Leaderless Politics
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Romanian Political Science Review Vol. XXI, No. 1 2021
Romanian Political Science Review vol. XXI, no. 1 2021 The end of the Cold War, and the extinction of communism both as an ideology and a practice of government, not only have made possible an unparalleled experiment in building a democratic order in Central and Eastern Europe, but have opened up a most extraordinary intellectual opportunity: to understand, compare and eventually appraise what had previously been neither understandable nor comparable. Studia Politica. Romanian Political Science Review was established in the realization that the problems and concerns of both new and old democracies are beginning to converge. The journal fosters the work of the first generations of Romanian political scientists permeated by a sense of critical engagement with European and American intellectual and political traditions that inspired and explained the modern notions of democracy, pluralism, political liberty, individual freedom, and civil rights. Believing that ideas do matter, the Editors share a common commitment as intellectuals and scholars to try to shed light on the major political problems facing Romania, a country that has recently undergone unprecedented political and social changes. They think of Studia Politica. Romanian Political Science Review as a challenge and a mandate to be involved in scholarly issues of fundamental importance, related not only to the democratization of Romanian polity and politics, to the “great transformation” that is taking place in Central and Eastern Europe, but also to the make-over of the assumptions and prospects of their discipline. They hope to be joined in by those scholars in other countries who feel that the demise of communism calls for a new political science able to reassess the very foundations of democratic ideals and procedures. -

1 the European Court of Justice Case of Breyer Mr. Alan S. Reid Sheffield
The European Court of Justice case of Breyer Mr. Alan S. Reid Sheffield Hallam University Abstract This case note analyses the impact and significance of the European Court of Justice decision in Breyer. The European Court of Justice has expanded the definition of personal data to include dynamic IP addresses. The judgment improves the privacy situation of internet users across the European Union. The facts of Breyer1 Patrick Breyer is a German politician and activist who belongs to the Pirate Party. The Pirate Party was originally set up in Sweden in 2006, as a single issue political party, committed to the modernisation of copyright law in Sweden, following the crackdown on The Pirate Bay peer-to-peer network. After limited success in Sweden, sister parties sprung up across Europe, in order to capitalise on the notoriety of The Pirate Bay. In order to broaden their appeal, the European Pirate Parties set out common themes of campaigning interest, in particular, on issues surrounding the internet, such as open access to information, freedom of expression and privacy. As a technophile and politician committed to internet freedoms, Patrick Breyer vociferously objected to various Federal German government websites retaining details of his dynamic Internet Protocol (IP) address after he had completed browsing. Internet Protocol (IP) addresses are the essential backbone of the internet. Internet protocols are the method by which interconnected computers and devices communicate, share and transfer data between themselves. An IP address consists of either four pairs of numbers (version 4)2 separated by three colons or eight pairs of numbers separated by six colons (version 6).3 The US organisation ICANN4, the Internet Corporation for Assigned Names and Numbering, is tasked with overseeing the interconnectivity and compatibility required for the continued successful operation of the internet infrastructure. -

Direct E-Democracy and Political Party Websites: in the United States and Sweden
Rochester Institute of Technology RIT Scholar Works Theses 5-1-2015 Direct E-Democracy and Political Party Websites: In the United States and Sweden Kirk M. Winans Follow this and additional works at: https://scholarworks.rit.edu/theses Recommended Citation Winans, Kirk M., "Direct E-Democracy and Political Party Websites: In the United States and Sweden" (2015). Thesis. Rochester Institute of Technology. Accessed from This Thesis is brought to you for free and open access by RIT Scholar Works. It has been accepted for inclusion in Theses by an authorized administrator of RIT Scholar Works. For more information, please contact [email protected]. Running head: E-DEMOCRACY AND POLITICAL PARTY WEBSITES Direct E-Democracy and Political Party Websites: In the United States and Sweden by Kirk M. Winans Thesis Submitted in Partial Fulfillment of the Graduation Requirements for the Degree of Master of Science Science, Technology and Public Policy Department of Public Policy College of Liberal Arts Rochester Institute of Technology May 1, 2015 E-DEMOCRACY AND POLITICAL PARTY WEBSITES Direct E-Democracy and Political Party Websites: In the United States and Sweden A thesis submitted to The Public Policy Department at Rochester Institute of Technology By Kirk M. Winans Under the faculty guidance of Franz Foltz, Ph.D. Submitted by: Kirk M. Winans Signature Date Accepted by: Dr. Franz Foltz Thesis Advisor, Graduate Coordinator Signature Date Associate Professor, Dept. of STS/Public Policy Rochester Institute of Technology Dr. Rudy Pugliese Committee Member Signature Date Professor, School of Communication Rochester Institute of Technology Dr. Ryan Garcia Committee Member Signature Date Assistant Professor, Dept. -

Institute for Information Law Self-Assessment Report (2009–2015)
Institute for Information Law Self-Assessment Report (2009–2015) ivir self-assessment report (2009–2015) Amsterdam, March 2016 Institute for Information Law (IViR) Vendelstraat 7 1012 XX Amsterdam The Netherlands Website: http://ivir.nl/ Phone: + 31 (0)20 525 3406 Email: [email protected] Layout: Suzanne Bakkum 2 ivir self-assessment report (2009–2015) Table of Contents Section I Description of the research group and its research program 1 1.1 Organization 1 Title 1 General description 1 Composition 1 Organization 1 Financing 2 1.2 Overall strategy 2 Mission and vision 2 Paradigm and research methods 2 Research profile and strategy 3 1.3 Past and future targets 4 1.4 Applicable performance indicators 5 Research quality 6 Relevance to society 6 1.5 Results obtained 7 Societal relevance 11 1.6 Own assessment of quality, relevance and viability 14 Research quality 15 Relevance to society 15 Viability 15 Previous external assessments 15 1.7 Relevant environmental factors and developments 16 1.8 SWOT analysis and benchmark/positioning 17 Benchmarks 18 Section II Appendices 19 2.1 Table describing the composition of the research unit 19 2.2 Table reflecting the publications output 20 2.3 Table indicating the research unit’s financing structure 21 2.4 Five most important scientific publications 21 2.5 Five most important societal publications 22 2.6 Previous external assessment reports 23 2.7 Awards and individual research grants 31 Prizes, honors and awards 31 Individual research grants 32 2.8 Publications output 33 2.9 Reports and studies of societal -

European Union Launches Full Scale War Against Internet Privacy with #Chatcontrol (Eprivacy Derogation)
European Union launches full scale war against internet privacy with #ChatControl (ePrivacy Derogation) On July 6, 2021, the European Union voted on the new “ChatControl” proposal. With a shocking number of 537 Members of the European Parliament voting in favor, 133 voting against and 20 abstentions, it was approved. The proposal was put forward under the banner of “emergency measures” and it allows internet companies to scan users’ private messages for material containing child sex abuse. This controversial decision is supposed to fix problems with the European Electronics Communications Code, which came into force last December. The so called “e-Privacy Interim Regulation” (2020/0259(COD)) requires online messenger and email service providers to automatically scan private message content in real time for suspicious text and image content using error-prone artificial intelligence. All cases identified by AI would be automatically disclosed to investigative authorities in the EU, without the individuals concerned knowing about it. This is intended to counter the spread of child pornography on the internet, at least that is the story behind it. But the EU’s plans for ChatControl have beenconfirmed to violate fundamental rights by a former judge of the European Court of Justice. The delegation of the European Pirate Party inserted in the Greens / EFA group has strongly condemned what it considers automated mass surveillance, which as they say means the end of privacy in digital correspondence. German Pirate Party Member of the European Parliament Patrick Breyer plans to take legal action against the regulation and is looking for victims of abuse who would file such a complainant. -

PL&B International
ANALYSIS European Union court rules that IP addresses are personal data The Breyer case, another landmark ruling on key data protection notions, covers the definition of personal data in relation to dynamic IP addresses and the “legitimate interest” legal basis for data processing. By Monika Kuschewsky . he Court of Justice of the EU only temporarily assigned and change website was accessed, or that of another (CJEU) has yet again issued an each time there is a new connection person who might use that computer. important ruling, interpreting from a computer or device to the Inter - The CJEU then considered whether Tkey notions of the EU Data Protection net. Website operators (as opposed to dynamic IP addresses may be treated as Directive (the Directive) in its recent Internet service providers, ISPs) do not personal data relating to an “identifi - judgement of 19 October 2016 in the usually possess all the information to able natural person”, who can be iden - Case Patrick Breyer vs. Bundesrepub - identify the users behind the IP tified indirectly. In interpreting this lik Deutschland (C -582/14). In particu - address. provision, the CJEU made two lar, the CJEU answered two questions, Though initially dismissed by a important statements: namely: (1) whether dynamic IP lower court, the case was brought • first, “it is not necessary that that addresses constitute personal data for before Germany’s highest civil court information alone allows the data website operators and (2) concerning (the Bundesgerichtshof or BGH), subject to be identified;” and, the permissible scope of Member which referred two questions for a pre - • second, “it is not required that all States’ implementing legislation con - liminary ruling to the CJEU. -

Revalidating Participation: Power and Pre - Figurative Politics Within Contemporary Leftwing Movements
Bart Cammaerts Revalidating participation: power and pre - figurative politics within contemporary leftwing movements Book section Original citation: Cammaerts, Bart (2019) Revalidating participation: power and pre -figurative politics within contemporary leftwing movements. In: Carpentier, Nico, (ed.) Respublika!: Experiments in the performance of participation and democracy. NeMe, Limassol, Cyprus, pp. 126-137. ISBN 9789963969586 © 2019 The Author This version available at: http://eprints.lse.ac.uk/id/eprint/91502 Available in LSE Research Online: January 2019 LSE has developed LSE Research Online so that users may access research output of the School. Copyright © and Moral Rights for the papers on this site are retained by the individual authors a nd/or other copyright owners. Users may download and/or print one copy of any article(s) in LSE Research Online to facilitate their private study or for non-commercial research. You may not engage in further distribution of the material or use it for any profit-making activities or any commercial gain. You may freely distribute the URL ( http://eprints.lse.ac.uk ) of the LSE Research Online website. This document is the author’s submitted version of the book section. There may be differences between this ve rsion and the published version. You are advised to consult the publisher’s version if you wish to cite from it. Revalidating Participation: Power and Pre-Figurative Politics within Contemporary Leftwing Movements 1 Bart Cammaerts London School of Economics and Political Science Introduction ‘Practice what you preach’ is a popular idiom not only within progressive politics, but also beyond, and this idea is also encapsulated in the famous Mahatma Gandhi quote: ‘If you want to change the world, start with yourself’. -

ESS9 Appendix A3 Political Parties Ed
APPENDIX A3 POLITICAL PARTIES, ESS9 - 2018 ed. 3.0 Austria 2 Belgium 4 Bulgaria 7 Croatia 8 Cyprus 10 Czechia 12 Denmark 14 Estonia 15 Finland 17 France 19 Germany 20 Hungary 21 Iceland 23 Ireland 25 Italy 26 Latvia 28 Lithuania 31 Montenegro 34 Netherlands 36 Norway 38 Poland 40 Portugal 44 Serbia 47 Slovakia 52 Slovenia 53 Spain 54 Sweden 57 Switzerland 58 United Kingdom 61 Version Notes, ESS9 Appendix A3 POLITICAL PARTIES ESS9 edition 3.0 (published 10.12.20): Changes from previous edition: Additional countries: Denmark, Iceland. ESS9 edition 2.0 (published 15.06.20): Changes from previous edition: Additional countries: Croatia, Latvia, Lithuania, Montenegro, Portugal, Slovakia, Spain, Sweden. Austria 1. Political parties Language used in data file: German Year of last election: 2017 Official party names, English 1. Sozialdemokratische Partei Österreichs (SPÖ) - Social Democratic Party of Austria - 26.9 % names/translation, and size in last 2. Österreichische Volkspartei (ÖVP) - Austrian People's Party - 31.5 % election: 3. Freiheitliche Partei Österreichs (FPÖ) - Freedom Party of Austria - 26.0 % 4. Liste Peter Pilz (PILZ) - PILZ - 4.4 % 5. Die Grünen – Die Grüne Alternative (Grüne) - The Greens – The Green Alternative - 3.8 % 6. Kommunistische Partei Österreichs (KPÖ) - Communist Party of Austria - 0.8 % 7. NEOS – Das Neue Österreich und Liberales Forum (NEOS) - NEOS – The New Austria and Liberal Forum - 5.3 % 8. G!LT - Verein zur Förderung der Offenen Demokratie (GILT) - My Vote Counts! - 1.0 % Description of political parties listed 1. The Social Democratic Party (Sozialdemokratische Partei Österreichs, or SPÖ) is a social above democratic/center-left political party that was founded in 1888 as the Social Democratic Worker's Party (Sozialdemokratische Arbeiterpartei, or SDAP), when Victor Adler managed to unite the various opposing factions. -

Luxembourg PATRICK DUMONT, RAPHAËL KIES & PHILIPPE
1 Luxembourg PATRICK DUMONT, RAPHAËL KIES & PHILIPPE POIRIER Université du Luxembourg Table 1. Cabinet composition of Juncker-Asseblorn II (or Juncker IV) For the composition of Juncker-Asseblorn II (or Juncker IV) on 1 January 2012, see Dumont et al. (2010: 1078–1079). Changes during 2012: Minister of Economy and Foreign Trade/Ministre de l’Économie et du Commerce extérieur: Jeannot Krecké (1950 male, LSAP) resigned and replaced by Etienne Schneider (1971 male, LSAP) on 1st February 2012. Institutional changes A number of decisions voted on by the Chamber of Deputies in 2011 became effective in 2012: first, as part of a long-term plan of reduction in the number of municipalities, sixteen of them merged into six new entities as of 1 January (Dumont et al. 2010; 2012: 202-205).. Second, as decided by a vote in December 2011, a new ombudsman (“mediateure”) was appointed. On 1 February, Lydie Err, former Socialist MP (and junior minister in 1998–9) took over from Marc Fischbach, who had been a Christian-democratic MEP, government minister in the 1990s, and a judge at the European Court of Human Rights, before being chosen as Luxembourg’s first ombudsman by parliamentary vote in December 2003. Err’s mandate is to last until 2020. Also on 1 February the socialist Etienne Schneider took office, as scheduled by an internal Socialist Worker’s Party (LSAP) vote in November 2011 (Dumont et al. 2012: 201), replacing Jeannot Krecké as Minister of Economy and Foreign Trade. The latter had made his frustration about his role in the government known to the public as early as 2010, arguing that the Economy portfolio was a coordination ministry deprived of the instruments that would enable its holder to initiate and implement reforms. -

'We Want Artists to Be Fully and Fairly Paid for Their Work'
Ananay Aguilar ‘We want Artists to be Fully and Fairly Paid for their Work’ Discourses on Fairness in the Neoliberal European Copyright Reform by Ananay Aguilar* Abstract: Elaborating on the President of the right reform—I shed light on the powerful discourses European Commission Jean-Claude Juncker’s agenda, on fairness that have dominated and shaped the re- EC Vice-President and Commissioner for the Digi- form process. Using discourse analysis, I found the tal Single Market Andrus Ansip wrote on his blog on concept of fairness to be mostly dependent on the 18th November 2015, “we want artists to be fully and stakeholders’ relative bargaining power and framed fairly paid for their work”—the phrase that serves as by hegemonic neo-liberal thought. Drawing on inter- the title to this article and that has reappeared in dif- views, fieldwork, media, and the documentation pro- ferent guises throughout the process of EU copy- duced by the European Union’s government through- right reform. By examining a case study on the Fair out the process, the case study also illustrates the Internet for Performers Campaign—a campaign ad- contested nature of copyright reform today. vanced in the context of the ongoing European copy- Keywords: Fairness; discourse analysis; copyright reform; EU; neo-liberalism © 2018 Ananay Aguilar Everybody may disseminate this article by electronic means and make it available for download under the terms and conditions of the Digital Peer Publishing Licence (DPPL). A copy of the license text may be obtained at http://nbn-resolving. de/urn:nbn:de:0009-dppl-v3-en8. -

Dear President of the European Parliament, Dear President of The
Dear President of the European Parliament, Dear President of the European Council, Dear President of the European Commission and Dear President of the French Republic, We all have a responsibility for the shared future of Europe. In this time of crisis, it is high time to re-evaluate some of the rules we have upheld till now and focus on the most important aspects of the European project, which will help us move forward. An unprecedented health crisis is currently affecting millions of people in Europe and tragically taking thousands of lives. However, this is not the end. The economic crisis will crush the hopes and dreams of generations of Europeans. We sincerely hope that we will all do whatever is in our power not to leave anyone behind. We firmly believe that the European Parliament needs to take on its responsibility and share the burden since it is the highest European directly elected body. We need to be part of the solution, not part of the problem. If we want the people to have confidence and trust in the European project, we need to show them that we are also ready to make concessions. Therefore, we would like to ask you to do everything in your power to change the treaties in order to have just a single seat of the Parliament in Brussels. This call has again gained a large majority of support in the 2018 Parliament discharge resolution adopted on 13 May 2020 and shall now be taken into account and acted upon. The financial and environmental costs of moving the Parliament are, especially in these times of digitally connected Europe, extremely high and hard to justify. -
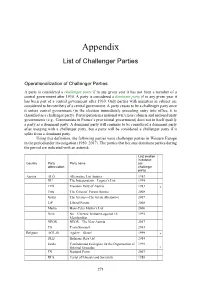
Challenger Party List
Appendix List of Challenger Parties Operationalization of Challenger Parties A party is considered a challenger party if in any given year it has not been a member of a central government after 1930. A party is considered a dominant party if in any given year it has been part of a central government after 1930. Only parties with ministers in cabinet are considered to be members of a central government. A party ceases to be a challenger party once it enters central government (in the election immediately preceding entry into office, it is classified as a challenger party). Participation in a national war/crisis cabinets and national unity governments (e.g., Communists in France’s provisional government) does not in itself qualify a party as a dominant party. A dominant party will continue to be considered a dominant party after merging with a challenger party, but a party will be considered a challenger party if it splits from a dominant party. Using this definition, the following parties were challenger parties in Western Europe in the period under investigation (1950–2017). The parties that became dominant parties during the period are indicated with an asterisk. Last election in dataset Country Party Party name (as abbreviation challenger party) Austria ALÖ Alternative List Austria 1983 DU The Independents—Lugner’s List 1999 FPÖ Freedom Party of Austria 1983 * Fritz The Citizens’ Forum Austria 2008 Grüne The Greens—The Green Alternative 2017 LiF Liberal Forum 2008 Martin Hans-Peter Martin’s List 2006 Nein No—Citizens’ Initiative against