DP8390 Network Interface Controller: an Introductory Guide Utb Nomdo H Ewr Eoyi Ilb Using
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Hardware Components and Internal PC Connections
Technological University Dublin ARROW@TU Dublin Instructional Guides School of Multidisciplinary Technologies 2015 Computer Hardware: Hardware Components and Internal PC Connections Jerome Casey Technological University Dublin, [email protected] Follow this and additional works at: https://arrow.tudublin.ie/schmuldissoft Part of the Engineering Education Commons Recommended Citation Casey, J. (2015). Computer Hardware: Hardware Components and Internal PC Connections. Guide for undergraduate students. Technological University Dublin This Other is brought to you for free and open access by the School of Multidisciplinary Technologies at ARROW@TU Dublin. It has been accepted for inclusion in Instructional Guides by an authorized administrator of ARROW@TU Dublin. For more information, please contact [email protected], [email protected]. This work is licensed under a Creative Commons Attribution-Noncommercial-Share Alike 4.0 License Higher Cert/Bachelor of Technology – DT036A Computer Systems Computer Hardware – Hardware Components & Internal PC Connections: You might see a specification for a PC 1 such as "containing an Intel i7 Hexa core processor - 3.46GHz, 3200MHz Bus, 384 KB L1 cache, 1.5MB L2 cache, 12 MB L3 cache, 32nm process technology; 4 gigabytes of RAM, ATX motherboard, Windows 7 Home Premium 64-bit operating system, an Intel® GMA HD graphics card, a 500 gigabytes SATA hard drive (5400rpm), and WiFi 802.11 bgn". This section aims to discuss a selection of hardware parts, outline common metrics and specifications -

Introduction
Chapter 1: Introduction Operating System Concepts with Java – 8th Edition 1.1 Silberschatz, Galvin and Gagne ©2009 Chapter 1: Introduction n What Operating Systems Do n Computer-System Organization n Computer-System Architecture n Operating-System Structure n Operating-System Operations n Process Management n Memory Management n Storage Management n Protection and Security Operating System Concepts with Java – 8th Edition 1.2 Silberschatz, Galvin and Gagne ©2009 Objectives n To provide a grand tour of the major operating systems components n To provide coverage of basic computer system organization Operating System Concepts with Java – 8th Edition 1.3 Silberschatz, Galvin and Gagne ©2009 What is an Operating System? n A program that acts as an intermediary between a user of a computer and the computer hardware n Operating system goals: l Execute user programs and make solving user problems easier l Make the computer system convenient to use l Use the computer hardware in an efficient manner Operating System Concepts with Java – 8th Edition 1.4 Silberschatz, Galvin and Gagne ©2009 Computer System Structure n Computer system can be divided into four components l Hardware – provides basic computing resources 4 CPU, memory, I/O devices l Operating system 4 Controls and coordinates use of hardware among various applications and users l Application programs – define the ways in which the system resources are used to solve the computing problems of the users 4 Word processors, compilers, web browsers, database systems, video games l Users 4 -

Introduction to PC Operating Systems
Introduction to PC Operating Systems Operating System Concepts 8th Edition Written by: Abraham Silberschatz, Peter Baer Galvin and Greg Gagne John Wiley & Sons, Inc. ISBN: 978-0-470-12872-5 Chapter 1 Introduction An operating system is a program that manages the computer hardware. It also provides a basis for application programs and acts as an intermediary between the computer user an the computer hardware. Mainframe, Personal Computers, Handheld Computes, others. Mainframe Operating Systems Designed primarily to optimize utilization of hardware. Personal Computer Operating Systems Designed to support complex games, business applications, etc. Handheld Computer Operating Systems Provide an environment in which a user can easily interface with the computer to execute programs. Other Operating Systems Are designed to be convenient, and some to be efficient and some a combination of the two. (i.e. number pad, indicator lights) Objectives • To provide a grand tour of the major components of operating systems. • To describe the basic organization of computer systems. What Operating Systems Do First, we need to understand that a computer system can be divided roughly into four components; hardware, operating system, application programs and users. Computer Hardware is the physical components of your computer system. Operating system is the set of computer instructions, called a computer program, that controls the allocation of computer hardware such as memory, disk devices, printers, and CD and DVD drives, and provides the capability for you to communicate with the computer. Systems software functions as a bridge between computer system hardware and the application software and is made up of many control programs, including the operating system, communications software and database manager. -

Network Interface Controller Drivers Release 20.02.1
Network Interface Controller Drivers Release 20.02.1 May 18, 2020 CONTENTS 1 Overview of Networking Drivers1 2 Features Overview4 2.1 Speed capabilities.....................................4 2.2 Link status.........................................4 2.3 Link status event......................................4 2.4 Removal event.......................................5 2.5 Queue status event.....................................5 2.6 Rx interrupt.........................................5 2.7 Lock-free Tx queue....................................5 2.8 Fast mbuf free.......................................5 2.9 Free Tx mbuf on demand..................................6 2.10 Queue start/stop......................................6 2.11 MTU update........................................6 2.12 Jumbo frame........................................6 2.13 Scattered Rx........................................6 2.14 LRO............................................7 2.15 TSO.............................................7 2.16 Promiscuous mode.....................................7 2.17 Allmulticast mode.....................................8 2.18 Unicast MAC filter.....................................8 2.19 Multicast MAC filter....................................8 2.20 RSS hash..........................................8 2.21 Inner RSS..........................................8 2.22 RSS key update.......................................9 2.23 RSS reta update......................................9 2.24 VMDq...........................................9 2.25 SR-IOV...........................................9 -

Personal Computer Hardware from Wikipedia, the Free Encyclopedia (Redirected from Computer Hardware)
Personal computer hardware From Wikipedia, the free encyclopedia (Redirected from Computer hardware) Personal computer hardware are component devices which are typically installed into or peripheral to a computer case to create a personal computer upon which system software is installed including a firmware interface such as a BIOS and an operating system which supports application software that performs the operator's desired functions. Operating systems usually communicate with devices through hardware buses by using software device drivers. Contents 1 Motherboard 2 Power supply 3 Removable media devices 4 Secondary storage 5 Sound card Hardware of a modern personal computer 6 Input and output peripherals 1. Monitor 6.1 Input 2. Motherboard 6.2 Output 3. CPU 7 See also 4. RAM 5. Expansion cards 6. Power supply 7. Optical disc drive Motherboard 8. Hard disk drive 9. Keyboard Main article: Motherboard 10. Mouse The motherboard is the main component inside the case. It is a large rectangular board with integrated circuitry that connects the other parts of the computer including the CPU, the RAM, the disk drives (CD, DVD, hard disk, or any others) as well as any peripherals connected via the ports or the expansion slots. Components directly attached to the motherboard include: The central processing unit (CPU) performs most of the calculations which enable a computer to function, and is sometimes referred to as the "brain" of the computer. It is usually cooled by a heat sink and fan. Newer CPUs include an on-die Graphics Processing Unit (GPU). The chip set mediates communication between the CPU and the other components of the system, including main memory. -

RAID and RAID Controllersdrive 1 Unit That Is Seen by the Attached System As a Single Drive
DRIVE 1 DRIVE 2 DRIVE 1 DRIVE 3 DRIVE 2 DRIVE 4 What is RAID and Why do Your Customers Need it? RAID (Redundant Array of Inexpensive Disks) is a data storage structure that allows a data center to combine two or more physical storage devices (HDDs, SSDs, or both) into a logical RAID and RAID ControllersDRIVE 1 unit that is seen by the attached system as a single drive. There are two basic RAID configurations: What is a Controller Card? 1. Striping (RAID 0) writes some data to one drive and some data to another, DRIVE 2 minimizing read and write access times and improving I/O performance. A controller card is a device that sits between the host system and the storage system, and allows the two systems to communicate with each other. 2. Mirroring (RAID 1) copies all information from one drive directly to another, preventing loss of data in the event of a drive failure. DRIVE 1 Mirroring Mirroring & Striping Duplicates data from primary Mirrors data that is striped, spread DRIVE 2 DRIVE 1 drive to secondary drive evenly across multiple disks DRIVE 1 DRIVE 1 DRIVE 3 DRIVE 2 DRIVE 2 DRIVE 2 DRIVE 4 There are two types of controller cards: Host Bus Adapters (HBAs), and RAID controller cards. 1. An HBA is an expansion card that plugs into a slot (such as PCI-e) on the computer DRIVE 1 system’s motherboard and provides fast, reliable non-RAID I/O between the host and RAID can be hardware-based or software-based.DRIVE 1 DRIVE 3 the storage devices. -

Network Interface Controller Drivers Release 17.11.10
Network Interface Controller Drivers Release 17.11.10 Feb 27, 2020 CONTENTS 1 Overview of Networking Drivers1 2 Features Overview4 2.1 Speed capabilities...................................4 2.2 Link status.......................................4 2.3 Link status event....................................4 2.4 Removal event.....................................5 2.5 Queue status event..................................5 2.6 Rx interrupt.......................................5 2.7 Lock-free Tx queue..................................5 2.8 Fast mbuf free.....................................6 2.9 Free Tx mbuf on demand...............................6 2.10 Queue start/stop....................................6 2.11 MTU update......................................6 2.12 Jumbo frame......................................6 2.13 Scattered Rx......................................7 2.14 LRO...........................................7 2.15 TSO...........................................7 2.16 Promiscuous mode..................................7 2.17 Allmulticast mode...................................8 2.18 Unicast MAC filter...................................8 2.19 Multicast MAC filter..................................8 2.20 RSS hash.......................................8 2.21 RSS key update....................................8 2.22 RSS reta update....................................9 2.23 VMDq..........................................9 2.24 SR-IOV.........................................9 2.25 DCB...........................................9 2.26 VLAN filter.......................................9 -

Adaptec 39320A/U320 SCSI RAID 0 Or 1 User's Guide
Adaptec™ 39320A/U320 SCSI RAID 0 or 1 User's Guide Introduction Hardware Installation BIOS RAID Configuration And Management Windows Operating System Driver Installation SCSI Cables and Connectors Adaptec U320 SCSI RAID 0 or 1 Specifications Adaptec U320 SCSI RAID 0 or 1 Troubleshooting Adaptec U320 SCSI RAID Regulatory Information Adaptec U320 SCSI RAID Glossary NOTE: A NOTE indicates important information that helps you make better use of your computer. NOTICE: A NOTICE indicates either potential damage to hardware or loss of data and tells you how to avoid the problem. CAUTION: A CAUTION indicates a potential for property damage, personal injury, or death. Information in this document is subject to change without notice. © 2004 Dell Inc. All rights reserved. Reproduction in any manner whatsoever without the written permission of Dell Inc. is strictly forbidden. Trademarks used in this text: Dell, the DELL logo, and Dell OpenManage are trademarks of Dell Inc.; Intel, Pentium, and Celeron are registered trademarks of Intel Corporation; Microsoft and Windows are registered trademarks of Microsoft Corporation. Red Hat is a registered trademark of Red Hat, Inc. Other trademarks and trade names may be used in this document to refer to either the entities claiming the marks and names or their products. Dell Inc. disclaims any proprietary interest in trademarks and trade names other than its own. Model Adaptec U320 SCSI RAID 0 or 1 March 2005 P/N NC234 Rev. A00 Initial release: April 2004 Last revised: March 2005 Back to Contents Page Introduction Adaptec™ U320 SCSI RAID 0 or 1 User's Guide Overview RAID Storage Management Utilities System Requirements Adaptec U320 SCSI RAID 0 or 1 Features Configuration Features RAID Performance Features RAID Management Features Fault Tolerance Features Software Utilities Operating System Drivers and Utility Adaptec U320 SCSI RAID 0 or 1 Firmware Overview The Adaptec U320 SCSI RAID 0 or 1 is a high-performance 64-bit/133-MHz PCI-X, dual-channel SCSI card with integrated RAID 0 and 1. -

Embedded Controller Hardware Design by Ken Arnold
A Volume in the Embedded Technology™ Series Embedded Controller Hardware Design by Ken Arnold www.LLH-Publishing.com www.EmbeddedControllerHardwareDesign.com ii Embedded Control Hardware Design © 2001 by LLH Technology Publishing. All rights reserved. No part of this book may be reproduced, in any form or by any means whatsoever, without permission in writing from the publisher. While every precaution has been taken in the preparation of this book, the publisher and author assume no responsibility for errors or omissions. Neither is any liability assumed for damages resulting from the use of the information contained herein. ISBN: 1-878707-52-3 Library of Congress Control Number: 00-135391 Printed in the United States of America 10 9 8 7 6 5 4 3 2 1 Project management and developmental editing: Harry Helms, LLH Technology Publishing Interior design and production services: Greg Calvert, Model, CO Cover design: Sergio Villareal, Vista, CA www.LLH-Publishing.com www.EmbeddedControllerHardwareDesign.com iii Dedication This book is dedicated in memory of my father, Kenneth Owen Arnold, who always encouraged me to follow my dreams. When other adults discouraged me from entering the engineering field, he told me, “If you really like what you’re doing and you’re good at it, you will be successful.” Nowadays I get paid to have fun doing things I’d do for free anyway, so that meets my definition of success! Thanks, Dad. iv Acknowledgment This book is a direct result of contributions from many of the students I have been fortunate enough to have in my embedded computer engineering courses at the University of California—San Diego extension. -
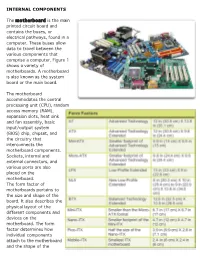
INTERNAL COMPONENTS the Motherboard Is the Main Printed
INTERNAL COMPONENTS The motherboard is the main printed circuit board and contains the buses, or electrical pathways, found in a computer. These buses allow data to travel between the various components that comprise a computer. Figure 1 shows a variety of motherboards. A motherboard is also known as the system board or the main board. The motherboard accommodates the central processing unit (CPU), random access memory (RAM), expansion slots, heat sink and fan assembly, basic input/output system (BIOS) chip, chipset, and the circuitry that interconnects the motherboard components. Sockets, internal and external connectors, and various ports are also placed on the motherboard. The form factor of motherboards pertains to the size and shape of the board. It also describes the physical layout of the different components and devices on the motherboard. The form factor determines how individual components attach to the motherboard and the shape of the computer case. Various form factors exist for motherboards, as shown in this chart. The most common form factor in desktop computers was the AT, based on the IBM AT motherboard. The AT motherboard can be up to approximately 1 foot wide. This cumbersome size led to the development of smaller form factors. The placement of heat sinks and fans often interferes with the use of expansion slots in smaller form factors. A newer motherboard form factor, ATX, improved on the AT design. The ATX case accommodates the integrated I/O ports on the ATX motherboard. The ATX power supply connects to the motherboard via a single 20-pin connector, instead of the confusing P8 and P9 connectors used with some earlier form factors. -

Embedded Controller Usage in Low Power Embedded Designs An
White Paper Matthew Lee Embedded Platform Application Engineer Controller Usage Intel Corporation in Low Power Embedded Designs An Overview September 2011 326133 Embedded Controller Usage in Low Power Embedded Designs Executive Summary Embedded Controllers are a common part of Intel’s low power embedded reference designs and, therefore, an important consideration for system designers to create derivative designs for an ODM or OEM. This white paper will provide system designers with sufficient knowledge to understand the form, fit and function of Embedded Controllers and how best to include them in a design. The Intel® Embedded Design Center provides qualified developers with web-based access to technical resources. Access Intel Confidential design materials, step-by step guidance, application reference solutions, training, Intel’s tool loaner program, and connect with an e-help desk and the embedded community. Design Fast. Design Smart. Get started today. http://www.intel.com/p/en_US/embedded. 2 Embedded Controller Usage in Low Power Embedded Designs Contents Background ...........................................................................................................5 Solution ................................................................................................................5 What Is An Embedded Controller? .............................................................................5 Embedded Controller Functional Overview ..................................................................7 Hard-Wired Functionality: -

Dell EMC Poweredge R340 Technical Guide
Dell EMC PowerEdge R340 Technical Guide Regulatory Model: E58S Series Regulatory Type: E58S001 June 2021 Rev. A07 Notes, cautions, and warnings NOTE: A NOTE indicates important information that helps you make better use of your product. CAUTION: A CAUTION indicates either potential damage to hardware or loss of data and tells you how to avoid the problem. WARNING: A WARNING indicates a potential for property damage, personal injury, or death. © 2018 2021 Dell Inc. or its subsidiaries. All rights reserved. Dell, EMC, and other trademarks are trademarks of Dell Inc. or its subsidiaries. Other trademarks may be trademarks of their respective owners. 1 Product overview Topics: • Introduction • New technologies Introduction The PowerEdge R340 rack system consists of the Intel® Xeon® E-2200 processor family used in conjunction with the Intel® C246 series chipset Platform Controller Hub (PCH). The PowerEdge R340 rack system is a two‐chip platform (enabled by the chipset) when compared to the traditional three‐chip platforms (Processor, Memory controller, and I/O controller). It also includes an integrated memory controller (IMC) and integrated I/O (IIO) (such as PCI Express and DMI3) on a single silicon die. New technologies The PowerEdge R340 is the ideal entry-level server for data centers & SMB to address small scale enterprise applications designed for productivity and data intensive applications for remote office/branch offices requiring maximum uptime. The PowerEdge R340 provides a choice of either 8x2.5” or 4x3.5” hot-plug drive configurations for added storage flexibility. 100% increase in core count significantly improves performance while a quiet, short-depth form factor is optimized for constrained spaces.