Distance-Bounding Protocols
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
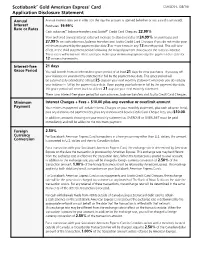
Scotiabank®* Gold American Express® Card Application Disclosure
File Name: DM-AQ_Disclosure_CSAGDS-E_0716 Trim: 8.5” x 11” Creative & Production Services Bleed: 0" Safety: n/a Mech Res: 300dpi 100 Yonge Street, 10th Floor Toronto, ON M5C 2W1 Colours: CMYK Scotiabank®* Gold American Express® Card CSAGDS-E (08/16) Application Disclosure Statement Annual Annual interest rates are in effect on the day the account is opened (whether or not a card is activated). Interest Purchases: 19.99% Rate or Rates Cash advances**, balance transfers and Scotia®* Credit Card Cheques: 22.99% Your preferred annual interest rates will increase to standard rates of 24.99% on purchases and 27.99% on cash advances, balance transfers and Scotia Credit Card Cheques if you do not make your minimum payment by the payment due date 2 or more times in any 12 month period. This will take effect in the third statement period following the missed payment that caused the rates to increase. These rates will remain in effect until you make your minimum payments by the payment due date for 12 consecutive months. Interest-free 21 days Grace Period You will benefit from an interest-free grace period of at least 21 days for new purchases± if you pay off your balance on your monthly statement in full by the payment due date. This grace period will be automatically extended to at least 25 days on your next monthly statement whenever you do not pay your balance in full by the payment due date. Upon paying your balance in full by the payment due date, this grace period will revert back to at least 21 days on your next monthly statement. -

Summary of Credit Terms- Union Bank® Cashback Rewards Visa® Card
Summary of Credit Terms- Union Bank® Cashback Rewards Visa® Card PLEASE NOTE: If you apply for the Union Bank Cashback Rewards Visa Card and meet our eligibility criteria for the Visa Signature® Card, you agree that we may consider your application as one for (and upgrade you to) the Union Bank Cashback Rewards Visa Signature Card. Interest Rates and Interest Charges Annual Percentage Rate Introductory APR for the first 12 months that your account is open. (APR) for Purchases 0.00% After that, your APR will be 13.99% to 23.99%, based on your creditworthiness. This APR will vary with the market based on the Prime Rate. APR for Balance Transfers 0.00% Introductory APR for the first 12 months that your account is open. After that, your APR will be 13.99% to 23.99%, based on your creditworthiness. This APR will vary with the market based on the Prime Rate. APR for Cash Advances 25.25%. This APR will vary with the market based on the Prime Rate. Penalty APR None Paying Interest Your due date is at least 21 calendar days after the close of each billing cycle. We will not charge you any interest on purchases if you pay your entire balance by the due date each month. We will begin charging interest on cash advances and balance transfers on the transaction date. Minimum Interest Charge If you are charged interest, the charge will be no less than $1.75. For Credit Card Tips from To learn more about factors to consider when applying for or using a credit card, visit the the Consumer Financial website of the Consumer Financial Protection Bureau at Protection Bureau http://www.consumerfinance.gov/learnmore. -

All in Credit Union Terms and Conditions
ALL IN CREDIT UNION 238 VIRGINIA AVENUE, P.O. DRAWER 8 DALEVILLE, ALABAMA 36332 Phone: 334.598.4411 AGREEMENTS AND DISCLOSURES THESE AGREEMENTS AND DISCLOSURES CONTAIN IMPORTANT MEMBERSHIP INFORMATION, NECESSARY TRUTH-IN-SAVINGS ACCOUNT DISCLOSURES, ELECTRONIC SERVICES AGREEMENT AND DISCLOSURES, FUNDS AVAILABILITY POLICY, AND PRIVACY POLICY DISCLOSURE, TOGETHER WITH ANY OTHER RELATED DOCUMENT AND/OR OTHER AGREEMENTS AND DISCLOSURES ALL OF WHICH, TO THE EXTENT APPLICABLE, ARE INCORPORATED INTO THIS AGREEMENT BY REFERENCE. IT IS YOUR RESPONSIBILITY TO READ THESE AGREEMENTS AND DISCLOSURES CAREFULLY AND NOTIFY US IMMEDIATELY IF ANY PROVISION IS UNCLEAR. IMPORTANT ACCOUNT OPENING INFORMATION – Federal law requires us to obtain sufficient information to verify Your identity. You may be asked several questions and to provide one or more forms of identification to fulfill this requirement. In some instances, We may use outside sources to confirm the information provided. The information You provide is protected by our privacy policy and federal law. Throughout these Agreements and Disclosures, the references to “We”, “Us”, “Our” and “Credit Union” mean ALL IN CREDIT UNION. The words “You” and “Your” mean each person applying for and/or using any of the services described herein. “Account” means any account or accounts established for You as set forth in these Agreements and Disclosures. The word “Card” means any ALL IN CREDIT UNION Debit Card/MasterCard issued to You by Us and any duplicates or renewals We may issue. MEMBERSHIP To apply for membership with ALL IN CREDIT UNION, You must complete, sign and return an application for membership. Your signature on Your application for membership informs the Credit Union that You would like to join the Credit Union and that You agree to conform to the Credit Union’s Bylaws and Amendments and subscribe for at least one share. -

Tips to Manage Your Student Loans Handbook.Pdf
Nelnet.com | 888.486.4722 ©2014 Nelnet, Inc. All rights reserved. Nelnet is a registered service mark of Nelnet, Inc. 1 Introduction .................. The Life of a Student Loan . 3 .......... Managing Your Money . 4 ............ Set Your Financial Goals . 6 ........... Budget Worksheet . 7 .............. Strategies to Save Money . 8 .......... Credit Card Tips . 9 ............... 10 How to Avoid Identity Theft ......... 11 Federal Student Loan Programs .... 13 Ten Things You Should Know About Student Loans ................ 15 Student Loan Repayment Plans ...... 16 Income-Driven Repayment Plans .... 18 Loan Repayment Estimates ........ 20 Create Your Nelnet.com Account .... 23 ..... 24 Make a Payment on Nelnet.com .... 25 What to Know About Paying Extra How to Avoid Delinquency and Default . 27 on Your Student Loan ........... Trouble Making Payments? ........ Four Easy Ways to Avoid Delinquency . 28 or Default on Your Student Loan Resume Guidelines and Standards..... 29 Interview Guidelines and Standards ..... 31 Student Loan Terms to Know ... 33 ....... Get Ready for Repayment . 35 ......... Servicer Contact Info . 44 ........... Entrance and Exit Counseling . 45 ....... 888.486.4722 . 46 Nelnet.com | LIVE LIFE SMART GUIDE :: 2 INTRODUCTION Congratulations! A higher education can significantly boost your earning potential. However, balancing your educational goals with good borrowing decisions is the key to a healthy financial future. With careful financial planning and a completed education, you’ll be well on your way to success. When you borrow Stafford Loans, you have six months (your grace period) from the time you graduate or drop below half-time student status until you start making payments on your federal student loans (repayment). When this happens, we’re one of the federal student loan servicers who may process your payments and answer your questions on behalf of the Department of Education. -

Money Math for Teens: Before You Choose a Credit Card
Money Math for Teens Before You Choose a Credit Card This Money Math for Teens lesson is part of a series created by Generation Money, a multimedia financial literacy initiative of the FINRA Investor Education Foundation, Channel One News and America Saves. Special thanks to Rudy Gawron for preparing the lesson and to Jill Sulam of Transformations Editing LLC for editorial guidance. Money Math for Teens. © Copyright 2014 by the FINRA Investor Education Foundation or FINRA Foundation. Reproduction for nonprofit, educational purposes is permitted and encouraged. All rights reserved. Before You Choose a Credit Card Lesson Plan OBJECTIVE To inform students about the subtle and not-so-subtle differences between credit cards and how to choose the right card for their individual needs. Students will be able to: 00 Identify different types of credit cards 00 Evaluate the differences between credit offers 00 Understand typical fees associated with credit accounts 00 Calculate the minimum monthly payment required on a credit card 00 Determine how to avoid finance charges. TEACHING MATERIALS 00 Lesson plan with answer key for student assessment 00 Before You Choose a Credit Card student handout 00 Student assessment worksheet LESSON ACTIVITY 1. Informally assess students’ prior knowledge through a group discussion. Ask: • How many different types of credit cards are there? • What horror stories have you heard about credit cards? • What kinds of behavior do you think could lead to financial trouble? • Are you aware of rewards programs? What kinds -

Consumer Fee Schedule Effective July 1, 2020
Consumer Fee Schedule Effective July 1, 2020 ATMs – Empower Network Transaction No Fee Surcharge No Fee (when using an Empower Debit and/or Credit Card at these locations) ATMs – Allpoint Network Transaction 10 free per month, then $2.00 per Empower Debit Card transaction Surcharge (Allpoint Network) No surcharge for Empower Debit Card Surcharge (Southern Tier) No surcharge fee (Select credit union locations – per Cooperative Agreement) ATMs-Out-of-Network & Point of Sale PIN-Based Debit Transactions Transaction 10 free per month, then $2.00 per Empower Debit Card transaction Surcharge Non-Empower/Non-Allpoint ATMs may assess a surcharge. Owners of the ATMs assess these surcharges. Checking Account (Share Draft) Checking No monthly fee Checking Plus+ $5.00 per month when average daily balance drops below $1,000 Share Draft Check Printing Prices vary Stop Payment (Including ACH) $15.00 each Courtesy Pay/Non-Sufficient Funds* up to $25.00 each presentment (Including ACH, ATM, or Debit Card transactions)* Check Protest/Collection Item $25.00 each *Opt-in required to receive Courtesy Pay on ATM or Debit Card transactions. If an Opt-in Form is not on file, the transaction will be declined when funds are unavailable in the account at time of authorization request. For more information and complete disclosures, visit: https://www.empowerfcu.com/ courtesypay +Those with an Empower Checking Plus account have been grandfathered. This account type is no longer available. Credit and/or Debit Replacement Card $5.00 each Expedited Card/Draft Retrieval $25.00 each Late Payment up to $25.00 each Miscellaneous Products & Services Safe Deposit Boxes (Limited availability) Prices vary Money Order/Official Check $1.00 each (Official Check - no fee if payable to account holder only. -

How Can Payments Modernization Benefit Canadian Businesses? Evaluating the Cost of Payments Processing
How can payments modernization benefit Canadian businesses? Evaluating the cost of payments processing Contents n Executive summary ........................................................2 n How are payments changing today to meet the needs of tomorrow? .................................................................4 n How do inefficiencies in current payments processing impact the business community in Canada? .....................8 n How is Canada responding to required changes in the payments infrastructure? ........................................16 n How can businesses in Canada benefit from a new payments infrastructure? .......................................18 n Key takeaways ..............................................................20 n Appendices ..................................................................22 How can payments modernization benefit Canadian businesses? Evaluating the cost of payments processing | 1 Executive summary This study focuses on identifying how the current payments ecosystem affects Canadian businesses through process inefficiencies, which ultimately result in increased operational costs. It also examines the spectrum of potential solutions that may create efficiency gains to small and medium enterprises (SMEs) and large corporates in the context of payments modernization efforts globally with a focus on Canada. The case for a modernized payments infrastructure in Canada is strong and has the potential to deliver significant benefits to small and medium enterprises (SMEs) as well as larger -

We're Making Some Changes to Your Rogers Bank Mastercard Account To
® WE’RE MAKING SOME CHANGES TO YOUR ROGERS BANKTM MASTERCARD ACCOUNT TO SERVE YOU BETTER When times are uncertain, the day-to-day pressures of managing personal finances can be very stressful. To provide you with more financial options, we’re introducing Rogers Bank Equal Payment Plans on a promotional basis. Whether it’s a planned purchase, or an unexpected expense, Equal Payment Plans will make it easy for you to turn larger purchases into monthly payments that fit within your budget. Attached is a summary about how Equal Payment Plans work, along with the detailed side-by-side changes to the following documents: (1) Disclosure Summary For any Rogers Bank Mastercard and (2) Rogers Bank Cardholder Agreement. These changes will take eFFect on January 12, 2021. Your use of the Account or your Card after January 12, 2021 will mean that you have accepted these changes. For residents of Quebec, if you do not agree with this change, you may terminate your Account with us by February 12, 2021 without cost or penalty after any remaining balance is paid off. All Equal Payment Plan offer details - including eligibility, term length and interest rates - will be provided to you, and your express consent will be required, at the time the Equal Payment Plan offer is made to you. What is an EQual Payment Plan? Typically, when you make a large purchase on your credit card, you pay the regular annual interest rate for Purchases on any amount of the purchase that you don’t pay off right away. With an Equal Payment Plan, you can divide the purchase into small equal payments over a fixed period of time, and at a lower (promotional) interest rate. -

Agreements and Disclosures Agreements and Table of Contents
Agreements and Disclosures Agreements and Table of Contents Disclosures for Agreements & Disclosures Page No. A. General Notices ....................................................................... 1 Denial of Services ....................................................... 1 Termination of Account ................................................ 1 Death of an Account Owner ......................................... 1 Obtaining Information .................................................. 1 Account and Credit Information .................................... 1 Application for Membership ......................................... 1 Welcome to SECU! USA Patriot Act ........................................................... 2 Account Ownership ..................................................... 2 Founded in Baltimore in 1951, SECU is the largest state-chartered Custodial Savings Account ........................................... 2 credit union in Maryland. As a not-for-profit institution governed by Payable on Death ........................................................ 2 a Board of Directors, elected by members like you, we’re different Minor Account ............................................................. 2 from most other financial institutions. Part of that difference is lower Estate Accounts .......................................................... 2 rates on credit cards, mortgages, and other loans and higher rates Power of Attorney ........................................................ 3 on deposits. Credit Union’s Attorneys’ -

Immediate Funds Transfer As a General Purpose Means of Payment Bruce J
Immediate Funds Transfer as a General Purpose Means of Payment Bruce J. Summers and Kirstin E. Wells1 January 2011 Introduction In a modern economy, transactions for goods and services as well as transactions in financial markets are paid for by transferring money held in accounts with banks. For the better part of the last century in the United States, most noncash payments were made with the paper check, a payment instrument that met most needs for payment services. Since the mid-1990s, use of the paper check has been in decline (Gerdes, 2008), a development that reflects technological advances and innovations by providers of payment services in response to needs for new and different payment instruments. Today, individuals, businesses, and governments can choose from a variety of payment instruments, each of which is designed to meet the specific needs for attributes such as certainty, speed, security, convenience, and cost (Foster et al., 2010). The most advanced means of transferring money between bank accounts is immediate funds transfer (IFT), which allows senders to pay receivers electronically in a highly convenient, certain and secure manner, with no or minimal delay in the receivers’ receipt and use of funds. Today in the U.S., most IFT payments are limited to large-value business payments, interbank transfers, and specialized financial market transactions that in total account for a small proportion of the total number of payments made. Industry data, however, indicate that the popularity of IFT for general purpose payments is growing (BAI, 2010). To date, most general purpose IFT payments are made on systems operated by nonbanks, the most recognized being PayPal.2 A notable development in a number of countries around the world, and also to a limited extent in the U.S., is broader use of IFT for general purpose payments. -

Direct Federal Regulation of Stationary Sources Under the Clean Air Act
University of Chicago Law School Chicago Unbound Journal Articles Faculty Scholarship 1980 Direct Federal Regulation of Stationary Sources Under the Clean Air Act David P. Currie Follow this and additional works at: https://chicagounbound.uchicago.edu/journal_articles Part of the Law Commons Recommended Citation David P. Currie, "Direct Federal Regulation of Stationary Sources Under the Clean Air Act," 128 University of Pennsylvania Law Review 1389 (1980). This Article is brought to you for free and open access by the Faculty Scholarship at Chicago Unbound. It has been accepted for inclusion in Journal Articles by an authorized administrator of Chicago Unbound. For more information, please contact [email protected]. 1980] DIRECT FEDERAL REGULATION OF STATIONARY SOURCES UNDER THE CLEAN AIR ACT DAVID P. CuRRIEt TABLE OF CONTENTS I. NEw-SOURCE PERFORMANCE STANDARDS ............... 1391 A. "New" Sources ................................. 1391 1. The Relevant Date ........................... 1392 2. The Commencement of Construction ........... 1393 a. Planning ................................. 1393 b. Contracting............................. 1394 c. Site Preparationand Ancillary Equipment .... 1395 3. M odification ................................ 1396 4. The "Bubble" Concept ....................... 1397 B. Other Threshold Requirements .................. 1401 1. Significant Contribution ...................... 1401 2. Mandatory Standards and Major Sources ........ 1404 3. Grain Elevators and Federal Sources ............ 1406 C. The Criteria -

STCU Mastercard Credit Card Agreement
hereunder shall otherwise remain in full force and effect until you have paid us all sums due us under this Agreement and returned all Cards. STCU Mastercard® Credit Card Agreement 4. MONTHLY PAYMENT. We will mail you a statement every month if your Account has a balance. You agree that you will pay each month This Credit Card Agreement (Agreement) and the Account Disclosures not less than the minimum monthly payment on or before the accompanying this Agreement will govern your STCU Mastercard scheduled monthly due date. The minimum monthly payment will be Credit Card and account issued by Spokane Teachers Credit Union 2.0% of your outstanding balance (“New Balance”) or $25.00, (“STCU”). In this Agreement the words “you,” “your,” “yours”, whichever is greater. If your outstanding balance is $25.00 or less, “applicant,” and “Borrowers” mean any person who signs the you agree to pay the balance in full. You may pay in full for all your application for this Account, any joint obligor, guarantor, authorized Account balances each month, or you may repay in monthly user, or the person whose name is embossed on the Card. The words installments. We can accept late payments or partial payments, or “we,” “us,” “our,” and “Credit Union” mean Spokane Teachers Credit checks, drafts or money orders marked “payment in full” without Union. The word “Card” means any one or more credit cards issued prejudice to our rights under this Agreement, which are hereby under this Account. If you sign an application for this Account or explicitly reserved. A credit posting from a merchant or reversal of sign or use any Card or PlN, or allow others to use the Card or fees do not constitute a minimum payment.