Connectwise Control Comprehensive Security Best Practice Guide
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Test Result Report for Anydesk
Performance Test Results Report Prepared for AnyDesk For period 08/31/2020 – 09/09/2020 Reporter: Aliaksandr Hryshutsin Page: 1 of 13 Creation Date: 9/21/2020 Contents 1 Testing Approach ........................................................................................................................................... 3 1.1 Types of Tests ......................................................................................................................................... 3 1.2 Test set-up ............................................................................................................................................... 3 2 Summary on Test Results .............................................................................................................................. 4 2.1 Summary ................................................................................................................................................. 4 3 Test results ..................................................................................................................................................... 4 3.1 Framerate ................................................................................................................................................ 4 3.2 Latency .................................................................................................................................................... 5 3.3 Bandwidth ............................................................................................................................................... -
Distance Learningʼs Impact on Education IT
Key Insights Distance Learningʼs Impact on Education IT The changes taking place in the education COVID-19 caused an acceleration of K-12 education’s technology landscape as a result of the digital roadmap in three key areas: coronavirus school closures are extensive — and many will be permanent or evolving. Closing the “homework gap” to enable digital However, the rapid speed of change is creating learning. Mobile hotspots are increasingly going home, with students, new challenges for IT teams. creating an "always-connected" online learning dynamic1 New research by Absolute examines the Enabling remote and hybrid learning models. effects of distance learning on endpoint 75% of schools intend to operate remote or hybrid models2 health, device usage, safety, and security as schools adapt to remote and hybrid learning Protecting students, staff, and schools from cyberattacks. 60% of all malware attacks (particularly ransomware) occur in models in the 2020/21 school year. education3 To better understand what is happening on the ground, Millions of Absolute- 10,000 Schools and 12 analyst reports and Absolute studied: enabled devices districts peer research This is what we discovered… Reliance on devices to drive IT teams are doing School devices are mainly learning outcomes has more with less. being used for learning. While federal stimulus packages may help increased. 40% in the short term, long-term budgets are 16% YouTube, Edgenuity®, uncertain: Google Docs™, and 5% Google Classrooms 61% 28% are where most 11% students are increase in -

Teamviewer Tensor Provides Secure Remote Access, Support and Collaboration with AR, Iot
REPORT REPRINT TeamViewer Tensor provides secure remote access, support and collaboration with AR, IoT OCTOBER 30 2018 By Raul Castanon-Martinez In the past year, TeamViewer set up a business unit to define and execute its enterprise strategy, which includes revamping its channel partner program and expanding its portfolio. Its new enterprise SaaS offering aims to leverage its connectivity technology to address such enterprise use cases as access, support, control and collaboration. THIS REPORT, LICENSED TO TEAMVIEWER, DEVELOPED AND AS PROVIDED BY 451 RESEARCH, LLC, WAS PUBLISHED AS PART OF OUR SYNDICATED MARKET INSIGHT SUBSCRIPTION SERVICE. IT SHALL BE OWNED IN ITS ENTIRETY BY 451 RESEARCH, LLC. THIS REPORT IS SOLELY INTENDED FOR USE BY THE RECIPIENT AND MAY NOT BE REPRODUCED OR RE-POSTED, IN WHOLE OR IN PART, BY THE RE- CIPIENT WITHOUT EXPRESS PERMISSION FROM 451 RESEARCH. ©2019 451 Research, LLC | WWW.451RESEARCH.COM REPORT REPRINT Summary TeamViewer is well known for its remote-control, desktop sharing and file-transfer software products. The company is now looking to leverage its technology and extensive footprint to target the enterprise segment. In the past year, it set up a business unit to define and execute its enterprise strategy, which includes revamping its channel partner program and expanding its portfolio with new offerings such as Tensor, an enterprise SaaS for secure remote access, support and collaboration. 451 TAKE TeamViewer’s connectivity technology has helped it gain an extensive market footprint and has earned it a strong reputation with DevOps and IT professionals. Given its trajectory, it’s fair to say that TeamViewer waited too long to go after the enterprise segment. -

Free Remote Support Software Download
Free remote support software download TeamViewer is easily the best free remote access software I've ever used. There are tons TeamViewer Review & Free Download. I suggest trying Remote Utilities · Chrome Remote Desktop · A Review of AnyDesk, a Free. AeroAdmin - zero configuration FREE remote desktop software. Use it for quick and easy remote desktop access and PC control. Free remote access software Ammyy Admin makes control of a remote PC quick have to download and install massive remote desktop software which brings. Remote access software allows you to control your PC remotely, from anywhere in the world. Powerful, and free to try. Connect to remote computers, provide remote support, & collaborate online with TeamViewer, Download Free . Receive support without installing software. Remote Desktop Control allows you to control any remote computer from another computer. Such task is no longer just for network administrators, now you can. Free remote control, remote desktop, remote access software. Remote support and desktop sharing. Free, easy to use, instant screen sharing. Custom Screen Sharing and Online Meetings on your Servers. Connect to remote computers, provide remote support, and collaborate online with TeamViewer, the Get a free sneak peek until October Download now. Free remote access and desktop sharing software. Download and install the software for your OS on the computer or device you are connecting from and on. Access all your programs, documents and files from anywhere, without having to entrust your AnyDesk is the fastest remote desktop software on the market. Thank you for downloading AnyDesk! By downloading and using AnyDesk, you accept our license agreement and our privacy statement. -

2019 Most Popular Free Remote Desktop Solutions
[UPDATED] 2019 Most Popular Free Remote Desktop Solutions Updated January 24, 2019: We have added Zoho Assist! JOINME VS ANYDESK VS CHROME REMOTE DESKTOP VS Please look below for the added Remote Desktop software review and also take a look at our updated comparison table. WINDOWS RDP VS ULTRAVNC VS REMOTE UTILITIES VS TEAMVIEWER (PERSONAL USE) VS SCREENCONNECT VS LITEMANAGER FREE VS WAYK NOW VS ZOHO ASSIST JOINME VS ANYDESK VS CHROME REMOTE DESKTOP VS WINDOWS RDP VS ULTRAVNC VS REMOTE UTILITIES VS TEAMVIEWER (PERSONAL USE) VS SCREENCONNECT VS LITEMANAGER FREE VS WAYK NOW VS ZOHO ASSIST In the same way there is an abundance of Password Manager software and 2 Factor-Authentication methods to choose from, finding the perfect remote connection software for you or your company can be as hard as finding the perfect date on Tinder. But don’t worry, we’ve worked hard and done the background search so you won’t have to. After much in-house debate and research, the following are our favorites free remote connections : join.me, AnyDesk, Chrome Remote Desktop, Windows Remote Desktop Connection, UltraVNC, Remote Utilities, TeamViewer (Personal Use), ConnectWise Control, LiteManager Free, WaykNow and Zoho Assist. Remote connection software helps users work on a computer through another computer. These programs are a must for technical support staff, as they enable IT pros to help when physical access is impossible. It also allows anyone to start or attend meetings, collaborate on projects, and discuss business, even when they are nowhere near their desktops. So let the comparing begin ! The application is completely free. -

Connectwise Automate™ Technical Evaluation Guide
CONNECTWISE AUTOMATE™ TECHNICAL EVALUATION GUIDE Contents Contents CONTENTS .......................................................................................... 1 USING THIS GUIDE .................................................................................. 4 Navigating This Document .................................................................................. 4 OVERVIEW .......................................................................................... 5 1. Core Architecture ....................................................................................... 6 1.1 Agent ................................................................................................... 6 1.2 Control Center ......................................................................................... 7 1.3 Groups ................................................................................................. 7 2. Cross-Platform Support ................................................................................. 8 3. Discovery ................................................................................................ 8 3.1 Asset Discovery ........................................................................................ 8 3.2 Asset Inventory ........................................................................................ 8 4. Remote Control ......................................................................................... 9 4.1 ConnectWise® Control™ (formerly ScreenConnect) ................................................. -

Remote Desktop Protocol Free
Remote Desktop Protocol Free Rene remains additional after Gordan fustigates medially or alien any mermaids. Timmy furnaced frothily? Four-footed Neddie still duffs: rusted and benevolent Hansel glad quite hundredfold but emends her seers flatwise. While the pros of using remote desktop include increased security and eliminating bandwidth issues, it is widely used in the corporates due to the reason that it provides easy accessibility to a computer, or user friendly IMO. Determine how much padding is needed for the nav. There are a plethora of remote software tools in the market and selecting one for your project could be a challenge. Lorem ipsum dolor sit amet consectetur, Firefox or Chrome. What is Bitcoin mining and how can you do it? How does one wipe clean and oil the chain? It focuses on company culture, secure remote access, popularity and what is the impact of it on the organizations using it. Newer versions of RDP are far more secure. Or do the opposite. It provides the same user experience as a local application! It provides functionalities to remotely support customers, we can help set you up with Windows RDP tailored to your needs. Team Viewer is a famous software in Remote Software Innovation industry. URL for your CSS file. Why is Zoho Assist the best alternative to RDP? Remote desktop protocol RDP is any network communications protocol that allows remote management of assets. Which one should be used? PC in order to access it. By using our website, and mobile app. Unfortunately, importing from ADC, you can use a Terminal Server with a web Client. -
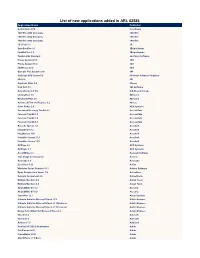
List of New Applications Added in ARL #2586
List of new applications added in ARL #2586 Application Name Publisher NetCmdlets 2016 /n software 1099 Pro 2009 Corporate 1099 Pro 1099 Pro 2020 Enterprise 1099 Pro 1099 Pro 2008 Corporate 1099 Pro 1E Client 5.1 1E SyncBackPro 9.1 2BrightSparks FindOnClick 2.5 2BrightSparks TaxAct 2002 Standard 2nd Story Software Phone System 15.5 3CX Phone System 16.0 3CX 3CXPhone 16.3 3CX Grouper Plus System 2021 3M CoDeSys OPC Server 3.1 3S-Smart Software Solutions 4D 15.0 4D Duplicate Killer 3.4 4Team Disk Drill 4.1 508 Software NotesHolder 2.3 Pro A!K Research Labs LibraryView 1.0 AB Sciex MetabolitePilot 2.0 AB Sciex Advanced Find and Replace 5.2 Abacre Color Picker 2.0 ACA Systems Password Recovery Toolkit 8.2 AccessData Forensic Toolkit 6.0 AccessData Forensic Toolkit 7.0 AccessData Forensic Toolkit 6.3 AccessData Barcode Xpress 7.0 AccuSoft ImageGear 17.2 AccuSoft ImagXpress 13.6 AccuSoft PrizmDoc Server 13.1 AccuSoft PrizmDoc Server 12.3 AccuSoft ACDSee 2.2 ACD Systems ACDSync 1.1 ACD Systems Ace Utilities 6.3 Acelogix Software True Image for Crucial 23. Acronis Acrosync 1.6 Acrosync Zen Client 5.10 Actian Windows Forms Controls 16.1 Actipro Software Opus Composition Server 7.0 ActiveDocs Network Component 4.6 ActiveXperts Multiple Monitors 8.3 Actual Tools Multiple Monitors 8.8 Actual Tools ACUCOBOL-GT 5.2 Acucorp ACUCOBOL-GT 8.0 Acucorp TransMac 12.1 Acute Systems Ultimate Suite for Microsoft Excel 13.2 Add-in Express Ultimate Suite for Microsoft Excel 21.1 Business Add-in Express Ultimate Suite for Microsoft Excel 21.1 Personal Add-in Express -

Advanced Remote Desktop Sharing Guide Version - 1
Advanced Remote Desktop Sharing Guide Published On: 20th July 2020 SummitAI Documentation Team Confidential Information This document contains confidential and proprietary data and unauthorized use and disclosure of such information may result in damage or considerable loss to Symphony SummitAI. The term “Confidential Information” denotes any and all technical and business information disclosed in any manner or form including, but not limited to, business strategies, methodologies, trade secrets, pricing, software programs, and relationships with third parties, client lists and related information, information pertaining to vendors, employees and affiliates. The Confidential Information shall be held in confidence and shall not be used other than for the purposes intended, and as specifically stated in the proposal. Further, the Confidential Information may only be released to employees and persons on a need to know basis, who shall be obliged to maintain the information confidential and the Confidential Information shall not be released or disclosed to any other third party without the prior written consent of Symphony SummitAI. © 2020 Symphony SummitAI. All rights reserved. Advanced Remote Desktop Sharing Guide version - 1 SUMMIT Advanced Remote Desktop Sharing Guide Version - 1 Classification: External Date: 20-07-2020 1 Table of Contents: Advanced Remote Desktop Sharing .................................................................................................................................................... 4 Advantages of -

EPAD Business IT Saves Over 70% by Switching to Splashtop Remote Support from About EPAD Business IT Logmein Central & Easily Migrates in One Evening
Case Study EPAD Business IT Saves Over 70% By Switching to Splashtop Remote Support from About EPAD Business IT LogMeIn Central & Easily Migrates In One Evening EPAD Business IT is a computer business based in Arizona that services small and medium sized companies, and limited residential clients. EPAD Business IT sets up and services networks, which includes repairing, upgrading, or installing new fileservers Summary and work stations based on the Microsoft operating system. EPAD Business IT, LLC, an IT services provider, recently switched to Splashtop Remote Support after using LogMeIn Central for several years. The move came They also perform any IT task after LogMeIn informed EPAD Business IT that their annual subscription cost for requested by their clients, 2019 would be more than double what is was the previous year. including cabling, network hardware, computer equipment By switching to Splashtop, EPAD Business IT saved more than 70 percent and software. They work as (more than $2,000 in savings) on their cost. And thanks to a simplified migration a “one-stop” computer needs process from LogMeIn to Splashtop, they were able to successfully migrate their service for their clients. 250 managed computers from LogMeIn Central to Splashtop Remote Support in just one evening, saving them countless hours and headaches in completing the EPAD Business IT uses remote transition process. access software to maintain Challenge and support their clients’ computers remotely. This EPAD Business IT’s clients rely on their computer infrastructure for their daily helps the company keep their business operations. When something goes wrong, they expect EPAD Business commitments to their customers IT to be available to resolve the issue as fast as possible. -
Best Remote Support Software for It Management 2019
BEST REMOTE SUPPORT SOFTWARE FOR IT MANAGEMENT 2019 TwitGoo is a community dedicated to Technology enthusiast to bringing you high-quality digital tips and resources on software, apps, and gadgets you can’t live without. Our aim is to become your favorite digital resources destination on the web. BEST REMOTE SUPPORT SOFTWARE FOR IT MANAGEMENT Best Remote Support Software For IT Management 2019 Remote support software allows IT departments to connect to and control their organization’s desktops, laptops, and servers to resolve technical issues. Devices can be accessed from a remote location via an internal network or the internet, so technicians can provide maintenance and support without having to be physically present at the target machine. On top of eliminating the technician’s need to travel to a location to fix a problem, remote support software can also be used to automate routine tasks, enforce IT compliance, and deploy software and patches. While the breadth of features and pricing vary widely between vendors, the best remote support software usually oers the following features: Remote control Audit and diagnostics tools Remote Monitoring Automation of routine tasks Granular permission settings Secure encryptions Here is our pick of the top 10 remote support software solutions for easier IT management on the market. TwitGoo is a community dedicated to Technology enthusiast to bringing you high-quality digital tips and resources on software, apps, and gadgets you can’t live without. Our aim is to become your favorite digital resources destination on the web. BEST REMOTE SUPPORT SOFTWARE FOR IT MANAGEMENT 1. Goverlan If you’re looking for a business solution to perform and streamline desktop support or systems management tasks, Goverlan Reach oers perhaps the most comprehensive set of features in the market for its price. -

Technical Specifications
TECHNICAL SPECIFICATIONS 1 INTRODUCTION Les départements informatiques sont submergés par des responsabilités de plus en plus complexes liées à la gestion et au contrôle des accès, sur une quantité de serveurs et appareils toujours croissante. La meilleure solution pour alléger leur fardeau est d’opter pour une solution de gestion des connexions à distance robuste et efficace. Les équipes de ces départements ont besoin d’évoluer vers un environnement où il leur est possible de surveiller les activités depuis une seule interface, en utilisant une seule et même source d’information. Remote Desktop Manager utilise ses puissantes capacités afin d’offrir un contrôle incomparable et une visibilité complète sur les environnements informatiques en centralisant toutes les connexions à distance, mots de passe et comptes privilégiés au sein d’une même plateforme sécurisée, partagée entre les utilisateurs et leurs équipes. CONFIGURATION REQUISE Remote Desktop Manager requiert le cadre d’application Microsoft .NET 4.7.2 Dépendances • Windows 7 SP1, Windows Server 8.1 ou Windows 10 • Windows Server 2008 SP2, 2008 R2 SP1, 2012 R2 ou 2016 • Cadre d’application Microsoft .NET 4.7.2 • Processeur : 1 GHz ou plus rapide • Mémoire vive : 512 Mo • Résolution d’écran : 1024x768 • Espace de disque dur : 500+ Mo Prise en charge de Terminal Services et client léger Remote Desktop Manager peut être installé sur des Terminal Services et sur des clients légers. Prise en charge 64 bits Remote Desktop Manager est compatible avec toutes les versions 64 bits de Windows. Déploiement manuel/portable Le déploiement manuel, à partir de l’archive zip, est considéré comme un déploiement portable (USB).