Prohibited Background Applications and Programs 12VPN Adobe
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Uila Supported Apps
Uila Supported Applications and Protocols updated Oct 2020 Application/Protocol Name Full Description 01net.com 01net website, a French high-tech news site. 050 plus is a Japanese embedded smartphone application dedicated to 050 plus audio-conferencing. 0zz0.com 0zz0 is an online solution to store, send and share files 10050.net China Railcom group web portal. This protocol plug-in classifies the http traffic to the host 10086.cn. It also 10086.cn classifies the ssl traffic to the Common Name 10086.cn. 104.com Web site dedicated to job research. 1111.com.tw Website dedicated to job research in Taiwan. 114la.com Chinese web portal operated by YLMF Computer Technology Co. Chinese cloud storing system of the 115 website. It is operated by YLMF 115.com Computer Technology Co. 118114.cn Chinese booking and reservation portal. 11st.co.kr Korean shopping website 11st. It is operated by SK Planet Co. 1337x.org Bittorrent tracker search engine 139mail 139mail is a chinese webmail powered by China Mobile. 15min.lt Lithuanian news portal Chinese web portal 163. It is operated by NetEase, a company which 163.com pioneered the development of Internet in China. 17173.com Website distributing Chinese games. 17u.com Chinese online travel booking website. 20 minutes is a free, daily newspaper available in France, Spain and 20minutes Switzerland. This plugin classifies websites. 24h.com.vn Vietnamese news portal 24ora.com Aruban news portal 24sata.hr Croatian news portal 24SevenOffice 24SevenOffice is a web-based Enterprise resource planning (ERP) systems. 24ur.com Slovenian news portal 2ch.net Japanese adult videos web site 2Shared 2shared is an online space for sharing and storage. -

Effective Unified Communications As a Service (Ucaas)
The Definitive Guide to UCaaS: Simplifying Unified Communications as a Service Table of Contents Complex and Expensive................... 3 Effective unified communications as a service Talking VoIP...................................... 4 (UCaaS) promises to deliver seamless, secure, and Communication System Patchwork.. 5 cost-effective communications—across multiple UCaaS in a Nutshell......................... 6 channels (voice, text, video, etc.), and on different Multiple Payoffs................................ 7 devices, anywhere the user needs it. The Real Risk................................... 8 Maximizing User Adoption................ 9 With UCaaS, virtually any business can realize the The Only Practical Solution: UCaaS. 10 benefits of a simpler, more cost effective way to UCaaS and Collaboration................ 11 communicate and collaborate. A trucking company Benefits of UCaaS........................... 12 saves on long distance charges and gains better Moving Forward with UCaaS........... 13 connections to customers. A global commerce company cuts costs and increases employee engagement with richer meetings leveraging VoIP and video. But how do you get there? Read on to learn about moving enterprise communications to the cloud, challenges behind unified communications, the role of the user, and the multiple pay-offs of successful UCaaS and collaboration. “With the modern, global workplace being increasingly disconnected due to differences in time and location, the need for effective unified communications and collaboration -

Instant Messaging Market, 2009-2013 Executive Summary
THE RADICATI GROUP, INC. A TECHNOLOGY MARKET RESEARCH FIRM 1900 EMBARCADERO ROAD, SUITE 206. • PALO ALTO, CA 94303 TEL. 650 322-8059 • FAX 650 322-8061 Instant Messaging Market, 2009-2013 Editor: Sara Radicati, Ph.D; Principal Analyst: Todd Yamasaki SCOPE This study examines the market for Instant Messaging (IM) solutions from 2009 to 2013. It provides extensive data regarding current installed base, broken out by region, business size, and other variables, including four year forecasts. This report also examines IM solution features, business strategies, plus product strengths and weaknesses. All market numbers, such as market size, forecasts, installed base, and any financial information presented in this study represent worldwide figures, unless otherwise indicated. All pricing numbers are expressed in $USD. METHODOLOGY The information and analysis in this report is based on primary research conducted by The Radicati Group, Inc. It consists of information collected from vendors, and users within global corporations via interviews and surveys. Secondary research sources have also been used, where appropriate, to cross-check the information collected. These include company annual reports and market size information from various market segments of the computer industry. EUROPE: 29E FITZJOHNS AVE • LONDON NW3 5JY • TEL. +44 (0)207 794 4298 • FAX. +44 (0)207 431 9375 e-mail: [email protected] http://www.radicati.com Instant Messaging Market, 2009-2013 – Executive Summary EXECUTIVE SUMMARY EXECUTIVE SUMMARY This study looks at the Instant Messaging market as comprising four different market segments: o Public IM networks – This segment includes free IM services which primarily target consumers, but are also prevalent amongst business users. -

Facebook Response to the ACCC's Digital Platform Services Inquiry
Facebook response to the ACCC’s Digital Platform Services Inquiry September 2020 Interim Report 8 March 2021 Executive Summary The growth in the use of messaging apps (private messaging services as referred to in the Digital Platform Services Inquiry (D SPI) Interim Report September 2020 (I nterim Report )) has been one of the key trends of the digital ecosystem in recent years, and this has accelerated during the COVID 19 pandemic as many families, friends and workplaces have used small group conversations and direct messaging to stay in touch. Many different competitive solutions have been developed to respond to this consumer demand - whether it is pre-installed and default messaging apps like iMessage and Android Messages which also have exclusive access to support SMS as well as their own proprietary protocols (along with similar device maker SMS solutions); the wide variety of downloadable apps offering messaging services such as Facebook Messenger, WhatsApp, Telegram, Signal, Snapchat, Discord, TikTok, Twitch or Google Chat (among others); or enterprise platforms such as Slack, Teams and Google Hangouts. Given the important role that messaging apps play in keeping Australian households connected and work colleagues productive, the inquiry as part of the DPSI by the Australian Competition and Consumer Commission ( ACCC ) into private messaging is timely. Following the release of the Interim Report, Facebook provides this submission in order to set forth its concerns with the conclusions reached in the Interim Report. In the Interim Report, the ACCC finds that Facebook’s online private messaging services (Facebook Messenger and WhatsApp) are not “competitively constrained” by other private messaging services, implying that - even though there is a broad array of competing private messaging services - they do not provide effective competition against Facebook’s services. -

Cisco SCA BB Protocol Reference Guide
Cisco Service Control Application for Broadband Protocol Reference Guide Protocol Pack #60 August 02, 2018 Cisco Systems, Inc. www.cisco.com Cisco has more than 200 offices worldwide. Addresses, phone numbers, and fax numbers are listed on the Cisco website at www.cisco.com/go/offices. THE SPECIFICATIONS AND INFORMATION REGARDING THE PRODUCTS IN THIS MANUAL ARE SUBJECT TO CHANGE WITHOUT NOTICE. ALL STATEMENTS, INFORMATION, AND RECOMMENDATIONS IN THIS MANUAL ARE BELIEVED TO BE ACCURATE BUT ARE PRESENTED WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED. USERS MUST TAKE FULL RESPONSIBILITY FOR THEIR APPLICATION OF ANY PRODUCTS. THE SOFTWARE LICENSE AND LIMITED WARRANTY FOR THE ACCOMPANYING PRODUCT ARE SET FORTH IN THE INFORMATION PACKET THAT SHIPPED WITH THE PRODUCT AND ARE INCORPORATED HEREIN BY THIS REFERENCE. IF YOU ARE UNABLE TO LOCATE THE SOFTWARE LICENSE OR LIMITED WARRANTY, CONTACT YOUR CISCO REPRESENTATIVE FOR A COPY. The Cisco implementation of TCP header compression is an adaptation of a program developed by the University of California, Berkeley (UCB) as part of UCB’s public domain version of the UNIX operating system. All rights reserved. Copyright © 1981, Regents of the University of California. NOTWITHSTANDING ANY OTHER WARRANTY HEREIN, ALL DOCUMENT FILES AND SOFTWARE OF THESE SUPPLIERS ARE PROVIDED “AS IS” WITH ALL FAULTS. CISCO AND THE ABOVE-NAMED SUPPLIERS DISCLAIM ALL WARRANTIES, EXPRESSED OR IMPLIED, INCLUDING, WITHOUT LIMITATION, THOSE OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT OR ARISING FROM A COURSE OF DEALING, USAGE, OR TRADE PRACTICE. IN NO EVENT SHALL CISCO OR ITS SUPPLIERS BE LIABLE FOR ANY INDIRECT, SPECIAL, CONSEQUENTIAL, OR INCIDENTAL DAMAGES, INCLUDING, WITHOUT LIMITATION, LOST PROFITS OR LOSS OR DAMAGE TO DATA ARISING OUT OF THE USE OR INABILITY TO USE THIS MANUAL, EVEN IF CISCO OR ITS SUPPLIERS HAVE BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES. -

Survey of Instant Messaging Applications Encryption Methods
Avrupa Bilim ve Teknoloji Dergisi European Journal of Science and Technology Cilt. 2, No. 4, S. 112-117, Haziran 2015 Vol. 2, No. 4, pp. 112-117, June 2015 © Telif hakkı EJOSAT’a aittir Copyright © 2014 EJOSAT Araştırma Makalesi www.ejosat.com ISSN:2148-2683 Research Article Survey of Instant Messaging Applications Encryption Methods Abdullah Talha Kabakus1*, Resul Kara2 1 Abant Izzet Baysal University, IT Center, 14280, Bolu, Turkey 2 Duzce University, Faculty of Engineering, Department of Computer Engineering, 81620, Duzce, Turkey (First received 15 February 2015 and in final form 29 May 2015) Abstract Instant messaging applications has already taken the place of traditional Short Messaging Service (SMS) and Multimedia Messaging Service (MMS) due to their popularity and usage easement they provide. Users of instant messaging applications are able to send both text and audio messages, different types of attachments such as photos, videos, and contact information to their contacts in real time. Because of instant messaging applications use internet instead of Short Message Service Technical Realization (GSM), they are free to use and they only require internet connection which is the most common way of communication today. The critical point here is providing privacy of these messages in order to prevent any vulnerable points for hackers and cyber criminals. According to the latest research by PricewaterhouseCoopers, percentage of global cyber attacks is increased to 48% with 42.8 million detected incidents. Another report that is published by security company Postini indicates that 90% of instant messaging targeted threats are highly destructive worms. In this study, instant messaging applications encryption methods are comparatively presented. -

Prism Vol. 9, No. 2 Prism About Vol
2 021 PRISMVOL. 9, NO. 2 | 2021 PRISM VOL. 9, NO. 2 NO. 9, VOL. THE JOURNAL OF COMPLEX OPER ATIONS PRISM ABOUT VOL. 9, NO. 2, 2021 PRISM, the quarterly journal of complex operations published at National Defense University (NDU), aims to illuminate and provoke debate on whole-of-government EDITOR IN CHIEF efforts to conduct reconstruction, stabilization, counterinsurgency, and irregular Mr. Michael Miklaucic warfare operations. Since the inaugural issue of PRISM in 2010, our readership has expanded to include more than 10,000 officials, servicemen and women, and practi- tioners from across the diplomatic, defense, and development communities in more COPYEDITOR than 80 countries. Ms. Andrea L. Connell PRISM is published with support from NDU’s Institute for National Strategic Studies (INSS). In 1984, Secretary of Defense Casper Weinberger established INSS EDITORIAL ASSISTANTS within NDU as a focal point for analysis of critical national security policy and Ms. Taylor Buck defense strategy issues. Today INSS conducts research in support of academic and Ms. Amanda Dawkins leadership programs at NDU; provides strategic support to the Secretary of Defense, Chairman of the Joint Chiefs of Staff, combatant commands, and armed services; Ms. Alexandra Fabre de la Grange and engages with the broader national and international security communities. Ms. Julia Humphrey COMMUNICATIONS INTERNET PUBLICATIONS PRISM welcomes unsolicited manuscripts from policymakers, practitioners, and EDITOR scholars, particularly those that present emerging thought, best practices, or train- Ms. Joanna E. Seich ing and education innovations. Publication threshold for articles and critiques varies but is largely determined by topical relevance, continuing education for national and DESIGN international security professionals, scholarly standards of argumentation, quality of Mr. -
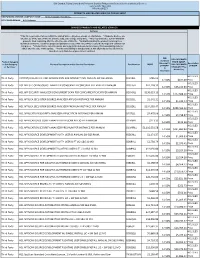
HCL Software's
IBM Branded, Fujistu Branded and Panasonic Branded Products and Related Services and Cloud Services Contract DIR-TSO-3999 PRICING SHEET PRODUCTS AND RELATED SERVICES PRICING SHEET RESPONDING VENDOR COMPANY NAME:____Sirius Computer Solutions_______________ PROPOSED BRAND:__HCL Software__________________________ BRANDED PRODUCTS AND RELATED SERVICES Software * This file is generated for use within the United States. All prices shown are US Dollars. * Products & prices are effective as of the date of this file and are subject to change at any time. * HCL may announce new or withdraw products from marketing after the effective date of this file. * Nothwithstanding the product list and prices identified on this file, customer proposals/quotations issued will reflect HCL's current offerings and commercial list prices. * Product list is not all inclusive and may not include products removed from availability (sale) or added after the date of this update. * Product availability is not guaranteed. Not all products listed below are found on every State/Local government contract. DIR DIR CUSTOMER Customer Product Category PRICE (MSRP- Discount % Description or SubCategory Product Description and/or Service Description Part Number MSRP DIR CUSTOMER off MSRP* of MSRP or Services* DISCOUNT Plus (2 Admin Fee) Decimals) HCL SLED Third Party CNTENT/COLLAB ACC AND WEBSPH PRTL SVR INTRANET PVU ANNUAL SW S&S RNWL E045KLL $786.02 14.50% $677.09 Price HCL SLED Third Party HCL APP SEC OPEN SOURCE ANALYZER CONSCAN PER CONCURRENT EVENT PER ANNUM D20H6LL $41,118.32 -

Test-Beds and Guidelines for Securing Iot Products and for Secure Set-Up Production Environments
IoT4CPS – Trustworthy IoT for CPS FFG - ICT of the Future Project No. 863129 Deliverable D7.4 Test-beds and guidelines for securing IoT products and for secure set-up production environments The IoT4CPS Consortium: AIT – Austrian Institute of Technology GmbH AVL – AVL List GmbH DUK – Donau-Universit t Krems I!AT – In"neon Technologies Austria AG #KU – JK Universit t Lin$ / Institute for &ervasive 'om(uting #) – Joanneum )esearch !orschungsgesellschaft mbH *+KIA – No,ia -olutions an. Net/or,s 0sterreich GmbH *1& – *1& -emicon.uctors Austria GmbH -2A – -2A )esearch GmbH -)!G – -al$burg )esearch !orschungsgesellschaft -''H – -oft/are 'om(etence 'enter Hagenberg GmbH -AG0 – -iemens AG 0sterreich TTTech – TTTech 'om(utertechni, AG IAIK – TU Gra$ / Institute for A((lie. Information &rocessing an. 'ommunications ITI – TU Gra$ / Institute for Technical Informatics TU3 – TU 3ien / Institute of 'om(uter 4ngineering 1*4T – 1-Net -ervices GmbH © Copyright 2020, the Members of the IoT4CPS Consortium !or more information on this .ocument or the IoT5'&- (ro6ect, (lease contact8 9ario Drobics7 AIT Austrian Institute of Technology7 mario:.robics@ait:ac:at IoT4C&- – <=>?@A Test-be.s an. guidelines for securing IoT (ro.ucts an. for secure set-up (ro.uction environments Dissemination level8 &U2LI' Document Control Title8 Test-be.s an. gui.elines for securing IoT (ro.ucts an. for secure set-u( (ro.uction environments Ty(e8 &ublic 4.itorBsC8 Katharina Kloiber 4-mail8 ,,;D-net:at AuthorBsC8 Katharina Kloiber, Ni,olaus DEr,, -ilvio -tern )evie/erBsC8 -te(hanie von )E.en, Violeta Dam6anovic, Leo Ha((-2otler Doc ID8 DF:5 Amendment History Version Date Author Description/Comments VG:? ?>:G?:@G@G -ilvio -tern Technology Analysis VG:@ ?G:G>:@G@G -ilvio -tern &ossible )esearch !iel.s for the -2I--ystem VG:> >?:G<:@G@G Katharina Kloiber Initial version (re(are. -

ASD-Covert-Foreign-Money.Pdf
overt C Foreign Covert Money Financial loopholes exploited by AUGUST 2020 authoritarians to fund political interference in democracies AUTHORS: Josh Rudolph and Thomas Morley © 2020 The Alliance for Securing Democracy Please direct inquiries to The Alliance for Securing Democracy at The German Marshall Fund of the United States 1700 18th Street, NW Washington, DC 20009 T 1 202 683 2650 E [email protected] This publication can be downloaded for free at https://securingdemocracy.gmfus.org/covert-foreign-money/. The views expressed in GMF publications and commentary are the views of the authors alone. Cover and map design: Kenny Nguyen Formatting design: Rachael Worthington Alliance for Securing Democracy The Alliance for Securing Democracy (ASD), a bipartisan initiative housed at the German Marshall Fund of the United States, develops comprehensive strategies to deter, defend against, and raise the costs on authoritarian efforts to undermine and interfere in democratic institutions. ASD brings together experts on disinformation, malign finance, emerging technologies, elections integrity, economic coercion, and cybersecurity, as well as regional experts, to collaborate across traditional stovepipes and develop cross-cutting frame- works. Authors Josh Rudolph Fellow for Malign Finance Thomas Morley Research Assistant Contents Executive Summary �������������������������������������������������������������������������������������������������������������������� 1 Introduction and Methodology �������������������������������������������������������������������������������������������������� -

The Extreme Right on Discord
Gaming and Extremism The Extreme Right on Discord Aoife Gallagher, Ciaran O’Connor, Pierre Vaux, Elise Thomas, Jacob Davey About the series This briefing is part of ISD’s Gaming and Extremism Series exploring the role online gaming plays in the strategy of far-right extremists in the UK and globally. This is part of a broader programme on the ‘Future of Extremism’ being delivered by ISD in the second half of 2021, charting the transformational shifts in the extremist threat landscape two decades on from 9/11, and the policy strategies required to counter the next generation of extremist threats. It provides a snapshot overview of the extreme right’s use of Discord. Gaming and Extremism Contents 3 Contents Executive Summary 4 Key Findings 4 Findings of Analysis 5 Vetting, Verification & Channel Creation 5 Function of Servers 5 The Role of Gaming 6 Case Studies 8 Conclusion 10 Methodology 11 Gaming and Extremism The Extreme Right on Discord 4 Executive summary Discord is a free service accessible via phones and Key Findings computers. It allows users to talk to each other in real time via voice, text or video chat and emerged • We found that the Discord primarily acts in 2015 as a platform designed to assist gamers in as a hub for extreme right-wing socialising communicating with each other while playing video and community building. Our analysis suggests games. The popularity of the platform has surged that Discord provides a safe space for users in recent years, and it is currently estimated to to share ideological material and explore have 140 million monthly active users.1 extremist movements. -

Test Result Report for Anydesk
Performance Test Results Report Prepared for AnyDesk For period 08/31/2020 – 09/09/2020 Reporter: Aliaksandr Hryshutsin Page: 1 of 13 Creation Date: 9/21/2020 Contents 1 Testing Approach ........................................................................................................................................... 3 1.1 Types of Tests ......................................................................................................................................... 3 1.2 Test set-up ............................................................................................................................................... 3 2 Summary on Test Results .............................................................................................................................. 4 2.1 Summary ................................................................................................................................................. 4 3 Test results ..................................................................................................................................................... 4 3.1 Framerate ................................................................................................................................................ 4 3.2 Latency .................................................................................................................................................... 5 3.3 Bandwidth ...............................................................................................................................................