1 Correspondence and Reduplication in Language Play: Evidence From
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Songs As Sights: Latinized Versions of Popular Lyrics As Sight Translation Exercises
CPL Online 3.1 Fall 2006 Judith P. Hallett Page 1 Songs As Sights: Latinized Versions of Popular lyrics As Sight Translation Exercises Judith P. Hallett Classics Department University of Maryland, College Park I. Introduction Neapoli amor est rex. Carmen amoris cantat grex. Oculos pulsat si luna , fruimini nunc amore. Mundus vinosis si nitet, potimini nunc amore. Tintinnabula tinnient, amatores laeti canent, “Vita Bella!” Cordaque—tippitippite tippitippite—saltabunt tarantella. Mica, stella. Astra salivam si movent, vescimini nunc amore. Nubes circumdat si pedes, vos superavit amor. Ambulatis si vigilantes somniante stupore. Ignoscite mihi, sed vos fungimini nunc amore. This, neo-Latin, text was designed as part of a classroom exercise, to reinforce memorization—or at least recognition—of the major verbs in classical Latin that govern an object in the ablative case. Of course, and as many Latin students learn, there is an “acronymic mnemonic” that supposedly serves a similar function, an English word formed by the first letters of these verbs: PUFF, for potior, utor, fungor and fruor. To be sure, this acronym neglects vescor, but, then again, the neo-Latin text is missing utor. More important, this text actually illustrates this construction in action, with the repeated ablative noun amore. It illustrates some other Latin linguistic phenomena worth reinforcing as well. One is the second person plural, present active indicative of third and fourth conjugation deponents such as these PUFF verbs. Others include the locative of Neapolis; present general conditions; the so-called dative of offense with ignosco; and the ablative absolute. What is more, this text is a loose translation of English lyrics—spiced with contemporary Italian words and allusions—known to, or at least knowable by, my students at the University of Maryland, College Park. -

Acquisition of Pig Latin : a Case Study*
J, child 1,ong. 16 (1989)~365 386. printed in Great Britain Acquisition of Pig Latin : a case study* NELSON COWAN CJniversity of Missouri, Columbia (Received I 2 July 1988. Revised 6 October I 988) ABSTRACT P A boy's acquisition of Pig 1,atin was monitored throughout the year preceding first grade. Abilities underlying this game include the iden- tification of words, deletion of the first syllabic onset (i.e. prevocalic i consonants) of each word, blending of this onset and the suffix [el] onto the word's end, and short-term memory for speech units. Performance improved over time as the underlying abilities developed. Meanwhile, various informative errors were made. Throughout most of the study, onsets that were correctly removed from a word's beginning were often added to its end incorrectly; unstressed function words were repeated intact and. not transformed; and the first syllabic onset was overlooked when the syllable was unstressed. Because speech games like this one depend upon basic language skills, they can clarify aspects of ordinary language development. A child's method of carrying out a speech game can reveal his or her conception of the language's units and rules (Sherzer 1970, 1982, Kir- schenblatt-Gimblett 1976, Morais, Carey, Alegria & Bertelson 1979, Alegria, Pignot & Morais 1982, Cowan & 1,eavitt 1982, 1987, Cowan, Braine & Leavitt 1985, l'reiman I 985, 1986, Content, Kolinsky, Morais & Bertelson 1986). The developmental course of a speech game therefore would seem to be a promising source of information about the acquisition of linguistic knowledge. However, little is known about this aspect of development. -
Trump Ends TPS, Devastates Salvadoran Families
FOR SNOW AND WEATHER UPDATES, VISIT DAILYTARHEEL.COM Serving UNC students and the University community since 1893 Volume 125, Issue 56 dailytarheel.com Wednesday, January 17, 2018 Trump ends TPS, devastates Salvadoran families By Marin Wolf Staff Writer Joseph Nolasco held a poster reading “TPS” in big blue letters above his head. Despite the wind and near-freezing temperature, the 9-year-old stayed focused on the speakers at the podium to his right. He eagerly shouted, “Protect TPS!” as he stood with his mother, even though he does not know what that phrase means for him and his family. As a third grader, Nolasco does not worry about his family’s legal status. He is busy learning about multiplication, division and fractions in math, his favorite sub- ject. Nolasco’s mother, Marina Vasquez of Durham, said she chose not to tell him too many details about the termination of the Temporary Protected Status that allowed her to come to the U.S. nearly 20 years ago after a devastating earthquake in El ONE STUDENT’S ASSAULT AND Salvador. “(My children) would suffer just like all of us if we even talked about separation,” ALERTCAROLINA’S RESPONSE Vasquez said through a translator. DTH/EMILY YUE El Centro Hispano hosted a press conference Saturday afternoon to speak By Kiana Cole She was walking from Kenan pass out. Maybe then he’d leave his grip until he heard the wit- out against the Secretary of Homeland Director of Investigations Music Building to her residence her alone. But she didn’t need to ness say she was calling the Security’s decision to end the TPS designa- hall. -

Word Games As Experimental Linguistics 1
Michael Cahill Word Games as Experimental Linguistics 1 Word Games as Experimental Linguistics Michael Cahill* “Word games” in languages can tell us something about syllable structure and underlying forms. Sometimes they are helpful in determining orthographic issues, such as whether to include a letter in the spelling or not. Here I introduce word games by discussing Pig Latin in English, and then report on two SIL projects which used language games to gain more insight into the language. 1. What are word games? There are undoubtedly many kinds of games with language around the world, but here I want to focus on one particular type. What I call “word games” in this article are games where people systematically insert sounds or switch the order of individual sounds or syllables. Pig Latin is perhaps the best-known word game in English. In Pig Latin, you remove the first consonants of a word, add them to -ay (phonetically [ei]) and put that new syllable at the end of the word. So ‘pig’ becomes ig-pay. ‘Star’ becomes ar-stay. ‘Scratch’ becomes atch-scray. It is not just the first consonant that moves, but the whole consonant cluster, even if it is not written as a consonant. ‘Choir’ becomes ire-quay and ‘squid’ becomes id-squay. (If the target word begins with a vowel, instead of removing a consonant you add ‘way’ at the end, so ‘item’ becomes item- way.) One of the main conclusions you can draw from Pig Latin is that the ONSET of a syllable in English is a psycholinguistically real unit, whether it is one consonant or three. -
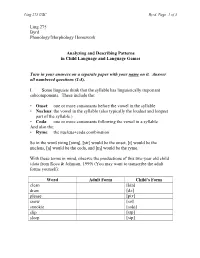
Ling 275 USC Byrd, Page 1 of 5
Ling 275 USC Byrd, Page 1 of 5 Ling 275 Byrd Phonology/Morphology Homework Analyzing and Describing Patterns in Child Language and Language Games Turn in your answers on a separate paper with your name on it. Answer all numbered questions (1-8). I. Some linguists think that the syllable has linguistically important subcomponents. These include the: • Onset: one or more consonants before the vowel in the syllable • Nucleus: the vowel in the syllable (also typically the loudest and longest part of the syllable.) • Coda: one or more consonants following the vowel in a syllable And also the: • Ryme: the nucleus+coda combination So in the word string [strIN], [str] would be the onset, [I] would be the nucleus, [N] would be the coda, and [IN] would be the ryme. With these terms in mind, observe the productions of this two-year old child (data from Roca & Johnson, 1999) (You may want to transcribe the adult forms yourself): Word Adult Form Child’s Form clean [kin] draw [dO] please [piz] snow [so] snookie [sUki] slip [sIp] sleep [sip] Ling 275 USC Byrd, Page 2 of 5 1. State, using the necessary terms above, the PATTERN of the child’s productions: For example “The child’s word forms must/must not…” Now consider the following example: Word Adult Form Child’s Form friend [fEn] 2. Restate the PATTERN, taking into account this form: Finally, consider the following forms from the same child. Word Adult Form Child’s Form straw [dO] skin [gIn] spoon [bun] 3. Do these forms conform to the PATTERN you observed and stated in (2)? 4. -

Translating the Language of Birds William Young Arlington, Virginia
® THE LANGUAGE QUARTERLY Vol. XXVIII, No. 1 Winter 2003 VERBATIM Editor: Erin McKean Founding Editor: Laurence Urdang Translating the Language of Birds William Young Arlington, Virginia any hobbyists who look for wild birds call izations and use songs or calls to create colloquial Mthemselves birders rather than birdwatchers. names. The willet, which was named for its song, also In addition to being able to identify species by is known by the colloquial names bill-willie, pill-wil- plumage, skilled birders tend to be familiar with let, pill-will-willet, and will-willet. In Australia, a col- bird songs and calls. Vocalizations sometimes pro- loquial name for the magpie-lark is peewit. vide the only reliable information for identifying a Many bird names describe a vocalization rather species in the field. than represent the actual sound. Examples include Birders who are not musically gifted (including the laughing gull, whistling kite, piping plover, me) face the difficult task of learning and remember- whooping crane, chipping sparrow, plaintive cuck- ing vocalizations for hundreds of species. The chal- oo, melodious blackbird, musician wren, snoring lenge is daunting because a particular species may rail, and dark chanting goshawk. Cisticolas, which utter multiple territorial songs, contact calls and are small, brownish songbirds found mostly in regional dialects. An effective learning technique is to Africa, are accomplished vocalists. The adjectives translate the vocalizations of a species into familiar used in their species names include bubbling, chat- words or phrases. Just as many people cannot tering, chirping, churring, croaking, piping, rat- remember lyrics to popular songs without singing the tling, siffling, singing, tinkling, tink-tink, trilling, melody, many birders cannot remember bird songs wailing, whistling, and zitting. -

Language Games
1 Author's Name: Stuart Davis Article Contract Number: 17106A/0179 Article Serial Number: 09-004 Article Title: Language Games Language Games The term language game refers to a fairly widespread language play phenomenon in which phonological forms of words are systematically alterred so as to disguise what they are. Other terms that are sometimes used instead of langauge games are secret languages, disguised speech, play-languages, and ludlings. The most well-known language game in the English-speaking world is Pig Latin. To change a normal English word into Pig Latin, the word-initial consonant (or consonant cluster) of the English word is moved to the end and then the vowel [e] is added after it. For example, the way one would say Pig Latin in Pig Latin would be [Ιgpe ætΙnle]. Not all language games are like English Pig Latin. In other language games, words are alterred in a different manner. Crucially, though, with any language game, the difference between the language game word and the corres- ponding word in the real language is a systematic one. In this way, the language game is potentially productive. When presented with a new word the speaker can automatically convert it into the corresponding language game form, and when hearing a language game form for the first time the speaker can immediately recover what the corresponding normal language word is. Because of this latter notion of recoverability certain types of language play, such as rhyming slang, should not be considered a language game. This article first discusses a typology of language games in which the various possible phonological alternations that occur in language games cross-linguistically are presented and exemplified. -

Images of Lawyers and the Three Stooges Randall T
University of Oklahoma College of Law From the SelectedWorks of Randall Coyne Spring 1997 Images of Lawyers and the Three Stooges Randall T. Coyne, University of Oklahoma College of Law Available at: https://works.bepress.com/randall_coyne/14/ +(,121/,1( Citation: 22 Okla. City U. L. Rev. 247 1997 Content downloaded/printed from HeinOnline (http://heinonline.org) Wed Jun 6 09:25:11 2012 -- Your use of this HeinOnline PDF indicates your acceptance of HeinOnline's Terms and Conditions of the license agreement available at http://heinonline.org/HOL/License -- The search text of this PDF is generated from uncorrected OCR text. -- To obtain permission to use this article beyond the scope of your HeinOnline license, please use: https://www.copyright.com/ccc/basicSearch.do? &operation=go&searchType=0 &lastSearch=simple&all=on&titleOrStdNo=0364-9458 IMAGES OF LAWYERS AND THE THREE STOOGES RANDALL COYNE* This Article surveys several of the Three Stooges "shorts"dealing with law and lawyers, particularlythe film Disorderin the Court. Professor Coyne provides a comedic portrayal of the courtroom through the lam- poons of the Three Stooges. According to film critic Leonard Maltin, an observation first made in a 1937 issue of Motion Picture Herald remains true today. "The public, upon which the screen depends for its existence, appears. ... , to be divided roughly into two groups, one composed of persons who laugh at the Three Stooges and the other made up of those who wonder why."' 1. THE STOOGE VERSION OF LAW Between 1934 and 1959, Columbia Studios released 190 short subjects starring the'Three Stooges. -

Pacific Languages Pacific Languages
Pacific Languages Pacific Languages AN INTRODUCTION John Lynch © 1998 University of Hawai‘i Press All rights reserved Printed in the United States of America 98 99 00 01 02 03 5 4 3 2 1 Library of Congress Cataloging-in-Publication Data Lynch, John Pacific languages: an introduction / [John Lynch]. p. cm. Includes bibliographical references and index. ISBN 0–8248–1898–9 (alk. paper) 1. Pacific Area—Languages. I. Title. P381.P3L96 1998 499—dc21 97–24552 CIP University of Hawai‘i Press books are printed on acid-free paper and meet the guidelines for permanence and durability of the Council on Library Resources Designed by Josie Herr This book is licensed under the terms of Creative Commons Attribution- NonCommercial-NoDerivatives 4.0 International (CC BY-NC-ND 4.0), which permits readers to freely download and share the work in print or electronic for- mat for non-commercial purposes, so long as credit is given to the author. Derivative works and commercial uses require permission from the publisher. For details, see https://creativecommons.org/licenses/by-nc-nd/4.0/. The Creative Commons license described above does not apply to any material that is separately copyrighted. Please refer to the credit lines and source nota- tions in the book to determine the copyright holders for images and other third- party material. The open-access ISBNs are 9780824842581 (PDF) and 9780824881832 (EPUB). The open-access editions of this publication were made possible by The Univer- sity of the South Pacific (USP) OER Course Conversion Grant. This competitive funding program is open to all USP faculty and staff wishing to integrate open materials into mainstream teaching and learning.