Websocket Adoption and the Landscape of the Real-Time Web
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

HTML5 Websocket Protocol and Its Application to Distributed Computing
CRANFIELD UNIVERSITY Gabriel L. Muller HTML5 WebSocket protocol and its application to distributed computing SCHOOL OF ENGINEERING Computational Software Techniques in Engineering MSc arXiv:1409.3367v1 [cs.DC] 11 Sep 2014 Academic Year: 2013 - 2014 Supervisor: Mark Stillwell September 2014 CRANFIELD UNIVERSITY SCHOOL OF ENGINEERING Computational Software Techniques in Engineering MSc Academic Year: 2013 - 2014 Gabriel L. Muller HTML5 WebSocket protocol and its application to distributed computing Supervisor: Mark Stillwell September 2014 This thesis is submitted in partial fulfilment of the requirements for the degree of Master of Science © Cranfield University, 2014. All rights reserved. No part of this publication may be reproduced without the written permission of the copyright owner. Declaration of Authorship I, Gabriel L. Muller, declare that this thesis titled, HTML5 WebSocket protocol and its application to distributed computing and the work presented in it are my own. I confirm that: This work was done wholly or mainly while in candidature for a research degree at this University. Where any part of this thesis has previously been submitted for a degree or any other qualification at this University or any other institution, this has been clearly stated. Where I have consulted the published work of others, this is always clearly attributed. Where I have quoted from the work of others, the source is always given. With the exception of such quotations, this thesis is entirely my own work. I have acknowledged all main sources of help. Where the thesis is based on work done by myself jointly with others, I have made clear exactly what was done by others and what I have contributed myself. -
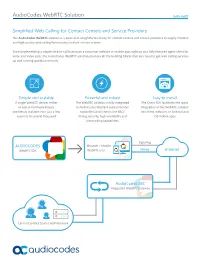
Audiocodes Webrtc Solution DATA SHEET
AudioCodes WebRTC Solution DATA SHEET Simplified Web Calling for Contact Centers and Service Providers The AudioCodes WebRTC solution is a quick and straightforward way for contact centers and service providers to supply intuitive and high-quality web calling functionality to their service centers. From implementing a simple click-to-call button on a consumer website or mobile app, right up to a fully featured agent client for voice and video calls, the AudioCodes WebRTC solution provides all the building blocks that you need to get web calling services up and running quickly and easily. Simple and scalable Powerful and robust Easy to install A single WebRTC device, either The WebRTC solution is fully integrated The Client SDK facilitates the quick virtual or hardware-based, in AudioCodes Mediant session border integration of the WebRTC solution seamlessly scalable from just a few controllers and inherits the SBCs’ into client websites or Android and sessions to several thousand strong security, high availability and iOS mobile apps transcoding capabilities Signaling AUDIOCODES Browser / Mobile WebRTC SDK WebRTC user Media Internet AudioCodes SBC Integrated WebRTC Gateway Carrier/Contact Center VoIP Network AudioCodes WebRTC Solution DATA SHEET Specifications WebRTC Gateway About AudioCodes AudioCodes Ltd. (NasdaqGS: AUDC) is a Deployment leading vendor of advanced voice networking VMWare KVM AWS Mediant 9000 Mediant 4000 method and media processing solutions for the digital workplace. With a commitment to the human 3,000 voice deeply embedded in its DNA, AudioCodes 5,000 WebRTC sessions 2,700 3,500 (20,000 on 1,000 enables enterprises and service providers (20K on roadmap) roadmap) to build and operate all-IP voice networks for unified communications, contact centers 3,000 1,050 integrated and hosted business services. -

A Websocket-Based Approach to Transporting Web Application Data
A WebSocket-based Approach to Transporting Web Application Data March 26, 2015 A thesis submitted to the Division of Graduate Studies and Research of the University of Cincinnati in partial fulfillment of the requirements for the degree of MASTER OF SCIENCE in the Department of Computer Science of the College of Engineering and Applied Science by Ross Andrew Hadden B.S., University of Cincinnati, Cincinnati, Ohio (2014) Thesis Adviser and Committee Chair: Dr. Paul Talaga Committee members: Dr. Fred Annexstein, Professor, and Dr. John Franco, Professor Abstract Most web applications serve dynamic data by either deferring an initial page response until the data has been retrieved, or by returning the initial response immediately and loading additional content through AJAX. We investigate another option, which is to return the initial response immediately and send additional content through a WebSocket connection as the data becomes available. We intend to illustrate the performance of this proposition, as compared to popular conventions of both a server- only and an AJAX approach for achieving the same outcome. This dissertation both explains and demonstrates the implementation of the proposed model, and discusses an analysis of the findings. We use a Node.js web application built with the Cornerstone web framework to serve both the content being tested and the endpoints used for data requests. An analysis of the results shows that in situations when minimal data is retrieved after a timeout, the WebSocket method is marginally faster than the server and AJAX methods, and when retrieving populated files or database records it is marginally slower. The WebSocket method considerably outperforms the AJAX method when making multiple requests in series, and when making requests in parallel the WebSocket and server approaches both outperform AJAX by a tremendous amount. -

The Websockets Package
The websockets Package Bryan W. Lewis [email protected] December 18, 2012 1 Introduction HTML 5 websockets define an efficient socket-like communication protocol for the web. The websockets package is a native websocket implementation for R that supports most of the draft IETF protocols in use today by web browsers. The websockets package is especially well-suited to interaction between R and web scripting languages like Javascript. Multiple simultaneous web- socket server and client connections are supported. The package has few dependencies and is written mostly in R. Packages are available for all major R platforms including GNU/Linux, OS X, and Windows. Websockets are a particularly simple way to expose R to the Web as a service–they let Javascript and other scripts embedded in web pages directly interact with R, bypassing traditional middleware layers like .NET, Java, and web servers normally used for such interaction. In some cases, websockets can be much more efficient than traditional Ajax schemes for interacting with clients over web protocols. Websockets also simplify service scalability in many cases. The websockets package provides three main capabilities: 1. An websocket service. 2. An websocket client. 3. A basic HTTP service. This guide illustrates each capability with simple examples. The websockets Package 2 Running an R websockets server, step by step The websockets package includes a server function that can initiate and respond to websocket and HTTP events over a network connection (websockets are an extension of standard HTTP). All R/Websocket server applications share the following basic recipe: 1. Load the library. 2. Initialize a websocket server with create_server. -

Web-Enabled DDS Version 1.0
Date: July 2016 Web-Enabled DDS Version 1.0 __________________________________________________ OMG Document Number: formal/2016-03-01 Standard document URL: http://www.omg.org/spec/DDS-WEB Machine Consumable File(s): Normative: http://www.omg.org/spec/DDS-WEB/20150901/webdds_rest1.xsd http://www.omg.org/spec/DDS-WEB/20150901/webdds_websockets1.xsd http://www.omg.org/spec/DDS-WEB/20131122/webdds_soap1_types.xsd http://www.omg.org/spec/DDS-WEB/20131122/webdds_soap1.wsdl http://www.omg.org/spec/DDS-WEB/20131122/webdds_soap1_notify.wsdl Non-normative: http://www.omg.org/spec/DDS-WEB/20150901/webdds_rest1_example.xml http://www.omg.org/spec/DDS-WEB/20150901/webdds_pim_model_v1.eap _______________________________________________ Copyright © 2013, eProsima Copyright © 2016, Object Management Group, Inc. (OMG) Copyright © 2013, Real-Time Innovations, Inc. (RTI) Copyright © 2013, THALES USE OF SPECIFICATION - TERMS, CONDITIONS & NOTICES The material in this document details an Object Management Group specification in accordance with the terms, condi- tions and notices set forth below. This document does not represent a commitment to implement any portion of this speci- fication in any company's products. The information contained in this document is subject to change without notice. LICENSES The companies listed above have granted to the Object Management Group, Inc. (OMG) a nonexclusive, royalty-free, paid up, worldwide license to copy and distribute this document and to modify this document and distribute copies of the modified version. Each of the copyright holders listed above has agreed that no person shall be deemed to have infringed the copyright in the included material of any such copyright holder by reason of having used the specification set forth herein or having conformed any computer software to the specification. -

HTML5 Websockets
HHTTMMLL55 -- WWEEBBSSOOCCKKEETTSS http://www.tutorialspoint.com/html5/html5_websocket.htm Copyright © tutorialspoint.com Web Sockets is a next-generation bidirectional communication technology for web applications which operates over a single socket and is exposed via a JavaScript interface in HTML 5 compliant browsers. Once you get a Web Socket connection with the web server, you can send data from browser to server by calling a send method, and receive data from server to browser by an onmessage event handler. Following is the API which creates a new WebSocket object. var Socket = new WebSocket(url, [protocal] ); Here first argument, url, specifies the URL to which to connect. The second attribute, protocol is optional, and if present, specifies a sub-protocol that the server must support for the connection to be successful. WebSocket Attributes Following are the attribute of WebSocket object. Assuming we created Socket object as mentioned above − Attribute Description Socket.readyState The readonly attribute readyState represents the state of the connection. It can have the following values − A value of 0 indicates that the connection has not yet been established. A value of 1 indicates that the connection is established and communication is possible. A value of 2 indicates that the connection is going through the closing handshake. A value of 3 indicates that the connection has been closed or could not be opened. Socket.bufferedAmount The readonly attribute bufferedAmount represents the number of bytes of UTF-8 text that have been queued using send method. WebSocket Events Following are the events associated with WebSocket object. Assuming we created Socket object as mentioned above − Event Event Handler Description open Socket.onopen This event occurs when socket connection is established. -

HTML5 and Java Technologies
HTML5 and Java Technologies Peter Doschkinow Senior Java Architect The following is intended to outline our general product direction. It is intended for information purposes only, and may not be incorporated into any contract. It is not a commitment to deliver any material, code, or functionality, and should not be relied upon in making purchasing decisions. The development, release, and timing of any features or functionality described for Oracle’s products remains at the sole discretion of Oracle. Agenda . Motivation . HTML5 Overview – Related Java Technologies . Thin Server Architecture . Demo Motivation . Need for clarification Gartner’s 2012 Emerging Technologies Hype Cycle – What is behind the hype . Architectural consequences of new trends . What does the Java platform offer to meet the new challenges . Building of common understanding Web Technology History . 1991 HTML . 1995 JavaScript @ Netscape . 1994 HTML2 . 1996 ECMAScript 1.0, 1.1 . 1996 CSS1 . 1997 ECMAScript 1.2 . 1997 HTML4 . 1998 ECMAScript 1.3 . 1998 CSS2 . 2000 ECMAScript 3 . 2000 XHTML1 . 2010 ECMAScript 5 . 2002 Tableless Web Design . Next: ECMAScript 6 Harmony . 2005 AJAX . 2009 HTML5: as of Dec 2012 W3C CR HTML5 Features W3C / Web Hypertext Application Technology Working Group(WHATWG) . Markup – Semantic markup replacing common usages of generic <span>, <div> . <nav>, <footer>,<audio>, <video>, ... API – Canvas 2D (for immidate mode 2D drawing),Timed media playback – Offline Web Applications, Local Srorage and Filesystem, Web Storage – Geolocation, Web Storage, IndexedDB – File API, Drag-and-Drop, Browser History – ... HTML5 Features Offloaded to other specs, originally part of HTML5 . WebSocket API, Server-Sent Events(SSE), Web Messaging, Web Workers, Web Storage (Web Apps WG ) . -

Towards Web-Based Delta Synchronization for Cloud Storage Services
Towards Web-based Delta Synchronization for Cloud Storage Services He Xiao and Zhenhua Li, Tsinghua University; Ennan Zhai, Yale University; Tianyin Xu, UIUC; Yang Li and Yunhao Liu, Tsinghua University; Quanlu Zhang, Microsoft Research; Yao Liu, SUNY Binghamton https://www.usenix.org/conference/fast18/presentation/xiao This paper is included in the Proceedings of the 16th USENIX Conference on File and Storage Technologies. February 12–15, 2018 • Oakland, CA, USA ISBN 978-1-931971-42-3 Open access to the Proceedings of the 16th USENIX Conference on File and Storage Technologies is sponsored by USENIX. Towards Web-based Delta Synchronization for Cloud Storage Services He Xiao Zhenhua Li ∗ Ennan Zhai Tianyin Xu Tsinghua University Tsinghua University Yale University UIUC Yang Li Yunhao Liu Quanlu Zhang Yao Liu Tsinghua University Tsinghua University Microsoft Research SUNY Binghamton Abstract savings in the presence of users’ file edits [29, 39, 40]. Delta synchronization (sync) is crucial for network-level Unfortunately, today delta sync is only available for efficiency of cloud storage services. Practical delta sync PC clients and mobile apps, but not for the web—the most pervasive and OS-independent access method [37]. techniques are, however, only available for PC clients 0 and mobile apps, but not web browsers—the most per- After a file f is edited into a new version f by users, vasive and OS-independent access method. To under- Dropbox’s PC client will apply delta sync to automati- stand the obstacles of web-based delta sync, we imple- cally upload only the altered bits to the cloud; in contrast, Dropbox’s web interface requires users to manually up- ment a delta sync solution, WebRsync, using state-of- 0 1 the-art web techniques based on rsync, the de facto delta load the entire content of f to the cloud. -

Study of Websocket Protocol for Real-Time Data Transfer Mr
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056 Volume: 07 Issue: 06 | June 2020 www.irjet.net p-ISSN: 2395-0072 Study of WebSocket Protocol for Real-Time Data Transfer Mr. Aniket Avinash Naik1, Mrs. Meghana R Khare2 1PG Student, Dept. of Electronics, Walchand College of Engineering, Sangli, Maharashtra, India 2Assistant Professor, Dept. of Electronics, Walchand College of Engineering, Sangli, Maharashtra, India ---------------------------------------------------------------------***--------------------------------------------------------------------- Abstract - Today, with rapid growth in number of store any state related information about client and hence internet users, there is increasing demand for real-time data HTTP is a stateless application layer protocol. update. There are lots of business entities who want their customers to get instant product specific information 2. NEED OF REAL-TIME COMMUNICATION updates on their web portals. HTML5 gives easy ways of Now days, REST APIs (Representational State Transfer implementing client side for real-time, full duplex client- – Application Programming Interface) plays a role of server communication over WebSocket protocol. This paper middleware for the data exchange between client and presents the necessity of real-time data exchange for web applications, comparison of WebSocket with various server. Client requests to the server for data resource application layer communication techniques like HTTP using unique identifier called URI (Uniform Resource polling, Long polling, Server Sent Events (SSE) etc., analysis Identifier). The request action is identified using normal of WebSocket handshake and data flow. This paper also HTTP methods viz. GET, PUT, POST and DELETE. The presents some of WebSocket implementation techniques at request – response cycle gets completed when server server and client side. -

Assessing Websocket Protocol Performance for Real- Time
School of Computing Teesside University Middlesbrough TS1 3BA Assessing WebSocket Protocol Performance for Real- Time Cryptocurrency Algorithmic Trading with Compiled, Intermediate and Interpreted Programming Languages in Cloud Environment An academic research paper for possible submission to Computers Journal (ISSN 2073-431X) Submitted in partial requirements for the degree of MSc in Computing Date: 24.8.2020 Martin Papík (18276455/1) Supervisor: Ing. Bohuš Získal, Ph.D. Wordcount: 8884 Article Assessing WebSocket Protocol Performance for Real- Time Cryptocurrency Algorithmic Trading with Compiled, Intermediate and Interpreted Programming Languages in Cloud Environment Martin Papík School of Computing, Teesside University, Middlesbrough TS1 3BA, United Kingdom; [email protected] Received: date; Accepted: date; Published: date Abstract: The most of cryptocurrency exchanges provide their market data via WebSocket API. Therefore, trading systems are recommended to utilize WebSocket protocol to be able to connect to the exchange and receive the data. Various programming languages and their respective libraries which contain the referential RFC 6455 implementation of WebSocket protocol can be used for development of communication interface within the trading system. Our study focuses on their evaluation in order to determine their performance differences which are determinative for communication speed that is an important criterion for profitable trading system. Six connectors were developed in compiled, intermediate and interpreted programming languages and their respective WebSocket libraries and deployed in the cloud. The WebSocket layer performance of each connector represented by the event latency metric was tested with three cryptocurrency exchanges producing high workloads on their WebSocket API data streams. In this experiment WebSocket protocol implementation in C++ and Go, both of which belong to the group of compiled languages, have been evaluated as the best performing implementations. -

The Definitive Guide to HTML5 Websocket // Example Websocket Server
For your convenience Apress has placed some of the front matter material after the index. Please use the Bookmarks and Contents at a Glance links to access them. Contents at a Glance Foreword ���������������������������������������������������������������������������������������� xiii About the Authors ���������������������������������������������������������������������������� xv About the Technical Reviewer ������������������������������������������������������� xvii Acknowledgments �������������������������������������������������������������������������� xix ■ Chapter 1: Introduction to HTML5 WebSocket �������������������������������� 1 ■ Chapter 2: The WebSocket API ����������������������������������������������������� 13 ■ Chapter 3: The WebSocket Protocol ��������������������������������������������� 33 ■ Chapter 4: Building Instant Messaging and Chat over WebSocket with XMPP ��������������������������������������������������������� 61 ■ Chapter 5: Using Messaging over WebSocket with STOMP ���������� 85 ■ Chapter 6: VNC with the Remote Framebuffer Protocol ������������� 109 ■ Chapter 7: WebSocket Security �������������������������������������������������� 129 ■ Chapter 8: Deployment Considerations �������������������������������������� 149 ■ Appendix A: Inspecting WebSocket Traffic ��������������������������������� 163 ■ Appendix B: WebSocket Resources �������������������������������������������� 177 Index ���������������������������������������������������������������������������������������������� 183 v CHAPTER 1 Introduction -

Javascript ROOT
Server/Client approach for ROOT7 graphics Sergey Linev, April 2017 Server/Client model • Server: – ROOT C++ application producing data • Client: – JavaScript producing graphical output • Communication: – websocket-based protocol 21.04.2017 S.Linev, Server/Client for ROOT7 graphics 2 Server/Client model auto h1 = new Histogram; auto c1 = new Canvas; c1->Add (h1, “hist”); c1->Draw(); while (flag) { h1->Fill(random()); websocket c1->Modified(); c1->Update(); } Server Client plain ROOT C++ code any web browser 21.04.2017 S.Linev, Server/Client for ROOT7 graphics 3 Communication • websocket – implemented in civetweb (THttpServer) – supported by all web browsers – long polling (async http) as fallback solution • Custom text-based protocol – server -> client: mainly object data as JSON – client -> server: commands or notification events – not directly accessible for the users • Unique objects ID for primitives in pad: – to get list of context menu items – to execute objects method 21.04.2017 S.Linev, Server/Client for ROOT7 graphics 5 Local clients localhost ROOT C++ Chrome JavaScript, websocket HTML, SVG, http server http WebGL http://localhost:8080/Canvases/c1/draw.htm?websocket • Run any browser on the some host • Use THttpServer bound to loopback address • Communication via websockets 21.04.2017 S.Linev, Server/Client for ROOT7 graphics 7 Local clients ROOT C++ WebKit JavaScript, API HTML, SVG, WebGL server http • Use WebKit or libChromium • Create necessary window(s) directly in C++ • Communication with WebKit API (no any sockets) 21.04.2017