Fundamentals of Computer Networks
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Introducing Zigbee Theory and Practice Into Information and Computer Technology Disciplines
AC 2007-1072: INTRODUCING ZIGBEE THEORY AND PRACTICE INTO INFORMATION AND COMPUTER TECHNOLOGY DISCIPLINES Crystal Bateman, Brigham Young University Crystal Bateman is an Undergraduate Student at BYU studying Information Technology. Her academic interests include ubiquitous technologies and usability. She is currently finishing an honors thesis on using mobile ZigBee motes in a home environment, and enjoying life with her husband and two daughters Janell Armstrong, Brigham Young University Janell Armstrong is a Graduate Student in Information Technology at BYU. Her interests are in ZigBee and public key infrastructure. She has three years experience as a Teacher's Assistant. Student memberships include IEEE, IEEE-CS, ACM, SWE, ASEE. C. Richard Helps, Brigham Young University Richard Helps is the Program Chair of the Information Technology program at BYU and has been a faculty member in the School of Technology since 1986. His primary scholarly interests are in embedded and real-time computing and in technology education. He also has interests in human-computer interfacing. He has been involved in ABET accreditation for about 8 years and is a Commissioner of CAC-ABET and a CAC accreditation team chair. He spent ten years in industry designing industrial automation systems and in telecommunications. Professional memberships include IEEE, IEEE-CS, ACM, SIGITE, ASEE. Page 12.982.1 Page © American Society for Engineering Education, 2007 Introducing ZigBee Theory and Practice into Information and Computer Technology Disciplines Abstract As pervasive computing turns from the desktop model to the ubiquitous computing ideal, the development challenges become more complex than simply connecting a peripheral to a PC. A pervasive computing system has potentially hundreds of interconnected devices within a small area. -

13 Embedded Communication Protocols
13 Embedded Communication Protocols Distributed Embedded Systems Philip Koopman October 12, 2015 © Copyright 2000-2015, Philip Koopman Where Are We Now? Where we’ve been: •Design • Distributed system intro • Reviews & process • Testing Where we’re going today: • Intro to embedded networking – If you want to be distributed, you need to have a network! Where we’re going next: • CAN (a representative current network protocol) • Scheduling •… 2 Preview “Serial Bus” = “Embedded Network” = “Multiplexed Wire” ~= “Muxing” = “Bus” Getting Bits onto the wire • Physical interface • Bit encoding Classes of protocols • General operation • Tradeoffs (there is no one “best” protocol) • Wired vs. wireless “High Speed Bus” 3 Linear Network Topology BUS • Good fit to long skinny systems – elevators, assembly lines, etc... • Flexible - many protocol options • Break in the cable splits the bus • May be a poor choice for fiber optics due to problems with splitting/merging • Was prevalent for early desktop systems • Is used for most embedded control networks 4 Star Network Topologies Star • Can emulate bus functions – Easy to detect and isolate failures – Broken wire only affects one node – Good for fiber optics – Requires more wiring; common for Star current desktop systems • Broken hub is catastrophic • Gives a centralized location if needed – Can be good for isolating nodes that generate too much traffic Star topologies increasing in popularity • Bus topology has startup problems in some fault scenarios • Safety critical control networks moving -

Survey of Important Issues in UAV Communications Networks
1 Survey of Important Issues in UAV Communication Networks Lav Gupta*, Senior Member IEEE, Raj Jain, Fellow, IEEE, and Gabor Vaszkun technology that can be harnessed for military, public and civil Abstract—Unmanned Aerial Vehicles (UAVs) have enormous applications. Military use of UAVs is more than 25 years old potential in the public and civil domains. These are particularly primarily consisting of border surveillance, reconnaissance and useful in applications where human lives would otherwise be strike. Public use is by the public agencies such as police, endangered. Multi-UAV systems can collaboratively complete missions more efficiently and economically as compared to single public safety and transportation management. UAVs can UAV systems. However, there are many issues to be resolved provide timely disaster warnings and assist in speeding up before effective use of UAVs can be made to provide stable and rescue and recovery operations when the public communication reliable context-specific networks. Much of the work carried out in network gets crippled. They can carry medical supplies to areas the areas of Mobile Ad Hoc Networks (MANETs), and Vehicular rendered inaccessible. In situations like poisonous gas Ad Hoc Networks (VANETs) does not address the unique infiltration, wildfires and wild animal tracking UAVs could be characteristics of the UAV networks. UAV networks may vary from slow dynamic to dynamic; have intermittent links and fluid used to quickly envelope a large area without risking the safety topology. While it is believed that ad hoc mesh network would be of the personnel involved. most suitable for UAV networks yet the architecture of multi-UAV UAVs come networks has been an understudied area. -

Ciena Carrier-Grade Ethernet As a Foundation for Campus Access
CARRIER-GRADE ETHERNET AS A FOUNDATION FOR CAMPUS ACCESS NETWORKS Introduction to Ethernet increase overall network reliability, targeting Existing campus access networks are constrained by dissimilar five- or six-9s availability using classic telecommunications and often stressed data networks—typically using numerous equipment supplier specifications to produce network legacy technologies such as ATM and Frame Relay. These elements with ultra-high reliability. In addition to increased disparate networks are becoming increasingly difficult to reliability, the scalability of carrier-grade Ethernet is several manage, leading to higher operational and maintenance costs. orders of magnitude higher than traditional Local Area Additionally, these legacy networks do not cater to the kinds Network (LAN) designs. of emerging real-time applications that are crucial for an Carrier-grade Ethernet technology has become widely effective Information and Communications Technology (ICT) adopted in the carrier and enterprise environments because environment, including VoIP, video, and cloud-based data of its ability to offer differentiated service at a highly attractive processing. These applications are all IP/Ethernet based, cost. Standards-based carrier Ethernet is defined by the Metro requiring a next-generation, highly resilient, scalable, and Ethernet Forum (MEF) and the Optical Interworking Forum packetized campus access network. (OIF) as a connection-oriented Layer 2 service. Carrier-grade To this end, many government agencies have embarked upon Ethernet enables the ability to offer bandwidth-assured, Layer modernization efforts that intend to transform ageing and 2 Virtual Private Networks (VPNs) with up to eight layers of legacy communications infrastructure into a consolidated, Quality of Service (QoS), allowing differentiated service next-generation network. -

Comparison of Network Topologies for Optical Fiber Communication
International Journal of Engineering Research & Technology (IJERT) ISSN: 2278-0181 Vol. 1 Issue 10, December- 2012 Comparison Of Network Topologies For Optical Fiber Communication Mr. Bhupesh Bhatia Ms. Ashima Bhatnagar Bhatia Department of Electronics and Communication, Department of Computer Science, Guru Prem Sukh Memorial College of Engineering, Tecnia Institute of Advanced Studies, Delhi Delhi Ms. Rashmi Ishrawat Department of Computer Science, Tecnia Institute of Advanced Studies, Delhi Abstract advent of the Information age. Optical In this paper, the various network topologies technologies can cost effectively meet have been compared. The signal is analyzed as it corporate bandwidth needs today and passes through each node in each of the network tomorrow. Internet connections offering topology. There is no appreciable signal degradation in the ring network. Also there is bandwidth on demand, to fiber on the increase in Quality factor i.e. signal keeps on LAN. Fiber to the home can provide true improving as it passes through the successiveIJERT IJERTbroadband connectivity for nodes. For the bus topology, the quality of signal telecommuters as well as converged goes on decreasing with increase in the number multimedia offerings for consumers [2]. of nodes and the power penalty goes on increasing. For the star topology, it is observed These different communication networks that received power values of each node at a can be configured in a number of same distance from the hub are same and the topologies. These include a bus, with or performance is same. For the tree topology, it is without a backbone, a star network, a observed that the performance is almost identical ring network, which can be redundant to the performance of ring topology, as signal quality is improved as it passes through the and/ or self-healing, or some successive nodes of the hierarchy. -

UMTS Core Network
UMTS Core Network V. Mancuso, I. Tinnirello GSM/GPRS Network Architecture Radio access network GSM/GPRS core network BSS PSTN, ISDN PSTN, MSC GMSC BTS VLR MS BSC HLR PCU AuC SGSN EIR BTS IP Backbone GGSN database Internet V. Mancuso, I. Tinnirello 3GPP Rel.’99 Network Architecture Radio access network Core network (GSM/GPRS-based) UTRAN PSTN Iub RNC MSC GMSC Iu CS BS VLR UE HLR Uu Iur AuC Iub RNC SGSN Iu PS EIR BS Gn IP Backbone GGSN database Internet V. Mancuso, I. Tinnirello 3GPP RelRel.’99.’99 Network Architecture Radio access network 2G => 3G MS => UE UTRAN (User Equipment), often also called (user) terminal Iub RNC New air (radio) interface BS based on WCDMA access UE technology Uu Iur New RAN architecture Iub RNC (Iur interface is available for BS soft handover, BSC => RNC) V. Mancuso, I. Tinnirello 3GPP Rel.’99 Network Architecture Changes in the core Core network (GSM/GPRS-based) network: PSTN MSC is upgraded to 3G MSC GMSC Iu CS MSC VLR SGSN is upgraded to 3G HLR SGSN AuC SGSN GMSC and GGSN remain Iu PS EIR the same Gn GGSN AuC is upgraded (more IP Backbone security features in 3G) Internet V. Mancuso, I. Tinnirello 3GPP Rel.4 Network Architecture UTRAN Circuit Switched (CS) core network (UMTS Terrestrial Radio Access Network) MSC GMSC Server Server SGW SGW PSTN MGW MGW New option in Rel.4: GERAN (GSM and EDGE Radio Access Network) PS core as in Rel.’99 V. Mancuso, I. Tinnirello 3GPP Rel.4 Network Architecture MSC Server takes care Circuit Switched (CS) core of call control signalling network The user connections MSC GMSC are set up via MGW Server Server (Media GateWay) SGW SGW PSTN “Lower layer” protocol conversion in SGW MGW MGW (Signalling GateWay) RANAP / ISUP PS core as in Rel.’99 SS7 MTP IP Sigtran V. -

An Overview of DWDM Networks
Telecommunication / Telecommunication An Overview of DWDM Networks 1.0 Introduction by Shaowen Song n traditional optical fiber networks, information is transmit- ted through optical fiber by a single lightbeam. In a Wilfrid Laurier University, Waterloo, ON I wavelength division multiplexing (WDM) network, the vast optical bandwidth of a fiber (approximately 30 THz corre- Abstract sponding to the low-loss region in a single-mode optical fiber) is carved up into wavelength channels, each of which carries a data stream indi- This article provides an overview of the applications of Dense Wavelength Division Multiplexing (DWDM) technology. It exam- vidually. The multiple channels of information (each having a different ines the network architecture and the recent development of two carrier wavelength) are transmitted simultaneously over a single fiber. The reason why this can be done is that optical beams with different major DWDM-based networks, namely the backbone network and the residential access network. The DWDM applications in Local wavelengths propagate without interfering with one another. When the Area Networks (LANs) are not included in the article. The article number of wavelength channels is above 20 in a WDM system, it is generally referred to as Dense WDM or DWDM. We use DWDM as a also looks into the future of broadband integrated service networks based on the DWDM technology. general term in this article. DWDM technology can be applied to different areas in the telecommu- nication networks, which includes the backbone networks, the residential access networks, and also the Local Area Networks (LANs). Sommaire Among these three areas, developments in the DWDM-based backbone network are leading the way, followed by the DWDM-based LANs. -

Analysis of Wifi and Wimax and Wireless Network Coexistence
International Journal of Computer Networks & Communications (IJCNC) Vol.6, No.6, November 2014 ANALYSIS OF WIFI AND WIMAX AND WIRELESS NETWORK COEXISTENCE Shuang Song and Biju Issac School of Computing, Teesside University, Middlesbrough, UK ABSTRACT Wireless networks are very popular nowadays. Wireless Local Area Network (WLAN) that uses the IEEE 802.11 standard and WiMAX (Worldwide Interoperability for Microwave Access) that uses the IEEE 802.16 standard are networks that we want to explore. WiMAX has been developed over 10 years, but it is still unknown to most people. However compared to WLAN, it has many advantages in transmission speed and coverage area. This paper will introduce these two technologies and make comparisons between WiMAX and WiFi. In addition, wireless network coexistence of WLAN and WiMAX will be explored through simulation. Lastly we want to discuss the future of WiMAX in relation to WiFi. KEY WORDS WiMAX, WiFi, wireless network, wireless coexistence, network simulation 1. INTRODUCTION With the development of multimedia communication, people need wireless broadband access with higher speed, larger coverage and mobility. The emergence of WiMAX (Worldwide Interoperability for Microwave Access) technology met the people's demand for wireless Internet to some extent. If wireless LAN technology (WLAN) solves the access problem of the "last one hundred meters", then WiMAX technology is the best access solution of the "last mile". Though WiMAX is an emerging and extremely competitive wireless broadband access technology, the development prospects of its market is still unknown. Hybrid networks as a supplement to cell based or IP packet based services, can fully reflect the characteristics of wide network coverage. -

Designing a Robust and Cost-Effective Campus Network
CAMPUS LAN Designing a Robust and Cost-Effective Campus Network Brocade is taking groundbreaking performance and reliability from the data center and extending it across the entire network all the way to the edge. Now, superior performance can be maximized across the entire campus network, giving you a more managed and efficient approach to growth. CAMPUS LAN DESIGN BRIEF CONTENTS Introduction........................................................................................................................................................................................................................................ 3 The Campus LAN............................................................................................................................................................3 Performance and Availability.........................................................................................................................................4 Security...........................................................................................................................................................................4 Management..................................................................................................................................................................4 Reducing Operational Expense.....................................................................................................................................4 Building a Tiered Campus Network ......................................................................................................................................................................................... -
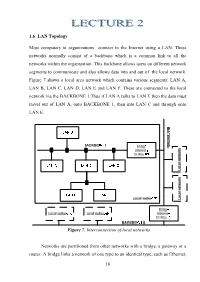
16 1.6 . LAN Topology Most Computers in Organizations Connect to the Internet Using a LAN. These Networks Normally Consist of A
1.6 . LAN Topology Most computers in organizations connect to the Internet using a LAN. These networks normally consist of a backbone which is a common link to all the networks within the organization. This backbone allows users on different network segments to communicate and also allows data into and out of the local network. Figure 7 shows a local area network which contains various segments: LAN A, LAN B, LAN C, LAN D, LAN E and LAN F. These are connected to the local network via the BACKBONE 1.Thus if LAN A talks to LAN E then the data must travel out of LAN A, onto BACKBONE 1, then into LAN C and through onto LAN E. Figure 7. Interconnection of local networks Networks are partitioned from other networks with a bridge, a gateway or a router. A bridge links a network of one type to an identical type, such as Ethernet, 16 or Token Ring to Token Ring. A gateway connects two dissimilar types of networks and routers operate in a similar way to gateways and can either connect to two similar or dissimilar networks. The key operation of a gateway, bridge or router is that they only allow data traffic through that is intended for another network, which is outside the connected network. This filters traffic and stops traffic, not intended for the network, from clogging-up the backbone. Most modern bridges, gateways and routers are intelligent and can automatically determine the topology of the network. Spanning-tree bridges have built-in intelligence and can communicate with other bridges. -

Satellite Communication & Networking
SATELLITE COMMUNICATION & NETWORKING Submitted By- Sanket Gupta NTPC Electronics & Communication National Thermal Power Corporation Raj Kumar Goel Engg. College INDEX 11.. IInnttrroodduuccttiioonn aa.. HHooww DDoo SSaatteelllliitteess WWoorrkk?? bb.. FFaaccttoorrss IInn SSaatteelllliittee Communication 22.. MMaajjoorr PPrroobblleemmss FFoorr SSaatteelllliitteess aa.. AAddvvaannttaaggeess OOff SSaatteelllliitteess Communication b.b. Disadvantages Of Satellites Communication 33.. TTyyppeess OOff SSaatteelllliitteess aa.. GGeeoossttaattiioonnaarryy EEaarrtthh OOrrbbiitt (GEO) bb.. LLooww EEaarrtthh OOrrbbiitt ((LLEEOO)) cc.. MMeeddiiuumm EEaarrtthh OOrrbbiitt ((MMEEOO)) 44.. FFrreeqquueennccyy BBaannddss OOff SSaatteelllliitteess aa.. SSaatteelllliittee SSeerrvviicceess bb.. FFrreeqquueennccyy BBaannddss 55.. TTeerrmmss UUsseedd IInn SSaatteelllliittee Communication 66.. CCoommppoonneennttss OOff SSaatteelllliittee Communication 7.7. Satellite Communication System 88.. SSaatteelllliittee EEaarrtthh SSttaattiioonn Introduction How Do Satellites Work? If two Stations on Earth want to communicate through rraaddiioo bbrrooaaddccaasstt bbuutt aarree ttoooo ffaarr aawwaayy ttoo uussee coconvnvenentitiononalal memeanans,s, ththenen ththesesee ststatatioionsns cacann ususee aa satellite as a relay station for their communicacommunication.tion. One Earth Station sends a transmission to the satellite. This is called an Uplink . ThThee sasateltellitlitee Transponder earthconverts station. the signalThis is calledand sends a Downlink it down.. to the -

Guidelines for IPX Provider Networks (Previously Inter- Service Provider IP Backbone Guidelines) Version 14.0 01 August 2018
GSM Association Non-confidential Official Document IR.34 - Guidelines for IPX Provider networks (Previously Inter-Service Provider IP Backbone Guidelines) Guidelines for IPX Provider networks (Previously Inter- Service Provider IP Backbone Guidelines) Version 14.0 01 August 2018 This is a Non-binding Permanent Reference Document of the GSMA Security Classification: Non-confidential Access to and distribution of this document is restricted to the persons permitted by the security classification. This document is confidential to the Association and is subject to copyright protection. This document is to be used only for the purposes for which it has been supplied and information contained in it must not be disclosed or in any other way made available, in whole or in part, to persons other than those permitted under the security classification without the prior written approval of the Association. Copyright Notice Copyright © 2018 GSM Association Disclaimer The GSM Association (“Association”) makes no representation, warranty or undertaking (express or implied) with respect to and does not accept any responsibility for, and hereby disclaims liability for the accuracy or completeness or timeliness of the information contained in this document. The information contained in this document may be subject to change without prior notice. Antitrust Notice The information contain herein is in full compliance with the GSM Association’s antitrust compliance policy. V14.0 Page 1 of 53 GSM Association Non-confidential Official Document IR.34 - Guidelines