Linux Tutorial
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

A Java Implementation of a Portable Desktop Manager Scott .J Griswold University of North Florida
UNF Digital Commons UNF Graduate Theses and Dissertations Student Scholarship 1998 A Java Implementation of a Portable Desktop Manager Scott .J Griswold University of North Florida Suggested Citation Griswold, Scott .,J "A Java Implementation of a Portable Desktop Manager" (1998). UNF Graduate Theses and Dissertations. 95. https://digitalcommons.unf.edu/etd/95 This Master's Thesis is brought to you for free and open access by the Student Scholarship at UNF Digital Commons. It has been accepted for inclusion in UNF Graduate Theses and Dissertations by an authorized administrator of UNF Digital Commons. For more information, please contact Digital Projects. © 1998 All Rights Reserved A JAVA IMPLEMENTATION OF A PORTABLE DESKTOP MANAGER by Scott J. Griswold A thesis submitted to the Department of Computer and Information Sciences in partial fulfillment of the requirements for the degree of Master of Science in Computer and Information Sciences UNIVERSITY OF NORTH FLORIDA DEPARTMENT OF COMPUTER AND INFORMATION SCIENCES April, 1998 The thesis "A Java Implementation of a Portable Desktop Manager" submitted by Scott J. Griswold in partial fulfillment of the requirements for the degree of Master of Science in Computer and Information Sciences has been ee Date APpr Signature Deleted Dr. Ralph Butler Thesis Advisor and Committee Chairperson Signature Deleted Dr. Yap S. Chua Signature Deleted Accepted for the Department of Computer and Information Sciences Signature Deleted i/2-{/1~ Dr. Charles N. Winton Chairperson of the Department Accepted for the College of Computing Sciences and E Signature Deleted Dr. Charles N. Winton Acting Dean of the College Accepted for the University: Signature Deleted Dr. -

Part II, Window Managers and Desktop Environments
Part II Window Managers and Desktop Environments The window manager is responsible for managing application windows and application- independent behavior, such as pop-up menus appearing in the background. The window manager manages the placement, borders, and decorations of all windows, and is responsible for the look and feel of your particular X session. Desktop environments typically include an integrated window manager, some sort of control panel, applications, and a consistent look and feel across applications. The chapters in Part II, Window Managers and Desktop Environments, are: Overview This chapter provides a conceptual introduction to window managers and desktop environments and briefly surveys some of the many window managers and desktop environments available for Linux. FVWM FVWM is a traditional window manager for Linux systems. It is now into its second major version, FVWM2. Window Maker Window Maker is an elegant X11 window manager designed to give integration support to GNUstep-based applications. It emulates the look and feel of OpenStep, the NeXTSTEP GUI. Enlightenment Enlightenment, often shortened to just E, may be the most elaborate and bizarre window manager available. Enlightenment’s motto, “time to rethink everything,” provides a good indication of the uniqueness and flashiness behind Enlightenment. Using GNOME GNOME, which stands for GNU Network Object Model Environment, is a freely available desktop environment that can be used with any of several window managers, including Enlightenment and Sawfish. Using KDE KDE, the K Desktop Environment, is another freely available desktop environment. KDE includes an assortment of games and utilities, as well as an integrated suite of office productivity applications.. -

Easy Slackware
1 Создание легкой системы на базе Slackware I - Введение Slackware пользуется заслуженной популярностью как классический linux дистрибутив, и поговорка "кто знает Red Hat тот знает только Red Hat, кто знает Slackware тот знает linux" несмотря на явный снобизм поклонников "бога Патре га" все же имеет под собой основания. Одним из преимуществ Slackware является возможность простого создания на ее основе практически любой системы, в том числе быстрой и легкой десктопной, о чем далее и пойдет речь. Есть дис трибутивы, клоны Slackware, созданные именно с этой целью, типа Аbsolute, но все же лучше создавать систему под себя, с максимальным учетом именно своих потребностей, и Slackware пожалуй как никакой другой дистрибутив подходит именно для этой цели. Легкость и быстрота системы определяется выбором WM (DM) , набором программ и оптимизацией программ и системы в целом. Первое исключает KDE, Gnome, даже новые версии XFCЕ, остается разве что LXDE, но набор программ в нем совершенно не устраивает. Оптимизация наиболее часто используемых про грамм и нескольких базовых системных пакетов осуществляется их сборкой из сорцов компилятором, оптимизированным именно под Ваш комп, причем каж дая программа конфигурируется исходя из Ваших потребностей к ее возможно стям. Оптимизация системы в целом осуществляется ее настройкой согласно спе цифическим требованиям к десктопу. Такой подход был выбран по банальной причине, возиться с gentoo нет ни какого желания, комп все таки создан для того чтобы им пользоваться, а не для компиляции программ, в тоже время у каждого есть минимальный набор из не большого количества наиболее часто используемых программ, на которые стоит потратить некоторое, не такое уж большое, время, чтобы довести их до ума. Кро ме того, такой подход позволяет иметь самые свежие версии наиболее часто ис пользуемых программ. -

Introduction to the Enlightenment Foundation Libraries
Introduction to the Enlightenment foundation libraries. An overview of EFL Kostis Kapelonis Introduction to the Enlightenment foundation libraries.: An overview of EFL Kostis Kapelonis Abstract The target audience of this document are UNIX programmers who are interested in the Enlightenment Foundation Libraries (EFL). You must already know C programming. You will not however learn how to program using the EFL. Instead, you will learn why you should program with the EFL. If you ever wanted to evaluate the EFL but did not see any advantages over previous graphic libraries then this document is for you! Table of Contents 1. Introduction ............................................................................................................................1 A little History ...................................................................................................................1 Related documentation ......................................................................................................... 2 Obtaining the EFL libraries ................................................................................................... 2 2. The EFL structure .................................................................................................................... 4 Organization of the Libraries ................................................................................................. 4 Brief description of each EFL library ...................................................................................... 5 3. -

An Introduction to the X Window System Introduction to X's Anatomy
An Introduction to the X Window System Robert Lupton This is a limited and partisan introduction to ‘The X Window System’, which is widely but improperly known as X-windows, specifically to version 11 (‘X11’). The intention of the X-project has been to provide ‘tools not rules’, which allows their basic system to appear in a very large number of confusing guises. This document assumes that you are using the configuration that I set up at Peyton Hall † There are helpful manual entries under X and Xserver, as well as for individual utilities such as xterm. You may need to add /usr/princeton/X11/man to your MANPATH to read the X manpages. This is the first draft of this document, so I’d be very grateful for any comments or criticisms. Introduction to X’s Anatomy X consists of three parts: The server The part that knows about the hardware and how to draw lines and write characters. The Clients Such things as terminal emulators, dvi previewers, and clocks and The Window Manager A programme which handles negotiations between the different clients as they fight for screen space, colours, and sunlight. Another fundamental X-concept is that of resources, which is how X describes any- thing that a client might want to specify; common examples would be fonts, colours (both foreground and background), and position on the screen. Keys X can, and usually does, use a number of special keys. You are familiar with the way that <shift>a and <ctrl>a are different from a; in X this sensitivity extends to things like mouse buttons that you might not normally think of as case-sensitive. -

Présentation Ligne De Commande
Kit de survie en lignes de commandes ... pour les nuls. Ceci est la version légèrement corrigée, étendue et complétée de la présentation du jeudi 2 juin 2018. Pourquoi la ligne de commande ? La ligne de commande est une chose qui a, pour des raisons marketting et en lien avec la massification de l'usage de l'outil informatique, peu à peu disparue alors qu'elle faisait partie intégrante des ordinateurs dans les années 80 et jusqu'en 1995 pour le grand public. Actuellement, la ligne de commande est perçue par les néophytes comme un objet de toute puissance ou de diabolisation. Les stéréotypes véhiculés par les media traditionnels associent souvent la ligne de commande, et in extenso le terminal, à un outil de hacker. Alors que cela a été pendant longtemps le quotidien de beaucoup d'utilisateurs. Posons un peu de vocabulaire : Linux est un noyau c'est à dire un binaire qui communique avec le matériel. Autour de lui est le système GNU (pour GNU is Not Unix). Le système GNU a été pensé dans les années 80 comme étant une alternative Libre au système (gratuit) mais propriétaire Unix. Dans les années 80, à la préhistoire informatique, les systèmes d'ordinateurs n'avaient pour ainsi dire pas d'interface graphique (et encore moins de souris) : un noyau, un interpréteur de commande (shell) et quelques utilitaires suffisaient à faire un ordinateur fonctionnel. Ici le système Microsoft Disk Operating System fonctionnant avec les fichier : msdos.sys et io.sys (l'équivalent du noyau), config.sys et autoexec.bat, à partir de là l'interpréteur de commande (ou shell) : COMMAND.COM s'exécute et affiche l'image précédente. -

System Administration
System Administration Varian NMR Spectrometer Systems With VNMR 6.1C Software Pub. No. 01-999166-00, Rev. C0503 System Administration Varian NMR Spectrometer Systems With VNMR 6.1C Software Pub. No. 01-999166-00, Rev. C0503 Revision history: A0800 – Initial release for VNMR 6.1C A1001 – Corrected errors on pg 120, general edit B0202 – Updated AutoTest B0602 – Added additional Autotest sections including VNMRJ update B1002 – Updated Solaris patch information and revised section 21.7, Autotest C0503 – Add additional Autotest sections including cryogenic probes Applicability: Varian NMR spectrometer systems with Sun workstations running Solaris 2.x and VNMR 6.1C software By Rolf Kyburz ([email protected]) Varian International AG, Zug, Switzerland, and Gerald Simon ([email protected]) Varian GmbH, Darmstadt, Germany Additional contributions by Frits Vosman, Dan Iverson, Evan Williams, George Gray, Steve Cheatham Technical writer: Mike Miller Technical editor: Dan Steele Copyright 2001, 2002, 2003 by Varian, Inc., NMR Systems 3120 Hansen Way, Palo Alto, California 94304 1-800-356-4437 http://www.varianinc.com All rights reserved. Printed in the United States. The information in this document has been carefully checked and is believed to be entirely reliable. However, no responsibility is assumed for inaccuracies. Statements in this document are not intended to create any warranty, expressed or implied. Specifications and performance characteristics of the software described in this manual may be changed at any time without notice. Varian reserves the right to make changes in any products herein to improve reliability, function, or design. Varian does not assume any liability arising out of the application or use of any product or circuit described herein; neither does it convey any license under its patent rights nor the rights of others. -

Pubtex Output 1999.12.10:0902
Solaris 8 (SPARC Platform Edition) Installation Guide Sun Microsystems, Inc. 901 San Antonio Road Palo Alto, CA 94303–4900 U.S.A. Part Number 806–0955–10 February 2000 Copyright 2000 Sun Microsystems, Inc. 901 San Antonio Road, Palo Alto, California 94303-4900 U.S.A. All rights reserved. This product or document is protected by copyright and distributed under licenses restricting its use, copying, distribution, and decompilation. No part of this product or document may be reproduced in any form by any means without prior written authorization of Sun and its licensors, if any. Third-party software, including font technology, is copyrighted and licensed from Sun suppliers. Parts of the product may be derived from Berkeley BSD systems, licensed from the University of California. UNIX is a registered trademark in the U.S. and other countries, exclusively licensed through X/Open Company, Ltd. Sun, Sun Microsystems, the Sun logo, SunOS, Sun Enterprise, Sun Enterprise Network Array, Sun Quad FastEthernet, SunSwift, SunVideo, Sun Workshop, Solaris, Solaris JumpStart, docs.sun.com, AnswerBook2, Java, JumpStart, OpenBoot, ONC, OpenWindows, PGX32, Power Management, Solstice, Solstice Enterprise Agents, ToolTalk, Ultra, Ultra Enterprise, Voyager, WebNFS, and XIL are trademarks, registered trademarks, or service marks of Sun Microsystems, Inc. in the U.S. and other countries. All SPARC trademarks are used under license and are trademarks or registered trademarks of SPARC International, Inc. in the U.S. and other countries. Products bearing SPARC trademarks are based upon an architecture developed by Sun Microsystems, Inc. Adobe, PostScript, and Display PostScript are trademarks or registered trademarks of Adobe Systems, Incorporated, which may be registered in certain jurisdictions. -

Installing Framemaker for UNIX®
Adobe ® FrameMaker ® 7.0 Installing FrameMaker for UNIX® © 2002 Adobe Systems Incorporated and its licensors. All rights reserved. Installing Adobe FrameMaker for UNIX This manual, as well as the software described in it, is furnished under license and may be used or copied only in accordance with the terms of such license. The content of this manual is furnished for informational use only, is subject to change without notice, and should not be construed as a com- mitment by Adobe Systems Incorporated. Adobe Systems Incorporated assumes no responsibility or liability for any errors or inaccuracies that may appear in this book. Except as permitted by such license, no part of this publication may be reproduced, stored in a retrieval system, or transmitted, in any form or by any means, electronic, mechanical, recording, or otherwise, without the prior written permission of Adobe Systems Incorporated. Please remember that existing artwork or images that you may want to include in your project may be protected under copyright law. The unautho- rized incorporation of such material into your new work could be a violation of the rights of the copyright owner. Please be sure to obtain any per- mission required from the copyright owner. Any references to company names in sample templates are for demonstration purposes only and are not intended to refer to any actual organization. Adobe, the Adobe logo, Acrobat, Acrobat Reader, Adobe Type Manager, ATM, Display PostScript, Distiller, Exchange, FrameMaker, InstantView, Post- Script, and SuperATM are trademarks of Adobe Systems Incorporated. The following are copyrights of their respective companies or organizations: Portions reproduced with the permission of Apple Computer, Inc. -
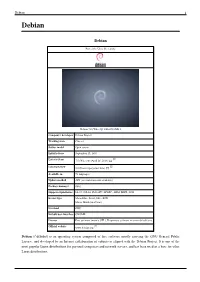
Debian 1 Debian
Debian 1 Debian Debian Part of the Unix-like family Debian 7.0 (Wheezy) with GNOME 3 Company / developer Debian Project Working state Current Source model Open-source Initial release September 15, 1993 [1] Latest release 7.5 (Wheezy) (April 26, 2014) [±] [2] Latest preview 8.0 (Jessie) (perpetual beta) [±] Available in 73 languages Update method APT (several front-ends available) Package manager dpkg Supported platforms IA-32, x86-64, PowerPC, SPARC, ARM, MIPS, S390 Kernel type Monolithic: Linux, kFreeBSD Micro: Hurd (unofficial) Userland GNU Default user interface GNOME License Free software (mainly GPL). Proprietary software in a non-default area. [3] Official website www.debian.org Debian (/ˈdɛbiən/) is an operating system composed of free software mostly carrying the GNU General Public License, and developed by an Internet collaboration of volunteers aligned with the Debian Project. It is one of the most popular Linux distributions for personal computers and network servers, and has been used as a base for other Linux distributions. Debian 2 Debian was announced in 1993 by Ian Murdock, and the first stable release was made in 1996. The development is carried out by a team of volunteers guided by a project leader and three foundational documents. New distributions are updated continually and the next candidate is released after a time-based freeze. As one of the earliest distributions in Linux's history, Debian was envisioned to be developed openly in the spirit of Linux and GNU. This vision drew the attention and support of the Free Software Foundation, who sponsored the project for the first part of its life. -

No Slide Title
Embedded Systems Class overview, Embedded systems introduction, Raspberry Pi, Linux OS, X-windows, Window manager, Desktop Environment Prof. Myung-Eui Lee (A-405) [email protected] Embedded Systems 1-1 KUT Embedded Systems Class Overview ⚫ Embedded Systems Class Operations » Past : 3 (credit) -2 (lecture) -2 (practice) » Now : 3 (credit) -1 (lecture) -1 (design) -2 (practice) » Future : 4 (credit) -2 (lecture) -2 (design) -0 (practice) ⚫ PBL : Problem or Project Based Learning » Problem : 4 problems » Project : 2 projects ⚫ 4 hours Class » 1 hour (lecture) + 1 hour (lecture or design) + 2 hours (practice) ▪ 1 hour (lecture) + 1 hour (lecture or design) : me ▪ 2 hours (practice) : Ph.D Park ⚫ Target Board : Raspberry Pi 3 » ARM + Linux Embedded Systems 1-2 KUT Embedded Systems Class Overview ⚫ Class Grade : » Mid Term Exam : 15 % [30 %] » Final Term Exam : 15 % [30 %] » Peer Evaluation : 10 % (Project #1 : 5% + Project #2 : 5%) » Project #1 Evaluation : 10 % » Project #2 Evaluation : 15 % » Experimental Lab. : 20 % [20 %] » Class Participation : 15 % [20 %] » Social Problem (Project #2) Optional : +5 % ⚫ Lecture Notes: http://microcom.koreatech.ac.kr Embedded Systems 1-3 KUT Embedded Systems ⚫ Definition of embedded system » Embedded system = H/W + S/W ▪ H/W = CPU + Memory + I/O ▪ S/W = Device driver + OS (or non OS) + Application program » Any electronic system that uses a CPU chip, but that is not a general-purpose workstation, desktop or laptop computer. » In embedded systems, the software typically resides in memory device, such as a flash memory or ROM chip. In contrast to a general-purpose computer that loads its programs into RAM each time. » Sometimes, single board and rack mounted general-purpose computers are called "embedded computers" if used to control. -
Towards a New Enlightenment? a Transcendent Decade
Towards a New Enlightenment? A Transcendent Decade Preface This book, Towards a New Enlightenment? A Transcendent Decade, is the eleventh in an annual series that BBVA’s OpenMind project dedicates to disseminating greater knowledge on the key questions of our time. We began this series in 2008, with the first book, Frontiers of Knowledge, that celebrated the launching of the prizes of the same name awarded annually by the BBVA Foundation. Since then, these awards have achieved worldwide renown. In that first book, over twenty major scientists and experts used language accessible to the general public to rigorously review the most relevant recent advances and perspectives in the different scientific and artistic fields recognized by those prizes. Since then, we have published a new book each year, always following the same model: collections of articles by key figures in their respective fields that address different aspects or perspectives on the fundamental questions that affect our lives and determine our futu- re: from globalization to the impact of exponential technologies, and on to include today’s major ethical problems, the evolution of business in the digital era, and the future of Europe. The excellent reaction to the first books in this series led us, in 2011, to create OpenMind (www.bbvaopenmind.com), an online community for debate and the dissemination of knowle- dge. Since then, OpenMind has thrived, and today it addresses a broad spectrum of scientific, technological, social, and humanistic subjects in different formats, including our books, as well as articles, posts, reportage, infographics, videos, and podcasts, with a growing focus on audiovisual materials.