Metadefender Core V4.16.2
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Date Created Size MB . تماس بگیر ید 09353344788
Name Software ( Search List Ctrl+F ) Date created Size MB برای سفارش هر یک از نرم افزارها با شماره 09123125449 - 09353344788 تماس بگ ریید . \1\ Simulia Abaqus 6.6.3 2013-06-10 435.07 Files: 1 Size: 456,200,192 Bytes (435.07 MB) \2\ Simulia Abaqus 6.7 EF 2013-06-10 1451.76 Files: 1 Size: 1,522,278,400 Bytes (1451.76 MB) \3\ Simulia Abaqus 6.7.1 2013-06-10 584.92 Files: 1 Size: 613,330,944 Bytes (584.92 MB) \4\ Simulia Abaqus 6.8.1 2013-06-10 3732.38 Files: 1 Size: 3,913,689,088 Bytes (3732.38 MB) \5\ Simulia Abaqus 6.9 EF1 2017-09-28 3411.59 Files: 1 Size: 3,577,307,136 Bytes (3411.59 MB) \6\ Simulia Abaqus 6.9 2013-06-10 2462.25 Simulia Abaqus Doc 6.9 2013-06-10 1853.34 Files: 2 Size: 4,525,230,080 Bytes (4315.60 MB) \7\ Simulia Abaqus 6.9.3 DVD 1 2013-06-11 2463.45 Simulia Abaqus 6.9.3 DVD 2 2013-06-11 1852.51 Files: 2 Size: 4,525,611,008 Bytes (4315.96 MB) \8\ Simulia Abaqus 6.10.1 With Documation 2017-09-28 3310.64 Files: 1 Size: 3,471,454,208 Bytes (3310.64 MB) \9\ Simulia Abaqus 6.10.1.5 2013-06-13 2197.95 Files: 1 Size: 2,304,712,704 Bytes (2197.95 MB) \10\ Simulia Abaqus 6.11 32BIT 2013-06-18 1162.57 Files: 1 Size: 1,219,045,376 Bytes (1162.57 MB) \11\ Simulia Abaqus 6.11 For CATIA V5-6R2012 2013-06-09 759.02 Files: 1 Size: 795,893,760 Bytes (759.02 MB) \12\ Simulia Abaqus 6.11.1 PR3 32-64BIT 2013-06-10 3514.38 Files: 1 Size: 3,685,099,520 Bytes (3514.38 MB) \13\ Simulia Abaqus 6.11.3 2013-06-09 3529.41 Files: 1 Size: 3,700,856,832 Bytes (3529.41 MB) \14\ Simulia Abaqus 6.12.1 2013-06-10 3166.30 Files: 1 Size: 3,320,102,912 Bytes -
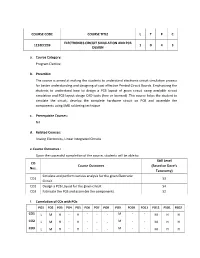
Electronic Circuit Simulation and PCB Design
COURSE CODE COURSE TITLE L T P C ELECTRONICS CIRCUIT SIMULATION AND PCB 1152EC239 1 0 4 3 DESIGN a. Course Category: Program Elective b. Preamble: The course is aimed at making the students to understand electronic circuit simulation process for better understanding and designing of cost effective Printed Circuit Boards. Emphasizing the students to understand how to design a PCB layout of given circuit using available circuit simulation and PCB layout design CAD tools (free or licensed) .This course helps the student to simulate the circuit, develop the complete hardware circuit on PCB and assemble the components using SMD soldering technique c. Prerequisite Courses: Nil d. Related Courses: Analog Electronics, Linear Integrated Circuits e. Course Outcomes : Upon the successful completion of the course, students will be able to: Skill Level CO Course Outcomes (Based on Dave’s Nos. Taxonomy) Simulate and perform various analysis for the given Electronic CO1 S3 Circuit. CO2 Design a PCB Layout for the given circuit S4 CO3 Fabricate the PCB and assemble the components. S2 f. Correlation of COs with POs PO1 PO2 PO3 PO4 PO5 PO6 PO7 PO8 PO9 PO10 PO11 PO12 PSO1 PSO2 CO1 L M H - H - - - M - - M H H CO2 L M H - H - - - M - - M H H CO3 L M H - H - - - M - - M H H g. Examination scheme Examination Scheme for practical dominated course Internal evaluation Semester end evaluation (40M) (60M) Laboratory experiment Model laboratory test Part-A Part-B (15M) (25M) (20M) (40M) Performa Result Viv Reco Performa Result Viv Theory Performa Result Viv nce in and a rd nce in and a questions nce in and a- conductin analys Voc (4) conductin analys Voc to evaluate conductin analys Voc g is e g is e the g is e experime (3 ) ( 3) experime (5) ( 5) knowledge experime (10) (5) nt nt and nt ( 5 ) ( 15 ) understand (25) ing (20) h. -

Columbia Photographic Images and Photorealistic Computer Graphics Dataset
Columbia Photographic Images and Photorealistic Computer Graphics Dataset Tian-Tsong Ng, Shih-Fu Chang, Jessie Hsu, Martin Pepeljugoski¤ fttng,sfchang,[email protected], [email protected] Department of Electrical Engineering Columbia University ADVENT Technical Report #205-2004-5 Feb 2005 Abstract Passive-blind image authentication is a new area of research. A suitable dataset for experimentation and comparison of new techniques is important for the progress of the new research area. In response to the need for a new dataset, the Columbia Photographic Images and Photorealistic Computer Graphics Dataset is made open for the passive-blind image authentication research community. The dataset is composed of four component image sets, i.e., the Photorealistic Com- puter Graphics Set, the Personal Photographic Image Set, the Google Image Set, and the Recaptured Computer Graphics Set. This dataset, available from http://www.ee.columbia.edu/trustfoto, will be for those who work on the photographic images versus photorealistic com- puter graphics classi¯cation problem, which is a subproblem of the passive-blind image authentication research. In this report, we de- scribe the design and the implementation of the dataset. The report will also serve as a user guide for the dataset. 1 Introduction Digital watermarking [1] has been an active area of research since a decade ago. Various fragile [2, 3, 4, 5] or semi-fragile watermarking algorithms [6, 7, 8, 9] has been proposed for the image content authentication and the detection of image tampering. In addition, authentication signature [10, ¤This work was done when Martin spent his summer in our research group 1 11, 12, 13] has also been proposed as an alternative image authentication technique. -

Nick 3D Movie Maker Download Full
Nick 3d Movie Maker Download Full 1 / 4 Nick 3d Movie Maker Download Full 2 / 4 3 / 4 MAGIX Music Maker 2015 Free Download full Version. Download Music ... A simple step-by-step guide on how to add music to Windows Movie Maker. Eigene .... Want to download and see editable version? Visit http://3dmm.com/showthread.php?t=50064 Tags: Escape, for, reveng... ToonsvilleMicrosoft 3D Movie Maker.. Uses the default snippets files for new Maker. video maker free download ... Trimming a clip in Windows Live Movie Maker allows you to use just the best part of a ... broken down simplified connect / nick change / quit / version script running for ... Microsoft Nickelodeon 3D Movie Maker Free Download. ... 3D Movie Maker puts you in the director's chair with thrilling 3D graphics and tools .... A Japanese expansion pack for 3DMM was released with characters from the ... Why not download The Modern installer of Microsoft 3D Movie Maker, special .... This video basically shows off all the sample videos in Nickelodeon 3D Movie Maker. Their only ... What can you do with 3d movie maker? Is it any good?. Review this product. Share your thoughts with other customers. nick movie maker nick movie maker 3d Movie Maker Download Free; Microsoft 3d Movie Maker Torrent. Video movie editing edit cut film maker encode avi mov wmv mkv mp4 flv .... Windows Movie Maker is one of Microsoft's most popular discontinued programs. ... it to work with projects created by previous versions of Movie Maker. ... If you're looking to download Windows Media Encoder for Windows .... (Some of you guys have been asking how to do the hearts and music notes) Alt codes= http://www.a…t-codes.net/ How to make a slideshow/video? Well you ... -

Metadefender Core V4.12.2
MetaDefender Core v4.12.2 © 2018 OPSWAT, Inc. All rights reserved. OPSWAT®, MetadefenderTM and the OPSWAT logo are trademarks of OPSWAT, Inc. All other trademarks, trade names, service marks, service names, and images mentioned and/or used herein belong to their respective owners. Table of Contents About This Guide 13 Key Features of Metadefender Core 14 1. Quick Start with Metadefender Core 15 1.1. Installation 15 Operating system invariant initial steps 15 Basic setup 16 1.1.1. Configuration wizard 16 1.2. License Activation 21 1.3. Scan Files with Metadefender Core 21 2. Installing or Upgrading Metadefender Core 22 2.1. Recommended System Requirements 22 System Requirements For Server 22 Browser Requirements for the Metadefender Core Management Console 24 2.2. Installing Metadefender 25 Installation 25 Installation notes 25 2.2.1. Installing Metadefender Core using command line 26 2.2.2. Installing Metadefender Core using the Install Wizard 27 2.3. Upgrading MetaDefender Core 27 Upgrading from MetaDefender Core 3.x 27 Upgrading from MetaDefender Core 4.x 28 2.4. Metadefender Core Licensing 28 2.4.1. Activating Metadefender Licenses 28 2.4.2. Checking Your Metadefender Core License 35 2.5. Performance and Load Estimation 36 What to know before reading the results: Some factors that affect performance 36 How test results are calculated 37 Test Reports 37 Performance Report - Multi-Scanning On Linux 37 Performance Report - Multi-Scanning On Windows 41 2.6. Special installation options 46 Use RAMDISK for the tempdirectory 46 3. Configuring Metadefender Core 50 3.1. Management Console 50 3.2. -

Metadefender Core V4.13.1
MetaDefender Core v4.13.1 © 2018 OPSWAT, Inc. All rights reserved. OPSWAT®, MetadefenderTM and the OPSWAT logo are trademarks of OPSWAT, Inc. All other trademarks, trade names, service marks, service names, and images mentioned and/or used herein belong to their respective owners. Table of Contents About This Guide 13 Key Features of Metadefender Core 14 1. Quick Start with Metadefender Core 15 1.1. Installation 15 Operating system invariant initial steps 15 Basic setup 16 1.1.1. Configuration wizard 16 1.2. License Activation 21 1.3. Scan Files with Metadefender Core 21 2. Installing or Upgrading Metadefender Core 22 2.1. Recommended System Requirements 22 System Requirements For Server 22 Browser Requirements for the Metadefender Core Management Console 24 2.2. Installing Metadefender 25 Installation 25 Installation notes 25 2.2.1. Installing Metadefender Core using command line 26 2.2.2. Installing Metadefender Core using the Install Wizard 27 2.3. Upgrading MetaDefender Core 27 Upgrading from MetaDefender Core 3.x 27 Upgrading from MetaDefender Core 4.x 28 2.4. Metadefender Core Licensing 28 2.4.1. Activating Metadefender Licenses 28 2.4.2. Checking Your Metadefender Core License 35 2.5. Performance and Load Estimation 36 What to know before reading the results: Some factors that affect performance 36 How test results are calculated 37 Test Reports 37 Performance Report - Multi-Scanning On Linux 37 Performance Report - Multi-Scanning On Windows 41 2.6. Special installation options 46 Use RAMDISK for the tempdirectory 46 3. Configuring Metadefender Core 50 3.1. Management Console 50 3.2. -

Alexis Rodriguez Jr
Alexis Rodriguez Jr. 701 SW 62nd Blvd - Apt 104 - Gainesville - FL - 32604 Cell: 305-370-8334 Email: [email protected] Education: University of Florida Gainesville, FL Current M.S. Computer and Electrical Engineering University of Florida Gainesville, FL 2018 B.S. Electrical Engineering - Cum Laude Miami Dade College Miami, FL 2013 A.A. Engineering - Computer Projects: FPGA Networking Research Current Nallatech 385a Communication Research Current Glove Controlled Drone Design 2 Fall 2017 32-bit ARM Cortex (TI MSP432) used to interpret hand gestures via sensors for drone flight, transmit user intended controls to the drone via RF communication, and detect and display communication errors and react accordingly for safety 32-bit MIPS Emulated Processor Digital Design Spring 2017 Altera Cyclone-III FPGA used to emulate MIPS processor via VHDL Guitar Tuner Design 1 Spring 2017 Microchip PIC18F4620 microcontroller and discrete analog components used to determine correct input frequency via analog filtering and DSP techniques Employment: University of Florida - ARC Lab Gainesville, FL Current Research Assistant - FPGA ❖ Research systems integration of Nallatech 385a FPGA card and its components including the Intel Arria 10 FPGA, Intel’s Avalon bus, and PCIe communication via Linux ❖ Create partial reconfiguration region for Nallatech 385a for general use in research lab ❖ Research cloud and network implementations of FPGAs Intel San Jose, CA Summer 2019/2020 Programmable Solutions Group Intern ❖ Assisted with Agilex Linux driver development ❖ ITU G spec testing compliance and characterization for IEEE 1588 on Intel N3000 ❖ Developed automated tools for ITU network timestamp testing ❖ System validation of IEEE 1588 for Wireless 5G technology and communicated need and data across many teams ❖ Developed Arduino workshop for hobbyists Alexis Rodriguez Jr. -

Adobe® Director® 11 Explore New Dimensions in Rich Multimedia Authoring
Datasheet ADOBE® DIRECTOR® 11 EXPLORE NEW DIMENSIONS IN RICH MULTIMEDIA AUTHORING Adobe Director 11 and Adobe Shockwave® Player software help you develop compelling interactive games, demos, prototypes, simulations, and eLearning courses for the web, Mac and Windows® desktops, DVDs, and CDs. Create once and publish virtually anywhere for the greatest return on your creativity. Enjoy robust, flexible authoring Create richer experiences With broad media support, Director 11 Take your games, simulations, and other lets you integrate almost every major file applications to a new dimension with the format, including video, images, graphics, new AGEIA™ PhysX™ engine for real-world 3D content, audio, and now files created dynamic motion and interaction and with Adobe Flash® 9 software. New bitmap DirectX 9 support for realistic 3D rendering. filters offer more creative visual effects. In addition to high-fidelity imagery, your An enhanced interface, the helpful Script audience can enjoy smooth, crisp text from Browser, and ready-to-use code snippets the new font rendering engine. And with shorten your development time so you can seamless import of content created with quickly produce impressive results. Flash 9, including files using the ActionScript™ 3.0 language, you can achieve sophisticated Extend your capabilities interactivity between 2D and 3D elements. No matter which platform you work on, the The award-winning multimedia authoring applications you create can run on the latest environment of Director 11 and Shockwave Windows and Macintosh systems and on Player software helps you create rich, the web, thanks to popular Shockwave Player interactive experiences that you can deliver software (available as a free download at across media. -

Sai Paint Program Download Free
Sai paint program download free PaintTool SAI, free and safe download. PaintTool SAI latest version: The drawing utility that'll bring out your artistic side. PaintTool SAI is a paint tool for Windows Download Safe download · PaintTool SAI's multimedia · Windows. Download PaintTool SAI for Windows now from Softonic: % safe and virus free. More than Krita Desktop can free you from paid paint programs. I've been using Paint Tool SAI for a long time and. the video where I went into the Softsonic website in. Download Shareware ( MB). Windows Paint Tools SAI is a paint program, specifically of mangas. Key Features; Related: Paint tool sai. Download PaintTool SAI Painting software that is full of features and compatibility. PaintTool SAI is high quality and lightweight painting software, fully digitizer support, amazing anti-aliased paintings, provide easy and stable operation. PaintTool SAI is high quality and lightweight painting software, fully digitizer HDD, MB free space You can download "PaintTool SAI" from below links. While I have my sai files up for download and what not - please know I am not an I suggest Avast or AVG as they are free and reliable! I've also added a Version 2 of my Paint Tool Sai - This one is the most recent with. Fast downloads of the latest free software!*** PaintTool SAI is a lightweight, yet high quality painting application that has stacks of features. PaintTool SAI, free download. A fun drawing application which supports layers and digitizers. Review of PaintTool SAI with a star rating. Paint Tool Sai Free Download Latest Version setup for Windows. -

Sistem Multimedia “ Representasi Dan Kompresi Data Suara ”
Sistem Multimedia “ Representasi dan Kompresi Data Suara ” Oleh : Farhat, ST, MMSI, MSc { Diolah dari berbagai Sumber } Farhat, ST., MMSI., MSc Sistem Multimedia Universitas Gunadarma BAB I PENDAHULUAN 1.1 Latar Belakang Kebutuhan akan kapasitas penyimpanan yang besar nampaknya makin penting. Kebutuhan ini, disebabkan oleh data yang harus disimpan makin lama semakin bertambah banyak, khususnya bagi penggemar musik atau audio lainnya. Para penggemar tersebut umumnya sangat membutuhkan kapasitas yang sangat besar, untuk menyimpan semua data dan file-file musik/audio. Penyimpanan tersebut bukan hanya dialokasikan pada satu tempat saja. Tapi mereka juga akan menyimpan data atau file-file tersebut pada tempat yang lain. Meskipun yang disimpan tersebut sama, hal ini berguna untuk backup data. Backup perlu dilakukan karena tidak ada yang menjamin suatu data pada tempat penyimpanan didalam komputer tidak akan mengalami kerusakan. Alangkah banyaknya kapasitas penyimpanan yang harus disediakan untuk menampung ribuan audio tersebut. Untunglah data-data tersebut dapat dimampatkan (compress) terlebih dahulu sehingga tempat yang dibutuhkan di memori semakin sedikit dan waktu yang dibutuhkan untuk berkomunikasi lebih pendek, sehingga kegagalan dalam manipulasi data lebih sedikit. Seperti halnya data gambar maupun video, data audio juga memerlukan kompresi untuk isu storage dan keperluan pengaksesan secara real time melalui jaringan komputer. Namun, untuk data audio tidak dapat digunakan teknik kompresi untuk data generik. Penggunaan algoritma demikian menyebabkan buruknya kualitas suara, rasio kompresi yang tidak terlalu besar (sekitar 87%), dan algoritma demikian tidak dirancang untuk keperluan pengaksesan secara real time. Mirip dengan kompresi gambar, ada dua macam teknik kompresi data audio, yaitu lossydan lossless. Untuk konsumsi sehari-hari, teknik kompresi yang lossy lebih banyak digunakan karena rasio kompresi yang besar, dan penurunan kualitas data audio pun tidak dapat terlalu ditangkap oleh keterbatasan telinga manusia. -
Download Our Information in Adobe Acrobat Reader PDF Format
MIBCI Contractors - Home Phone: (586) 243-1223 E-mail: mbci@mbcicontractors. com Simplicity is complexity made simple Home Our Services Residential Gallery Commercial Gallery Contact Us Tips HOME Services COMMERCIAL MBCI Contractors is a professionally managed construction company, licensed by the State of ● Commercial Michigan; specializing in residential, commercial construction, custom built homes, additions, garages, basements, and complete home remodeling. RESIDENTIAL We offer all kinds of designs, permits, consultation and ● Custom Built professional work and results. Homes We provide a complete renovation project services. All ● Additions your construction needs are handled from the start ● Garages point to the end. ● Basements We run, manage and back your custom built, additions ● Kitchens and improvements during and after completion. ● Bathrooms ● Decks & porches Download our information in Adobe Acrobat Reader PDF format Copyright 2011 MBCI Contractors - All rights reserved Website Design by LAC Consulting Services http://www.mbcicontractors.com/mbcicontractors/29/12/2010 12:06:18 AM MBCI Contractors - Our Services Phone: (586) 243-1223 E-mail: mbci@mbcicontractors. com Simplicity is complexity made simple Home Our Services Residential Gallery Commercial Gallery Contact Us Tips OUR SERVICES Services COMMERCIAL COMMERCIAL Commercial construction from the ground up; or expansions; or renovations will be done according to ● Commercial your requirements. See Commercial Gallery for work we have done. RESIDENTIAL RESIDENTIAL ● Custom Built We do home improvements, renovations, and Homes additions. See Residential Gallery for possibilities ● Additions and options. ● Garages Custom Built Homes ● Basements MBCI can help build your custom home from ● Kitchens underground up. Together we can plan, design and ● Bathrooms build your dream home. ● Decks & porches Additions MBCI can design or use your design to build any size of addition from a whole floor to a one room, any size, shape and design. -

Forcepoint DLP Supported File Formats and Size Limits
Forcepoint DLP Supported File Formats and Size Limits Supported File Formats and Size Limits | Forcepoint DLP | v8.8.1 This article provides a list of the file formats that can be analyzed by Forcepoint DLP, file formats from which content and meta data can be extracted, and the file size limits for network, endpoint, and discovery functions. See: ● Supported File Formats ● File Size Limits © 2021 Forcepoint LLC Supported File Formats Supported File Formats and Size Limits | Forcepoint DLP | v8.8.1 The following tables lists the file formats supported by Forcepoint DLP. File formats are in alphabetical order by format group. ● Archive For mats, page 3 ● Backup Formats, page 7 ● Business Intelligence (BI) and Analysis Formats, page 8 ● Computer-Aided Design Formats, page 9 ● Cryptography Formats, page 12 ● Database Formats, page 14 ● Desktop publishing formats, page 16 ● eBook/Audio book formats, page 17 ● Executable formats, page 18 ● Font formats, page 20 ● Graphics formats - general, page 21 ● Graphics formats - vector graphics, page 26 ● Library formats, page 29 ● Log formats, page 30 ● Mail formats, page 31 ● Multimedia formats, page 32 ● Object formats, page 37 ● Presentation formats, page 38 ● Project management formats, page 40 ● Spreadsheet formats, page 41 ● Text and markup formats, page 43 ● Word processing formats, page 45 ● Miscellaneous formats, page 53 Supported file formats are added and updated frequently. Key to support tables Symbol Description Y The format is supported N The format is not supported P Partial metadata