Cryptanalysis of Boyen's Attribute-Based Encryption Scheme
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
Disability Classification System
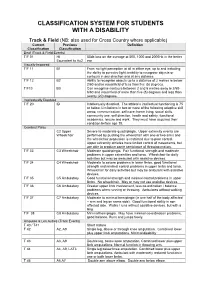
CLASSIFICATION SYSTEM FOR STUDENTS WITH A DISABILITY Track & Field (NB: also used for Cross Country where applicable) Current Previous Definition Classification Classification Deaf (Track & Field Events) T/F 01 HI 55db loss on the average at 500, 1000 and 2000Hz in the better Equivalent to Au2 ear Visually Impaired T/F 11 B1 From no light perception at all in either eye, up to and including the ability to perceive light; inability to recognise objects or contours in any direction and at any distance. T/F 12 B2 Ability to recognise objects up to a distance of 2 metres ie below 2/60 and/or visual field of less than five (5) degrees. T/F13 B3 Can recognise contours between 2 and 6 metres away ie 2/60- 6/60 and visual field of more than five (5) degrees and less than twenty (20) degrees. Intellectually Disabled T/F 20 ID Intellectually disabled. The athlete’s intellectual functioning is 75 or below. Limitations in two or more of the following adaptive skill areas; communication, self-care; home living, social skills, community use, self direction, health and safety, functional academics, leisure and work. They must have acquired their condition before age 18. Cerebral Palsy C2 Upper Severe to moderate quadriplegia. Upper extremity events are Wheelchair performed by pushing the wheelchair with one or two arms and the wheelchair propulsion is restricted due to poor control. Upper extremity athletes have limited control of movements, but are able to produce some semblance of throwing motion. T/F 33 C3 Wheelchair Moderate quadriplegia. Fair functional strength and moderate problems in upper extremities and torso. -

Ifds Functional Classification System & Procedures
IFDS FUNCTIONAL CLASSIFICATION SYSTEM & PROCEDURES MANUAL 2009 - 2012 Effective – 1 January 2009 Originally Published – March 2009 IFDS, C/o ISAF UK Ltd, Ariadne House, Town Quay, Southampton, Hampshire, SO14 2AQ, GREAT BRITAIN Tel. +44 2380 635111 Fax. +44 2380 635789 Email: [email protected] Web: www.sailing.org/disabled 1 Contents Page Introduction 5 Part A – Functional Classification System Rules for Sailors A1 General Overview and Sailor Evaluation 6 A1.1 Purpose 6 A1.2 Sailing Functions 6 A1.3 Ranking of Functional Limitations 6 A1.4 Eligibility for Competition 6 A1.5 Minimum Disability 7 A2 IFDS Class and Status 8 A2.1 Class 8 A2.2 Class Status 8 A2.3 Master List 10 A3 Classification Procedure 10 A3.0 Classification Administration Fee 10 A3.1 Personal Assistive Devices 10 A3.2 Medical Documentation 11 A3.3 Sailors’ Responsibility for Classification Evaluation 11 A3.4 Sailor Presentation for Classification Evaluation 12 A3.5 Method of Assessment 12 A3.6 Deciding the Class 14 A4 Failure to attend/Non Co-operation/Misrepresentation 16 A4.1 Sailor Failure to Attend Evaluation 16 A4.2 Non Co-operation during Evaluation 16 A4.3 International Misrepresentation of Skills and/or Abilities 17 A4.4 Consequences for Sailor Support Personnel 18 A4.5 Consequences for Teams 18 A5 Specific Rules for Boat Classes 18 A5.1 Paralympic Boat Classes 18 A5.2 Non-Paralympic Boat Classes 19 Part B – Protest and Appeals B1 Protest 20 B1.1 General Principles 20 B1.2 Class Status and Protest Opportunities 21 B1.3 Parties who may submit a Classification Protest -

A Decade of Lattice Cryptography
Full text available at: http://dx.doi.org/10.1561/0400000074 A Decade of Lattice Cryptography Chris Peikert Computer Science and Engineering University of Michigan, United States Boston — Delft Full text available at: http://dx.doi.org/10.1561/0400000074 Foundations and Trends R in Theoretical Computer Science Published, sold and distributed by: now Publishers Inc. PO Box 1024 Hanover, MA 02339 United States Tel. +1-781-985-4510 www.nowpublishers.com [email protected] Outside North America: now Publishers Inc. PO Box 179 2600 AD Delft The Netherlands Tel. +31-6-51115274 The preferred citation for this publication is C. Peikert. A Decade of Lattice Cryptography. Foundations and Trends R in Theoretical Computer Science, vol. 10, no. 4, pp. 283–424, 2014. R This Foundations and Trends issue was typeset in LATEX using a class file designed by Neal Parikh. Printed on acid-free paper. ISBN: 978-1-68083-113-9 c 2016 C. Peikert All rights reserved. No part of this publication may be reproduced, stored in a retrieval system, or transmitted in any form or by any means, mechanical, photocopying, recording or otherwise, without prior written permission of the publishers. Photocopying. In the USA: This journal is registered at the Copyright Clearance Center, Inc., 222 Rosewood Drive, Danvers, MA 01923. Authorization to photocopy items for in- ternal or personal use, or the internal or personal use of specific clients, is granted by now Publishers Inc for users registered with the Copyright Clearance Center (CCC). The ‘services’ for users can be found on the internet at: www.copyright.com For those organizations that have been granted a photocopy license, a separate system of payment has been arranged. -

Multi-Input Functional Encryption with Unbounded-Message Security
Multi-Input Functional Encryption with Unbounded-Message Security Vipul Goyal ⇤ Aayush Jain † Adam O’ Neill‡ Abstract Multi-input functional encryption (MIFE) was introduced by Goldwasser et al. (EUROCRYPT 2014) as a compelling extension of functional encryption. In MIFE, a receiver is able to compute a joint function of multiple, independently encrypted plaintexts. Goldwasser et al. (EUROCRYPT 2014) show various applications of MIFE to running SQL queries over encrypted databases, computing over encrypted data streams, etc. The previous constructions of MIFE due to Goldwasser et al. (EUROCRYPT 2014) based on in- distinguishability obfuscation had a major shortcoming: it could only support encrypting an apriori bounded number of message. Once that bound is exceeded, security is no longer guaranteed to hold. In addition, it could only support selective-security,meaningthatthechallengemessagesandthesetof “corrupted” encryption keys had to be declared by the adversary up-front. In this work, we show how to remove these restrictions by relying instead on sub-exponentially secure indistinguishability obfuscation. This is done by carefully adapting an alternative MIFE scheme of Goldwasser et al. that previously overcame these shortcomings (except for selective security wrt. the set of “corrupted” encryption keys) by relying instead on differing-inputs obfuscation, which is now seen as an implausible assumption. Our techniques are rather generic, and we hope they are useful in converting other constructions using differing-inputs obfuscation to ones using sub-exponentially secure indistinguishability obfuscation instead. ⇤Microsoft Research, India. Email: [email protected]. †UCLA, USA. Email: [email protected]. Work done while at Microsoft Research, India. ‡Georgetown University, USA. Email: [email protected]. -

Algorithms and Complexity Results for Learning and Big Data
Algorithms and Complexity Results for Learning and Big Data BY Ad´ am´ D. Lelkes B.Sc., Budapest University of Technology and Economics, 2012 M.S., University of Illinois at Chicago, 2014 THESIS Submitted as partial fulfillment of the requirements for the degree of Doctor of Philosophy in Mathematics in the Graduate College of the University of Illinois at Chicago, 2017 Chicago, Illinois Defense Committee: Gy¨orgyTur´an,Chair and Advisor Lev Reyzin, Advisor Shmuel Friedland Lisa Hellerstein, NYU Tandon School of Engineering Robert Sloan, Department of Computer Science To my parents and my grandmother / Sz¨uleimnek´esnagymam´amnak ii Acknowledgments I had a very enjoyable and productive four years at UIC, which would not have been possible without my two amazing advisors, Lev Reyzin and Gy¨orgy Tur´an. I would like to thank them for their guidance and support in every aspect of my graduate studies and research and for always being available when I had questions. Gyuri's humility, infinite patience, and meticulous attention to detail, as well as the breadth and depth of his knowledge, set an example for me to aspire to. Lev's energy and enthusiasm for research and his effectiveness at doing it always inspired me; the hours I spent in Lev's office were often the most productive hours of my week. Both Gyuri and Lev served as role models for me both as researchers and as people. Also, I would like to thank Gyuri and his wife R´ozsafor their hospitality. They invited me to their home a countless number of times, which made time in Chicago much more pleasant. -

Access Control Encryption for General Policies from Standard Assumptions
Access Control Encryption for General Policies from Standard Assumptions Sam Kim David J. Wu Stanford University Stanford University [email protected] [email protected] Abstract Functional encryption enables fine-grained access to encrypted data. In many scenarios, however, it is important to control not only what users are allowed to read (as provided by traditional functional encryption), but also what users are allowed to send. Recently, Damg˚ardet al. (TCC 2016) introduced a new cryptographic framework called access control encryption (ACE) for restricting information flow within a system in terms of both what users can read as well as what users can write. While a number of access control encryption schemes exist, they either rely on strong assumptions such as indistinguishability obfuscation or are restricted to simple families of access control policies. In this work, we give the first ACE scheme for arbitrary policies from standard assumptions. Our construction is generic and can be built from the combination of a digital signature scheme, a predicate encryption scheme, and a (single-key) functional encryption scheme that supports randomized functionalities. All of these primitives can be instantiated from standard assumptions in the plain model and therefore, we obtain the first ACE scheme capable of supporting general policies from standard assumptions. One possible instantiation of our construction relies upon standard number-theoretic assumptions (namely, the DDH and RSA assumptions) and standard lattice assumptions (namely, LWE). Finally, we conclude by introducing several extensions to the ACE framework to support dynamic and more fine-grained access control policies. 1 Introduction In the last ten years, functional encryption [BSW11, O'N10] has emerged as a powerful tool for enforcing fine-grained access to encrypted data. -

Materials and Welding
Rules for Materials and Welding Part 2 July 2021 RULES FOR MATERIALS AND WELDING JULY 2021 PART 2 American Bureau of Shipping Incorporated by Act of Legislature of the State of New York 1862 © 2021 American Bureau of Shipping. All rights reserved. ABS Plaza 1701 City Plaza Drive Spring, TX 77389 USA PART 2 Foreword (1 July 2021) For the 1996 edition, the “Rules for Building and Classing Steel Vessels – Part 2: Materials and Welding” was re-titled “Rule Requirements for Materials and Welding (Part 2).” The purpose of this generic title was to emphasize the common applicability of the material and welding requirements in “Part 2” to ABS classed vessels, other marine structures and their associated machinery, and thereby make “Part 2” more readily a common “Part” of the various ABS Rules and Guides, as appropriate. Accordingly, the subject booklet, Rules for Materials and Welding (Part 2), is to be considered, for example, as being applicable and comprising a “Part” of the following ABS Rules and Guides: ● Rules for Building and Classing Marine Vessels ● Rules for Building and Classing Steel Vessels for Service on Rivers and Intracoastal Waterways ● Rules for Building and Classing Mobile Offshore Units ● Rules for Building and Classing Steel Barges ● Rules for Building and Classing High-Speed Craft ● Rules for Building and Classing Floating Production Installations ● Rules for Building and Classing Light Warships, Patrol and High-Speed Naval Vessels ● Guide for Building and Classing Liftboats ● Guide for Building and Classing International Naval Ships ● Guide for Building and Classing Yachts In the 2002 edition, Section 4, “Piping” was added to Part 2, Chapter 4, “Welding and Fabrication”. -

Witness Encryption Instructor: Sanjam Garg Scribe: Fotis Iliopoulos
CS 276 { Cryptography Sept 8, 2014 Lecture 18: Witness Encryption Instructor: Sanjam Garg Scribe: Fotis Iliopoulos 1 A story Imagine that a billionaire who loves mathematics, would like to award with 1 million dollars the mathematician(s) who will prove the Riemann Hypothesis. Of course, neither does the billionaire know if the Riemann Hypothesis is true, nor if he will be still alive (if and) when a mathematician will come up with a proof. To overcome these couple of problems, the billionaire decides to: 1. Put 1 million dollars in gold in a big treasure chest. 2. Choose an arbitrary place of the world, dig up a hole, and hide the treasure chest. 3. Encrypt the coordinates of the treasure chest in a message so that only the mathematician(s) who can actually prove the Riemann Hypothesis can decrypt it. 4. Publish the ciphertext in every newspaper in the world. The goal of this lecture is to help the billionaire with step 3. To do so, we will assume for simplicity that the proof is at most 10000 pages long. The latter assumption implies that the language L = fx such that x is an acceptable Riemann Hypothesis proofg is in NP and therefore, using a reduction, we can come up with a circuit C that takes as input x and outputs 1 if x is a proof for the Riemann Hypothesis or 0 otherwise. Our goal now is to design a pair of PPT machines (Enc; Dec) such that: 1. Enc(C; m) takes as input the circuit C and m 2 f0; 1g and outputs a ciphertext e 2 f0; 1g∗. -

Ciphertext-Policy Attribute-Based Encryption: an Expressive, Efficient
Ciphertext-Policy Attribute-Based Encryption: An Expressive, Efficient, and Provably Secure Realization Brent Waters ∗ University of Texas at Austin [email protected] Abstract We present a new methodology for realizing Ciphertext-Policy Attribute Encryption (CP- ABE) under concrete and noninteractive cryptographic assumptions in the standard model. Our solutions allow any encryptor to specify access control in terms of any access formula over the attributes in the system. In our most efficient system, ciphertext size, encryption, and decryption time scales linearly with the complexity of the access formula. The only previous work to achieve these parameters was limited to a proof in the generic group model. We present three constructions within our framework. Our first system is proven selectively secure under a assumption that we call the decisional Parallel Bilinear Diffie-Hellman Exponent (PBDHE) assumption which can be viewed as a generalization of the BDHE assumption. Our next two constructions provide performance tradeoffs to achieve provable security respectively under the (weaker) decisional Bilinear-Diffie-Hellman Exponent and decisional Bilinear Diffie- Hellman assumptions. ∗Supported by NSF CNS-0716199, CNS-0915361, and CNS-0952692, Air Force Office of Scientific Research (AFO SR) under the MURI award for \Collaborative policies and assured information sharing" (Project PRESIDIO), Department of Homeland Security Grant 2006-CS-001-000001-02 (subaward 641), a Google Faculty Research award, and the Alfred P. Sloan Foundation. 1 Introduction Public-Key encryption is a powerful mechanism for protecting the confidentiality of stored and transmitted information. Traditionally, encryption is viewed as a method for a user to share data to a targeted user or device. -

Functional Encryption As Mediated Obfuscation
University of Montana ScholarWorks at University of Montana Graduate Student Theses, Dissertations, & Professional Papers Graduate School 2012 Functional Encryption as Mediated Obfuscation Robert Perry Hooker The University of Montana Follow this and additional works at: https://scholarworks.umt.edu/etd Let us know how access to this document benefits ou.y Recommended Citation Hooker, Robert Perry, "Functional Encryption as Mediated Obfuscation" (2012). Graduate Student Theses, Dissertations, & Professional Papers. 475. https://scholarworks.umt.edu/etd/475 This Thesis is brought to you for free and open access by the Graduate School at ScholarWorks at University of Montana. It has been accepted for inclusion in Graduate Student Theses, Dissertations, & Professional Papers by an authorized administrator of ScholarWorks at University of Montana. For more information, please contact [email protected]. FUNCTIONAL ENCRYPTION AS MEDIATED OBFUSCATION By ROBERT PERRY HOOKER Bachelor of Science, Western State College, Gunnison, Colorado, 2005 Thesis presented in partial fulfillment of the requirements for the degree of Master of Science in Computer Science The University of Montana Missoula, MT May 2012 Approved by: Dr. Sandy Ross, Dean of The Graduate School Graduate School Dr. Mike Rosulek, Chair Department of Computer Science Dr. Douglas Raiford Department of Computer Science Dr. Mark Kayll Department of Mathematical Sciences Acknowledgments This thesis would have been impossible without the advice, mentoring, and constant reassurance of my advisor, Mike Rosulek. I am continually impressed with his patience, work ethic, and equanimity. Mike is a consummate educator: always kind, never frustrated, and genuinely passionate about his work. I’m also grateful to my teachers in the UM CS department: Michael Cassens, Min Chen, Glen Granzow, Joel Henry, Jesse Johnson, Doug Raiford, Yolanda Reimer, and Alden Wright. -

Obfuscating Compute-And-Compare Programs Under LWE
58th Annual IEEE Symposium on Foundations of Computer Science Obfuscating Compute-and-Compare Programs under LWE Daniel Wichs Giorgos Zirdelis Northeastern University Northeastern University [email protected] [email protected] Abstract—We show how to obfuscate a large and expres- that the obfuscated program can be simulated given black- sive class of programs, which we call compute-and-compare box access to the program’s functionality. Unfortunately, programs, under the learning-with-errors (LWE) assumption. they showed that general purpose VBB obfuscation is un- Each such program CC[f,y] is parametrized by an arbitrary polynomial-time computable function f along with a target achievable. This leaves open two possibilities: (1) achieving value y and we define CC[f,y](x) to output 1 if f(x)=y weaker security notions of obfuscation for general programs, and 0 otherwise. In other words, the program performs an and (2) achieving virtual black box obfuscation for restricted arbitrary computation f and then compares its output against classes of programs. y a target . Our obfuscator satisfies distributional virtual-black- Along the first direction, Barak et al. proposed a weaker box security, which guarantees that the obfuscated program does not reveal any partial information about the function f security notion called indistinguishability obfuscation (iO) or the target value y, as long as they are chosen from some which guarantees that the obfuscations of two functionally distribution where y has sufficient pseudo-entropy given f. equivalent programs are indistinguishable. In a breakthrough We also extend our result to multi-bit compute-and-compare result, Garg, Gentry, Halevi, Raykova, Sahai and Waters MBCC[f,y,z](x) z programs which output a message if [GGH+13b] showed how to iO-obfuscate all polynomial- f(x)=y. -

Fully Secure and Fast Signing from Obfuscation
Fully Secure and Fast Signing from Obfuscation Kim Ramchen Brent Waters University of Texas at Austin University of Texas at Austin [email protected] [email protected] Abstract In this work we explore new techniques for building short signatures from obfuscation. Our goals are twofold. First, we would like to achieve short signatures with adaptive security proofs. Second, we would like to build signatures with fast signing, ideally significantly faster than comparable signatures that are not based on obfuscation. The goal here is to create an \imbalanced" scheme where signing is fast at the expense of slower verification. We develop new methods for achieving short and fully secure obfuscation-derived signatures. Our base signature scheme is built from punctured programming and makes a novel use of the “prefix technique" to guess a signature. We find that our initial scheme has slower performance than comparable algorithms (e.g. EC-DSA). We find that the underlying reason is that the underlying PRG is called ≈ `2 times for security parameter `. To address this issue we construct a more efficient scheme by adapting the Goldreich-Goldwasser- Micali [GGM86] construction to form the basis for a new puncturable PRF. This puncturable PRF accepts variable-length inputs and has the property that evaluations on all prefixes of a message can be efficiently pipelined. Calls to the puncturable PRF by the signing algorithm therefore make fewer invocations of the underlying PRG, resulting in reduced signing costs. We evaluate our puncturable PRF based signature schemes using a variety of cryptographic candidates for the underlying PRG. We show that the resulting performance on message signing is competitive with that of widely deployed signature schemes.