Advances in Side-Channel Security
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Cache-Timing Attack Against Aes Crypto System - Countermeasures Review
Edith Cowan University Research Online Australian Information Security Management Conference Conferences, Symposia and Campus Events 2014 Cache-timing attack against aes crypto system - countermeasures review Yaseen H. Taha University of Khartoum Settana M. Abdulh University of Khartoum Naila A. Sadalla University of Khartoum Huwaida Elshoush University of Khartoum Follow this and additional works at: https://ro.ecu.edu.au/ism Part of the Information Security Commons DOI: 10.4225/75/57b65fd1343d3 12th Australian Information Security Management Conference. Held on the 1-3 December, 2014 at Edith Cowan University, Joondalup Campus, Perth, Western Australia. This Conference Proceeding is posted at Research Online. https://ro.ecu.edu.au/ism/166 CACHE-TIMING ATTACK AGAINST AES CRYPTO SYSTEM - COUNTERMEASURES REVIEW Yaseen.H.Taha, Settana.M.Abdulh, Naila.A.Sadalla, Huwaida Elshoush University of Khartoum, Sudan [email protected], [email protected], [email protected], [email protected] Abstract Side channel attacks are based on side channel information, which is information that is leaked from encryption systems. Implementing side channel attacks is possible if and only if an attacker has access to a cryptosystem (victim) or can interact with cryptosystem remotely to compute time statistics of information that collected from targeted system. Cache timing attack is a special type of side channel attack. Here, timing information caused by cache effect is collected and analyzed by an attacker to guess sensitive information such as encryption key or plaintext. Cache timing attack against AES was known theoretically until Bernstein carry out a real implementation of the attack. Fortunately, this attack can be a success only by exploiting bad implementation in software or hardware, not for algorithm structure weaknesses, and that means attack could be prevented if proper implementation has been used. -

Exploiting Switching Noise for Stealthy Data Exfiltration from Desktop Computers
Your Noise, My Signal: Exploiting Switching Noise for Stealthy Data Exfiltration from Desktop Computers Zhihui Shao∗ Mohammad A. Islam∗† Shaolei Ren University of California, Riverside University of Texas at Arlington University of California, Riverside [email protected] [email protected] [email protected] ABSTRACT program’s usage pattern of CPU resources, if detected by another Attacks based on power analysis have been long existing and stud- program, can be modulated for information transfer between the ied, with some recent works focused on data exfiltration from victim two [50, 57]. Consequently, to mitigate data theft risks, enterprise systems without using conventional communications (e.g., WiFi). users commonly have restricted access to outside networks — all Nonetheless, prior works typically rely on intrusive direct power data transfer from and to the outside is tightly scrutinized. measurement, either by implanting meters in the power outlet or Nevertheless, such systems may still suffer from data exfiltration tapping into the power cable, thus jeopardizing the stealthiness of at- attacks that bypass the conventional communications protocols tacks. In this paper, we propose NoDE (Noise for Data Exfiltration), (e.g., WiFi) by transforming the affected computer into a transmitter a new system for stealthy data exfiltration from enterprise desk- and establishing a covert channel. For example, the transmitting top computers. Specifically, NoDE achieves data exfiltration over computer can modulate the intensity of the generated acoustic a building’s power network by exploiting high-frequency voltage noise by varying its cooling fan or hard disk spinning speed to ripples (i.e., switching noises) generated by power factor correction carry 1/0 bit information (e.g., a high fan noise represents “1” and circuits built into today’s computers. -

Some Comments on the First Round AES Evaluation Of
Some Comments on the First Round AES Evaluation of RC6 1 2 1 Scott Contini , Ronald L. Rivest , M.J.B. Robshaw , 1 and Yiqun Lisa Yin 1 RSA Lab oratories, 2955 Campus Drive, San Mateo, CA 94403, USA fscontini,matt,yiqung@rsa. com 2 M.I.T. Lab oratory for Computer Science, 545 Technology Square, Cambridge, MA 02139, USA [email protected] 1 Intro duction The rst round of the AES pro cess is coming to an end. Since August of 1998, the cryptographic community has had the opp ortunity to consider each of the fteen prop osed AES candidates. In this note, we take the opp ortunity to answer some of the questions and to resp ond to some of the issues that have b een raised ab out the suitabilityofRC6 as an AES candidate. 2 Encryption/Decryption Performance of RC6 Since the publication of RC6 a variety of researchers and implementors have examined RC6 and considered its p erformance in a wide range of environments. 2.1 32-bit architectures RC6 is one of the fastest AES prop osals on 32-bit architectures, particularly so on the NIST reference platform of a 200 MHz Pentium Pro. It is argued by many that the most reasonable way to assess the p erformance of an algorithm is to consider its sp eed in an assembly language implementation. We agree that this is the case. However it is also interesting to consider how the p erformance of RC6 compares when using di erent compilers. It is imp ortant to note that to take advantage of compiler-sp eci c optimizations the source co de provided to the compiler might need to b e changed. -

An Adaptive-Ciphertext Attack Against I XOR C Block Cipher Modes With
A A-C A “I ⊕ C” B C M W O Jon Passki Tom Ritter [email protected] [email protected] May 24, 2012 Abstract Certain block cipher confidentiality modes are susceptible to an adaptive chosen-ciphertext attack against the underlying format of the plaintext. When the application decrypts altered ciphertext and attempts to process the manipulated plaintext, it may disclose information about intermediate values resulting in an oracle. In this paper we describe how to recognize and exploit such an oracle to decrypt ciphertext and control the decryption to result in arbitrary plaintext. We also discuss ways to mitigate and remedy the issue. 1 I Quoting from [1]: Adaptive chosen-ciphertext attacks on cryptographic protocols allow an attacker to decrypt a cipher- text C, getting the plaintext M, by submitting a series of chosen-ciphertexts C0= 6 C to an oracle which returns information on the decryption. The ciphertexts can be adaptively chosen so that information on previous decryptions is available before the next chosen ciphertext is submitted. Adaptive chosen-ciphertext attacks against different confidentiality modes are not novel. The CBC confidentiality mode can suffer from a side channel attack against padding verification [2], popularized by [3]. A variant of the Cipher Feedback (CFB) confidentiality mode has been attacked in different encryption mail protocols by [4, 5, 1], and the padding schemes of asymmetric ciphers are another source of such attacks [6, 7]. In some form, they rely on the use of an oracle that leaks or communicates information back to attackers. We examine four different confidentiality modes encrypting plaintext that is separated by a delimiter, and the absence or inclusion of that delimiter generates an oracle by the application. -

Cs 255 (Introduction to Cryptography)
CS 255 (INTRODUCTION TO CRYPTOGRAPHY) DAVID WU Abstract. Notes taken in Professor Boneh’s Introduction to Cryptography course (CS 255) in Winter, 2012. There may be errors! Be warned! Contents 1. 1/11: Introduction and Stream Ciphers 2 1.1. Introduction 2 1.2. History of Cryptography 3 1.3. Stream Ciphers 4 1.4. Pseudorandom Generators (PRGs) 5 1.5. Attacks on Stream Ciphers and OTP 6 1.6. Stream Ciphers in Practice 6 2. 1/18: PRGs and Semantic Security 7 2.1. Secure PRGs 7 2.2. Semantic Security 8 2.3. Generating Random Bits in Practice 9 2.4. Block Ciphers 9 3. 1/23: Block Ciphers 9 3.1. Pseudorandom Functions (PRF) 9 3.2. Data Encryption Standard (DES) 10 3.3. Advanced Encryption Standard (AES) 12 3.4. Exhaustive Search Attacks 12 3.5. More Attacks on Block Ciphers 13 3.6. Block Cipher Modes of Operation 13 4. 1/25: Message Integrity 15 4.1. Message Integrity 15 5. 1/27: Proofs in Cryptography 17 5.1. Time/Space Tradeoff 17 5.2. Proofs in Cryptography 17 6. 1/30: MAC Functions 18 6.1. Message Integrity 18 6.2. MAC Padding 18 6.3. Parallel MAC (PMAC) 19 6.4. One-time MAC 20 6.5. Collision Resistance 21 7. 2/1: Collision Resistance 21 7.1. Collision Resistant Hash Functions 21 7.2. Construction of Collision Resistant Hash Functions 22 7.3. Provably Secure Compression Functions 23 8. 2/6: HMAC And Timing Attacks 23 8.1. HMAC 23 8.2. -

Tap Code 1 2 3 4 5 1 a B C D E 2 F G H I J 3 L M N O P 4 Q R S T U 5
Solution to Kryptos 2: Challenge 1 The audio files indicate that the prisoners are communicating with each other by “tapping”. There are two distinct tapping sounds which indicate the two prisoners are exchanging some sort of information back and forth. Furthermore, unlike Morse Code, each audio file is made up of pairs of taps which leads one to believe that each pair of taps corresponds to a word or letter. The longest tapping sequence is five, so if one assumes that each tap-pair corresponds to a pair of integers between 1 and 5, then this code could encipher 25 items – most likely letters. At this point, one could try a frequency analysis to help identify which pairs of integers correspond to which letters. Alternatively, a little research might yield the “tap code” (see e.g. Wikipedia) which has been used by prisoners of war in various conflicts throughout history, most recently Vietnam. It is based on the Polybius square, some of which have slightly different arrangements of the 26 letters placed into 25 cells. Challenge 1 was based on the following key found on Wikipedia: Tap code 1 2 3 4 5 1 A B C D E 2 F G H I J 3 L M N O P 4 Q R S T U 5 V W X Y Z The tap code table This has all letters except “K”, so “C” is used instead. The letter “X” is used to separate sentences. The first audio file begins with the following tap-pairs: (2,4), (4,3), (1,3), (3,4), (5,1), (1,5), (4,2),… which yields the following plaintext: i, s, c, o, v, e, r, … By adding in the likely punctuation, the complete conversation can be decoded: PLAINTEXT Prisoner 1: Is cover intact? Prisoner 2: Yes. -

Side-Channel Attacks
Side-Channel Attacks Aleksei Ivanov 26th November 2005 1 Introduction and patches the result with all 0's.This results in small, constant time when compared to complete Side-channel attacks are described in [5] as follows. multiplication. Timing side channel information Side-channel attacks are attacks that are based on can be obtained either by precisely measuring the side channel information. Side channel Information time taken by one encryption or by averaging the that can be retrieved from the encryption device time taken over several encryptions [4]. that is neither plain text to be encrypted nor the cipher text resulting from the encryption process. There are several kind of side-channel attacks, in 2.2 Power Consumption Attacks the [2] timing attack is referred to as the most Devices consume power and the power dissipated common one. Then There is one kind of informa- by a device is an other side channel. Dierential tion leakage referred to in [1] as power consumption power analysis (DPA) is a power consumption side leakage, that is a big help to the timing attacks. It channel attack that divides the encryption into a is even harder to protect a system against the power number of time slots and measures power in each consumption attacks when attacker has direct ac- slot for dierent plain text input. A small number cess to the encryption device. of the power measurements correlate with each bit The purpose of this paper is to get an overview of the interval stage during encryption [4]. of attacks on encryption systems where an attacker This attack requires little knowledge of the device is using other ways to obtain the encryption key and is dicult to hide the channel information if than breaking the mathematical algorithm. -

Some Words on Cryptanalysis of Stream Ciphers Maximov, Alexander
Some Words on Cryptanalysis of Stream Ciphers Maximov, Alexander 2006 Link to publication Citation for published version (APA): Maximov, A. (2006). Some Words on Cryptanalysis of Stream Ciphers. Department of Information Technology, Lund Univeristy. Total number of authors: 1 General rights Unless other specific re-use rights are stated the following general rights apply: Copyright and moral rights for the publications made accessible in the public portal are retained by the authors and/or other copyright owners and it is a condition of accessing publications that users recognise and abide by the legal requirements associated with these rights. • Users may download and print one copy of any publication from the public portal for the purpose of private study or research. • You may not further distribute the material or use it for any profit-making activity or commercial gain • You may freely distribute the URL identifying the publication in the public portal Read more about Creative commons licenses: https://creativecommons.org/licenses/ Take down policy If you believe that this document breaches copyright please contact us providing details, and we will remove access to the work immediately and investigate your claim. LUND UNIVERSITY PO Box 117 221 00 Lund +46 46-222 00 00 Some Words on Cryptanalysis of Stream Ciphers Alexander Maximov Ph.D. Thesis, June 16, 2006 Alexander Maximov Department of Information Technology Lund University Box 118 S-221 00 Lund, Sweden e-mail: [email protected] http://www.it.lth.se/ ISBN: 91-7167-039-4 ISRN: LUTEDX/TEIT-06/1035-SE c Alexander Maximov, 2006 Abstract n the world of cryptography, stream ciphers are known as primitives used Ito ensure privacy over a communication channel. -

Sok: Design Tools for Side-Channel-Aware Implementations
SoK: Design Tools for Side-Channel-Aware Implementations Ileana Buhan∗, Lejla Batina∗, Yuval Yarom†, and Patrick Schaumont‡ ∗ Radboud University, Digital Security † University of Adelaide and Data61 ‡ Worcester Polytechnic Institute Abstract—Side-channel attacks that leak sensitive information involve collecting side-channel traces, e.g., power traces, from through a computing device’s interaction with its physical envi- the device and analyzing these traces to demonstrate an attack ronment have proven to be a severe threat to devices’ security, or the existence of leaks. While effective, such methodologies particularly when adversaries have unfettered physical access to the device. Traditional approaches for leakage detection measure require the physical device’s presence for evaluation, and this the physical properties of the device. Hence, they cannot be demand poses significant challenges. used during the design process and fail to provide root cause In the pre-silicon stage of the development, the device does analysis. An alternative approach that is gaining traction is to not yet exist; hence it cannot be adequately assessed. Con- automate leakage detection by modeling the device. The demand versely, in the post-silicone stage, detailed design information to understand the scope, benefits, and limitations of the proposed tools intensifies with the increase in the number of proposals. may not be accessible, for example, when using third-party In this SoK, we classify approaches to automated leakage components. Consequently, it may be challenging to identify detection based on the model’s source of truth. We classify the root cause of leakage. Moreover, detecting, verifying, and the existing tools on two main parameters: whether the model mitigating side-channel leaks require expert knowledge and includes measurements from a concrete device and the abstrac- expensive equipment. -

Jan. 2012 Issue
AmateurAmateur AA RR SS SocietySociety NewsNews Newsletter of The Amateur Radio Society of India (Member of IARU) English / Hindi Quarterly Volume I Issue 7 KARBIL/2009/38494 Jan. 2012 Price : Rs.10/- President’s message From the Editor’s desk Dear members all of us active hams are looking at Most of us were privileged to be a part learning more about. Here's wishing you all a HAPPY of Hamfest 2011 which was held in ARSI applied for and obtained special NEW YEAR 2012. More and more Kochi. It was an extremely well suffix for use by all Indian hams in amateurs are showing interest in organised and coordinated event with a commemoration of India's first HUGE gathering of hams and SWL's Formula 1 race meet at Greater Noida. working Satellites, so I have all having a chance to have an eyeball Many hams took an active part in the included a list of operational with their old friends and make new effort in running this most prestigious satellites along with the details. ones. The location and facilities were event. really great. Band conditions seems to be The propagation on the HF bands is improving – I expect a lot of activity The display and sales areas were just picking up nicely and we can hear and this year resulting in more news and like a major exhibition and there was work stations worldwide after a gap of space to move around and see what one some months. reports for me to include in the could pick up for homebrew efforts and newsletter, Hi Please send articles, augment one's shack. -

Bad Cryptography Bruce Barnett Who Am I?
Bad Cryptography Bruce Barnett Who am I? • Security consultant @ NYSTEC • 22 years a research scientist @ GE’s R&D Center • 15 years software developer, system administrator @ GE and Schlumberger • I’m not a cryptographer • I attended a lot of talks at Blackhat/DEFCON • Then I took a course on cryptography……….. Who should attend this talk? • Project Managers • Computer programmers • Those that are currently using cryptography • Those that are thinking about using cryptography in systems and protocols • Security professionals • Penetration testers who don’t know how to test cryptographic systems and want to learn more • … and anybody who is confused by cryptography Something for everyone What this presentation is … • A gentle introduction to cryptography • An explanation why cryptography can’t be just “plugged in” • Several examples of how cryptography can be done incorrectly • A brief description of why certain choices are bad and how to exploit it. • A checklist of warning signs that indicate when “Bad Cryptography” is happening. Example of Bad Cryptography!!! Siren from snottyboy http://soundbible.com/1355-Warning-Siren.html What this talk is not about • No equations • No certificates • No protocols • No mention of SSL/TLS/HTTPS • No quantum cryptography • Nothing that can cause headaches • (Almost) no math used Math: Exclusive Or (XOR) ⊕ Your Cat Your Roommates' Will you have Cat kittens? No kittens No kittens Note that this operator can “go backwards” (invertible) What is encryption and decryption? Plain text Good Morning, Mr. Phelps -
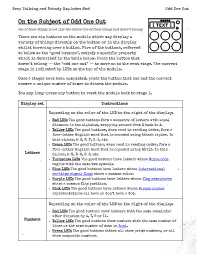
On the Subject of Odd One Out
Keep Talking and Nobody Explodes Mod Odd One Out On the Subject of Odd One Out One of these things is not like the others! One of these things just doesn’t belong! There are six buttons on the module which may display a variety of things directly on the button or in the display whilst hovering over a button. Five of the buttons, referred to below as the “good buttons”, satisfy a specific property which is described in the table below. Press the button that doesn’t belong — the “odd one out” — to move on to the next stage. The current stage is indicated by LEDs at the top of the module. Once 5 stages have been completed, press the button that has had the correct answer a unique number of times to disarm the module. You may long-press any button to reset the module back to stage 1. Display set Instructions Depending on the color of the LED to the right of the display: Red LED: The good buttons form a sequence of letters with equal distance in the alphabet, wrapping around from Z back to A. Yellow LED: The good buttons, when read in reading order, form a five-letter English word that is encoded using Atbash cipher. In this cipher, A↔Z, B↔Y, C↔X, etc. Green LED: The good buttons, when read in reading order, form a five-letter English word that is encoded using ROT13. In this Letters cipher, A↔N, B↔O, C↔P, etc. Turquoise LED: The good buttons have letters whose Morse code begins with the same two symbols.