CIS Microsoft Windows 10 Enterprise (Release 1607) Benchmark
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Before the FEDERAL COMMUNICATIONS COMMISSION Washington, D.C
Before the FEDERAL COMMUNICATIONS COMMISSION Washington, D.C. 20554 In the Matter of ) ) PN Comments – Accessibility of ) CG Docket No. 10-213 Communications Technologies ) To: Consumer & Governmental Affairs Bureau COMMENTS OF MICROSOFT CORPORATION Accessibility is a business imperative for Microsoft, as both a matter of compliance and an area ripe for innovation. We are investing in design principles and natural user interfaces that help individuals of all abilities,1 and innovating in touch, gesture, and speech recognition that can be used to improve communications services available to people with disabilities. Some of our innovations were not designed exclusively for accessibility, such as the work we’ve done on the Windows touch interface, or Bing’s voice-activated search for our Windows Phone digital personal assistant Cortana. Other innovation is focused on helping people with disabilities, such as Microsoft’s partnership with the UK non-profit “Guide Dogs for the Blind” to enable better independent mobility, which we discuss below. In implementing the Twenty-First Century Communications and Video Accessibility Act of 2010 (“CVAA”), the Commission has left space for such innovation to occur by avoiding overly prescriptive regulations and setting reasonable compliance deadlines that provide industry time to research break-through solutions. For a company like Microsoft, that is already investing 1 Microsoft, Digital Inclusion and Natural User Interface Technology: A Policy Framework, http://download.microsoft.com/download/C/1/A/C1AA2411-C3AE-4D21-8C46- F33CE49BBFCF/Digital-Inclusion-Natural-User-Interface-Technology.pdf. in accessibility solutions and offers a multitude of devices, software and services to a wide range of customers around the world, that space is key for us to best use our technological know-how to deliver accessibility advancements that benefit people with disabilities. -

Text File Converted with Freeware Acropad
XP Tips & Tweaks These tips and tweaks have come from hundreds of individuals across the internet. I have included some of web sites links (below) that cover this popular topic. I have not tried most of these tips, so let me know if some don't work or have mistakes. Tips & Tweaks Links TipsDr Paul Thurrott's Supersite for Windows - XP Tips & Tricks Microsoft WinXP Support Center Microsoft WinXP Professional Microsoft WinXP Home Microsoft WinXP Knowledge Base Articles Microsoft Power Toys for Windows XP Microsoft Windows XP Tips Microsoft Windows XP User Tips Archive Microsoft Windows XP Professional Tips Microsoft Windows XP Home Edition Tips Microsoft Tips & Tricks for Windows XP Professional Microsoft Tips for Techies Stop Jerky Graphics If you are connected to a LAN and have problems with jerky graphics, this might be the solution: ·Right-click "My Computer". ·Select "Manage". ·Click on "Device Manager". ·Double-click on your NIC under "Network Adapters". ·In the new window, select the "Advanced" tab. ·Select "Connection Type" and manually set the value of your NIC. (Not "Auto Sense" which is default.). ·You should reboot. Shutdown XP Faster Like previous versions of windows, it takes long time to restart or shutdown windows XP when the "Exit Windows" sound is enabled. To solve this problem you must disable this useless sound. ·Click Start button. ·Go to settings > Control Panel > Sound, Speech and Audio devices > Sounds and Audio Devices > Sounds. ·Then under program events and windows menu click on "Exit Windows" sub-menu and highlight it. Now from sounds you can select, choose "none" and then click Apply and OK. -

The Downadup Codex a Comprehensive Guide to the Threat’S Mechanics
Security Response The Downadup Codex A comprehensive guide to the threat’s mechanics. Edition 2.0 Introduction Contents Introduction.............................................................1 Since its appearance in late-2008, the Downadup worm has become Editor’s Note............................................................5 one of the most wide-spread threats to hit the Internet for a number of Increase in exploit attempts against MS08-067.....6 years. A complex piece of malicious code, this threat was able to jump W32.Downadup infection statistics.........................8 certain network hurdles, hide in the shadows of network traffic, and New variants of W32.Downadup.B find new ways to propagate.........................................10 defend itself against attack with a deftness not often seen in today’s W32.Downadup and W32.Downadup.B threat landscape. Yet it contained few previously unseen features. What statistics................................................................12 set it apart was the sheer number of tricks it held up its sleeve. Peer-to-peer payload distribution...........................15 Geo-location, fingerprinting, and piracy...............17 It all started in late-October of 2008, we began to receive reports of A lock with no key..................................................19 Small improvements yield big returns..................21 targeted attacks taking advantage of an as-yet unknown vulnerability Attempts at smart network scanning...................23 in Window’s remote procedure call (RPC) service. Microsoft quickly Playing with Universal Plug and Play...................24 released an out-of-band security patch (MS08-067), going so far as to Locking itself out.................................................27 classify the update as “critical” for some operating systems—the high- A new Downadup variant?......................................29 Advanced crypto protection.................................30 est designation for a Microsoft Security Bulletin. -

Tokenvator Release 3 Written by Alexander Polce Leary | July 22, 2021 Tokenvator Release 3 Is a Long Overdue Update That Includes a Major Overhaul to the Tool
Tokenvator Release 3 written by Alexander Polce Leary | July 22, 2021 Tokenvator Release 3 is a long overdue update that includes a major overhaul to the tool. From the user interface, it will be mostly familiar with some command line tweaks. Under the surface, large portions of the code base have been reworked, and parts of the base have had some updates. In this series, we will go over some of the changes and new features added. Teaser Alert: Adding Privileges & Creating Tokens Improvements First and foremost, the user interface. Historically, every action had a series of positional arguments that were clunky and generally difficult to remember. They were also not very flexible, and as the commands started to have more, and additional optional arguments, they became completely unwieldy. These have been replaced with flags that will auto complete. For instance, to list and enable privileges: This also works in the non-interactive mode (though it won’t tab complete – sorry, it’s Windows): Additionally, the scroll back function was improved and numerous bugs were resolved. For instance, now when you press up you will always go to the last command issued. A printable command history has also been added if you want to copy and paste instead or keep a log of your actions. The info functionality was improved again, removing many bugs and adding additional information, such as impersonation contexts: (Tokens) > whoami [*] Operating as NT AUTHORITY\SYSTEM (Tokens) > info [*] Primary Token [+] User: S-1-5-21-258464558-1780981397-2849438727-1001 -
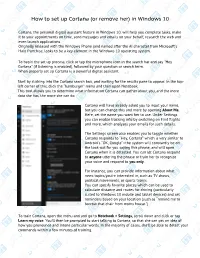
How to Set up Cortana (Or Remove Her) in Windows 10
How to set up Cortana (or remove her) in Windows 10 Cortana, the personal digital assistant feature in Windows 10, will help you complete tasks, make it to your appointments on time, send messages and emails on your behalf, research the web and even launch applications. Orignally released with the Windows Phone (and named after the AI character from Microsoft's Halo franchise, looks to be a key element in the Windows 10 operating system. To begin the set up process, click or tap the microphone icon in the search bar and say "Hey Cortana" (if listening is enabled), followed by your question or search term. When properly set up Cortana is a powerful digital assistant. Start by clicking into the Cortana search box, and waiting for the results pane to appear. In the top- left corner of this, click the “hamburger” menu and then open Notebook. This tool allows you to determine what information Cortana can gather about you, and the more data she has, the more she can do. Cortana will have already asked you to input your name, but you can change this and more by opening About Me. Here, set the name you want her to use. Under Settings you can enable tracking info by switching on Find flights and more, which analyses your emails for such details. The Settings screen also enables you to toggle whether Cortana responds to “Hey, Cortana” which is very similar to Android’s “OK, Google“–the system will constantly be on the look-out for you saying this phrase, and will open Cortana when it is detected. -

Oracle® Database Administrator's Reference
Oracle® Database Administrator's Reference 18c for Microsoft Windows E83889-01 August 2018 Oracle Database Administrator's Reference, 18c for Microsoft Windows E83889-01 Copyright © 1996, 2018, Oracle and/or its affiliates. All rights reserved. Primary Authors: Tanaya Bhattacharjee, Sunil Surabhi, Mark Bauer Contributing Authors: Lance Ashdown Contributors: Alexander Key, Sivaselvam Narayanasamy, Ricky Chen, David Collelo, David Friedman, Prakash Jashnani, Sue K. Lee, Rich Long, Satish Panchumarthy, Ravi Thammaiah, Michael Verheij This software and related documentation are provided under a license agreement containing restrictions on use and disclosure and are protected by intellectual property laws. Except as expressly permitted in your license agreement or allowed by law, you may not use, copy, reproduce, translate, broadcast, modify, license, transmit, distribute, exhibit, perform, publish, or display any part, in any form, or by any means. Reverse engineering, disassembly, or decompilation of this software, unless required by law for interoperability, is prohibited. The information contained herein is subject to change without notice and is not warranted to be error-free. If you find any errors, please report them to us in writing. If this is software or related documentation that is delivered to the U.S. Government or anyone licensing it on behalf of the U.S. Government, then the following notice is applicable: U.S. GOVERNMENT END USERS: Oracle programs, including any operating system, integrated software, any programs installed on the hardware, and/or documentation, delivered to U.S. Government end users are "commercial computer software" pursuant to the applicable Federal Acquisition Regulation and agency- specific supplemental regulations. As such, use, duplication, disclosure, modification, and adaptation of the programs, including any operating system, integrated software, any programs installed on the hardware, and/or documentation, shall be subject to license terms and license restrictions applicable to the programs. -

Security Assessment Security Policy Assessment
Security Assessment Security Policy Assessment Prepared for: Jonathan Doe Prepared by: Austin Archer 3/23/2018 CONFIDENTIALITY NOTE: The information contained in this report is for the exclusive use of the client specified above and may contain confidential, privileged and non-disclosable information. If the recipient of this report is not the client or addressee, such recipient is strictly prohibited from reading, photocopying, distributing or otherwise using this report or its contents in any way. Scan Date: 4/1/2014 Security Policy Assessment SECURITY ASSESSMENT Table of Contents 1 - Summary 1.1 - Sampled Systems 2 - Local Security Settings (Sampled Systems) 2.1 - Account Policies 2.1.1 - Password Policy 2.1.2 - Account Lockout Policy 2.2 - Local Policies 2.2.1 - Audit Policy 2.2.2 - User Rights Assignment 2.2.3 - Security Options PROPRIETARY & CONFIDENTIAL Page 2 of 14 Security Policy Assessment SECURITY ASSESSMENT 1 - Summary 1.1 - Sampled Systems IP Addresses Computer Name Operating System 10.0.7.28 tandem Windows 7 Enterprise 172.20.1.3, 10.0.1.3 DC01 Windows Server 2012 Standard PROPRIETARY & CONFIDENTIAL Page 3 of 14 Security Policy Assessment SECURITY ASSESSMENT 2 - Local Security Settings (Sampled Systems) 2.1 - Account Policies 2.1.1 - Password Policy Policy Setting Computers Enforce password history 0 passwords remembered TANDEM 24 passwords remembered DC01 Maximum password age 42 days All Sampled Minimum password age 1 days All Sampled Minimum password length 7 characters All Sampled Password must meet complexity requirements -

Run-Commands-Windows-10.Pdf
Run Commands Windows 10 by Bettertechtips.com Command Action Command Action documents Open Documents Folder devicepairingwizard Device Pairing Wizard videos Open Videos Folder msdt Diagnostics Troubleshooting Wizard downloads Open Downloads Folder tabcal Digitizer Calibration Tool favorites Open Favorites Folder dxdiag DirectX Diagnostic Tool recent Open Recent Folder cleanmgr Disk Cleanup pictures Open Pictures Folder dfrgui Optimie Drive devicepairingwizard Add a new Device diskmgmt.msc Disk Management winver About Windows dialog dpiscaling Display Setting hdwwiz Add Hardware Wizard dccw Display Color Calibration netplwiz User Accounts verifier Driver Verifier Manager azman.msc Authorization Manager utilman Ease of Access Center sdclt Backup and Restore rekeywiz Encryption File System Wizard fsquirt fsquirt eventvwr.msc Event Viewer calc Calculator fxscover Fax Cover Page Editor certmgr.msc Certificates sigverif File Signature Verification systempropertiesperformance Performance Options joy.cpl Game Controllers printui Printer User Interface iexpress IExpress Wizard charmap Character Map iexplore Internet Explorer cttune ClearType text Tuner inetcpl.cpl Internet Properties colorcpl Color Management iscsicpl iSCSI Initiator Configuration Tool cmd Command Prompt lpksetup Language Pack Installer comexp.msc Component Services gpedit.msc Local Group Policy Editor compmgmt.msc Computer Management secpol.msc Local Security Policy: displayswitch Connect to a Projector lusrmgr.msc Local Users and Groups control Control Panel magnify Magnifier -

Windows Messenger Live Msn Download
Windows messenger live msn download Windows Live Messenger latest version: See. Hear. Share. Instantly.. Windows Live Messenger previously known as MSN Messenger, was renamed as part of. MSN Messenger is an instant messaging program that lets you send instant messages to your friends, and much more. Previously known as MSN Messenger, Windows Live Messenger is Microsoft's answer to instant messaging. While largely the same as its predecessor. Windows Live Messenger free download. on their MSN or Hotmail account, as the integration with the email accounts can be. Mobile and web: Using a public computer without Messenger? No problem! You can chat on the web from Windows Live Hotmail or use. Share photos: Look at photos together, right in the conversation window and Messenger tells you when people you know post new photos on Windows Live. Microsoft Windows live messenger free Download Link: Latest Version. Old Version of MSN (Live) Messenger. Website. Developer. Microsoft Corporation. Latest Version. Windows. Messenger, which offers the user the same functionalities as Windows Live Messenger. Windows Live Messenger Final Deutsch: Der Windows Live Messenger, Nachfolger des MSN Messenger, in der Version: - vom How to Download and Install Windows Live Messenger. Windows Live Messenger is a great way to talk to people online. You can now have a personal picture. Windows 7 by default is installed without Windows Live Messenger. So to get it, we will need to download and install it. select, like setting Bing as the default search provider and setting MSN as your browser home page. is a free, personal email service from Microsoft. -

Ultimate Spider-Man™ README Last Updated: 6/28/05
Ultimate Spider-Man™ README Last Updated: 6/28/05 TABLE OF CONTENTS INTRODUCTION INSTALLATION & SET UP 1. Minimum System Requirements 2. Autoplay 3. DirectX(R) Detection & Installation VIDEO ISSUES 1. Monitors 2. In-game and Desktop Resolutions 3. Graphical Corruption When Changing Video Settings 4. Windowed Mode/Standby Mode 5. Changing Brightness and Contrast GENERAL ISSUES 1. Alt-Tab & Alt-Enter 2. Uninstalling with Antivirus Software Enabled 3. Gamepad Options 4. Invert Controls Setting 5. Options for Lower End Systems INTRODUCTION Refer to this document if you encounter difficulties with one or more aspects of installation or running the Ultimate Spider-Man™ game. Many of the most commonly encountered issues are covered here. INSTALLATION & SET UP 1. Ultimate Spider-Man™ Minimum System Requirements • 3D hardware accelerator card required - 100% DirectX(R) 9.0c-compliant 64 MB video card and drivers* • Microsoft(R) Windows(R) 2000/XP • Pentium(R) III 1.2 GHz or Athlon(TM) 1.2 GHz or higher processor • 256 MB of RAM • 3500 MB of uncompressed hard disk space (plus 400 MB for the Windows(R) swap file) • A 100% Windows(R) 2000/XP - compatible computer system including: • DirectX(R) 9.0c (Included) • 100% DirectX(R) 9.0c-compliant true 16-bit sound card and drivers • 100% Windows(R) 2000/XP - compatible mouse, keyboard and drivers • 100% Windows(R) 2000/XP - compatible quad speed CD-ROM drive (600 K/sec sustained transfer rate) and drivers *Supported Chipsets for Windows 2000/XP All NVIDIA(R) GeForce2(TM) and better chipsets All ATI(R) Radeon 7500(TM) and better chipsets *Important Note: Some 3D accelerator cards with the chipsets listed here may not be compatible with the 3D acceleration features utilized by Ultimate Spider-Man™. -

Critical Vulnerabilities Bulletin
January 18th, 2021 Critical Vulnerabilities Bulletin Confidential | Cyberint Copyright © All Rights Reserved 2020 CRITICAL VULNERABILITIES BULLETIN | INDUSTRY SECURITY BULLETIN JANUARY 14, 2021 EXECUTIVE SUMMARY Due to an unusual increase in Critical vulnerabilities found on Windows operating systems, Cyberint's Research Team has decided to release this bulletin to alert our customers of the potential impact. This bulletin will be expanded at the end of the month, as part of the Monthly Vulnerability bulletin we plan on releasing. The reason for this bulletin lies at 2 newly discovered vulnerabilities: 1. <No CVE assigned yet> - Corrupt NTFS OS partition without user interaction. 2. <No CVE assigned yet> - Trigger a BSOD by trying to access a system path. 3. CVE-2020-1398 - Potential bypass of Bitlocker protected systems, including Lock Screen bypass. We suspect that threat actors and updated malware may attempt to exploit these vulnerabilities to further impact potential victims. Confidential | Cyberint Copyright © All Rights Reserved 2020 2 CRITICAL VULNERABILITIES BULLETIN | INDUSTRY SECURITY BULLETIN JANUARY 14, 2021 NTFS CORRUPTION VULNERABILITY Published by a known vulnerability researcher, jonasLyk, it is possible to cause disk partition corruption by executing a cd command as a low privilege user, to a unique path, which causes the Windows Operating System to alert the user to a corrupted partition and force a restart. Whilst technical details are scarce, and the exact reason for the issue being unknown at this time, affected Windows builds using the NTFS file system include those from 1803 all the way to 20H2. According to SANS, the $bitmap is an attribute reserved for files marked as deleted, while $i30 is marked as an NTFS index attribute. -

Using Windows Media Player Version 12 (Windows 7) from the Media Player Help System John Lortz ([email protected]) – Discoverskills (
Using Windows Media Player Version 12 (Windows 7) From the Media Player Help System John Lortz ([email protected]) – DiscoverSkills (www.DiscoverSkills.com) You can use Windows Media Player to find and play digital media files on your computer or network, play CDs and DVDs, and stream media from the Internet. You can also rip music from audio CDs, burn CDs of your favorite music, sync media files to portable device, and find and purchase content on the Internet through online stores. Getting started with Windows Media Player Windows Media Player provides an intuitive, easy-to-use interface to play digital media files, organize your digital media collection, burn CDs of your favorite music, rip music from CDs, sync digital media files to a portable device, and shop for digital media content from online stores. Start Windows Media Player To start Windows Media Player, click the Start button , click All Programs, and then click Windows Media Player. Two ways to enjoy your media: the Player Library and Now Playing mode Windows Media Player allows you to toggle between two modes: the Player Library, which gives you comprehensive control over the Player's many features; and Now Playing mode, which gives you a simplified view of your media that's ideal for playback. From the Player Library, you can go to Now Playing mode by clicking the Switch to Now Playing button in the lower- right corner of the Player. To return to the Player Library, click the Switch to Library button in the upper-right corner of the Player. Player Library In the Player Library, you can access and organize your digital media collection.