Addis Ababa University School of Graduate Studies College of Natural Sciences Department of Computer Science
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Free and Open Source Software for Electronic Health Information
Washington University Journal of Law & Policy Volume 30 Open Source and Proprietary Models of Innovation 2009 Slouching Toward Open Innovation: Free and Open Source Software for Electronic Health Information Greg R. Vetter University of Houston Law Center Follow this and additional works at: https://openscholarship.wustl.edu/law_journal_law_policy Part of the Computer Law Commons, and the Intellectual Property Law Commons Recommended Citation Greg R. Vetter, Slouching Toward Open Innovation: Free and Open Source Software for Electronic Health Information, 30 WASH. U. J. L. & POL’Y 179 (2009), https://openscholarship.wustl.edu/law_journal_law_policy/vol30/iss1/8 This Essay is brought to you for free and open access by the Law School at Washington University Open Scholarship. It has been accepted for inclusion in Washington University Journal of Law & Policy by an authorized administrator of Washington University Open Scholarship. For more information, please contact [email protected]. Slouching Toward Open Innovation: Free and Open Source Software for Electronic Health Information Greg R. Vetter INTRODUCTION Gartner, one of the most respected market research firms for information technology, recently called open source software the ―biggest disruptor the software industry has ever seen and postulated it will eventually result in cheaper software and new business models.‖1 The degree to which this prediction materializes depends on many influences, one of which is the subject of this Article. I argue that some software markets are more favorable for open source approaches than others. Using a case study of one particular software market, this Article develops a tentative framework of factors characterizing markets likely to disfavor contemporary approaches in free and open source software (―FOSS‖).2 Associate Professor of Law, University of Houston Law Center; Co-Director, Institute for Intellectual Property and Information Law; biography available at: http://www.law.uh.edu/ faculty/gvetter (last visited Mar. -

A Cloud Based Patient-Centered Ehealth Record
International Journal on Advances in Life Sciences, vol 7 no 1 & 2, year 2015, http://www.iariajournals.org/life_sciences/ 30 A Cloud Based Patient-Centered eHealth Record Konstantinos Koumaditis, Leonidas Katelaris, and Marinos Themistocleous Department of Digital Systems University of Piraeus Piraeus, Greece e-mail: (konkoum,lkatelaris,mthemist)@unipi.gr Abstract - This research focuses on the Patient-Centered integrated view of citizens health status. The latter is reflected e-Health (PCEH) concept by introducing its importance in EHRs and Personal Health Records (PHRs), which are and demonstrating a multidisciplinary project that being enriched and exploited by different actors and combines advanced technologies. The project links stakeholders (i.e., health and care professionals, citizens, several aspects of PCEH functionality, such as: (a) nutrition experts, hospitals, etc.) in the health ecosystem. homecare telemedicine technologies, (b) e-prescribing, e- Three general PHR models have been proposed [7]: a) the referral, e-learning and (c) state-of-the-art technologies stand-alone model, b) Electronic Health Record (EHR) like cloud computing and Service Oriented Architecture system, and c) the integrated one, which is an interoperable (SOA), will lead to an innovative integrated e-health system providing linkage with a variety of patient platform that delivers many benefits to the society, the information sources, such as EHRs, home diagnostics, economy, the industry and the research community. This insurance claims etc. The main types of health information paper provides insights of the PCEH concept and the supported by PHRs are problem lists, procedures, major current stages of the project. In doing so, we aim to illnesses, provider lists, allergy data, home-monitored data, increase the awareness of this significant work and family history, social history and lifestyle, immunizations, disseminate the knowledge gained so far through our medications and laboratory tests [8, 9]. -
PDF File, 212 KB
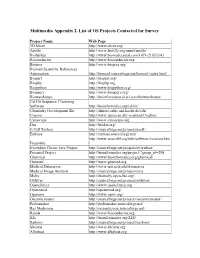
Multimedia Appendix 2. List of OS Projects Contacted for Survey Project Name Web Page 3D Slicer http://www.slicer.org/ Apollo http://www.fruitfly.org/annot/apollo/ Biobuilder http://www.biomedcentral.com/1471-2105/5/43 Bioconductor http://www.bioconductor.org Biojava http://www.biojava.org/ Biomail Scientific References Automation http://biomail.sourceforge.net/biomail/index.html Bioperl http://bioperl.org/ Biophp http://biophp.org Biopython http://www.biopython.org/ Bioquery http://www.bioquery.org/ Biowarehouse http://bioinformatics.ai.sri.com/biowarehouse/ Cd-Hit Sequence Clustering Software http://bioinformatics.org/cd-hit/ Chemistry Development Kit http://almost.cubic.uni-koeln.de/cdk/ Coasim http://www.daimi.au.dk/~mailund/CoaSim/ Cytoscape http://www.cytoscape.org Das http://biodas.org/ E-Cell System http://sourceforge.net/projects/ecell/ Emboss http://emboss.sourceforge.net/ http://www.ensembl.org/info/software/versions.htm Ensemble l Eviewbox Dicom Java Project http://sourceforge.net/projects/eviewbox/ Freemed Project http://bioinformatics.org/project/?group_id=298 Ghemical http://www.bioinformatics.org/ghemical/ Gnumed http://www.gnumed.org Medical Dataserver http://www.mii.ucla.edu/dataserver Medical Image Analysis http://sourceforge.net/projects/mia Moby http://biomoby.open-bio.org/ Olduvai http://sourceforge.net/projects/olduvai/ Openclinica http://www.openclinica.org Openemed http://openemed.org/ Openemr http://www.oemr.org/ Oscarmcmaster http://sourceforge.net/projects/oscarmcmaster/ Probemaker http://probemaker.sourceforge.net/ -

Comparison of Open-Source Electronic Health Record Systems Based on Functional and User Performance Criteria
Original Article Healthc Inform Res. 2019 April;25(2):89-98. https://doi.org/10.4258/hir.2019.25.2.89 pISSN 2093-3681 • eISSN 2093-369X Comparison of Open-Source Electronic Health Record Systems Based on Functional and User Performance Criteria Saptarshi Purkayastha1, Roshini Allam1, Pallavi Maity1, Judy W. Gichoya2 1Department of BioHealth Informatics, Indiana University–Purdue University Indianapolis, Indianapolis, IN, USA 2Dotter Institute, Oregon Health and Science University, Portland, OR, USA Objectives: Open-source Electronic Health Record (EHR) systems have gained importance. The main aim of our research is to guide organizational choice by comparing the features, functionality, and user-facing system performance of the five most popular open-source EHR systems. Methods: We performed qualitative content analysis with a directed approach on recently published literature (2012–2017) to develop an integrated set of criteria to compare the EHR systems. The functional criteria are an integration of the literature, meaningful use criteria, and the Institute of Medicine’s functional requirements of EHR, whereas the user-facing system performance is based on the time required to perform basic tasks within the EHR system. Results: Based on the Alexa web ranking and Google Trends, the five most popular EHR systems at the time of our study were OSHERA VistA, GNU Health, the Open Medical Record System (OpenMRS), Open Electronic Medical Record (OpenEMR), and OpenEHR. We also found the trends in popularity of the EHR systems and the locations where they were more popular than others. OpenEMR met all the 32 functional criteria, OSHERA VistA met 28, OpenMRS met 12 fully and 11 partially, OpenEHR-based EHR met 10 fully and 3 partially, and GNU Health met the least with only 10 criteria fully and 2 partially. -

Open Source Et Gestion De L'information Médicale : Aperçu Des Projets Existants
Open source et gestion de l'information médicale : aperçu des projets existants Ateliers CISP Club 2011 – Alexandre BRULET Open Source : bref historique... 1969 : UNIX (Bell Labs°) 1975 : distribué à des universités pour « fins éducatives » avec les codes sources... 1977 : projet BSD 1984 : projet GNU (R. Stallman) (sources partagées) 1985 : Free Software Fondation (cadre légal – licence GPL) 1989 : licence BSD modifiée (open source) 1991 : noyau GNU/Linux ? OS dérivés (NetBSD, FreeBSD, SunOS ...) 1993 : Slackware 1993 : Debian 1994 : Red Hat > 50 OS dérivés > 100 OS dérivés 1998 : MPL (ex : SUSE) > 50 OS dérivés (Knopix, Ubuntu...) (Mandriva, Fedora ...) 1999 : licence Apache UNESCO 2004 : logiciels libres patrimoine de l'humanité (…) > 35 licences libres recensées sur wikipédia (PHP, Cecil, MIT, CPL, W3C, etc.) Open source : un fonctionnement communautaire ● La « pyramide » Linux : développeurs / 'maintainers' / chefs de projet sys USB net (...) L. Torvalds / A. Morton ● Système de «patchs» : publics, signés, discutés, soumis, (approuvés) ● Versions stables régulières et archivées (mirroirs) ● Système de «paquets» permettant la cohérence des OS ● Mode de fonctionnement repris par la plupart des distributions basées sur Linux ainsi que leurs « filles » : Debian → Ubuntu, Slackware → Zenwalk, RedHat → Fedora, etc. ● Idem pour les logiciels (xfce/gnome/kde, OOo, Gimp, Firefox, etc.) Le monde open source : un immense agrégat de communautés... OS OS OS Projets GNU OS OS OS Noyau OS OS OS Noyau OS OS Projets BSD Programme open source Programme propriétaire Système OS d'exploitation Quid des logiciels médicaux ? Petit tour du monde de l'open source médical à partir d'une liste proposée par Wikipédia. 1. Logiciels médicaux francophones : MedinTux ● Petite communauté depuis 2005 (marseille), licence CeCiLL ● DMI cabinet / hôpital - objectif = ergonomie ● Programmes serveurs et clients, consultation web possible. -

Pipenightdreams Osgcal-Doc Mumudvb Mpg123-Alsa Tbb
pipenightdreams osgcal-doc mumudvb mpg123-alsa tbb-examples libgammu4-dbg gcc-4.1-doc snort-rules-default davical cutmp3 libevolution5.0-cil aspell-am python-gobject-doc openoffice.org-l10n-mn libc6-xen xserver-xorg trophy-data t38modem pioneers-console libnb-platform10-java libgtkglext1-ruby libboost-wave1.39-dev drgenius bfbtester libchromexvmcpro1 isdnutils-xtools ubuntuone-client openoffice.org2-math openoffice.org-l10n-lt lsb-cxx-ia32 kdeartwork-emoticons-kde4 wmpuzzle trafshow python-plplot lx-gdb link-monitor-applet libscm-dev liblog-agent-logger-perl libccrtp-doc libclass-throwable-perl kde-i18n-csb jack-jconv hamradio-menus coinor-libvol-doc msx-emulator bitbake nabi language-pack-gnome-zh libpaperg popularity-contest xracer-tools xfont-nexus opendrim-lmp-baseserver libvorbisfile-ruby liblinebreak-doc libgfcui-2.0-0c2a-dbg libblacs-mpi-dev dict-freedict-spa-eng blender-ogrexml aspell-da x11-apps openoffice.org-l10n-lv openoffice.org-l10n-nl pnmtopng libodbcinstq1 libhsqldb-java-doc libmono-addins-gui0.2-cil sg3-utils linux-backports-modules-alsa-2.6.31-19-generic yorick-yeti-gsl python-pymssql plasma-widget-cpuload mcpp gpsim-lcd cl-csv libhtml-clean-perl asterisk-dbg apt-dater-dbg libgnome-mag1-dev language-pack-gnome-yo python-crypto svn-autoreleasedeb sugar-terminal-activity mii-diag maria-doc libplexus-component-api-java-doc libhugs-hgl-bundled libchipcard-libgwenhywfar47-plugins libghc6-random-dev freefem3d ezmlm cakephp-scripts aspell-ar ara-byte not+sparc openoffice.org-l10n-nn linux-backports-modules-karmic-generic-pae -

Implementing an Open Source EMR in a Nursing Informatics Course
Implementing an Open Source EMR in a Nursing Informatics Course Nina Multak Emad Khazraee Michelle Rogers Prudence Dalrymple [email protected] [email protected] [email protected] [email protected] Drexel University Abstract Electronic medical record (EMR) systems are being implemented widely in hospital and office based settings. This technology is becoming a standard documentation modality for inpatient and outpatient clinical settings. While practicing clinicians have learned to use these systems with the benefit of institutional or practice based training, the educational benefit of providing EMR training to students prior to their exposure to the clinical environment has not been widely explored. This preliminary research evaluated multiple EMR systems for educational use in a nursing school curriculum. EMR training including classroom lectures, computer based training sessions and practice with interdisciplinary medical simulation are incorporated in this educational program, providing students access to an EMR system before using one with actual patients. The ADDIE model of systemic instructional design was utilized for this study. Additionally, deliberate practice, an evidence-based construct grounded in information processing and behavioral theories of skill acquisition and maintenance guided the design of this study. Preliminary results reveal a high level of learner interest and satisfaction with the training methodology. Further exploration of EMR systems and the impact this component has on nursing education and practice are planned. Keywords: education, EMR, simulation, documentation Introduction The Institute of Medicine Committee on Data Standards for Patient Safety reports evidence that improved clinical efficiencies, patient safety, and quality care outcomes can be promoted by having an effectively structured and implemented EMR1. -

The State of Open Source Electronic Health Record Projects: a Software Anthropology Study
JMIR MEDICAL INFORMATICS Alsaffar et al Original Paper The State of Open Source Electronic Health Record Projects: A Software Anthropology Study Mona Alsaffar1*, MSc; Peter Yellowlees2*, MBBS, MD; Alberto Odor3,4*, MSc, MD; Michael Hogarth5*, MD 1University of California-Davis, Department of Health Informatics, Sacramento, CA, United States 2University of California-Davis, Department of Psychiatry, Sacramento, CA, United States 3Health Informatics Graduate Group, University of California-Davis, Sacramento, CA, United States 4Betty Irene School of Nursing, University of California-Davis, Sacramento, CA, United States 5University of California-Davis, Department of Pathology, Sacramento, CA, United States *all authors contributed equally Corresponding Author: Mona Alsaffar, MSc University of California-Davis Department of Health Informatics 3700 Business Dr, Suite 130 Sacramento, CA, 95820 United States Phone: 1 9167348710 Fax: 1 (916) 734 3486 Email: [email protected] Abstract Background: Electronic health records (EHR) are a key tool in managing and storing patients' information. Currently, there are over 50 open source EHR systems available. Functionality and usability are important factors for determining the success of any system. These factors are often a direct reflection of the domain knowledge and developers' motivations. However, few published studies have focused on the characteristics of free and open source software (F/OSS) EHR systems and none to date have discussed the motivation, knowledge background, and demographic characteristics of the developers involved in open source EHR projects. Objective: This study analyzed the characteristics of prevailing F/OSS EHR systems and aimed to provide an understanding of the motivation, knowledge background, and characteristics of the developers. Methods: This study identified F/OSS EHR projects on SourceForge and other websites from May to July 2014. -

Fred Trotter
NCVHS Testimony on Meaningful Use April 28th, 2009 Today I will present this testimony to the National Committee on Vital Health and Statistics (NCVHS) Good morning. My name is Fred Trotter. Introduction I represent a community of health software developers and clinical users that respect software freedom. This community operates in the legacy of the VA VistA underground railroad. There are several important commercial EHR vendors that respect software freedom they are an important part of our community but they are only a part and certainly not a majority. While FOSS (Free and Open Source Software) vendors are critical to our community. I hope to convince you today that the notion of ‘vendors’ is too small for the task of computerizing healthcare. I hope to convince you that we need an open software community to solve this problem. I believe this because this is the only thing that has substantially worked so far and that given the magnitude of this problem, this is the only thing that has any chance of working in the future. Before we can move into that future, we need to have a candid dialog about the failure that typifies current health IT. Relevant Biography I appreciate the opportunity to testify today. More importantly I am thankful that you have chosen to invite a person from our community to speak to you. I must discuss why I am qualified to be a representative of my community. This important because legitimacy here is not earned with degrees or certifications. The FOSS community respects me because I have made substantial code and documentation contributions under FOSS licenses. -

Our Lady of Lourdes Hospital Executive Summary Student Consultant, Radford Shiozaki & Rintaro Sato Community Partner, Dr
Our Lady of Lourdes Hospital Executive Summary Student Consultant, Radford Shiozaki & Rintaro Sato Community Partner, Dr. Abundio Palencia Jr. I. About the Organization Our Lady of Lourdes Hospital (OLLH) is a private, non-profit, 50-bed tertiary hospital in Daet, Camarines Norte, Philippines. The hospital provides essential medical services to the residents of the entire Bicol region. The late Dr. Abundio Palencia Sr. founded OLLH in 1965. Today, Dr. Palencia’s sons and daughter direct a majority of the hospital’s clinical and administrative roles. Official Vision To establish the hospital as one of the very best in the entire southern Luzon area that takes care of the sick as well as the healthy person in all of his dimension. Official Mission To serve the community in all of its health related needs. Recognizing that the person is the sum of all that he is, the hospital is geared towards the care and well being of all the parts of the person -- physical, emotional, mental, and spiritual. We will work to contribute to the attainment of a happy and healthy community. II. Improving Internal Communication and Information Management by Implementing a Framework for an EMR System One of the top priorities identified by the hospital staff was to create an easy way to retrieve medical data. Currently, patient charts are paper-based and stored in a room in the back of the hospital. The room is running out of physical space to store all the charts and some of the paper charts are getting damaged from mold and insects. The paper charts are also in danger of getting damaged from floods or fires. -

Meaningful Use Interactive Charts
MEANINGFUL USE INTERACTIVE CHARTS Reference Guide for Healthcare Providers to Secure Stimulus 4010, Moorpark Avenue, #205, San Jose, California 95117 USA Tel: +1-602-842-2738 Email: [email protected] www.visolve.com MEANINGFUL USE INTERACTIVE CHARTS MEANINGFUL USE INTERACTIVE CHARTS The need for certified EMR/EHR adoption for healthcare providers has never been so important, thanks to ARRA incentives. However, the process required to get there has never been so complicated. The aggressive timelines, intense competition, complex certification process and non-adoption penalties makes the task even harder and frustrating for physicians, taking away quality time from patient care. This step-by-step reference guide aims to save time, improve informed decision making, speed up preparation and ultimately help healthcare providers understand the process to demonstrate meaningful use and secure stimulus funds as well as enhance the efficiency of their business operations. Are you eligible for ARRA incentives? Yes Eligible Professionals/Hospitals decided to obtain incentives Implementation of Yes No EHRs Comparison MU Compliance In-house EHR? Using Certified No If FY >= Obtain Certification EHRs? 2015 Yes Yes Retrieve Certification Numbers Demonstrate Meaningful Penalties EHR by submitting Quality measures Apply for EHR Medicare/Medicaid incentives Enjoy the benefit once the grant is approved!!! 4010, Moorpark Avenue, #205, San Jose, California 95117 USA Tel: +1-408602-689842-26342738 Email: [email protected] www.visolve.com APPLYING GENERAL ARRA GRANTS Ready to apply for incentives Eligible Hospitals? Professionals? Identifying the Obtain DUNS (Data Universal funding opportunity Number) by registering here number (FON) Register at Central Contractor Registration (CCR) at Register at grants.gov http://www.ccr.gov Download a grant application package 1. -

An Empirical Case Analysis on the Vendor Products with Electronic
Journal of Xi'an University of Architecture & Technology Issn No : 1006-7930 An Empirical Case Analysis on the Vendor Products with Electronic Health Records on Global Perspectives Ali Fahem Neamah Computer science and IT faculty, wasit university Iraq [email protected] Abstract The maintenance and logging in the health records is always required so that the overall predictive mining can be done on the patient records. In addition, the recording and maintenance of electronic health records is quite mandatory whereby the digital repository related to the patient is very important so that the future based predictions and the analytics can be retained. In addition to this, the patient records are providing the medical practitioners the higher degree of accuracy in the predictions and the aspects related to the knowledge discovery about that particular patient to have the effectiveness. By this way, the overall medical records can be maintained. In this research manuscript, the enormous tools and the vendors are presented usable for the electronic health records. The presented work is having the cavernous analytics on the vendor products associated with the electronic health records whereby the global perspectives and data analytics are cited. Keywords:Electronic Health Records, EHR, EMR, Electronic Medical Records Introduction Electronic Health Records (EHR) as well as Electronic Medical Records (EMR) are very important for the integration of records associated with the patients so that the overall records can be maintained about the specific set of patients [1, 2]. There are assorted suites and libraries for the electronic health and medical records thereby the medical records are logged for the future usage [3, 4, 5].