Microsoft Research Connections: an Overview
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Trident Development Framework
Trident Development Framework Tom MacAdam Jim Covill Kathleen Svendsen Martec Limited Prepared By: Martec Limited 1800 Brunswick Street, Suite 400 Halifax, Nova Scotia B3J 3J8 Canada Contractor's Document Number: TR-14-85 (Control Number: 14.28008.1110) Contract Project Manager: David Whitehouse, 902-425-5101 PWGSC Contract Number: W7707-145679/001/HAL CSA: Malcolm Smith, Warship Performance, 902-426-3100 x383 The scientific or technical validity of this Contract Report is entirely the responsibility of the Contractor and the contents do not necessarily have the approval or endorsement of the Department of National Defence of Canada. Contract Report DRDC-RDDC-2014-C328 December 2014 © Her Majesty the Queen in Right of Canada, as represented by the Minister of National Defence, 2014 © Sa Majesté la Reine (en droit du Canada), telle que représentée par le ministre de la Défense nationale, 2014 Working together for a safer world Trident Development Framework Martec Technical Report # TR-14-85 Control Number: 14.28008.1110 December 2014 Prepared for: DRDC Atlantic 9 Grove Street Dartmouth, Nova Scotia B2Y 3Z7 Martec Limited tel. 902.425.5101 1888 Brunswick Street, Suite 400 fax. 902.421.1923 Halifax, Nova Scotia B3J 3J8 Canada email. [email protected] www.martec.com REVISION CONTROL REVISION REVISION DATE Draft Release 0.1 10 Nov 2014 Draft Release 0.2 2 Dec 2014 Final Release 10 Dec 2014 PROPRIETARY NOTICE This report was prepared under Contract W7707-145679/001/HAL, Defence R&D Canada (DRDC) Atlantic and contains information proprietary to Martec Limited. The information contained herein may be used and/or further developed by DRDC Atlantic for their purposes only. -

Understanding the Attack Surface and Attack Resilience of Project Spartan’S (Edge) New Edgehtml Rendering Engine
Understanding the Attack Surface and Attack Resilience of Project Spartan’s (Edge) New EdgeHTML Rendering Engine Mark Vincent Yason IBM X-Force Advanced Research yasonm[at]ph[dot]ibm[dot]com @MarkYason [v2] © 2015 IBM Corporation Agenda . Overview . Attack Surface . Exploit Mitigations . Conclusion © 2015 IBM Corporation 2 Notes . Detailed whitepaper is available . All information is based on Microsoft Edge running on 64-bit Windows 10 build 10240 (edgehtml.dll version 11.0.10240.16384) © 2015 IBM Corporation 3 Overview © 2015 IBM Corporation Overview > EdgeHTML Rendering Engine © 2015 IBM Corporation 5 Overview > EdgeHTML Attack Surface Map & Exploit Mitigations © 2015 IBM Corporation 6 Overview > Initial Recon: MSHTML and EdgeHTML . EdgeHTML is forked from Trident (MSHTML) . Problem: Quickly identify major code changes (features/functionalities) from MSHTML to EdgeHTML . One option: Diff class names and namespaces © 2015 IBM Corporation 7 Overview > Initial Recon: Diffing MSHTML and EdgeHTML (Method) © 2015 IBM Corporation 8 Overview > Initial Recon: Diffing MSHTML and EdgeHTML (Examples) . Suggests change in image support: . Suggests new DOM object types: © 2015 IBM Corporation 9 Overview > Initial Recon: Diffing MSHTML and EdgeHTML (Examples) . Suggests ported code from another rendering engine (Blink) for Web Audio support: © 2015 IBM Corporation 10 Overview > Initial Recon: Diffing MSHTML and EdgeHTML (Notes) . Further analysis needed –Renamed class/namespace results into a new namespace plus a deleted namespace . Requires availability -

Online Visualization of Geospatial Stream Data Using the Worldwide Telescope
Online Visualization of Geospatial Stream Data using the WorldWide Telescope Mohamed Ali#, Badrish Chandramouli*, Jonathan Fay*, Curtis Wong*, Steven Drucker*, Balan Sethu Raman# #Microsoft SQL Server, One Microsoft Way, Redmond WA 98052 {mali, sethur}@microsoft.com *Microsoft Research, One Microsoft Way, Redmond WA 98052 {badrishc, jfay, curtis.wong, sdrucker}@microsoft.com ABSTRACT execution query pipeline. StreamInsight has been used in the past This demo presents the ongoing effort to meld the stream query to process geospatial data, e.g., in traffic monitoring [4, 5]. processing capabilities of Microsoft StreamInsight with the On the other hand, the WorldWide Telescope (WWT) [9] enables visualization capabilities of the WorldWide Telescope. This effort a computer to function as a virtual telescope, bringing together provides visualization opportunities to manage, analyze, and imagery from the various ground and space-based telescopes in process real-time information that is of spatio-temporal nature. the world. WWT enables a wide range of user experiences, from The demo scenario is based on detecting, tracking and predicting narrated guided tours from astronomers and educators featuring interesting patterns over historical logs and real-time feeds of interesting places in the sky, to the ability to explore the features earthquake data. of planets. One interesting feature of WWT is its use as a 3-D model of earth, enabling its use as an earth viewer. 1. INTRODUCTION Real-time stream data acquisition has been widely used in This demo presents the ongoing work at Microsoft Research and numerous applications such as network monitoring, Microsoft SQL Server groups to meld the value of stream query telecommunications data management, security, manufacturing, processing of StreamInsight with the unique visualization and sensor networks. -

Nessus 8.3 User Guide
Nessus 8.3.x User Guide Last Updated: September 24, 2021 Table of Contents Welcome to Nessus 8.3.x 12 Get Started with Nessus 15 Navigate Nessus 16 System Requirements 17 Hardware Requirements 18 Software Requirements 22 Customize SELinux Enforcing Mode Policies 25 Licensing Requirements 26 Deployment Considerations 27 Host-Based Firewalls 28 IPv6 Support 29 Virtual Machines 30 Antivirus Software 31 Security Warnings 32 Certificates and Certificate Authorities 33 Custom SSL Server Certificates 35 Create a New Server Certificate and CA Certificate 37 Upload a Custom Server Certificate and CA Certificate 39 Trust a Custom CA 41 Create SSL Client Certificates for Login 43 Nessus Manager Certificates and Nessus Agent 46 Install Nessus 48 Copyright © 2021 Tenable, Inc. All rights reserved. Tenable, Tenable.io, Tenable Network Security, Nessus, SecurityCenter, SecurityCenter Continuous View and Log Correlation Engine are registered trade- marks of Tenable,Inc. Tenable.sc, Tenable.ot, Lumin, Indegy, Assure, and The Cyber Exposure Company are trademarks of Tenable, Inc. All other products or services are trademarks of their respective Download Nessus 49 Install Nessus 51 Install Nessus on Linux 52 Install Nessus on Windows 54 Install Nessus on Mac OS X 56 Install Nessus Agents 58 Retrieve the Linking Key 59 Install a Nessus Agent on Linux 60 Install a Nessus Agent on Windows 64 Install a Nessus Agent on Mac OS X 70 Upgrade Nessus and Nessus Agents 74 Upgrade Nessus 75 Upgrade from Evaluation 76 Upgrade Nessus on Linux 77 Upgrade Nessus on Windows 78 Upgrade Nessus on Mac OS X 79 Upgrade a Nessus Agent 80 Configure Nessus 86 Install Nessus Home, Professional, or Manager 87 Link to Tenable.io 88 Link to Industrial Security 89 Link to Nessus Manager 90 Managed by Tenable.sc 92 Manage Activation Code 93 Copyright © 2021 Tenable, Inc. -

The Fourth Paradigm
ABOUT THE FOURTH PARADIGM This book presents the first broad look at the rapidly emerging field of data- THE FOUR intensive science, with the goal of influencing the worldwide scientific and com- puting research communities and inspiring the next generation of scientists. Increasingly, scientific breakthroughs will be powered by advanced computing capabilities that help researchers manipulate and explore massive datasets. The speed at which any given scientific discipline advances will depend on how well its researchers collaborate with one another, and with technologists, in areas of eScience such as databases, workflow management, visualization, and cloud- computing technologies. This collection of essays expands on the vision of pio- T neering computer scientist Jim Gray for a new, fourth paradigm of discovery based H PARADIGM on data-intensive science and offers insights into how it can be fully realized. “The impact of Jim Gray’s thinking is continuing to get people to think in a new way about how data and software are redefining what it means to do science.” —Bill GaTES “I often tell people working in eScience that they aren’t in this field because they are visionaries or super-intelligent—it’s because they care about science The and they are alive now. It is about technology changing the world, and science taking advantage of it, to do more and do better.” —RhyS FRANCIS, AUSTRALIAN eRESEARCH INFRASTRUCTURE COUNCIL F OURTH “One of the greatest challenges for 21st-century science is how we respond to this new era of data-intensive -

Facing the Future: European Research Infrastructures for the Humanities and Social Sciences
Facing the Future: European Research Infrastructures for the Humanities and Social Sciences Adrian Duşa, Dietrich Nelle, Günter Stock, and Gert G. Wagner (Eds.) Facing the Future: European Research Infrastructures for the Humanities and Social Sciences E d i t o r s : Adrian Duşa (SCI-SWG), Dietrich Nelle (BMBF), Günter Stock (ALLEA), and Gert. G. Wagner (RatSWD) ISBN 978-3-944417-03-5 1st edition © 2014 SCIVERO Verlag, Berlin SCIVERO is a trademark of GWI Verwaltungsgesellschaft für Wissenschaftspoli- tik und Infrastrukturentwicklung Berlin UG (haftungsbeschränkt). This book documents the results of the conference Facing the Future: European Research Infrastructure for Humanities and Social Sciences (November 21/22 2013, Berlin), initiated by the Social and Cultural Innovation Strategy Work- ing Group of ESFRI (SCI-SWG) and the German Federal Ministry of Education and Research (BMBF), and hosted by the European Federation of Academies of Sciences and Humanities (ALLEA) and the German Data Forum (RatSWD). Thanks and appreciation are due to all authors, speakers and participants of the conference, and all involved institutions, in particular the German Federal Ministry of Education and Research (BMBF). The ministry funded the conference and this subsequent publication as part of the Union of the German Academies of Sciences and Humanities’ project “Survey and Analysis of Basic Humanities and Social Science Research at the Science Academies Related Research Insti- tutes of Europe”. The views expressed in this publication are exclusively the opinions of the authors and not those of the German Federal Ministry of Education and Research. Editing: Dominik Adrian, Camilla Leathem, Thomas Runge, Simon Wolff Layout and graphic design: Thomas Runge Contents Preface . -

WWW 2013 22Nd International World Wide Web Conference
WWW 2013 22nd International World Wide Web Conference General Chairs: Daniel Schwabe (PUC-Rio – Brazil) Virgílio Almeida (UFMG – Brazil) Hartmut Glaser (CGI.br – Brazil) Research Track: Ricardo Baeza-Yates (Yahoo! Labs – Spain & Chile) Sue Moon (KAIST – South Korea) Practice and Experience Track: Alejandro Jaimes (Yahoo! Labs – Spain) Haixun Wang (MSR – China) Developers Track: Denny Vrandečić (Wikimedia – Germany) Marcus Fontoura (Google – USA) Demos Track: Bernadette F. Lóscio (UFPE – Brazil) Irwin King (CUHK – Hong Kong) W3C Track: Marie-Claire Forgue (W3C Training, USA) Workshops Track: Alberto Laender (UFMG – Brazil) Les Carr (U. of Southampton – UK) Posters Track: Erik Wilde (EMC – USA) Fernanda Lima (UNB – Brazil) Tutorials Track: Bebo White (SLAC – USA) Maria Luiza M. Campos (UFRJ – Brazil) Industry Track: Marden S. Neubert (UOL – Brazil) Proceedings and Metadata Chair: Altigran Soares da Silva (UFAM - Brazil) Local Arrangements Committee: Chair – Hartmut Glaser Executive Secretary – Vagner Diniz PCO Liaison – Adriana Góes, Caroline D’Avo, and Renato Costa Conference Organization Assistant – Selma Morais International Relations – Caroline Burle Technology Liaison – Reinaldo Ferraz UX Designer / Web Developer – Yasodara Córdova, Ariadne Mello Internet infrastructure - Marcelo Gardini, Felipe Agnelli Barbosa Administration– Ana Paula Conte, Maria de Lourdes Carvalho, Beatriz Iossi, Carla Christiny de Mello Legal Issues – Kelli Angelini Press Relations and Social Network – Everton T. Rodrigues, S2Publicom and EntreNós PCO – SKL Eventos -
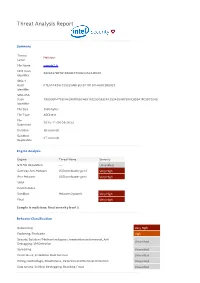
Sample2.Js Malware Summary
Threat Analysis Report Summary Threat Malicious Level File Name sample2.js MD5 Hash 580E637B97B16698CC750B445223D5C0 Identifier SHA-1 Hash 07E507426F72522DABFECF91181D7F64DC3B8D23 Identifier SHA-256 Hash 790999F47B2FA4396FF6B0A6916E295D832A12B3495A87590C859A1FE9D73245 Identifier File Size 3586 bytes File Type ASCII text File 2015-11-06 09:26:23 Submitted Duration 38 seconds Sandbox 27 seconds Replication Engine Analysis Engine Threat Name Severity GTI File Reputation --- Unverified Gateway Anti-Malware JS/Downloader.gen.f Very High Anti-Malware JS/Downloader.gen.f Very High YARA Custom Rules Sandbox Malware.Dynamic Very High Final Very High Sample is malicious: f inal severit y level 5 Behavior Classif icat ion Networking Very High Exploiting, Shellcode High Security Solution / Mechanism bypass, termination and removal, Anti Unverified Debugging, VM Detection Spreading Unverified Persistence, Installation Boot Survival Unverified Hiding, Camouflage, Stealthiness, Detection and Removal Protection Unverified Data spying, Sniffing, Keylogging, Ebanking Fraud Unverified Dynamic Analysis Action Severity Malware behavior: networking activities from non-executable file Very High ATTENTION: connection made to a malicious website (see Web/URL Very High reputation for details) Detected suspicious Java Script content High Downloaded data from a webserver Low Modified INTERNET_OPTION_CONNECT_RETRIES: number of times that Low WinInet attempts to resolve and connect to a host Connected to a specific service provider Low Cracks a URL into its component -

Extracting Insights from Differences: Analyzing Node-Aligned Social
Extracting Insights from Differences: Analyzing Node-aligned Social Graphs by Srayan Datta A dissertation submitted in partial fulfillment of the requirements for the degree of Doctor of Philosophy (Computer Science and Engineering) in The University of Michigan 2019 Doctoral Committee: Associate Professor Eytan Adar, Chair Associate Professor Mike Cafarella Assistant Professor Danai Koutra Associate Professor Clifford Lampe Srayan Datta [email protected] ORCID iD: 0000-0002-5800-830X c Srayan Datta 2019 To my family and friends ii ACKNOWLEDGEMENTS There are several people who made this dissertation possible, first among this long list is my adviser, Eytan Adar. Pursuing a doctoral program after just finishing un- dergraduate studies can be a daunting task but Eytan made it easy with his patience, kindness, and guidance. I learned a lot from our collaborations and idle conversations and I am very grateful for that. I would like to extend my thanks to the rest of my thesis committee, Mike Ca- farella, Danai Koutra and Cliff Lampe for their suggestions and constructive feed- back. I would also like to thank the following faculty members, Daniel Romero, Ceren Budak, Eric Gilbert and David Jurgens for their long insightful conversations and suggestions about some of my projects. I would like to thank all of friends and colleagues who helped (as a co-author or through critique) or supported me through this process. This is an enormous list but I am especially thankful to Chanda Phelan, Eshwar Chandrasekharan, Sam Carton, Cristina Garbacea, Shiyan Yan, Hari Subramonyam, Bikash Kanungo, and Ram Srivatasa. I would like to thank my parents for their unwavering support and faith in me. -

Denying Extremists a Powerful Tool Hany Farid ’88 Has Developed a Means to Root out Terrorist Propaganda Online
ALUMNI GAZETTE Denying Extremists a Powerful Tool Hany Farid ’88 has developed a means to root out terrorist propaganda online. But will companies like Google and Facebook use it? By David Silverberg be a “no-brainer” for social media outlets. Farid is not alone in his criticism of so- But so far, the project has faced resistance cial media companies. Last August, a pan- Hany Farid ’88 wants to clean up the In- from the leaders of Facebook, Twitter, and el in the British Parliament issued a report ternet. The chair of Dartmouth’s comput- other outlets who argue that identifying ex- charging that Facebook, Twitter, and er science department, he’s a leader in the tremist content is more difficult, presenting Google are not doing enough to prevent field of digital forensics. In the past several more gray areas, than child pornography. their networks from becoming recruitment years, he has played a lead role in creating In a February 2016 blog post, Twitter laid tools for extremist groups. programs to identify and root out two of out its official position: “As many experts Steve Burgess, president of the digital fo- the worst online scourges: child pornogra- and other companies have noted, there is rensics firm Burgess Consulting and Foren- phy and extremist political content. no ‘magic algorithm’ for identifying terror- sics, admires Farid’s dedication to projects “Digital forensics is an exciting field, es- ist content on the Internet, so global online that, according to Burgess, aren’t common pecially since you can have an impact on platforms are forced to make challenging in the field. -

Microsoft .NET Gadgeteer a New Way to Create Electronic Devices
Microsoft .NET Gadgeteer A new way to create electronic devices Nicolas Villar Microsoft Research Cambridge, UK What is .NET Gadgeteer? • .NET Gadgeteer is a new toolkit for quickly constructing, programming and shaping new small computing devices (gadgets) • Takes you from concept to working device quickly and easily Driving principle behind .NET Gadgeteer • Low threshold • Simple gadgets should be very simple to build • High ceiling • It should also be possible to build sophisticated and complex devices The three key components of .NET Gadgeteer The three key components of .NET Gadgeteer The three key components of .NET Gadgeteer Some background • We originally built Gadgeteer as a tool for ourselves (in Microsoft Research) to make it easier to prototype new kinds of devices • We believe the ability to prototype effectively is key to successful innovation Some background • Gadgeteer has proven to be of interest to other researchers – but also hobbyists and educators • With the help of colleagues from all across Microsoft, we are working on getting Gadgeteer out of the lab and into the hands of others Some background • Nicolas Villar, James Scott, Steve Hodges Microsoft Research Cambridge • Kerry Hammil Microsoft Research Redmond • Colin Miller Developer Division, Microsoft Corporation • Scarlet Schwiderski-Grosche, Stewart Tansley Microsoft Research Connections • The Garage @ Microsoft First key component of .NET Gadgeteer Quick example: Building a digital camera Some existing hardware modules Mainboard: Core processing unit Mainboard -
Network Analysis with Nodexl
Social data: Advanced Methods – Social (Media) Network Analysis with NodeXL A project from the Social Media Research Foundation: http://www.smrfoundation.org About Me Introductions Marc A. Smith Chief Social Scientist Connected Action Consulting Group [email protected] http://www.connectedaction.net http://www.codeplex.com/nodexl http://www.twitter.com/marc_smith http://delicious.com/marc_smith/Paper http://www.flickr.com/photos/marc_smith http://www.facebook.com/marc.smith.sociologist http://www.linkedin.com/in/marcasmith http://www.slideshare.net/Marc_A_Smith http://www.smrfoundation.org http://www.flickr.com/photos/library_of_congress/3295494976/sizes/o/in/photostream/ http://www.flickr.com/photos/amycgx/3119640267/ Collaboration networks are social networks SNA 101 • Node A – “actor” on which relationships act; 1-mode versus 2-mode networks • Edge B – Relationship connecting nodes; can be directional C • Cohesive Sub-Group – Well-connected group; clique; cluster A B D E • Key Metrics – Centrality (group or individual measure) D • Number of direct connections that individuals have with others in the group (usually look at incoming connections only) E • Measure at the individual node or group level – Cohesion (group measure) • Ease with which a network can connect • Aggregate measure of shortest path between each node pair at network level reflects average distance – Density (group measure) • Robustness of the network • Number of connections that exist in the group out of 100% possible – Betweenness (individual measure) F G •