The Institution of Electronics and Telecommunication Engineers
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

An Efficient Way for Statistical Review Using the Rshiny Application
PhUSE EU Connect 2018 Paper AD03 An Efficient Way for Statistical Review Using the RShiny Application Adarsh Nagare, Cytel, Pune, India Sameer Bamnote, Cytel, Pune, India ABSTRACT Statisticians often need to review critical reports before study submissions. Many reports include outputs based on statistical testing or model-based analysis. To ensure the accuracy of these reports, most of the time the Statistician needs to writes independent code. In case of tight timelines, it may not be feasible and quality of review can be impacted. To address this we describe use of an application that can save time for the Statistician. This application was created using open-source software R and Shiny, providing an efficient, time saving solution for review of critical statistical outputs without the need for extensive code writing. The aim is to review results for t-tests, AN(C)OVA, their non-parametric alternatives and model-based analysis which are performed in SAS®. User has flexibility to provide input data in excel, csv or SAS format. User can select the statistical test (or specify the model) as per requirement and statistical outputs will be just a click away. This paper demonstrates the application with a variety of illustrations. INTRODUCTION The authors work with clients from clinical research and FMCG field as Statisticians. As a part of the role we have to deal with programmers routinely to do the desired work (i.e. Tables, Listings and Figures) required for various reports. Most of the time, as a Statistician we need to validate the results for modelling or statistical tests or cross check them by writing independent code to ensure accuracy of the results, prior to the submissions. -

HP Digital Signage Display
HP LD4220tm and LD4720tm Digital Signage Touch Displays User Guide © 2011 Hewlett-Packard Development Company, L.P. The information contained herein is subject to change without notice. The only warranties for HP products and services are set forth in the express warranty statements accompanying such products and services. Nothing herein should be construed as constituting an additional warranty. HP shall not be liable for technical or editorial errors or omissions contained herein. This document contains proprietary information that is protected by copyright. No part of this document may be photocopied, reproduced, or translated to another language without the prior written consent of Hewlett-Packard Company. Microsoft®, Windows®, and Windows Vista™ are either trademarks or registered trademarks of Microsoft Corporation in the United States and/or other countries. First Edition (September 2011) Document Part Number: 626998-001 About this guide This guide provides information on setting up the display, installing drivers, using the On-Screen Display menu, troubleshooting, and technical specifications. WARNING! Text set off in this manner indicates that failure to follow directions could result in bodily harm or loss of life. CAUTION: Text set off in this manner indicates that failure to follow directions could result in damage to equipment or loss of information. NOTE: Text set off in this manner provides important supplemental information. ENWW iii iv About this guide ENWW Table of contents 1 Product features ............................................................................................................................................ -

Volume8, Issue11(1) November 2018
International Journal of Management, IT & Engineering Vol. 8 Issue 11(1), November 2018, ISSN: 2249-0558 Impact Factor: 7.119 Journal Homepage: http://www.ijmra.us, Email: [email protected] Double-Blind Peer Reviewed Refereed Open Access International Journal - Included in the International Serial Directories Indexed & Listed at: Ulrich's Periodicals Directory ©, U.S.A., Open J-Gage as well as in Cabell’s Directories of Publishing Opportunities, U.S.A Industrial Unrest and National Development (A Study of Selected Non-Union-Dominated Manufacturing Firms in South East Nigeria) OKEKE, MARCEL CHINEMERE (PhD) Abstract This study investigated the effect of industrial unrest on national development by studying selected non-union dominated manufacturing firms in South East Nigeria. It adopted survey research design and collected data from primary sources with structured questionnaire. Relevant literature was reviewed based on conceptual, theoretical, and empirical frameworks. The population was 509 comprising managers and employees selected purposively through stratified random method from the five states. The study used complete enumeration Four hundred and thirteen (413) out of the 509 copies of the questionnaire distributed were correctly completed, returned and used for the analysis indicating a response rate of 81%. Data were presented with tables and research questions were presented with statistically weighted means and standard deviation applied to the Likert scale items. Two hypotheses were formulated and tested with t-test statistic for difference in two means at 0.05 level of significance and 411 degrees of freedom. The results indicated that the managers and workers admitted that the items relating to the causes of industrial unrest were prevalent in the society. -

Download Slide (PDF Document)
When Django is too bloated Specialized Web-Applications with Werkzeug EuroPython 2017 – Rimini, Italy Niklas Meinzer @NiklasMM Gotthard Base Tunnel Photographer: Patrick Neumann Python is amazing for web developers! ● Bottle ● BlueBream ● CherryPy ● CubicWeb ● Grok ● Nagare ● Pyjs ● Pylons ● TACTIC ● Tornado ● TurboGears ● web2py ● Webware ● Zope 2 Why would I want to use less? ● Learn how stuff works Why would I want to use less? ● Avoid over-engineering – Wastes time and resources – Makes updates harder – It’s a security risk. Why would I want to use less? ● You want to do something very specific ● Plan, manage and document chemotherapy treatments ● Built with modern web technology ● Used by hospitals in three European countries Patient Data Lab Data HL7 REST Pharmacy System Database Printers Werkzeug = German for “tool” ● Developed by pocoo team @ pocoo.org – Flask, Sphinx, Jinja2 ● A “WSGI utility” ● Very lightweight ● No ORM, No templating engine, etc ● The basis of Flask and others Werkzeug Features Overview ● WSGI – WSGI 1.0 compatible, WSGI Helpers ● Wrapping of requests and responses ● HTTP Utilities – Header processing, form data parsing, cookies ● Unicode support ● URL routing system ● Testing tools – Testclient, Environment builder ● Interactive Debugger in the Browser A simple Application A simple Application URL Routing Middlewares ● Separate parts of the Application as wsgi apps ● Combine as needed Request Static files DB Part of Application conn with DB access User Dispatcher auth Part of Application without DB access Response HTTP Utilities ● Work with HTTP dates ● Read and dump cookies ● Parse form data Using the test client Using the test client - pytest fixtures Using the test client - pytest fixtures Interactive debugger in the Browser Endless possibilities ● Connect to a database with SQLalchemy ● Use Jinja2 to render documents ● Use Celery to schedule asynchronous tasks ● Talk to 3rd party APIs with requests ● Make syscalls ● Remote control a robot to perform tasks at home Thank you! @NiklasMM NiklasMM Photographer: Patrick Neumann. -

News Bulletin April, May and June 2017 Wishing
NEWS BULLETIN APRIL, MAY AND JUNE 2017 WISHING YOU ALL A VERY HAPPY RAMNAVAMI, BUDDHA PURNIMA & RAMJAN EID ! DIPA KARMAKAR CONFERRED WITH PADMA SHRI AWARD 2017 Indian trailblazing gymnast Dipa Karmakar on 13th April 2017 (Thursday) received the coveted Padma Shri Award from President Pranab Mukherjee in the national capital. Dipa Karmakar, hailing from Agartala, missed the bronze medal by 0.150 points as American gymnast Simone Biles won her third gold medal at the Rio Olympics last year. The 23-year- old had created history when she became the first Indian gymnast to enter the final on her debut at the quadrennial multi- discipline games after finishing eighth in the qualifying round. She had initially come to spotlight after winning a bronze medal at the 2014 Commonwealth Games in Glasgow, thus becoming the first Indian female gymnast to achieve the feat. Prime Minister Narendra Modi and others applauded gymnast Dipa Karmakar, who underwent knee surgery recently, as she is assisted by an officer to receive Padma Shri from President Pranab Mukherjee. Dipa’s parents Mrs. Gauri and Mr. Dulal Karmakar and her coach Mr. B. S. Nandi were also present during the ceremony. ART: R. V. LOKHANDE SAI GYMNASTICS COACH TRANSFERRED Mr. Ramakrishna V. Lokhande SAI Gymnastics Coach, who was posted under SAI Day Boarding Scheme (DBS) at Muktangan English School Pune since 1997, is hereby transferred to SAI STC University Complex Aurangabad. Mr. Lokhande joined at his new place of posting on 17th April 2017. He produced National Champions and International gymnasts’ i. e. Rucha Divekar and Roma Joglekar from Day Boarding Scheme (DBS) of SAI adopted Muktangan English School Pune. -

Graphics Library Display Drivers
Application Report SPMA039A–December 2011–Revised July 2013 Stellaris® Graphics Library Display Drivers DaveWilson ABSTRACT The Stellaris Graphics Library (grlib) offers a compact yet powerful collection of graphics functions allowing the development of compelling user interfaces on small monochrome or color displays attached to Stellaris microcontrollers. This application report describes how to support a new display device in the Stellaris Graphics Library. Contents 1 Introduction .................................................................................................................. 1 2 Library Structure ............................................................................................................ 2 3 Display Driver API .......................................................................................................... 3 4 Conclusion ................................................................................................................... 8 5 References ................................................................................................................... 9 1 Introduction The Stellaris Graphics Library (grlib) is included in all StellarisWare® firmware development packages supporting evaluation or development kits that include color displays. The Graphics library provides a collection of graphics functions that allow you to develop user interfaces on small monochrome or color displays attached to Stellaris microcontrollers. This list includes ek-lm3s3748, dk-lm3s9b96, rdk-idm, rdk- -

Static GK Capsule 2017
AC Static GK Capsule 2017 Hello Dear AC Aspirants, Here we are providing best AC Static GK Capsule2017 keeping in mind of upcoming Competitive exams which cover General Awareness section . PLS find out the links of AffairsCloud Exam Capsule and also study the AC monthly capsules + pocket capsules which cover almost all questions of GA section. All the best for upcoming Exams with regards from AC Team. AC Static GK Capsule Static GK Capsule Contents SUPERLATIVES (WORLD & INDIA) ...................................................................................................................... 2 FIRST EVER(WORLD & INDIA) .............................................................................................................................. 5 WORLD GEOGRAPHY ................................................................................................................................................ 9 INDIA GEOGRAPHY.................................................................................................................................................. 14 INDIAN POLITY ......................................................................................................................................................... 32 INDIAN CULTURE ..................................................................................................................................................... 36 SPORTS ....................................................................................................................................................................... -

Enhanced Vasculogenic Capacity Induced by 5-Fluorouracil Chemoresistance in a Gastric Cancer Cell Line
International Journal of Molecular Sciences Article Enhanced Vasculogenic Capacity Induced by 5-Fluorouracil Chemoresistance in a Gastric Cancer Cell Line Sara Peri 1,† , Alessio Biagioni 2,† , Giampaolo Versienti 2, Elena Andreucci 2 , Fabio Staderini 1 , Giuseppe Barbato 1 , Lisa Giovannelli 3 , Francesco Coratti 1, Nicola Schiavone 2,*, Fabio Cianchi 1,* , Laura Papucci 2,‡ and Lucia Magnelli 2,‡ 1 Department of Experimental and Clinical Medicine, University of Florence, Largo Brambilla, 3-50134 Firenze, Italy; sara.peri@unifi.it (S.P.); fabio.staderini@unifi.it (F.S.); [email protected] (G.B.); [email protected] (F.C.) 2 Department of Experimental and Clinical Biomedical Sciences “Mario Serio”, University of Florence, Viale G.B. Morgagni, 50-50134 Firenze, Italy; alessio.biagioni@unifi.it (A.B.); giampaolo.versienti@unifi.it (G.V.); e.andreucci@unifi.it (E.A.); laura.papucci@unifi.it (L.P.); lucia.magnelli@unifi.it (L.M.) 3 Department of Neuroscience, Psychology, Drug Research and Children’s Health, University of Florence, Viale Pieraccini, 6-50139 Firenze, Italy; lisa.giovannelli@unifi.it * Correspondence: nicola.schiavone@unifi.it (N.S.); fabio.cianchi@unifi.it (F.C.); Tel.: +39-055-275-1309 (N.S.); +39-055-412-029 (F.C.) † S.P. and A.B. contributed equally as first authors. ‡ L.P. and L.M. contributed equally as last authors. Abstract: Chemotherapy is still widely used as a coadjutant in gastric cancer when surgery is not Citation: Peri, S.; Biagioni, A.; possible or in presence of metastasis. During tumor evolution, gatekeeper mutations provide a Versienti, G.; Andreucci, E.; Staderini, selective growth advantage to a subpopulation of cancer cells that become resistant to chemotherapy. -

Self-Adapting Software for Cyberphysical Systems
Self-Adapting Software for Cyberphysical Systems Gabe Fierro Electrical Engineering and Computer Sciences University of California, Berkeley Technical Report No. UCB/EECS-2021-159 http://www2.eecs.berkeley.edu/Pubs/TechRpts/2021/EECS-2021-159.html June 2, 2021 Copyright © 2021, by the author(s). All rights reserved. Permission to make digital or hard copies of all or part of this work for personal or classroom use is granted without fee provided that copies are not made or distributed for profit or commercial advantage and that copies bear this notice and the full citation on the first page. To copy otherwise, to republish, to post on servers or to redistribute to lists, requires prior specific permission. Self-Adapting Software for Cyberphysical Systems by Gabriel Tomas Fierro A dissertation submitted in partial satisfaction of the requirements for the degree of Doctor of Philosophy in Computer Science in the Graduate Division of the University of California, Berkeley Committee in charge: Professor David E. Culler, Chair Professor Joseph M. Hellerstein Associate Professor Stefano Schiavon Spring 2021 Self-Adapting Software for Cyberphysical Systems Copyright 2021 by Gabriel Tomas Fierro 1 Abstract Self-Adapting Software for Cyberphysical Systems by Gabriel Tomas Fierro Doctor of Philosophy in Computer Science University of California, Berkeley Professor David E. Culler, Chair The built environment | the buildings, utilities, infrastructure, cities and other constructed elements of the anthropocene | is becoming increasingly digitized. The complex array of equipment, sensors and other devices in these environments constitute cyberphysical systems which produce an incredible volume of data. However, this cyberphysical data is hard to ac- cess and understand because of the extreme heterogeneity and scale of the built environment: essentially every cyberphysical system is a custom-built “one-off" collection of equipment, devices and data sources that has been continually operated, retrofitted, expanded and main- tained over years, decades and centuries. -

Touch & Display Integration
Latest Advances in Touch and Display Integration for Smartphones and Tablets PN: 507-000167-01 Rev. D Introduction Capacitive touchscreen technology has revolutionized smartphones and tablets, and is now finding its way into laptops, desktop displays, Table of Contents and all-in-one PCs. Because the market for these devices is fiercely competitive, vendors are constantly challenged to design systems Introduction................................................ 1 with high display quality, ease of navigation, high performance, compact form factors, long battery life, and low cost. Because the Integrating touch sensors into the display touchscreen plays such an influential role in the user experience, stack-up ..................................................... 2 the choice of its design can be a determining factor in a product’s ultimate success. Integrating the touch controller and display The ability to turn a display into a “touch pad” requires combining driver ICs ................................................... 4 these two previously distinct functions in seamless fashion. Historically, adding touch sensors to the display has been handled Advantages of In-Cell TDDI solutions ........ 6 in an autonomous fashion by different companies supplying different Engineering, manufacturing, and support layers in a laminated panel “stack-up” that is then assembled by a advantages ................................................ 6 separate manufacturer. Recent advances in technology have made it possible to integrate the touch sensors directly into the display, as Device design advantages ......................... 6 well as to integrate the Touch Controller and Display Driver functions in a single integrated circuit (IC). Conclusion ................................................ 7 This white paper outlines the touch and display integration technologies currently available1, including a new and innovative solution that is expected to dominate designs for new devices in the foreseeable future. -
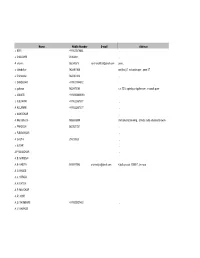
PMC Architect List
Name Mobile Number E-mail Address a BERI +919422416884 , a CHAUDHRI 26363841 , A chavan 962345513 [email protected] pune , a chimbalkar 9422401434 pushkraj 31 mukand nager , pune 37 a Chimbalkar 9422401434 , a DANDEKAR +919823084532 , a gaikwad 9822475765 s.n. 127a agtechpa rkgaikeaven , e aundh pune a KOKATE +9198906609018 , a KULKARNI +919822867377 , A KULKARNI +919822867377 , a MANGOKAR , A Muralidharan 9868943699 civil construction wing , all india radio,schoona bhawan a PARDESHI 9822621231 , a PUNGONKAR , A SHETH 250233623 , a SUTAR , A P MAHADKAR , A. B. SIRDESAI A. B. VAIDYA 9890047993 [email protected] 4,dattaprasad,1206B/7 , jm road A. G. BHADE A. J. HATKAR A. N. FATEH A. P. MAHDKAR A. R. JOSHI A. S. THOMBARE +919822027452 , A. V. GAWADE Registration No CA\77\4270 CA\94\17004 abc ca/75/708 CA/75/708 CA\97\21869 ca/2005/36683 CA/04/33802 CA/85/09380 CA\85\9380 CA\ \5298 CA/89/12033 CA\86\10340 CA\76\2678 CA/2004/33112 CA\83\7717 CA\83\7830 CA\83\ CA\81\6581 CA\00\54135 CA\77\3607 CA\86\9741 CA\ \7830 CA\75\698 CA/86/10352 CA\84\8081 Name Mobile Number E-mail Address A. V. PATIL A. W. LIMYE AARTI JAYANT JOSHI +919423305778 AASIA MEHMOOD SHAIKH 9850030183 aasia [email protected] 77 WANNORIE TWIN TOWER , BUNGLOW PUNE ABHAY ANIL PAWAR 9881120459 [email protected] 4, Sulkshana Heights, 120/11, Modern Colony, , Paud Road, Kothrud ABHAY B. SHARMA ABHAY BAPUJI DESAI ABHAY M TONDANKAR ABHAY PRADEEP BHOSALE 9422001474 rajshree.associates2k@gmail. 9/B,GIRIDARSHAN SOC., , BANER RD., AUNDH, PUNE com 07. -

Chip-On-Glass LCD Driver Technology
Chip-on-Glass LCD Driver Technology Well-proven Approach from NXP Reduces Medical System Design Costs Executive Summary 1 Executive Summary Use of LCD Displays in Medical Imaging 1 Progress in Liquid Crystal Display (LCD) medical imaging technology has The Chip-on-Glass Value Proposition 2 led to its increasing adoption for diagnostic viewing of medical images. Understanding the Conventional Surface Mount Method 2 Although LCD monitors have many advantages over cathode-ray tube The Alternative Chip-on-Glass Concept 3 monitors, cost continues to be a factor when medical professionals choose Comparing Design Effort Associated equipment. The rising overall cost of medical care adds further urgency to with COD and SMD Approaches 4 decrease equipment cost where possible. Cost Benefits of the COG Solutions versus the SMD Approach 5 For systems that require LCD displays, a typical design approach has been Example Case for Cost Comparison 6 to mount the display glass as well as the integrated circuit driving the References 9 display directly onto a printed circuit board (PCB). This approach results Acronyms 9 in a complex and area-intense PCB design. To address this issue, NXP has developed a Chip-on-Glass (COG) LCD driver approach whereby the integrated circuit mounts directly on the display glass, with the overall impact being a reduction in system cost. COG is a very reliable and well- established technology, which is often used in the automobile industry. Use of LCD Displays in Medical Imaging The need for imagery displays in medicine is vast, with technology such as digital X-ray, CT, MRI, and ultrasound just a few examples.