AVG Ultimate User Manual
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

CERIAS Tech Report 2017-5 Deceptive Memory Systems by Christopher N
CERIAS Tech Report 2017-5 Deceptive Memory Systems by Christopher N. Gutierrez Center for Education and Research Information Assurance and Security Purdue University, West Lafayette, IN 47907-2086 DECEPTIVE MEMORY SYSTEMS ADissertation Submitted to the Faculty of Purdue University by Christopher N. Gutierrez In Partial Fulfillment of the Requirements for the Degree of Doctor of Philosophy December 2017 Purdue University West Lafayette, Indiana ii THE PURDUE UNIVERSITY GRADUATE SCHOOL STATEMENT OF DISSERTATION APPROVAL Dr. Eugene H. Spa↵ord, Co-Chair Department of Computer Science Dr. Saurabh Bagchi, Co-Chair Department of Computer Science Dr. Dongyan Xu Department of Computer Science Dr. Mathias Payer Department of Computer Science Approved by: Dr. Voicu Popescu by Dr. William J. Gorman Head of the Graduate Program iii This work is dedicated to my wife, Gina. Thank you for all of your love and support. The moon awaits us. iv ACKNOWLEDGMENTS Iwould liketothank ProfessorsEugeneSpa↵ord and SaurabhBagchi for their guidance, support, and advice throughout my time at Purdue. Both have been instru mental in my development as a computer scientist, and I am forever grateful. I would also like to thank the Center for Education and Research in Information Assurance and Security (CERIAS) for fostering a multidisciplinary security culture in which I had the privilege to be part of. Special thanks to Adam Hammer and Ronald Cas tongia for their technical support and Thomas Yurek for his programming assistance for the experimental evaluation. I am grateful for the valuable feedback provided by the members of my thesis committee, Professor Dongyen Xu, and Professor Math ias Payer. -

Amateur Computer Group of New Jersey NEWS Volume 39, Number 01 January 2014
Amateur Computer Group of New Jersey NEWS Volume 39, Number 01 January 2014 Main Meeting/Election Report ACGNJ Meetings Brenda Bell, ACGNJ For the very latest news on ACGNJ meetings, please On December 6, 2013, we held our Annual Business visit the ACGNJ Website (www.acgnj.org). Meeting, with 8 persons attending. Having reached a Board of Directors Meeting: December 31, 7:00 PM quorum, the meeting was called to order at 9:09 PM. MOVED to Friday, January 3, 7:00 PM. Mike Redlich presented a President's Report. (Due to the New Year's Holiday) Malthi Masurekar presented a Treasurer's Report. Board of Directors Meeting: Friday, Jan 3, 7:00 PM Several topics were raised for discussion, including Mike Redlich (president (at) acgnj.org) membership issues and outreach to other clubs. Main Meeting: Friday, January 3. 8:00 PM Election results. Without discussion, and with no Mike Redlich (president (at) acgnj.org) additional candidates being nominated for our two Lunics (Linux/UNIX): Monday, January 6, 8:00 PM still open Director positions, John Raff moved that Andreas Meyer (lunics (at) acgnj.org) the Secretary cast one vote for the pat slate. The Investing: Thursday, January 9, 8:00 PM motion was seconded and carried. Jim Cooper (jim (at) thecoopers.org). President: Michael Redlich NJ Gamers: Friday, January 10, 6:00 PM Vice-President: Wendy Bell Gregg McCarthy (greggmajestic (at) gmail.com) Secretary: Brenda Bell Treasurer: Malthi Masurekar Layman’s Forum: Monday, January 13, 8:00 PM Directors (Two year term, through end of 2015): Matt Skoda (som359 (at) gmail.com) Gregg McCarthy Java: Tuesday, January 14, 7:30 PM John Raff Mike Redlich (mike (at) redlich.net) Frank Warren Window Pains: Friday, January 17, 7:00 PM Directors (From last year, through end of 2014): !!!WARNING!!! This meeting will NOT be held in Bob Hawes our usual location. -

File Scavenger User Guide
File Scavenger® Version 3.2 Comprehensive Data Recovery Tool For Microsoft® Windows® 7, Vista, XP, 2008, 2003, 2000 and NT User’s Guide Revision: 4 Date: September 2010 QueTek® Consulting Corporation COPYRIGHT © Copyright 1998-2010. This document contains materials protected by International Copyright Laws. All rights reserved. No part of this manual may be reproduced, transmitted or transcribed in any form and for any purpose without the express written permission of QueTek® Consulting Corporation. TRADEMARKS Companies and products mentioned in this manual are for identification purpose only. Product names or brand names appearing in this manual may or may not be registered trademarks or copyrights of their respective companies. NOTICE Reasonable effort has been made to ensure that the information in this manual is accurate. QueTek® Consulting Corporation assumes no liability for technical inaccuracies, typographical, or other errors contained herein. QueTek® Consulting Corporation provides this manual “as is” without warranty of any kind, either express or implied, including, but not limited to the implied warranties or conditions of merchantability or fitness for a particular purpose. In no event shall QueTek® Consulting Corporation be liable for any loss of profits, or for direct, indirect, special, incidental or consequential damages arising from any defect or error in QueTek® Consulting Corporation’s products or manuals. Information in this manual is subject to change without notice and does not represent a commitment on the part of QueTek® Consulting Corporation. User Guide - ii LICENSE AGREEMENT AND LIMITED WARRANTY READ THE FOLLOWING TERMS AND CONDITIONS CAREFULLY PRIOR TO PURCHASING THE LICENSE CODE TO UNLOCK FILE SCAVENGER®. -

User's Manual Undelete® for Windows
User’s Manual Undelete® for Windows® Up-to-the-minute Data Protection® July 2007 This document describes the installation and operation of the Undelete file recovery solutions. It applies to the Server, Desktop Client, Professional and Home Editions of Undelete and is intended for Windows users and system managers. Revision/Update Information: This is a revised manual Software Versions: Undelete 5.0 Server Edition Undelete 5.0 Professional Edition Undelete 5.0 Home Edition Undelete 5.0 Desktop Client Operating Systems: Windows Server 2003 Windows XP Windows 2000 Diskeeper Corporation, Burbank, California ________________________ July 2007 _________ © 2000 — 2007 by Diskeeper Corporation The Software described in this document is owned by Diskeeper Corporation and is protected by United States copyright laws and international treaty provisions. Therefore, you must treat the Software like any other copyrighted material (e.g. a book or musical recording) except that you may either (a) make one copy of the Software solely for backup or archival purposes, or (b) transfer the Software to a single hard disk provided you keep the original solely for backup or archival purposes. You may not copy the user documentation provided with the Software, except for your own authorized use. RESTRICTED RIGHTS LEGEND The software and documentation are provided with RESTRICTED RIGHTS. Use, duplication, or disclosure by the Government is subject to restrictions as set forth in subparagraph (c)(1)(ii) of the Rights in Technical Data and Computer Software clause at DFARS 252.227-7013 or subparagraphs (c)(1) and (2) of the Commercial Computer Software-Restricted Rights at 48 CFR 52.227-19 as applicable. -
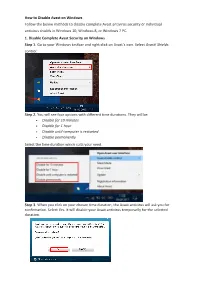
How to Disable to Antivirus
How to Disable Avast on Windows Follow the below methods to disable complete Avast antivirus security or individual antivirus shields in Windows 10, Windows 8, or Windows 7 PC. 1. Disable Complete Avast Security on Windows Step 1. Go to your Windows taskbar and right click on Avast’s icon. Select Avast! Shields control. Step 2. You will see four options with different time durations. They will be: • Disable for 10 minutes • Disable for 1 hour • Disable until computer is restarted • Disable permanently Select the time duration which suits your need. Step 3. When you click on your chosen time duration, the Avast antivirus will ask you for confirmation. Select Yes. It will disable your Avast antivirus temporarily for the selected duration. @CK How to disable or turn off AVG antivirus. 1. For AVG antivirus software: 1. Right-click the AVG icon in the system tray next to the clock. 2. Click "Temporarily disable AVG protection". 3. Choose how long you want the protection to be disabled and whether to disable the firewall as well, and then click "OK". 2. You can also disable AVG from the "Advanced settings": 1. Open the AVG Program. @CK 2. On the "Options" menu, click "Advanced settings". 3. Select "Temporarily disable AVG protection" in the menu on the left side. 4. Click the "Temporarily disable AVG protection" button. 5. Choose how long you want the protection to be disabled and whether to disable the Firewall as well, and then click "OK". @CK HOW TO DEACTIVATE / ACTIVATE AVIRA PROTECTION 1. Open the Avira Control Center 2. -

Hostscan 4.8.01064 Antimalware and Firewall Support Charts
HostScan 4.8.01064 Antimalware and Firewall Support Charts 10/1/19 © 2019 Cisco and/or its affiliates. All rights reserved. This document is Cisco public. Page 1 of 76 Contents HostScan Version 4.8.01064 Antimalware and Firewall Support Charts ............................................................................... 3 Antimalware and Firewall Attributes Supported by HostScan .................................................................................................. 3 OPSWAT Version Information ................................................................................................................................................. 5 Cisco AnyConnect HostScan Antimalware Compliance Module v4.3.890.0 for Windows .................................................. 5 Cisco AnyConnect HostScan Firewall Compliance Module v4.3.890.0 for Windows ........................................................ 44 Cisco AnyConnect HostScan Antimalware Compliance Module v4.3.824.0 for macos .................................................... 65 Cisco AnyConnect HostScan Firewall Compliance Module v4.3.824.0 for macOS ........................................................... 71 Cisco AnyConnect HostScan Antimalware Compliance Module v4.3.730.0 for Linux ...................................................... 73 Cisco AnyConnect HostScan Firewall Compliance Module v4.3.730.0 for Linux .............................................................. 76 ©201 9 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. -

Malware List.Numbers
CLASS A - Tested once a month (and as significant updates and samples are available) (95% or higher detection rate) CLASS B - Tested every two months (and if many new samples or significant updates are available) (95 - 85% detection rate) CLASS C - Tested every three months (85-75% detection rate) CLASS D - Tested every six months (75% or lower detection rates) For Comparison, not an actual Antivirus CLASS F - Excluded from future testing (read notes) Notes, comments, remarks, FAQ and everything else. McAfee Endpoint Protection for Malware Family (by year) # Malware Sample Type MD5 Hash Avast 9.0 Intego VirusBarrier X8 10.8 Norman 3.0.7664 ESET 6.0 Sophos 9 F-Secure 1.0 Kaspersky Security 14 G Data AntiVirus for Mac Dr Web 9.0.0 Avira ClamXav 2.6.4 (web version) Norton 12.6 (26) Comodo Webroot 8 Thirtyseven4 Total Security eScan 5.5-7 iAntivirus 1.1.4 (282) ProtectMac 1.3.2 - 1.4 BitDefender 2.30 - 3.0.6681 McAfee Internet Security for Mac* AVG AntiVirus for Mac Dr Web Light 6.0.6 (201207050) Max Secure Antivirus MacBooster X-Protect Gatekeeper Intego VirusBarrier 2013 10.7 Intego VirusBarrier X6 VirusBarrier Express 1.1.6 (79) Panda Antivirus 1.6 Bitdefender (App Store) 2.21 MacKeeper 2.5.1 - 2.8 (476) Panda Antivirus 10.7.6 Trend Micro Titanium 3.0 McAfee Security 1.2.0 (1549) Norton 11.1.1 (2) Trend Micro Smart Sur. 1.6.1101 McAfee VirusScan for Mac 8.6.1 FortiClient 5.0.6.131 Quick Heal Total Sec 1.0 MacScan 2.9.4 McAfee Virex 7.7 (163) Magician 1.4.3 Vipre 1.0.51 Mac Malware Remover 1.1.6 MD5 Hash Mac 1 Price -> Free $39.99 (Internet -

Contrôles De Conformité Nessus Audit Des Configurations Et Du Contenu Du Système 14 Janvier 2014 (Révision 74)
Contrôles de conformité Nessus Audit des configurations et du contenu du système 14 janvier 2014 (Révision 74) Table des matières Introduction ......................................................................................................................................... 4 Prérequis ...................................................................................................................................................... 4 Clients de Nessus et de SecurityCenter .................................................................................................... 4 Normes et conventions ............................................................................................................................... 4 Normes de conformité ................................................................................................................................. 5 Audits de configuration, fuites de données et conformité ....................................................................... 6 Qu'est-ce qu'un audit ? .............................................................................................................................. 6 Audit et scan des vulnérabilités .................................................................................................................. 6 Exemples d'éléments d'audit ...................................................................................................................... 6 Windows .................................................................................................................................................................... -

Q3 Consumer Endpoint Protection Jul-Sep 2020
HOME ANTI- MALWARE PROTECTION JUL - SEP 2020 selabs.uk [email protected] @SELabsUK www.facebook.com/selabsuk blog.selabs.uk SE Labs tested a variety of anti-malware (aka ‘anti-virus’; aka ‘endpoint security’) products from a range of well-known vendors in an effort to judge which were the most effective. Each product was exposed to the same threats, which were a mixture of targeted attacks using well-established techniques and public email and web-based threats that were found to be live on the internet at the time of the test. The results indicate how effectively the products were at detecting and/or protecting against those threats in real time. 2 Home Anti-Malware Protection July - September 2020 MANAGEMENT Chief Executive Officer Simon Edwards CONTENTS Chief Operations Officer Marc Briggs Chief Human Resources Officer Magdalena Jurenko Chief Technical Officer Stefan Dumitrascu Introduction 04 TEstING TEAM Executive Summary 05 Nikki Albesa Zaynab Bawa 1. Total Accuracy Ratings 06 Thomas Bean Solandra Brewster Home Anti-Malware Protection Awards 07 Liam Fisher Gia Gorbold Joseph Pike 2. Threat Responses 08 Dave Togneri Jake Warren 3. Protection Ratings 10 Stephen Withey 4. Protection Scores 12 IT SUPPORT Danny King-Smith 5. Protection Details 13 Chris Short 6. Legitimate Software Ratings 14 PUBLICatION Sara Claridge 6.1 Interaction Ratings 15 Colin Mackleworth 6.2 Prevalence Ratings 16 Website selabs.uk Twitter @SELabsUK 6.3 Accuracy Ratings 16 Email [email protected] Facebook www.facebook.com/selabsuk 6.4 Distribution of Impact Categories 17 Blog blog.selabs.uk Phone +44 (0)203 875 5000 7. -

AVG Performance User Manual
AVG Performance User Manual Document revision 2014.06 (29.7.2015) Copyright AVG Technologies CZ, s.r.o. All rights reserved. All other trademarks are the property of their respective owners. 1 Contents 1. In.t.r..o.d..u..c..t.i.o.n.......................................................................................................... 4 1.1 Hardware. .r.e..q.u..i.r.e.m..e..n..t.s........................................................................................ 5 1.2 Software. .r.e.q..u..ir.e..m..e..n.t.s......................................................................................... 5 2. AV..G.. .Z..e..n............................................................................................................... 6 2.1 Zen Insta..ll.a.t..io..n. .P..r.o..c.e..s.s....................................................................................... 7 2.1.1 We.l.c.o..m...e. .D..i.a.l.o.g.......................................................................................... 7 2.1.2 De.s.t.i.n.a..t.i.o.n.. .F..o.l.d.e..r...................................................................................... 7 2.2 Zen User. .I.n.t.e..r.f.a..c.e.............................................................................................. 9 2.2.1 Ca.t.e.g..o..r.y. .t..il.e.s............................................................................................ 9 2.2.2 De.v.i.c.e..s. .r..ib..b.o..n........................................................................................... 9 2.2.3 Me.s.s..a.g..e..s. .b..u.t.t..o.n....................................................................................... -

Nessus and Antivirus
Nessus and Antivirus January 31, 2014 (Revision 4) Table of Contents Introduction ......................................................................................................................................... 3 Standards and Conventions........................................................................................................................... 3 Overview .............................................................................................................................................. 3 A Note on SCAP Audits ................................................................................................................................. 4 Microsoft Windows Defender ............................................................................................................. 4 Kaspersky Internet Security 2012 ...................................................................................................... 4 AVG 2012 ............................................................................................................................................. 7 Norton Internet Security 2012 .......................................................................................................... 10 Norton 360 ......................................................................................................................................... 14 Panda Internet Security 2012 ........................................................................................................... 18 Trend Micro Titanium -

2012 Consumer Security Products Performance Benchmarks (Edition 2) Antivirus and Internet Security Windows 7
2012 Consumer Security Products Performance Benchmarks (Edition 2) Antivirus and Internet Security Windows 7 November 2011 Document: 2012 Consumer Security Products Performance Benchmarks (Edition 2) Authors: M. Baquiran, D. Wren Company: PassMark Software Date: 14 November 2011 Edition: 2 File: antivirus_12-performance-testing-ed2.docx Consumer Internet Security and Antivirus Solutions PassMark Software Table of Contents TABLE OF CONTENTS ......................................................................................................................................... 2 REVISION HISTORY ............................................................................................................................................ 4 REFERENCES ...................................................................................................................................................... 4 EXECUTIVE SUMMARY ...................................................................................................................................... 5 OVERALL SCORE ................................................................................................................................................ 6 PRODUCTS AND VERSIONS ............................................................................................................................... 8 INTERNET SECURITY SOFTWARE .................................................................................................................................. 8 ANTIVIRUS SOFTWARE .............................................................................................................................................