Blockchain Elections: Smart Contract Electoral System Design and Implementation
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
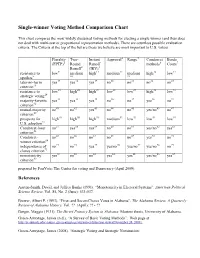
Single-Winner Voting Method Comparison Chart
Single-winner Voting Method Comparison Chart This chart compares the most widely discussed voting methods for electing a single winner (and thus does not deal with multi-seat or proportional representation methods). There are countless possible evaluation criteria. The Criteria at the top of the list are those we believe are most important to U.S. voters. Plurality Two- Instant Approval4 Range5 Condorcet Borda (FPTP)1 Round Runoff methods6 Count7 Runoff2 (IRV)3 resistance to low9 medium high11 medium12 medium high14 low15 spoilers8 10 13 later-no-harm yes17 yes18 yes19 no20 no21 no22 no23 criterion16 resistance to low25 high26 high27 low28 low29 high30 low31 strategic voting24 majority-favorite yes33 yes34 yes35 no36 no37 yes38 no39 criterion32 mutual-majority no41 no42 yes43 no44 no45 yes/no 46 no47 criterion40 prospects for high49 high50 high51 medium52 low53 low54 low55 U.S. adoption48 Condorcet-loser no57 yes58 yes59 no60 no61 yes/no 62 yes63 criterion56 Condorcet- no65 no66 no67 no68 no69 yes70 no71 winner criterion64 independence of no73 no74 yes75 yes/no 76 yes/no 77 yes/no 78 no79 clones criterion72 81 82 83 84 85 86 87 monotonicity yes no no yes yes yes/no yes criterion80 prepared by FairVote: The Center for voting and Democracy (April 2009). References Austen-Smith, David, and Jeffrey Banks (1991). “Monotonicity in Electoral Systems”. American Political Science Review, Vol. 85, No. 2 (June): 531-537. Brewer, Albert P. (1993). “First- and Secon-Choice Votes in Alabama”. The Alabama Review, A Quarterly Review of Alabama History, Vol. ?? (April): ?? - ?? Burgin, Maggie (1931). The Direct Primary System in Alabama. -

Document Country: Macedonia Lfes ID: Rol727
Date Printed: 11/06/2008 JTS Box Number: lFES 7 Tab Number: 5 Document Title: Macedonia Final Report, May 2000-March 2002 Document Date: 2002 Document Country: Macedonia lFES ID: ROl727 I I I I I I I I I IFES MISSION STATEMENT I I The purpose of IFES is to provide technical assistance in the promotion of democracy worldwide and to serve as a clearinghouse for information about I democratic development and elections. IFES is dedicated to the success of democracy throughout the world, believing that it is the preferred form of gov I ernment. At the same time, IFES firmly believes that each nation requesting assistance must take into consideration its unique social, cultural, and envi I ronmental influences. The Foundation recognizes that democracy is a dynam ic process with no single blueprint. IFES is nonpartisan, multinational, and inter I disciplinary in its approach. I I I I MAKING DEMOCRACY WORK Macedonia FINAL REPORT May 2000- March 2002 USAID COOPERATIVE AGREEMENT No. EE-A-00-97-00034-00 Submitted to the UNITED STATES AGENCY FOR INTERNATIONAL DEVELOPMENT by the INTERNATIONAL FOUNDATION FOR ELECTION SYSTEMS I I TABLE OF CONTENTS EXECUTNE SUMMARY I I. PROGRAMMATIC ACTNITIES ............................................................................................. 1 A. 2000 Pre Election Technical Assessment 1 I. Background ................................................................................. 1 I 2. Objectives ................................................................................... 1 3. Scope of Mission .........................................................................2 -

A Canadian Model of Proportional Representation by Robert S. Ring A
Proportional-first-past-the-post: A Canadian model of Proportional Representation by Robert S. Ring A thesis submitted to the School of Graduate Studies in partial fulfilment of the requirements for the degree of Master of Arts Department of Political Science Memorial University St. John’s, Newfoundland and Labrador May 2014 ii Abstract For more than a decade a majority of Canadians have consistently supported the idea of proportional representation when asked, yet all attempts at electoral reform thus far have failed. Even though a majority of Canadians support proportional representation, a majority also report they are satisfied with the current electoral system (even indicating support for both in the same survey). The author seeks to reconcile these potentially conflicting desires by designing a uniquely Canadian electoral system that keeps the positive and familiar features of first-past-the- post while creating a proportional election result. The author touches on the theory of representative democracy and its relationship with proportional representation before delving into the mechanics of electoral systems. He surveys some of the major electoral system proposals and options for Canada before finally presenting his made-in-Canada solution that he believes stands a better chance at gaining approval from Canadians than past proposals. iii Acknowledgements First of foremost, I would like to express my sincerest gratitude to my brilliant supervisor, Dr. Amanda Bittner, whose continuous guidance, support, and advice over the past few years has been invaluable. I am especially grateful to you for encouraging me to pursue my Master’s and write about my electoral system idea. -

Approval Voting Under Dichotomous Preferences: a Catalogue of Characterizations
Draft – June 25, 2021 Approval Voting under Dichotomous Preferences: A Catalogue of Characterizations Florian Brandl Dominik Peters University of Bonn Harvard University [email protected] [email protected] Approval voting allows every voter to cast a ballot of approved alternatives and chooses the alternatives with the largest number of approvals. Due to its simplicity and superior theoretical properties it is a serious contender for use in real-world elections. We support this claim by giving eight characterizations of approval voting. All our results involve the reinforcement axiom, which requires choices to be consistent across different electorates. In addition, we consider strategyproofness, consistency with majority opinions, consistency under cloning alternatives, and invariance under removing inferior alternatives. We prove our results by reducing them to a single base theorem, for which we give a simple and intuitive proof. 1 Introduction Around the world, when electing a leader or a representative, plurality is by far the most common voting system: each voter casts a vote for a single candidate, and the candidate with the most votes is elected. In pioneering work, Brams and Fishburn (1983) proposed an alternative system: approval voting. Here, each voter may cast votes for an arbitrary number of candidates, and can thus choose whether to approve or disapprove of each candidate. The election is won by the candidate who is approved by the highest number of voters. Approval voting allows voters to be more expressive of their preferences, and it can avoid problems such as vote splitting, which are endemic to plurality voting. Together with its elegance and simplicity, this has made approval voting a favorite among voting theorists (Laslier, 2011), and has led to extensive research literature (Laslier and Sanver, 2010). -

Governance in Decentralized Networks
Governance in decentralized networks Risto Karjalainen* May 21, 2020 Abstract. Effective, legitimate and transparent governance is paramount for the long-term viability of decentralized networks. If the aim is to design such a governance model, it is useful to be aware of the history of decision making paradigms and the relevant previous research. Towards such ends, this paper is a survey of different governance models, the thinking behind such models, and new tools and structures which are made possible by decentralized blockchain technology. Governance mechanisms in the wider civil society are reviewed, including structures and processes in private and non-profit governance, open-source development, and self-managed organisations. The alternative ways to aggregate preferences, resolve conflicts, and manage resources in the decentralized space are explored, including the possibility of encoding governance rules as automatically executed computer programs where humans or other entities interact via a protocol. Keywords: Blockchain technology, decentralization, decentralized autonomous organizations, distributed ledger technology, governance, peer-to-peer networks, smart contracts. 1. Introduction This paper is a survey of governance models in decentralized networks, and specifically in networks which make use of blockchain technology. There are good reasons why governance in decentralized networks is a topic of considerable interest at present. Some of these reasons are ideological. We live in an era where detailed information about private individuals is being collected and traded, in many cases without the knowledge or consent of the individuals involved. Decentralized technology is seen as a tool which can help protect people against invasions of privacy. Decentralization can also be viewed as a reaction against the overreach by state and industry. -

Automated Verification for Functional and Relational Properties of Voting
Automated Verification for Functional and Relational Properties of Voting Rules Bernhard Beckert, Thorsten Bormer, Michael Kirsten, Till Neuber, and Mattias Ulbrich Abstract In this paper, we formalise classes of axiomatic properties for voting rules, discuss their characteristics, and show how symmetry properties can be exploited in the verification of other properties. Following that, we describe how automated verification methods such as software bounded model checking and deductive verification can be used to verify implementations of voting rules. We present a case study, where we use and compare different approaches to verify that plurality voting satisfies the majority and the anonymity property. 1 Introduction Axiomatic definitions of characteristic properties for voting rules are important both for understanding existing voting rules and for designing new ones. For the trustworthiness of elections, it is also important to analyse the algorithmic descriptions of voting rules and to prove that they have the desired properties, i.e., they satisfy the declarative description. There are two classes of voting rule properties, namely (a) functional (absolute) properties, such as the majority criterion, which refer to single voting results, and (b) relational properties, such as anonymity, which are defined by comparing two (or more) results. In this paper, we first formally define these two classes of properties and discuss their characteristics (Section 2). We then show how symmetry properties { which are a particular kind of relational properties { can be exploited to more efficiently verify voting rules w.r.t. other (functional) properties (Section 3). Proving properties of voting rules by hand is tedious and error-prone { in particular, if the rules and properties evolve during design and various versions have to be verified. -

Another Consideration in Minority Vote Dilution Remedies: Rent
Another C onsideration in Minority Vote Dilution Remedies : Rent -Seeking ALAN LOCKARD St. Lawrence University In some areas of the United States, racial and ethnic minorities have been effectively excluded from the democratic process by a variety of means, including electoral laws. In some instances, the Courts have sought to remedy this problem by imposing alternative voting methods, such as cumulative voting. I examine several voting methods with regard to their sensitivity to rent-seeking. Methods which are less sensitive to rent-seeking are preferred because they involve less social waste, and are less likely to be co- opted by special interest groups. I find that proportional representation methods, rather than semi- proportional ones, such as cumulative voting, are relatively insensitive to rent-seeking efforts, and thus preferable. I also suggest that an even less sensitive method, the proportional lottery, may be appropriate for use within deliberative bodies, where proportional representation is inapplicable and minority vote dilution otherwise remains an intractable problem. 1. INTRODUCTION When President Clinton nominated Lani Guinier to serve in the Justice Department as Assistant Attorney General for Civil Rights, an opportunity was created for an extremely valuable public debate on the merits of alternative voting methods as solutions to vote dilution problems in the United States. After Prof. Guinier’s positions were grossly mischaracterized in the press,1 the President withdrew her nomination without permitting such a public debate to take place.2 These issues have been discussed in academic circles,3 however, 1 Bolick (1993) charges Guinier with advocating “a complex racial spoils system.” 2 Guinier (1998) recounts her experiences in this process. -

Voting Systems∗
Voting Systems∗ Paul E. Johnson May 27, 2005 Contents 1 Introduction 3 2 Mathematical concepts 4 2.1 Transitivity. 4 2.2 Ordinal versus Cardinal Preferences . 5 3 The Plurality Problem 7 3.1 Two Candidates? No Problem! . 7 3.2 Shortcomings of Plurality Rule With More than Two Candidates . 9 4 Rank-order voting: The Borda Count 14 4.1 The Borda Count . 15 4.2 A Paradox in the Borda Procedure . 17 4.3 Another Paradox: The Borda Winner Is A Loser? . 20 4.4 Inside the Guts of the Borda Count . 21 ∗This is a chapter prepared for educational usage by undergraduates at the University of Kansas and for eventual inclusion in a mathematics textbook that is being written with Saul Stahl of the University of Kansas Department of Mathematics. Revisions will be ongoing, so comments & corrections are especially welcome. Please contact Paul Johnson <[email protected]>. 1 4.5 Digression on the Use of Cardinal Preferences . 25 5 Sequential Pairwise Comparisons 28 5.1 A Single Elimination Tournament . 28 5.2 Dominated Winner Paradox . 30 5.3 The Intransitivity of Majority Rule . 30 6 Condorcet Methods: The Round Robin Tournament 35 6.1 Searching for an Unbeatable Set of Alternatives . 36 6.2 The Win-Loss Record . 37 6.3 Aggregated Pairwise Voting: The Borda Count Strikes Back! . 38 6.4 The Schulze Method . 43 7 Single Vote Systems: Cousins of Plurality and Majority Rule 57 8 Conclusion 63 List of Figures 1 Hypothetical Football Tournament . 29 2 Tournament Structure for the Dominated Winner Paradox . 31 3 The Smith Set . -

Democracy Lost: a Report on the Fatally Flawed 2016 Democratic Primaries
Democracy Lost: A Report on the Fatally Flawed 2016 Democratic Primaries Election Justice USA | ElectionJusticeUSA.org | [email protected] Table of Contents I. INTRODUCTORY MATERIAL........................................................................................................2 A. ABOUT ELECTION JUSTICE USA...............................................................................................2 B. EXECUTIVE SUMMARY...............................................................................................................2 C. ACKNOWLEDGEMENTS..............................................................................................................7 II. SUMMARY OF DIRECT EVIDENCE FOR ELECTION FRAUD, VOTER SUPPRESSION, AND OTHER IRREGULARITIES.......................................................................................................7 A. VOTER SUPPRESSION..................................................................................................................7 B. REGISTRATION TAMPERING......................................................................................................8 C. ILLEGAL VOTER PURGING.........................................................................................................8 D. EVIDENCE OF FRAUDULENT OR ERRONEOUS VOTING MACHINE TALLIES.................9 E. MISCELLANEOUS........................................................................................................................10 F. ESTIMATE OF PLEDGED DELEGATES AFFECTED................................................................11 -

Crowdsourcing Applications of Voting Theory Daniel Hughart
Crowdsourcing Applications of Voting Theory Daniel Hughart 5/17/2013 Most large scale marketing campaigns which involve consumer participation through voting makes use of plurality voting. In this work, it is questioned whether firms may have incentive to utilize alternative voting systems. Through an analysis of voting criteria, as well as a series of voting systems themselves, it is suggested that though there are no necessarily superior voting systems there are likely enough benefits to alternative systems to encourage their use over plurality voting. Contents Introduction .................................................................................................................................... 3 Assumptions ............................................................................................................................... 6 Voting Criteria .............................................................................................................................. 10 Condorcet ................................................................................................................................. 11 Smith ......................................................................................................................................... 14 Condorcet Loser ........................................................................................................................ 15 Majority ................................................................................................................................... -
![Arxiv:2105.00216V1 [Cs.MA] 1 May 2021](https://docslib.b-cdn.net/cover/2651/arxiv-2105-00216v1-cs-ma-1-may-2021-942651.webp)
Arxiv:2105.00216V1 [Cs.MA] 1 May 2021
Lecture Notes on Voting Theory Davide Grossi Bernoulli Institute for Maths, CS and AI University of Groningen Amsterdam Center for Law and Economics Institute for Logic, Language and Computation University of Amsterdam www.davidegrossi.me ©Davide Grossi 2021 arXiv:2105.00216v1 [cs.MA] 1 May 2021 Contents 1 Choosing One Out of Two 2 1.1 Preliminaries ................................... ........ 2 1.1.1 Keydefinitions ................................. ..... 2 1.1.2 Basicaxioms ................................... .... 3 1.2 Plurality is the best . when m =2 .............................. 5 1.2.1 Axiomatic characterizations of plurality when m =2................. 6 1.2.2 Plurality as maximum likelihood estimator when m =2 ............... 7 1.3 Chapternotes.................................... ....... 10 1.4 Exercises ....................................... ...... 10 2 Choosing One Out of Many 11 2.1 Beyondplurality ................................. ........ 11 2.1.1 Plurality selects unpopular options . ............. 11 2.1.2 Morevotingrules............................... ...... 12 2.1.3 MoreaxiomsforSCFs ............................. ..... 16 2.1.4 Impossibility results for SCFs: examples . .............. 17 2.2 There is no obvious social choice function when m> 2.................... 17 2.2.1 Socialpreferencefunctions. ........... 17 2.2.2 Arrow’stheorem ................................ ..... 18 2.3 Social choice by maximum likelihood & closest consensus .................. 21 2.3.1 The Condorcet model when m> 2........................... 21 -

2016 US Presidential Election Herrade Igersheim, François Durand, Aaron Hamlin, Jean-François Laslier
Comparing Voting Methods: 2016 US Presidential Election Herrade Igersheim, François Durand, Aaron Hamlin, Jean-François Laslier To cite this version: Herrade Igersheim, François Durand, Aaron Hamlin, Jean-François Laslier. Comparing Voting Meth- ods: 2016 US Presidential Election. 2018. halshs-01972097 HAL Id: halshs-01972097 https://halshs.archives-ouvertes.fr/halshs-01972097 Preprint submitted on 7 Jan 2019 HAL is a multi-disciplinary open access L’archive ouverte pluridisciplinaire HAL, est archive for the deposit and dissemination of sci- destinée au dépôt et à la diffusion de documents entific research documents, whether they are pub- scientifiques de niveau recherche, publiés ou non, lished or not. The documents may come from émanant des établissements d’enseignement et de teaching and research institutions in France or recherche français ou étrangers, des laboratoires abroad, or from public or private research centers. publics ou privés. WORKING PAPER N° 2018 – 55 Comparing Voting Methods: 2016 US Presidential Election Herrade Igersheim François Durand Aaron Hamlin Jean-François Laslier JEL Codes: D72, C93 Keywords : Approval voting, range voting, instant runoff, strategic voting, US Presidential election PARIS-JOURDAN SCIENCES ECONOMIQUES 48, BD JOURDAN – E.N.S. – 75014 PARIS TÉL. : 33(0) 1 80 52 16 00= www.pse.ens.fr CENTRE NATIONAL DE LA RECHERCHE SCIENTIFIQUE – ECOLE DES HAUTES ETUDES EN SCIENCES SOCIALES ÉCOLE DES PONTS PARISTECH – ECOLE NORMALE SUPÉRIEURE INSTITUT NATIONAL DE LA RECHERCHE AGRONOMIQUE – UNIVERSITE PARIS 1 Comparing Voting Methods: 2016 US Presidential Election Herrade Igersheim☦ François Durand* Aaron Hamlin✝ Jean-François Laslier§ November, 20, 2018 Abstract. Before the 2016 US presidential elections, more than 2,000 participants participated to a survey in which they were asked their opinions about the candidates, and were also asked to vote according to different alternative voting rules, in addition to plurality: approval voting, range voting, and instant runoff voting.