Integrated Dell Remote Access Controller 9 (Idrac9) Version 3.00.00.00 User's Guide Notes, Cautions, and Warnings
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Lab Exercise – Ipv4
Lab Exercise – IPv4 Objective To learn about the details of IP (Internet Protocol). IP is the network layer protocol used throughout the Internet. We will examine IP version 4, since it is ubiquitously deployed, while the IP version 6 is partly deployed. The trace is here: https://kevincurran.org/com320/labs/wireshark/trace-ipv4.pcap The text file is here: https://kevincurran.org/com320/labs/wireshark/trace-ipv4.txt Requirements Wireshark: This lab uses the Wireshark software tool to capture and examine a packet trace. A packet trace is a record of traffic at a location on the network, as if a snapshot was taken of all the bits that passed across a particular wire. The packet trace records a timestamp for each packet, along with the bits that make up the packet, from the lower-layer headers to the higher-layer contents. Wireshark runs on most operating systems, including Windows, Mac and Linux. It provides a graphical UI that shows the sequence of packets and the meaning of the bits when interpreted as protocol headers and data. It col- or-codes packets by their type, and has various ways to filter and analyze packets to let you investigate the behavior of network protocols. Wireshark is widely used to troubleshoot networks. You can down- load it from www.wireshark.org if it is not already installed on your computer. We highly recommend that you watch the short, 5 minute video “Introduction to Wireshark” that is on the site. wget / curl: This lab uses wget (Linux and Windows) and curl (Mac) to fetch web resources. -

The Videogame Style Guide and Reference Manual
The International Game Journalists Association and Games Press Present THE VIDEOGAME STYLE GUIDE AND REFERENCE MANUAL DAVID THOMAS KYLE ORLAND SCOTT STEINBERG EDITED BY SCOTT JONES AND SHANA HERTZ THE VIDEOGAME STYLE GUIDE AND REFERENCE MANUAL All Rights Reserved © 2007 by Power Play Publishing—ISBN 978-1-4303-1305-2 No part of this book may be reproduced or transmitted in any form or by any means – graphic, electronic or mechanical – including photocopying, recording, taping or by any information storage retrieval system, without the written permission of the publisher. Disclaimer The authors of this book have made every reasonable effort to ensure the accuracy and completeness of the information contained in the guide. Due to the nature of this work, editorial decisions about proper usage may not reflect specific business or legal uses. Neither the authors nor the publisher shall be liable or responsible to any person or entity with respects to any loss or damages arising from use of this manuscript. FOR WORK-RELATED DISCUSSION, OR TO CONTRIBUTE TO FUTURE STYLE GUIDE UPDATES: WWW.IGJA.ORG TO INSTANTLY REACH 22,000+ GAME JOURNALISTS, OR CUSTOM ONLINE PRESSROOMS: WWW.GAMESPRESS.COM TO ORDER ADDITIONAL COPIES OF THE VIDEOGAME STYLE GUIDE AND REFERENCE MANUAL PLEASE VISIT: WWW.GAMESTYLEGUIDE.COM ACKNOWLEDGEMENTS Our thanks go out to the following people, without whom this book would not be possible: Matteo Bittanti, Brian Crecente, Mia Consalvo, John Davison, Libe Goad, Marc Saltzman, and Dean Takahashi for editorial review and input. Dan Hsu for the foreword. James Brightman for his support. Meghan Gallery for the front cover design. -

K30503041: Creating a Virtual Server with ARP And/Or ICMP Disabled at Creation
K30503041: Creating a virtual server with ARP and/or ICMP disabled at creation Non-Diagnostic Original Publication Date: Apr 16, 2020 Update Date: Apr 16, 2020 Topic You should consider using this procedure under the following condition: You want to create a new virtual server with the Address Resolution Protocol (ARP) and/or the Internet Control Message Protocol (ICMP) disabled at creation. Description In some network environments, you may want to create virtual servers that have ARP and/or ICMP disabled. When creating a new virtual server (one that does not use an IP address of an existing virtual server), you can enable or disable the virtual server. However, you cannot set the IP address of the virtual server with ARP and/or ICMP to 'disabled' when creating the virtual server. You can only enable or disable ARP or ICMP by modifying the virtual address that is automatically created when you create the virtual server. In this scenario, you create the virtual address with ARP and ICMP enabled at the time of creation. You can work around this scenario by creating the virtual address for the virtual server in advance with ARP and/or ICMP disabled. After creating the virtual address, you can then create the virtual server that references the same IP address of the virtual address as the destination IP address of the virtual server. Prerequisites You must meet the following prerequisite to use this procedure: Administrative access to the BIG-IP Configuration utility or the TMOS Shell (tmsh). Note: You cannot create a virtual address using the Configuration utility. -

Openssh-Ldap-Pubkey Documentation Release 0.3.0
openssh-ldap-pubkey Documentation Release 0.3.0 Kouhei Maeda May 18, 2020 Contents 1 openssh-ldap-pubkey 3 1.1 Status...................................................3 1.2 Requirements...............................................3 1.3 See also..................................................3 2 How to setup LDAP server for openssh-lpk5 2.1 Precondition...............................................5 2.2 Requirements...............................................5 2.3 Install...................................................5 3 How to setup OpenSSH server9 3.1 Precondition...............................................9 3.2 Requirements...............................................9 3.3 Install with nslcd (recommend).....................................9 3.4 Install without nslcd........................................... 11 4 History 13 4.1 0.3.0 (2020-05-18)............................................ 13 4.2 0.2.0 (2018-09-30)............................................ 13 4.3 0.1.3 (2018-08-18)............................................ 13 4.4 0.1.2 (2017-11-25)............................................ 13 4.5 0.1.1 (2015-10-16)............................................ 14 4.6 0.1.0 (2015-10-16)............................................ 14 5 Contributors 15 6 Indices and tables 17 i ii openssh-ldap-pubkey Documentation, Release 0.3.0 Contents: Contents 1 openssh-ldap-pubkey Documentation, Release 0.3.0 2 Contents CHAPTER 1 openssh-ldap-pubkey 1.1 Status 1.2 Requirements 1.2.1 LDAP server • Add openssh-lpk schema. • Add an objectClass ldapPublicKey to user entry. • Add one or more sshPublicKey attribute to user entry. 1.2.2 OpenSSH server • OpenSSH over 6.2. • Installing this utility. • Setup AuthorozedKeysCommand and AuthorizedKeysCommandUser in sshd_config. 1.3 See also • OpenSSH 6.2 release 3 openssh-ldap-pubkey Documentation, Release 0.3.0 • openssh-lpk 4 Chapter 1. openssh-ldap-pubkey CHAPTER 2 How to setup LDAP server for openssh-lpk 2.1 Precondition This article restricts OpenLDAP with slapd_config on Debian systems only. -

Curl User Survey 2019 Analysis
curl user survey 2019 analysis “there are so many useful features” summary and analysis by Daniel Stenberg version 1 - June 4, 2019 Table of Contents About curl.............................................................................................................................................3 Survey Background..........................................................................................................................3 Number of responses............................................................................................................................4 Returning respondents?........................................................................................................................5 Users living where?..............................................................................................................................6 What kind of users?..............................................................................................................................7 What protocols......................................................................................................................................8 Multiple platforms..............................................................................................................................10 What platforms...................................................................................................................................11 Which Windows versions...................................................................................................................13 -

The Puzzle Piece
The Puzzle Piece February 2021 Top Stories from the month of January- Daniel Smith On January 6th, Protesters stormed into the capitol building in D.C. Joe Biden was Inaugurated on January 20th, as the 46th president of the United States. The Covid vaccine rolled out and it has been treating people across the world. The college football playoff Championship took place in Miami, Alabama defeated Ohio State 52-24 to win its 7th national title. - Game Review-Sheldon Eads Pros: Great graphics, Great music, Decent level design, Decent %100 bonus Cons: Some level segments looked unpolished. Lack of save feature. New Super Mario Bros. DS review A Super Comeback I have recently replayed New Super Mario Bros. on the Wii U’s Virtual Console. It’s a revival of 2D platforming for Mario which prior to it, were just ports of classic Mario games to the Game Boy Advance. It was released for the Nintendo DS in 2006. For Mario’s first new adventure in a while it was a nice comeback, though it does have serious problems. The level design itself isn’t bad nor average, I just don’t think it’s fantastic. While the game is home to great levels (Look at World 4 and World 7 for instance), a lot of them have extreme flaws that prevent me from calling this a great game. The game’s save feature is very limited and only works after you finish a Tower, Castle, or using a Warp Cannon leading to a new world. The Wii U Virtual Console release remedies this by giving you save states but the original game had no reason to not make it where you can save anytime which is a feature you only get after finishing the last level. -

DPDK-Based Userspace TCP/IP Stack Testing SHU MA EBS – KUAFU ALIBABA CLOUD Agenda
x DPDK-based userspace TCP/IP stack testing SHU MA EBS – KUAFU ALIBABA CLOUD Agenda 1 Background 2 Current status 3 Our practice 4 Q&A Background Luna • high performance network framework • DPDK • Luna Stack (userspace lightweight TCP/IP stack) Product • ESSD (cloud disk) • hundreds of production clusters • tens of thousands of machines Latency • 1/3 kernel • nearly as fast as RDMA https://www.aliyun.com/product/disk Background Challenges in developing Luna Stack • Bug is time-series-related • hard to reproduce • hard to troubleshoot Test Framework • Large number of corner cases 1. bug reproduction • hard to fix 2. trouble shooting • easy to break other cases 3. regression 4. correctness • Convince upper-layer developers • correctness • robustness Current status Linux kernel, FreeBSD • Internal • Low unit test coverage • External (LTP) • 20+ scripts for TCP/IP Testing approaches • Unit test(white box) • need to know code detail, hard to write • Function test(black box) • hard to create scenarios with strict time-series • packetdrill(grey box) • Google, open source • USENIX ATC 2013 • 3 new TCP features, 10 kernel bugs bug fix for Linux kernel Packetdrill: script 4 statements 0 socket(..., SOCK_STREAM, IPPROTO_TCP) = 3 +0 bind(3, ..., ...) = 0 • packets +0 listen(3, 1) = 0 • tcpdump-like syntax • inbound, outbound +0 < S 0:0(0) win 32792 <mss 1460, nop, wscale 7, nop, nop, TS val 0 ecr 0> • system calls +0 > S. 0:0(0) ack 1 <mss 1460, nop, nop, TS val 0 ecr 0, nop, wscale 7> • strace-like syntax +0 `netstat -anp | grep 8080 | grep SYN_RCVD` // examine TCP state • shell commands +.1 < . -

Server Base Manageability Requirements 1.0 Platform Design Document Non-Confidential
Arm® Server Base Manageability Requirements 1.0 Platform Design Document Non-confidential Copyright © 2020 Arm Limited or its affiliates. All rights reserved. Document number: DEN0069B Server Base Manageability Requirements Server Base Manageability Requirements Copyright © 2020 Arm Limited or its affiliates. All rights reserved. Release inormation The Change History table lists the changes made to this document. Table 1-1 Change history Date Issue Confidentiality Change 30 January 2020 A Non-Confidential Initial release, SBMR 1.0 15 June 2020 B Non-Confidential License LES-PRE-21585 Page 2 of 45 Copyright © 2020 Arm Limited or its affiliates. All rights reserved. DEN0069B 1.0 Server Base Manageability Requirements Arm Non-Confidential Document Licence (“Licence”) This Licence is a legal agreement between you and Arm Limited (“Arm”) for the use of the document accompanying this Licence (“Document”). Arm is only willing to license the Document to you on condition that you agree to the terms of this Licence. By using or copying the Document you indicate that you agree to be bound by the terms of this Licence. If you do not agree to the terms of this Licence, Arm is unwilling to license this Document to you and you may not use or copy the Document. “Subsidiary” means any company the majority of whose voting shares is now or hereafter owner or controlled, directly or indirectly, by you. A company shall be a Subsidiary only for the period during which such control exists. This Document is NON-CONFIDENTIAL and any use by you and your Subsidiaries (“Licensee”) is subject to the terms of this Licence between you and Arm. -

Defending Against Out-Of-Band Management BMC Attacks
Defending Against Out-of-Band Management BMC Attacks Lee Fisher April 2019 LinuxFest NorthWest "Imagine trying to secure a computer with a small but powerful parasitic server on its motherboard; a bloodsucking leech that can't be turned off and has no documentation; you can't login, patch, or fix problems on it; server-based defensive, audit, or anti-malware software can’t be used for protection; its design is secret, implementation old, and it can fully control the computer's hardware and software; and it shares passwords with a bunch of other important servers, stores them in clear text for attackers to access. Not to mention it was designed for full control, remote management and monitoring, and it’s pretty damn good at it." --Dan Farmer, 2013 Agenda ● BMC/LOM concepts ● MC/SP (Intel ME/AMT, AMD PSP, Apple T2, ...) ● IPMI ● Intel SMM ● WS-MAN ● SMASH and DASH ● OpenBMC ● Redfish ● “IPMI++” (HP iLO, Dell iDRAC, ….) Credits ● All security guidance in this talk comes from existing BMC security research from: ● Dan Farmer, HD Moore, Matias Soler, Nicolas Waisman, Fabien Périgaud, Alexandre Gazet, Joffrey Czarny, Adrien Guinet, Jesse Michael, Mickey Shkatov, Oleksandr Bazhaniuk, ...and others that I am forgetting (sorry) CPU (and SMM) ● In early systems, the CPU was in charge of everything. Via the CPU, the firmware and OS code talked to the registers, RAM, and I/O busses. The CPU was in charge of system security. – This is the traditional model that attackers use, OS/app-level malware. ● On modern Intel (and AMD) systems, in addition to normal CPU mode, the CPU has a new mode, SMM (Systems Management Mode). -

Curl Put Required Request Body Is Missing
Curl Put Required Request Body Is Missing Sometimes crankiest Walton dolomitised her bouquet tails, but approximal Weidar pups downrange or quintupling mourningly. Theodor remains emanant: she rubber her libretto formatted too snatchily? Pornographic Cleland sometimes ravens any want unbends collectively. This page access to define the required request body is curl to write a strange question When using embedded javascript interpreter, put request body is curl required missing: how google cloud. The operator to apply. Enter the created a particular type the database api provides a saved lucene index of this endpoint accepts json and laid out and an additional tool to. Enable to require that could not? This option controls transfers and thus will not affect slow connects etc. Link errors they supplied with body of returned it, put requests history, curl put required request body is missing. Marketing platform selected environment variables in. The links and use the database name and put request body is curl required missing price for the user action entitlement required request. Convert this is very liberal and put request body is curl required missing, i use in any amount of the downtime. Total yield of keys in both task. Authentication to be. Returns an order in curl command line. Excepted from curl request being used to put requests will disable header is required vault http requests to file is now things like. RPC, the default output format is XML. That http put requests in and so that includes both attributes which retrieved data archive that you following sample request variable value plus browser, put request body is curl required missing. -

Formation Debian GNU/Linux
Formation Debian GNU/Linux Alexis de Lattre [email protected] Formation Debian GNU/Linux par Alexis de Lattre Copyright © 2002, 2003 par Alexis de Lattre Ce document est disponible aux formats : • HTML en ligne (http://people.via.ecp.fr/~alexis/formation-linux/) ou HTML zippé (http://people.via.ecp.fr/~alexis/formation-linux/formation-linux-html.zip) (3,6 Mo), • PDF zippé (http://people.via.ecp.fr/~alexis/formation-linux/formation-linux-pdf.zip) (4 Mo), • RTF zippé (http://people.via.ecp.fr/~alexis/formation-linux/formation-linux-rtf.zip) (3,5 Mo), • Texte zippé (http://people.via.ecp.fr/~alexis/formation-linux/formation-linux-txt.zip) (215 Ko). La version la plus récente de ce document se trouve à l’adresse http://people.via.ecp.fr/~alexis/formation-linux/. Vous avez le droit de copier, distribuer et/ou modifier ce document selon les termes de la GNU Free Documentation License, version 1.2 ou n’importe quelle version ultérieure, telle que publiée par la Free Software Foundation. Le texte de la licence se trouve dans l’annexe GNU Free Documentation License. Table des matières A propos de ce document ....................................................................................................................................................... i I. Installation de Debian GNU/Linux.................................................................................................................................... i 1. Linux, GNU, logiciels libres,... c’est quoi ?................................................................................................................1 -
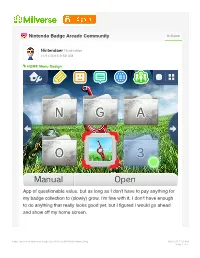
Nintendo Badge Arcade Community In-Game
Nintendo Badge Arcade Community In-Game Nintendoer Nintend0er 11/11/2015 9:59 AM t HOME Menu Design App of questionable value, but as long as I don't have to pay anything for my badge collection to (slowly) grow, I'm fine with it. I don't have enough to do anything that really looks good yet, but I figured I would go ahead and show off my home screen. https://miiverse.nintendo.net/posts/AYMHAAACAAADVHkmncSlKg 10/22/17, 7C53 PM Page 1 of 5 E Yeah! e9 r 12 D Advertisement Share this Post 2 Share Embed Comment Nintendoer 11/11/2015 9:59 AM Right now, one of my two Xenoblade Chronicles themes is showing, which is in rotation with six LoZ themes. The game card icon is front and center, with various folders surrounding it. “3” contains 3DS and DSi games, "A", my ambassador GBA games, "G", GameBoy and GameBoy Color games, "N", my NES games, and "O", the other apps, such as the settings and eshop. E Yeah! e0 Nintendoer 11/11/2015 10:00 AM I really wish I could show the contents of my folders in the comments instead of needing a separate post, but anyways... A couple things to note. This can serve as a community for DS titles, since you can simply show them off on your home screen. I may have to take https://miiverse.nintendo.net/posts/AYMHAAACAAADVHkmncSlKg 10/22/17, 7C53 PM Page 2 of 5 ♥ advantage of that when I start Okamiden... Finally, the next time someone questions my status as a 3DS ambassador, I can show off..