Master's Thesis
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Fill Your Boots: Enhanced Embedded Bootloader Exploits Via Fault Injection and Binary Analysis
IACR Transactions on Cryptographic Hardware and Embedded Systems ISSN 2569-2925, Vol. 2021, No. 1, pp. 56–81. DOI:10.46586/tches.v2021.i1.56-81 Fill your Boots: Enhanced Embedded Bootloader Exploits via Fault Injection and Binary Analysis Jan Van den Herrewegen1, David Oswald1, Flavio D. Garcia1 and Qais Temeiza2 1 School of Computer Science, University of Birmingham, UK, {jxv572,d.f.oswald,f.garcia}@cs.bham.ac.uk 2 Independent Researcher, [email protected] Abstract. The bootloader of an embedded microcontroller is responsible for guarding the device’s internal (flash) memory, enforcing read/write protection mechanisms. Fault injection techniques such as voltage or clock glitching have been proven successful in bypassing such protection for specific microcontrollers, but this often requires expensive equipment and/or exhaustive search of the fault parameters. When multiple glitches are required (e.g., when countermeasures are in place) this search becomes of exponential complexity and thus infeasible. Another challenge which makes embedded bootloaders notoriously hard to analyse is their lack of debugging capabilities. This paper proposes a grey-box approach that leverages binary analysis and advanced software exploitation techniques combined with voltage glitching to develop a powerful attack methodology against embedded bootloaders. We showcase our techniques with three real-world microcontrollers as case studies: 1) we combine static and on-chip dynamic analysis to enable a Return-Oriented Programming exploit on the bootloader of the NXP LPC microcontrollers; 2) we leverage on-chip dynamic analysis on the bootloader of the popular STM8 microcontrollers to constrain the glitch parameter search, achieving the first fully-documented multi-glitch attack on a real-world target; 3) we apply symbolic execution to precisely aim voltage glitches at target instructions based on the execution path in the bootloader of the Renesas 78K0 automotive microcontroller. -

STM32-P103 User's Manual
STM-P103 development board User's manual Document revision C, August 2016 Copyright(c) 2014, OLIMEX Ltd, All rights reserved INTRODUCTION STM32-P103 board is development board which allows you to explore thee features of the ARM Cortex M3 STM32F103RBT6 microcontroller produced by ST Microelectronics Inc. The board has SD/MMC card connector and allows USB Mass storage device demo to be evaluated. The RS232 driver and connector allows USB to Virtual COM port demo to be evaluated. The CAN port and driver allows CAN applications to be developed. The UEXT connector allows access to all other UEXT modules produced by OLIMEX (like MOD-MP3, MOD-NRF24LR, MOD-NOKIA6610, etc) to be connected easily. In the prototype area the customer can solder his own custom circuits and interface them to USB, CAN, RS232 etc. STM32-P103 is almost identical in hardware design to STM32-P405. The major difference is the microcontroller used (STM32F103 vs STM32F405). Another board with STM32F103 and a display is STM32-103STK. A smaller (and cheaper board) with STM32F103 is the STM32-H103. Both boards mentioned also have a version with the newer microcontroller STM32F405 used. The names are respectively STM32-405STK and STM32-H405. BOARD FEATURES STM32-P103 board features: - CPU: STM32F103RBT6 ARM 32 bit CORTEX M3™ - JTAG connector with ARM 2×10 pin layout for programming/debugging with ARM-JTAG, ARM-USB- OCD, ARM-USB-TINY - USB connector - CAN driver and connector - RS232 driver and connector - UEXT connector which allow different modules to be connected (as MOD-MP3, -

Reconfigurable Embedded Control Systems: Problems and Solutions
RECONFIGURABLE EMBEDDED CONTROL SYSTEMS: PROBLEMS AND SOLUTIONS By Dr.rer.nat.Habil. Mohamed Khalgui ⃝c Copyright by Dr.rer.nat.Habil. Mohamed Khalgui, 2012 v Martin Luther University, Germany Research Manuscript for Habilitation Diploma in Computer Science 1. Reviewer: Prof.Dr. Hans-Michael Hanisch, Martin Luther University, Germany, 2. Reviewer: Prof.Dr. Georg Frey, Saarland University, Germany, 3. Reviewer: Prof.Dr. Wolf Zimmermann, Martin Luther University, Germany, Day of the defense: Monday January 23rd 2012, Table of Contents Table of Contents vi English Abstract x German Abstract xi English Keywords xii German Keywords xiii Acknowledgements xiv Dedicate xv 1 General Introduction 1 2 Embedded Architectures: Overview on Hardware and Operating Systems 3 2.1 Embedded Hardware Components . 3 2.1.1 Microcontrollers . 3 2.1.2 Digital Signal Processors (DSP): . 4 2.1.3 System on Chip (SoC): . 5 2.1.4 Programmable Logic Controllers (PLC): . 6 2.2 Real-Time Embedded Operating Systems (RTOS) . 8 2.2.1 QNX . 9 2.2.2 RTLinux . 9 2.2.3 VxWorks . 9 2.2.4 Windows CE . 10 2.3 Known Embedded Software Solutions . 11 2.3.1 Simple Control Loop . 12 2.3.2 Interrupt Controlled System . 12 2.3.3 Cooperative Multitasking . 12 2.3.4 Preemptive Multitasking or Multi-Threading . 12 2.3.5 Microkernels . 13 2.3.6 Monolithic Kernels . 13 2.3.7 Additional Software Components: . 13 2.4 Conclusion . 14 3 Embedded Systems: Overview on Software Components 15 3.1 Basic Concepts of Components . 15 3.2 Architecture Description Languages . 17 3.2.1 Acme Language . -

Insider's Guide STM32
The Insider’s Guide To The STM32 ARM®Based Microcontroller An Engineer’s Introduction To The STM32 Series www.hitex.com Published by Hitex (UK) Ltd. ISBN: 0-9549988 8 First Published February 2008 Hitex (UK) Ltd. Sir William Lyons Road University Of Warwick Science Park Coventry, CV4 7EZ United Kingdom Credits Author: Trevor Martin Illustrator: Sarah Latchford Editors: Michael Beach, Alison Wenlock Cover: Wolfgang Fuller Acknowledgements The author would like to thank M a t t Saunders and David Lamb of ST Microelectronics for their assistance in preparing this book. © Hitex (UK) Ltd., 21/04/2008 All rights reserved. No part of this publication may be reproduced, stored in a retrieval system or transmitted in any form or by any means, electronic, mechanical or photocopying, recording or otherwise without the prior written permission of the Publisher. Contents Contents 1. Introduction 4 1.1 So What Is Cortex?..................................................................................... 4 1.2 A Look At The STM32 ................................................................................ 5 1.2.1 Sophistication ............................................................................................. 5 1.2.2 Safety ......................................................................................................... 6 1.2.3 Security ....................................................................................................... 6 1.2.4 Software Development .............................................................................. -

Μc/OS-II™ Real-Time Operating System
μC/OS-II™ Real-Time Operating System DESCRIPTION APPLICATIONS μC/OS-II is a portable, ROMable, scalable, preemptive, real-time ■ Avionics deterministic multitasking kernel for microprocessors, ■ Medical equipment/devices microcontrollers and DSPs. Offering unprecedented ease-of-use, ■ Data communications equipment μC/OS-II is delivered with complete 100% ANSI C source code and in-depth documentation. μC/OS-II runs on the largest number of ■ White goods (appliances) processor architectures, with ports available for download from the ■ Mobile Phones, PDAs, MIDs Micrium Web site. ■ Industrial controls μC/OS-II manages up to 250 application tasks. μC/OS-II includes: ■ Consumer electronics semaphores; event flags; mutual-exclusion semaphores that eliminate ■ Automotive unbounded priority inversions; message mailboxes and queues; task, time and timer management; and fixed sized memory block ■ A wide-range of embedded applications management. FEATURES μC/OS-II’s footprint can be scaled (between 5 Kbytes to 24 Kbytes) to only contain the features required for a specific application. The ■ Unprecedented ease-of-use combined with an extremely short execution time for most services provided by μC/OS-II is both learning curve enables rapid time-to-market advantage. constant and deterministic; execution times do not depend on the number of tasks running in the application. ■ Runs on the largest number of processor architectures with ports easily downloaded. A validation suite provides all documentation necessary to support the use of μC/OS-II in safety-critical systems. Specifically, μC/OS-II is ■ Scalability – Between 5 Kbytes to 24 Kbytes currently implemented in a wide array of high level of safety-critical ■ Max interrupt disable time: 200 clock cycles (typical devices, including: configuration, ARM9, no wait states). -

Retrofitting Leakage Resilient Authenticated Encryption To
Retrofitting Leakage Resilient Authenticated Encryption to Microcontrollers Florian Unterstein1∗, Marc Schink1∗, Thomas Schamberger2∗, Lars Tebelmann2∗, Manuel Ilg1 and Johann Heyszl1 1 Fraunhofer Institute for Applied and Integrated Security (AISEC), Germany [email protected], [email protected] 2 Technical University of Munich, Germany, Department of Electrical and Computer Engineering, Chair of Security in Information Technology {t.schamberger,lars.tebelmann}@tum.de Abstract. The security of Internet of Things (IoT) devices relies on fundamental concepts such as cryptographically protected firmware updates. In this context attackers usually have physical access to a device and therefore side-channel attacks have to be considered. This makes the protection of required cryptographic keys and implementations challenging, especially for commercial off-the-shelf (COTS) microcontrollers that typically have no hardware countermeasures. In this work, we demonstrate how unprotected hardware AES engines of COTS microcontrollers can be efficiently protected against side-channel attacks by constructing a leakage resilient pseudo random function (LR-PRF). Using this side-channel protected building block, we implement a leakage resilient authenticated encryption with associated data (AEAD) scheme that enables secured firmware updates. We use concepts from leakage resilience to retrofit side-channel protection on unprotected hardware AES engines by means of software-only modifications. The LR-PRF construction leverages frequent key changes and low data complexity together with key dependent noise from parallel hardware to protect against side-channel attacks. Contrary to most other protection mechanisms such as time-based hiding, no additional true randomness is required. Our concept relies on parallel S-boxes in the AES hardware implementation, a feature that is fortunately present in many microcontrollers as a measure to increase performance. -
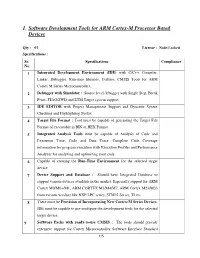
1. Software Development Tools for ARM Cortex-M Processor Based Devices
1. Software Development Tools for ARM Cortex-M Processor Based Devices Qty : 01 License : Node-Locked Specifications : Sr. Specifications Compliance No. 1 Integrated Development Environment (IDE) with C/C++ Compiler, Linker, Debugger, Run-time libraries, Utilities, CMSIS Tools for ARM Cortex M Series Microcontrollers. 2 Debugger with Simulator : Source level debugger with Single Step, Break Point, JTAG/SWD and ETM Target system support 3 IDE EDITOR with Project Management Support and Dynamic Syntax Checking and Highlighting Syntax. 4 Target File Format : Tool must be capable of generating the Target File Format of executable in BIN or HEX Format. 5 Integrated Analysis Tools must be capable of Analysis of Code and Execution Time, Code and Data Trace. Complete Code Coverage information for program execution with Execution Profiler and Performance Analyzer for analyzing and optimizing your code. 6 Capable of creating the Run -Time Environment for the selected target device. 7 Device Support and Database : Should have Integrated Database to support various devices available in the market. Especially support for ARM Cortex M0/M0+/M1, ARM CORTEX M3/M4/M7, ARM Cortex M23/M33 from various vendors like NXP LPC series, STM32 Series, TI etc. 8 There must be Provision of Incorporating New Cortex -M Series Devises . IDE must be capable to pre-configure the development tools for the selected target device. 9 Software Packs with ready -to -use CMSIS : The tools should provide extensive support for Cortex Microcontroller Software Interface Standard 1/5 (CMSIS) with features of collecting libraries, source modules, configuration and header files and documentation. Generic software pack to support a wide range of devices and applications. -

SEGGER's Advanced Debug Technology Made Available For
SEGGER Microcontroller – The Embedded Experts SEGGER’s Advanced Debug Technology Made Available for STM32 Nucleo & Discovery MCU Boards Hilden, Germany – April 26th, 2016 SEGGER has now introduced J-Link firmware for the embedded ST-LINK on STM32 Nucleo, STM32 Discovery and other microcontroller unit (MCU) evaluation boards from STMicroelectronics. This brings the proven reliability and industry-leading performance of SEGGER’s highly popular J-Link debug technology to these items of hardware, thereby leading to more efficient development processes. The upgrade turns a board’s ST-LINK interface into a fully functional J-Link, which can then be employed to debug the board's application processor. By upgrading to the J-Link firmware, developers will subsequently be able to set an unlimited number of breakpoints in Flash memory and debug their applications considerably faster - resulting in better use of engineering resources and shortened time to market. The J-Link firmware offers compatibility with all major tool chains, including those using GDB (GNU Debugger), on all major host platforms (Windows, Mac, Linux), while also attaining elevated operational benchmarks, including the fastest download speed into RAM and Flash memory. The tool needed to upgrade the firmware of the on-board ST-LINKs can be downloaded free of charge from SEGGER’s website. If it ever becomes necessary to do so, the exchange process is completely reversible, restoring the original ST-LINK functionality. “With J-Link firmware installed, users of STM32 Nucleo and STM32 Discovery evaluation boards, amongst others, will benefit from access to essential tools like SEGGER RTT and SystemView for real-time analysis purposes. -

Quick Start Guide for ST STM32F4-Eval and Emide
1 Quick Start Guide for ST STM32F4-Eval and emIDE 1. emIDE software download • Please download emIDE toolchain from emIDE.org. emIDE comes not with an installation program, you can just unzip the file to any location, e.g. c:\emIDE. 2. Segger evaluation software download •Please visit http://segger.com/st-stm3240g-eval.html for latest version of Seg- ger eval softare for STM32F4-Eval. The file contains the Segger software, sample applications as also product documentation. • Unzip the file to the folder of your choice, e.g. c:\work 2. STM32F4-Eval evalboard • Power the evalboard with the ST power supply (+5V regulated input). • Connect J-Link to the board. The ‘Found New Hardware’ Wizard may appear. If so please download and install the J-Link driver from http://segger.com/jlink-soft- ware.html. • Connect the eval board to your network. 3. emIDE workspace • Start emIDE and open the workspace from "Start\Start_STM32F40G_Eval.emP". • Build the project with [F7] or select from the top menu bar, “Build”, then “Buildl’. • Start the debug session with [F5] or select from the top menu bar, "Debug", "Start\Continue". • emIDE downloads the application and halts in main(). Press again [F5] to start the application. 4. Segger webserver sample • The default sample application starts the Segger TCP/IP stack and a web server. • If no DHCP server runs in your network please have a look in the C file "IP_Config_STM32F407.c" how to setup a static ip address. • Please start the PC tool "UDPDiscover.exe" from the directory "Start\Win- dows\TCPIP\UDPDiscover". -

STM32 ARM® Cortex™-M3 Microcontrollers Core: Cortex-M3
34 | SPRING 2008 STM32 ARM® Cortex™-M3 Microcontrollers Core: Cortex-M3 The STM32 family of 32-bit excellent real-time behavior all combined with industry-leading Flash microcontrollers is based power consumption. The STM32 is offered in two pin and on the breakthrough ARM software compatible product lines. The Performance line takes Cortex-M3 core specifically the 32-bit MCU world to new levels of performance and developed for embedded energy efficiency. With its Cortex-M3 core at 72 MHz, it is applications. The STM32 family able to perform high-end computation. Its peripheral set brings benefits from the Cortex-M3 superior control and connectivity. The Access line is the entry architectural enhancements, point of the STM32 family. It has the power of the 32-bit MCU including the Thumb-2® but at a 16-bit MCU cost. Its peripheral set offers excellent instruction set to deliver connectivity and control. improved performance combined with better code density, a tightly coupled nested vectored interrupt controller for Features M • Only seven external components required for a base system • 1.25 DMIPS/MHz Cortex-M3 Core • Easy development and fast time to market – Thumb-2 instruction set brings 32-bit performance with 16-bit code density STM32 Block Diagram – Single cycle multiply and hardware division – Tightly coupled nested vectored interrupt controller • 32 KB-128 KB high performance Flash (256 KB-512 KB available in Q2 2008) • 6 KB-20 KB SRAM (32 KB-64 KB available in Q2 2008) • Low power – Run mode as low as 27 mA at 72 MHz (executing -

Openflow, in Proceedings of the Interna- Tional Conference on Pervasive Computing and Communication Workshops (Percom Workshops)
Traffic Control for Multi-homed End-hosts via Software Defined Networking Anees Mohsin Hadi Al-Najjar B.Sc. (Computer Science), M.Sc. (Computer Science) A thesis submitted for the degree of Doctor of Philosophy at The University of Queensland in 2019 School of Information Technology & Electrical Engineering Abstract Software Defined Networking (SDN) is an emerging technology that allows computer networks to be more efficiently managed and controlled by providing a high level of abstraction and network programmability. Having powerful abstractions and pro- grammability via a centralised network controller provides new potential improve- ments to computer networks, such as easier network management, faster innovation and reduced cost. SDN has been successfully applied in wide area and data centre networks, and has achieved a significant improvement in network performance and efficiency. However, using SDN to control network traffic in end-host devices has not been investigated thoroughly. The research presented in this thesis aims to address this gap and inves- tigates the potential benefits of SDN for end-hosts. This thesis explores the feasibility of applying the SDN methodology to control network traffic on multi-homed end de- vices. The objective was to create a control mechanism by changing the network stack on the client in a way that is transparent to the application layer, the network infras- tructure, and other hosts on the network. In contrast to other solutions such as MPTCP, which require a protocol stack upgrade on all the participating nodes, the approach presented in this thesis allows quick and easy client-side-only deployment. This thesis presents an architecture for embedding SDN components, i.e. -

Ipv6 for Helenos
Charles University in Prague Faculty of Mathematics and Physics MASTER THESIS Mgr. Bc. Anton´ınSteinhauser IPv6 for HelenOS Department of Distributed and Dependable Systems Supervisor of the master thesis: Mgr. Martin Dˇeck´y Study programme: Informatics Specialization: Software Systems Prague 2013 I am much obliged to my thesis supervisor, Mgr. Martin Dˇeck´y,for his advices and hints in this research. I declare that I carried out this master thesis independently, and only with the cited sources, literature and other professional sources. I understand that my work relates to the rights and obligations under the Act No. 121/2000 Coll., the Copyright Act, as amended, in particular the fact that the Charles University in Prague has the right to conclude a license agreement on the use of this work as a school work pursuant to Section 60 paragraph 1 of the Copyright Act. In Prague date 18. 7. 2013 Anton´ınSteinhauser N´azevpr´ace:IPv6 for HelenOS Autor: Anton´ınSteinhauser Katedra: Katedra distribuovan´ych a spolehliv´ych syst´em˚u Vedouc´ıdiplomov´epr´ace: Mgr. Martin Dˇeck´y,Katedra distribuovan´ych a spolehliv´ych syst´em˚u Abstrakt: Tato pr´acerozˇsiˇrujeoperaˇcn´ısyst´emHelenOS o podporu nov´ehoIPv6 protokolu. Implementace protokolu IPv6 je na stejn´e´urovni jako dˇr´ıvˇejˇs´ıimple- mentace IPv4 protokolu. S´ıˇtov´ystack HelenOS nyn´ınab´ız´ıtˇrim´odypr´acese s´ıt´ı: uˇz´ıv´an´ıpouze IPv4 protokolu, uˇz´ıv´an´ıpouze IPv6 protokolu a du´aln´ım´od, kter´y umoˇzˇnujepouˇz´ıvat oba protokoly najednou. Pr´acepopisuje pˇredchoz´ıstav s´ıˇtov´ehostacku HelenOS, analyzuje rozd´ılymezi IPv4 protokolem a IPv6 protokolem a zd˚uvodˇnujejednotliv´astrategick´arozhod- nut´ı.