the architecture of the protocol trans- lator of the Arrowhead framework, and is interoperable with all of its associated protocols. The design requirements are defined to comply with a service-oriented architecture (SOA) and RESTful interaction through HTTP, with minimal requirement of the consuming client to be familiar with OPC UA semantics. Effort is put into making translation as transparent as possible, but limits the scope of this work to exclude a complete semantic translation. The solution presented in this thesis satisfies structural- and foundational interoperability, and bridges interaction to be independent of OPC UA services. The resulting translator is capable of accessing the content of any OPC UA server with simple HTTP-requests, where addressing is oriented around OPC UA nodes. Preface I was first introduced to the opportunity of doing this project as part of master's thesis in 2015 by Prof. Jerker Delsing. He was the coordinator of the Arrowhead Project, which at the time was the largest industrial automation project in Europe, with 78 partners and a budget of 68 million euro. -

OPC Unified Architecture Interoperability for Industrie 4.0 and the Internet of Things
1 OPC Unified Architecture Interoperability for Industrie 4.0 and the Internet of Things IoT Industrie 4.0 M2M 2 Welcome to the OPC Foundation! As the international standard for vertical and horizontal communication, OPC-UA provides semantic interoper- ability for the smart world of connect- ed systems. Thomas J. Burke President und Executive Director OPC Foundation OPC Unified Architecture (OPC-UA) is the data ex- OPC-UA is an IEC standard and therefore ideally change standard for safe, reliable, manufacturer- suited for cooperation with other organizations. and platform-independent industrial communication. As a global non-profit organization, the OPC Foun- It enables data exchange between products from dation coordinates the further development of the different manufacturers and across operating sys- OPC standard in collaboration with users, manufac- tems. The OPC-UA standard is based on specifica- turers and researchers. Activities include: tions that were developed in close cooperation be- tween manufacturers, users, research institutes and ➞ Development and maintenance of specifications consortia, in order to enable safe information ex- ➞ Certification and compliance tests of change in heterogeneous systems. implementations ➞ Cooperation with other standards organizations OPC has been very popular in the industry and also becoming more popular in other markets like the This brochure provides an overview of IoT, M2M Internet of Things (IoT). With the introduction of Ser- (Machine to Machine) and Industrie 4.0 requirements vice-Oriented-Architecture (SOA) in industrial auto- and illustrates solutions, technical details and imple- mation systems in 2007, OPC-UA started to offer a mentations based on OPC-UA. scalable, platform-independent solution which com- The broad approval among representatives from re- bines the benefits of web services and integrated search, industry and associations indicates OPC-UA security with a consistent data model. -
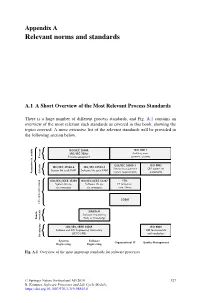
Relevant Norms and Standards
Appendix A Relevant norms and standards A.1 A Short Overview of the Most Relevant Process Standards There is a huge number of different process standards, and Fig. A.1 contains an overview of the most relevant such standards as covered in this book, showing the topics covered. A more extensive list of the relevant standards will be provided in the following section below. ISO/IEC 15504, ISO 19011 ISO/IEC 330xx Auditing man- agement systems Process Process assessment ISO/IEC 20000-1 ISO 9001 ISO/IEC 15504-6 ISO/IEC 15504-5 Service management QM system re- System life cycle PAM Software life cycle PAM Assessments, audits Criteria system requirements quirements ISO/IEC/IEEE 15288 ISO/IEC/IEEE 12207 ITIL System life cy- Software life cy- IT Infrastruc- cle processes cle processes ture Library COBIT Life cycle processes SWEBoK Software engineering Funda- Body of Knowledge mentals ISO/IEC/IEEE 24765 ISO 9000 Systems and SW Engineering Vocabulary QM fundamentals (SEVOCAB) and vocabulary Vocabulary Systems Software Organzational IT Quality Management Engineering Engineering Fig. A.1 Overview of the most important standards for software processes © Springer Nature Switzerland AG 2018 327 R. Kneuper, Software Processes and Life Cycle Models, https://doi.org/10.1007/978-3-319-98845-0 328 A Relevant norms and standards A.2 ISO and IEC Standards The International Organization for Standardization (ISO) is the main international standard-setting organisation, working with representatives from many national standard-setting organisations. Standards referring to electrical, electronic and re- lated technologies, including software, are often published jointly with its sister organisation, the International Electrotechnical Commission (IEC), but IEC also publishes a number of standards on their own. -

IEC 61508 Standard for Functional Safety of Electrical/Electronic/Programmable Electronic Safety-Related Systems
IEC 61508 Overview Report A Summary of the IEC 61508 Standard for Functional Safety of Electrical/Electronic/Programmable Electronic Safety-Related Systems exida Sellersville, PA 18960, USA +1-215-453-1720 © exida IEC 61508 Overview Report, Version 2.0, January 2, 2006 Page 1 of 29 1 Overall Document Summary IEC 61508 is an international standard for the “functional safety” of electrical, electronic, and programmable electronic equipment. This standard started in the mid 1980s when the International Electrotechnical Committee Advisory Committee of Safety (IEC ACOS) set up a task force to consider standardization issues raised by the use of programmable electronic systems (PES). At that time, many regulatory bodies forbade the use of any software-based equipment in safety critical applications. Work began within IEC SC65A/Working Group 10 on a standard for PES used in safety-related systems. This group merged with Working Group 9 where a standard on software safety was in progress. The combined group treated safety as a system issue. The total IEC 61508 standard is divided into seven parts. Part 1: General requirements (required for compliance); Part 2: Requirements for electrical/electronic/programmable electronic safety-related systems (required for compliance); Part 3: Software requirements (required for compliance); Part 4: Definitions and abbreviations (supporting information) Part 5: Examples of methods for the determination of safety integrity levels (supporting information) Part 6: Guidelines on the application of parts 2 and 3 (supporting information) Part 7: Overview of techniques and measures (supporting information). Parts 1, 3, 4, and 5 were approved in 1998. Parts 2, 6, and 7 were approved in February 2000. -

OPC Unified Architecture for Mtconnectr
OPC Unified Architecture for MTConnect R Companion Specification Release Candidate 2.0RC8 February 19, 2019 MTConnect R is a registered trademark of AMT - The Association for Manufacturing Technology. Use of MTConnect R is limited to use as specified on http://www.mtconnect.org/. February 19, 2019 Specification Type: Industry Standard Specification Comments: Title: OPC Unified Architecture for MT- Date: February 19, 2019 Connect Version: 2.0RC8 Software: LaTeX Authors: William Sobel, Randy Armstrong, Source: OPC_UA_MTConnect_2.0RC8.pdf John Turner, Russell Waddell, Shaurabh Singh Owner: MTConnect Institute Status: Release Candidate Document History Version Date Reason Comments Mantis 2.00 RC8 2019-02-18 Revision Added list of tables 4631 2.00 RC8 2019-02-18 Revision Added table for reset triggers and suggested status codes 4630 2.00 RC8 2019-02-18 Revision Removed data rate issue from page 77 4629 2.00 RC7 2019-02-12 Revision 2.0 RC6: 8.4.6.2 MTConnect Condition Branching Example – 4608 Need to improve documentation of condition branching 2.00 RC7 2019-02-12 Revision Document 2.0 RC 6: 8.4.7 Messages – need to improve message 4607 handling 2.00 RC7 2019-02-12 Node Ids List of NodeIds as CSV 4612 2.00 RC7 2019-02-12 Revision A chapter for Profiles and Namespaces needs to be added 4611 2.00.06 2019-01-22 Revision Added missing class types and made MTMessageType a Variable instead of an Event 2.00.05 2018-12-09 Revision Fixed Composition 2.00.04 2018-11-30 Initial Initial Release Candidate MTConnect R OPC UA Companion Specification - Release Candidate 2.0RC8 i Contents 1 Scope1 2 OPC Unified Architecture for MTConnect Companion Specification Goals2 3 Who Will Find Benefit from this Companion Specification?3 4 Normative References3 4.1 OPC UA References............................ -

D1.5 Impact on Standards and Open Initiatives - First Analysis
Ref. Ares(2020)1266005 - 28/02/2020 D1.5 Impact on standards and open initiatives - First analysis Version 1.0 Document Information Contract Number 825473 Project Website https://elastic-project.eu/ Contractual Deadline M15, Feb 2020 Dissemination Level CO Nature R Author(s) Thales R&T Contributor(s) BSC, ISEP, SIX, THALIT Reviewer(s) SIX, BSC Keywords Railway Safety Standards, Open Initiatives, Impact Notices: The ELASTIC project has received funding from the European Union’s Horizon 2020 research and innovation programme under the grant agreement Nº 825473. © 2019 ELASTIC. A Software Architecture for Extreme-ScaLe Big-Data AnalyticS in Fog CompuTing ECosystems. All rights reserved. D1.5 Impact on standards and open initiatives - First analysis Version 1.0 Change Log Version Author Description of Change V0.1 TRT Initial Draft Contribution on the analysis of OpenFog V0.2 BSC Initiative V0.2 TRT Contribution 61508 std, Railway std V0.3 SIX DMTF V0.4 ISEP FIWARE V0.5 BSC OpenFog V0.6 THALIT Contribution 61508 std, Railway std V0.7 TRT Final version, including revision V0.8 SIX Internal review V1.0 BSC Final adjustments. Version released to EC. 2 D1.5 Impact on standards and open initiatives - First analysis Version 1.0 Table of contents Change Log ...................................................................................... 2 1. Executive Summary ....................................................................... 5 2. Introduction ............................................................................... 6 2.1 Purpose