RSA DLP Support Matrix
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
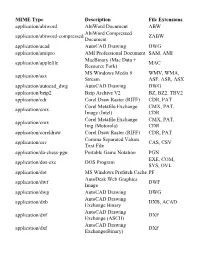
MIME Type Description File Extensions Application/Abiword
MIME Type Description File Extensions application/abiword AbiWord Document ABW AbiWord Compressed application/abiword-compressed ZABW Document application/acad AutoCAD Drawing DWG application/amipro AMI Professional Document SAM, AMI MacBinary (Mac Data + application/applefile MAC Resource Fork) MS Windows Media 9 WMV, WMA, application/asx Stream ASF, ASR, ASX application/autocad_dwg AutoCAD Drawing DWG application/bzip2 Bzip Archive V2 BZ, BZ2, TBV2 application/cdr Corel Draw Raster (RIFF) CDR, PAT Corel Metafile Exchange CMX, PAT, application/cmx Image (Intel) CDR Corel Metafile Exchange CMX, PAT, application/cmx Img (Motorola) CDR application/coreldraw Corel Draw Raster (RIFF) CDR, PAT Comma Separated Values application/csv CAS, CSV Text File application/da-chess-pgn Portable Game Notation PGN EXE, COM, application/dos-exe DOS Program SYS, OVL application/dot MS Windows Prefetch Cache PF AutoDesk Web Graphics application/dwf DWF Image application/dwg AutoCAD Drawing DWG AutoCAD Drawing application/dxb DXB, ACAD Exchange Binary AutoCAD Drawing application/dxf DXF Exchange (ASCII) AutoCAD Drawing application/dxf DXF Exchange(Binary) EMF, TMP, EMF, TMP, application/emf Windows Enhanced Metafile WMF application/envoy Envoy Document EVY, ENV Comma Separated Values application/excel CAS, CSV Text File MS Excel XLS, XLA, application/excel Worksheet/Add-In/Template XLT, XLB EXE, COM, application/exe DOS Program SYS, OVL EXE, VXD, application/exe MS Windows Driver (16 bit) SYS, DRV, 386 MS Windows Program (16 application/exe EXE, MOD, BIN bit) -
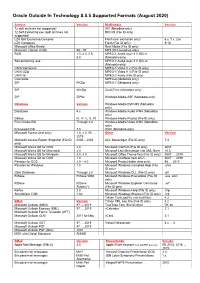
Supported Formats (August 2020)
Oracle Outside In Technology 8.5.5 Supported Formats (August 2020) Archive Version Multimedia Version 7z split archives not supported) AVI (Metadata only) 7z Self Extracting exe (split archives not DICOM (File ID only) supported) LZA Self Extracting Compres Flash (text extraction only) 6.x, 7.x, Lite LZH Compress Flash (File ID only) 9,10 Microsoft Office Binder Real Media (File ID only) Microsoft Cabinet (CAB) 95 – 97 MP3 (ID3 metadata only) RAR 1.5, 2.0, 2.9, MPEG-1 Audio layer 3 V ID3 v1 5.0 (Metadata only) Self-extracting .exe MPEG-1 Audio layer 3 V ID3 v2 (Metadata only) UNIX Compress MPEG-1 Video V 2 (File ID only) UNIX GZip MPEG-1 Video V 3 (File ID only) UNIX tar MPEG-2 Audio (File ID only) Uuencode MPEG-4 (Metadata only) ZIP PKZip MPEG-7 (Metadata only) ZIP WinZip QuickTime (Metadata only) ZIP ZIP64 Windows Media ASF (Metadata only) Database Version Windows Media DVR-MS (Metadata only) DataEase 4.x Windows Media Audio WMA (Metadata only) DBase III, IV, V, X, X1 Windows Media Playlist (File ID only) First Choice DB Through 3.0 Windows Media Video WMV (Metadata only) Framework DB 3.0 WAV (Metadata only) Microsoft Access (text only) 1.0, 2.0, 95 … Other Version 2019 Microsoft Access Report Snapshot (File ID 2000 – 2003 AOL Messenger (File ID only) 7.3 only) Microsoft Works DB for DOS 2.0 Microsoft InfoPath (File ID only) 2007 Microsoft Works DB for Macintosh 2.0 Microsoft Live Messenger (via XML filter) 10.0 Microsoft Works DB for Windows 3.0, 4.0 Microsoft Office Theme files (File ID only) 2007 … 2019 Microsoft Works DB for DOS -

Docuarchive Product Sheet
DocuArchive Product Sheet Contents 1 What this document contains ............................................................................................... 3 2 DocuArchive Server components ........................................................................................ 3 2.1 DocuArchive ArchiveServer ..................................................................................................... 3 2.1.1 Hardware and software requirements ...................................................................................... 3 2.1.2 Runtime environment ............................................................................................................... 3 2.1.3 Supported storage technologies .............................................................................................. 4 2.1.4 Quantitative characteristics ...................................................................................................... 5 2.2 DocuArchive MediaServer ....................................................................................................... 6 2.2.1 Runtime requirements .............................................................................................................. 6 2.2.2 Hardware and software requirements ...................................................................................... 6 2.3 DocuArchive DBServer ............................................................................................................ 6 2.3.1 Hardware and software requirements ..................................................................................... -

IBM Lotus Notes/Domino Next - New Ways to Work …
Уффе Соренсен IBM Lotus Notes/Domino Next - New ways to work … @uffesorensen usorensen #ibmsocbiz ● Major new release of all components ● Notes / Domino / iNotes 8.5.4 - the “Social Edition” Public Beta (based on Code Drop 6) in mid-Nov 2012 Target General Availability 1q2013 Notes and Domino software The flexible and comprehensive collaboration solution & application platform The Users: The Servers: ● Notes (Mac, Linux, Windows) ● Domino ● ● iNotes Universal access IBM XWork ● Notes Traveler ● Internet Explorer Remain productive regardless of location ● Firefox ● Safari Browser ● iOS Open application ● Android development ● Rich Nokia clients Fully extensible, standards-based, Web 2.0 / OpenSocial 2.0, XPages Advanced Collaboration collaboration foundation Collaboration capabilities Mobile E-mail, calendar, in context contacts, Instant messaging, user profiles Seamless, file sharing, office uninterrupted workflow, productivity tools activity stream Proven, reliable & scalable infrastructure Security-rich, high availability, simple upgrades ©2012 IBM Corporation The Notes rich client: Your “everything working together” - in one place ... Social Networks: Social File Activities, Blogs, Wikis, .. Sharing Standard Instant Web Browser Messaging of the operating system Documents, Feeds, Presentations, My Widgets, Spreadsheets Live Text Compositions / mashups of E-Mail, collaborative and Calendar, Contacts Business Apps One intuitive UI as the central place where everything integrates in context ©2012 IBM Corporation Lotus Notes / Domino -

Introduction
Introduction The m-Learning Initiative The multi-touch book that you have has been designed to house the content for a college course at Kennebec Valley Community College. The course is part of KVCC’s Associates of Science in Psychology. The Social Sciences and Psychology Department created this m-Learning Initiative and initiated a 1:1 Apple iPad program. Curricula in the courses has been geared to take advantage of the hardware and software tools of the iPad to: Enhance in-class teaching methods. Elevate assessment and evaluation of authentic artifacts that demonstrate student learning. Increase student-to-student interaction and student-to-teacher interaction. Prepare students for the emerging mobile-computing based workplace. Other instructors at other institutions wishing to use this material are free to access the CourseBook in the Apple Bookstore. CourseBooks The CourseBook series has been developed to enhance the delivery of course content across the entire program and take advantage of the tools within Apple’s ecosystem in order to deliver more engaging course materials with embedded interactions, video, and links to apps and web content that support teaching and learning. The content of these CourseBooks have been developed by the authors and represents independent scholarly activity on the part of each author who has contributed to the development of each CourseBook. How to use this CourseBook For the students within the Mental Health Program, the content of this CourseBook aligns with activities, expectations, and assignments that are found in the KVCC Learning Management System (LMS). Students are expected to read and absorb the information in the CourseBook, review the Assessment expectations outlined in each Chapter, and participate in the expectations set by the Instructor of the course in the LMS. -

Mac OS X: an Introduction for Support Providers
Mac OS X: An Introduction for Support Providers Course Information Purpose of Course Mac OS X is the next-generation Macintosh operating system, utilizing a highly robust UNIX core with a brand new simplified user experience. It is the first successful attempt to provide a fully-functional graphical user experience in such an implementation without requiring the user to know or understand UNIX. This course is designed to provide a theoretical foundation for support providers seeking to provide user support for Mac OS X. It assumes the student has performed this role for Mac OS 9, and seeks to ground the student in Mac OS X using Mac OS 9 terms and concepts. Author: Robert Dorsett, manager, AppleCare Product Training & Readiness. Module Length: 2 hours Audience: Phone support, Apple Solutions Experts, Service Providers. Prerequisites: Experience supporting Mac OS 9 Course map: Operating Systems 101 Mac OS 9 and Cooperative Multitasking Mac OS X: Pre-emptive Multitasking and Protected Memory. Mac OS X: Symmetric Multiprocessing Components of Mac OS X The Layered Approach Darwin Core Services Graphics Services Application Environments Aqua Useful Mac OS X Jargon Bundles Frameworks Umbrella Frameworks Mac OS X Installation Initialization Options Installation Options Version 1.0 Copyright © 2001 by Apple Computer, Inc. All Rights Reserved. 1 Startup Keys Mac OS X Setup Assistant Mac OS 9 and Classic Standard Directory Names Quick Answers: Where do my __________ go? More Directory Names A Word on Paths Security UNIX and security Multiple user implementation Root Old Stuff in New Terms INITs in Mac OS X Fonts FKEYs Printing from Mac OS X Disk First Aid and Drive Setup Startup Items Mac OS 9 Control Panels and Functionality mapped to Mac OS X New Stuff to Check Out Review Questions Review Answers Further Reading Change history: 3/19/01: Removed comment about UFS volumes not being selectable by Startup Disk. -

GNU CPIO GNU Cpio 2.5 June 2002
GNU CPIO GNU cpio 2.5 June 2002 by Robert Carleton Copyright c 1995, 2001, 2002 Free Software Foundation, Inc. This is the first edition of the GNU cpio documentation, and is consistent with GNU cpio 2.5. Published by the Free Software Foundation 59 Temple Place - Suite 330, Boston, MA 02111-1307, USA Permission is granted to make and distribute verbatim copies of this manual provided the copyright notice and this permission notice are preserved on all copies. Permission is granted to copy and distribute modified versions of this manual under the con- ditions for verbatim copying, provided that the entire resulting derived work is distributed under the terms of a permission notice identical to this one. Permission is granted to copy and distribute translations of this manual into another lan- guage, under the above conditions for modified versions, except that this permission notice may be stated in a translation approved by the Free Software Foundation. Chapter 2: Tutorial 1 1 Introduction GNU cpio copies files into or out of a cpio or tar archive, The archive can be another file on the disk, a magnetic tape, or a pipe. GNU cpio supports the following archive formats: binary, old ASCII, new ASCII, crc, HPUX binary, HPUX old ASCII, old tar, and POSIX.1 tar. The tar format is provided for compatability with the tar program. By default, cpio creates binary format archives, for compatibility with older cpio programs. When extracting from archives, cpio automatically recognizes which kind of archive it is reading and can read archives created on machines with a different byte-order. -

IBM PC Club IBM PC Club
San Jose PC CI ub Newsletter Document Number SJPCN03 May 4, 1982 Edited by Bonnie Lamb F98/142 San Jose 8 + 276-3653 VM(SJEVMl/LAMB) IBM PC Club IBM PC Club CONTENTS IBM SAN JOSE PC NEWSLETTER 1 Errata 1 April Meeting . 2 Special Interest Groups (SIG) 3 Survey Results ....... 3 San Jose PC Club Profile 5 Tips and Techniques 6 Programming notes 8 Electrohome 1302 Color Monitor with the PC 11 VOLKSWRITER Comparison to EASYWRITER 12 PC Puzzler 14 I nstall Notes 16 PC Club Program Library Directory 17 PC Add-Ons .... 19 SORT Comparisons 20 Help Wanted/Help Offered 21 Classified 22 PC Newsletter Articles 23 ii SJPCN03 05/04/82 IBM PC Club IBM SAN JOSE PC NEWSLETTER This month's newsletter has some survey results, sort performance information, a crossword puzzle (don't peek at the answers), and other good stuff. Time is short, we should have gone to press yesterday, so I'll close with next month's activity schedule: DATE DAY TIME LOCATION EVENT May 11 Tue. 5 p.m. STL Cafeteria PC Club Meeting May 12 Wed. 7:30p.m. DYSAN Santa Clara SVCC May 18 Tue. 5 p.m. STL K210 Phototypsetting SIG May 25 Tue. 5 p.m. STL K210 Visiclub (SIG) Meeting June 1 Tue. 5 p.m. STL K210 Advisory Meeting ERRATA The Silicon Valley Computer Club (SVCC) has found a bug in the BIOS modification that was printed in SJPCNOI to allow double-sided floppies. Details of symptoms and a possible fix are in the works. Look in next month's newsletter for this in formation. -

DECEMBER 1984 Editorial
SECRET UJUJUVC!JUJUJlb f5l5CBl!JWVU~ !D~~WCB~ Cf l!l U1 v ffil! f] Ill~(! ffi g 00 (!{il C!J l! '7 00 {iJ U1 ~ [1{iJ w~ NOV-DEC 1984 EO 1. 4. (c) P .L. 86- 36 . TRENDS IN HF COMMUNICATIONS (U) •••••••••••• • ••• J.._ ___---..._.1. \\:>............ 1 • SWITCHBOARD: • PAST, PRESENT AND FUTURE (U) •• ~ ............. I • • \ I .......... 5 \ OUT OF MY DEPTH (U) .......................•............•...; .. i .. \ ... ·........ 7 . • • • • • • • • • • • • • • • • • • • • • • ! I ...\ .......... s 1 EXPLORING A DOS DISKETTE (U)................... I ...... :; , ........ 12 HUMAN FACTORS (U) •••••••••••••••••••••••••••••• I l ........ 22 CAN YOU TOP THIS? (U) ........................... E. Leigh Sawyer ... , \~ ••••••• 24 PERSONAL COMPUTING IN A GROUP (U).............. • •••••• 25 FACTION LINE (U) ••• , •••••••••••••••••••••••• • ••• Cal Q. Lator •••••••••••••• • 35 NSA-CROSTIC NO. 59 (U) •••.•••••••••••••••••••••• D.H.W.;.,, ••••••••••••••••• 36 'flllS BOC\'.JMBNT <JONTl.INS <JOBl'JWORB MATl'JRIAh Ghi'tSSIFIEB BY tfSA/SSSM lH 2 SECRET BEGI:a\-SSIFY 0N. 0r igiriet iug Agency's Betezminatior:t Reqaized Declassified and Approved for Release by NSA on 'I 0- '16-2012 pursuant to E 0 . 13526, MOR Case # 54 77B OCID: 4009933 Published by Pl, Techniques and Standards EO 1. 4. ( c) P~L. 86-36 VOL. XI, No. 11-12 NOVEMBER-DECEMBER 1984 Editorial PUBLISHER BOARD OF EDITORS Edi.tor ...•••......_I _______ ... 1(963-3045s .) Product ion .•....•. I .(963-3369s) . : : : :· Collection .••••••..•••• i------.jc963-396ls) Computer Security •: ' •••••• 1 ,(859-6044) Cryptolinguist ics. l 963-1 f03s) Data Systems .•...•.•• ·l ., 963-4,953s) Information Science " • ..... I lc963-.5111s> Puzzles .......... David H. Williams'f(9637'Il03s) Special Research • ..•. Vera R. Filby;! C968'-7119s) Traffic Analysis •. Robert J. Hanyo!<f! (968-3888s) For subscript ions .. , send name and organizat~on to: I w14I i P.L. -

Symantec Web Security Service Policy Guide
Web Security Service Policy Guide Revision: NOV.07.2020 Symantec Web Security Service/Page 2 Policy Guide/Page 3 Copyrights Broadcom, the pulse logo, Connecting everything, and Symantec are among the trademarks of Broadcom. The term “Broadcom” refers to Broadcom Inc. and/or its subsidiaries. Copyright © 2020 Broadcom. All Rights Reserved. The term “Broadcom” refers to Broadcom Inc. and/or its subsidiaries. For more information, please visit www.broadcom.com. Broadcom reserves the right to make changes without further notice to any products or data herein to improve reliability, function, or design. Information furnished by Broadcom is believed to be accurate and reliable. However, Broadcom does not assume any liability arising out of the application or use of this information, nor the application or use of any product or circuit described herein, neither does it convey any license under its patent rights nor the rights of others. Policy Guide/Page 4 Symantec WSS Policy Guide The Symantec Web Security Service solutions provide real-time protection against web-borne threats. As a cloud-based product, the Web Security Service leverages Symantec's proven security technology, including the WebPulse™ cloud community. With extensive web application controls and detailed reporting features, IT administrators can use the Web Security Service to create and enforce granular policies that are applied to all covered users, including fixed locations and roaming users. If the WSS is the body, then the policy engine is the brain. While the WSS by default provides malware protection (blocks four categories: Phishing, Proxy Avoidance, Spyware Effects/Privacy Concerns, and Spyware/Malware Sources), the additional policy rules and options you create dictate exactly what content your employees can and cannot access—from global allows/denials to individual users at specific times from specific locations. -
![Archive and Compressed [Edit]](https://docslib.b-cdn.net/cover/8796/archive-and-compressed-edit-1288796.webp)
Archive and Compressed [Edit]
Archive and compressed [edit] Main article: List of archive formats • .?Q? – files compressed by the SQ program • 7z – 7-Zip compressed file • AAC – Advanced Audio Coding • ace – ACE compressed file • ALZ – ALZip compressed file • APK – Applications installable on Android • AT3 – Sony's UMD Data compression • .bke – BackupEarth.com Data compression • ARC • ARJ – ARJ compressed file • BA – Scifer Archive (.ba), Scifer External Archive Type • big – Special file compression format used by Electronic Arts for compressing the data for many of EA's games • BIK (.bik) – Bink Video file. A video compression system developed by RAD Game Tools • BKF (.bkf) – Microsoft backup created by NTBACKUP.EXE • bzip2 – (.bz2) • bld - Skyscraper Simulator Building • c4 – JEDMICS image files, a DOD system • cab – Microsoft Cabinet • cals – JEDMICS image files, a DOD system • cpt/sea – Compact Pro (Macintosh) • DAA – Closed-format, Windows-only compressed disk image • deb – Debian Linux install package • DMG – an Apple compressed/encrypted format • DDZ – a file which can only be used by the "daydreamer engine" created by "fever-dreamer", a program similar to RAGS, it's mainly used to make somewhat short games. • DPE – Package of AVE documents made with Aquafadas digital publishing tools. • EEA – An encrypted CAB, ostensibly for protecting email attachments • .egg – Alzip Egg Edition compressed file • EGT (.egt) – EGT Universal Document also used to create compressed cabinet files replaces .ecab • ECAB (.ECAB, .ezip) – EGT Compressed Folder used in advanced systems to compress entire system folders, replaced by EGT Universal Document • ESS (.ess) – EGT SmartSense File, detects files compressed using the EGT compression system. • GHO (.gho, .ghs) – Norton Ghost • gzip (.gz) – Compressed file • IPG (.ipg) – Format in which Apple Inc. -

~Softwore Mate TM Operating Environment Release Notes
AA-HD99B-TK Operating Environment Release Notes ~softwore mate TM Operating Environment Release Notes Version 1.1 First Printing, January 1987 © Digital Equipment Corporation 1986. All Rights Reserved. The information in this document is subject to change without notice and should not be construed as a commitment by Digital Equipment Corporation. Digital Equipment Corporation assumes no responsibility for any errors that may appear in this document. The software described in this document is furnished under a license and may only be used or copied in accordance with the terms of such license. No responsibility is assumed for the use or reliability of software on equip ment that is not supplied by DIGITAL or its affiliated companies. MS-DOS is a trademark of Microsoft Corporation. The following are trademarks of Digital Equipment Corporation: ~DmDDmD'M MASSBUS VAX DEC PDP VAXmate DECmate PIOS VMS DECsystem-IO Professional VT DECSYSTEM-20 Rainbow VT220 DECUS RSTS VT240 DECwriter RSX Work Processor mBOL UNIBUS Printed in U.S.A. VAXmate Application Installation Guide Request Form The VAXmate Application Installation Guide describes the installation of selected industry-standard applications in the VAXmate server environment. Please send a complimentary copy of the VAX mate Application Installation Guide to: Name Company Address City State Zip If DIGITAL employee, indicate Badge # -------- Application types I use most are: _ Word Processing _ Data Base Management Spreadsheet Graphics _ Languages _ Integrated Software _ Programming Utilities Screen Editors Games Communications _ Project Management CAD/CAM Electronic Mail _ Desk-top Publishing _ Artificial Intelligence Other------- ~DmDDmD'OO T.~ --- - - ----------- - ---TII-IIr---- .'f::;;~::;7h' -i United States I I I I I I I I I I BUSINESS REPLY MAIL I FIRST CLASS PERMIT NO.