MOR1 DOCID: 604773 TITLE: Scientific and Technical Intelligence Analysis AUTHOR
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Reginald Victor Jones CH FRS (1911-1997)
Catalogue of the papers and correspondence of Reginald Victor Jones CH FRS (1911-1997) by Alan Hayward NCUACS catalogue no. 95/8/00 R.V. Jones 1 NCUACS 95/8/00 Title: Catalogue of the papers and correspondence of Reginald Victor Jones CH FRS (1911-1997), physicist Compiled by: Alan Hayward Description level: Fonds Date of material: 1928-1998 Extent of material: 230 boxes, ca 5000 items Deposited in: Churchill Archives Centre, Churchill College, Cambridge CB3 0DS Reference code: GB 0014 2000 National Cataloguing Unit for the Archives of Contemporary Scientists, University of Bath. NCUACS catalogue no. 95/8/00 R.V. Jones 2 NCUACS 95/8/00 The work of the National Cataloguing Unit for the Archives of Contemporary Scientists, and the production of this catalogue, are made possible by the support of the Research Support Libraries Programme. R.V. Jones 3 NCUACS 95/8/00 NOT ALL THE MATERIAL IN THIS COLLECTION MAY YET BE AVAILABLE FOR CONSULTATION. ENQUIRIES SHOULD BE ADDRESSED IN THE FIRST INSTANCE TO: THE KEEPER OF THE ARCHIVES CHURCHILL ARCHIVES CENTRE CHURCHILL COLLEGE CAMBRIDGE R.V. Jones 4 NCUACS 95/8/00 LIST OF CONTENTS Items Page GENERAL INTRODUCTION 6 SECTION A BIOGRAPHICAL A.1 - A.302 12 SECTION B SECOND WORLD WAR B.1 - B.613 36 SECTION C UNIVERSITY OF ABERDEEN C.1 - C.282 95 SECTION D RESEARCH TOPICS AND SCIENCE INTERESTS D.1 - D.456 127 SECTION E DEFENCE AND INTELLIGENCE E.1 - E.256 180 SECTION F SCIENCE-RELATED INTERESTS F.1 - F.275 203 SECTION G VISITS AND CONFERENCES G.1 - G.448 238 SECTION H SOCIETIES AND ORGANISATIONS H.1 - H.922 284 SECTION J PUBLICATIONS J.1 - J.824 383 SECTION K LECTURES, SPEECHES AND BROADCASTS K.1 - K.495 450 SECTION L CORRESPONDENCE L.1 - L.140 495 R.V. -

The Magazine of RAF 100 Group Association
. The magazine of RAF 100 Group Association RAF 100 Group Association Chairman Roger Dobson: Tel: 01407 710384 RAF 100 Group Association Secretary Janine Bradley: Tel: 01723 512544 Email: [email protected] www.raf100groupassociation.org.uk Home to RAF 100 Group Association Memorabilia City of Norwich Aviation Museum Old Norwich Road, Horsham St Faith, Norwich, Norfolk NR10 3JF Telephone: 01603 893080 www.cnam.org.uk 2 Dearest Friends My heartfelt thanks to the kind and generous member who sent a gorgeous bouquet of flowers on one of my darkest days. Thank you so much! The card with them simply said: ‘ RAF 100 Group’ , and with the wealth of letters and cards which continue to arrive since the last magazine, I feel your love reaching across the miles. Thank you everyone for your support and encouragement during this difficult time. It has now passed the three month marker since reading that shocking email sent by Tony telling me he wasn’t coming home from London … ever ! I now know he has been leading a double life, and his relationship with another stretches back into the past. I have no idea what is truth and what is lies any more. To make it worse, they met up here in the north! There are times when I feel my heart can’t take any more … yet somehow, something happens to tell me I am still needed. My world has shrunk since I don’t have a car any more. Travel is restricted. But right here in Filey I now attend a Monday Lunch Club for my one hot meal of the week. -

Coventry: Thursday, 14 November 1940 Ebook, Epub
COVENTRY: THURSDAY, 14 NOVEMBER 1940 PDF, EPUB, EBOOK Frederick Taylor | 368 pages | 10 Jan 2017 | Bloomsbury Publishing PLC | 9781408860281 | English | London, United Kingdom Coventry: Thursday, 14 November 1940 PDF Book Coventry Cathedral was left as a ruin, and is today still the principal reminder of the bombing. Historian Dr Henry Irving, an associate fellow at the Institute of English Studies, said: "What Harrisson describes is a psychological desperation and helplessness. Spence later knighted for this work insisted that instead of re-building the old cathedral it should be kept in ruins as a garden of remembrance and that the new cathedral should be built alongside, the two buildings together effectively forming one church. Retrieved 15 October He said: "The houses on both sides of the street were burning. Accessibility help Skip to navigation Skip to content Skip to footer. They state that while Churchill was indeed aware that a major bombing raid would take place, no one knew what the target would be. Preview — Coventry by Frederick Taylor. Teaching the Bible through popular culture and the arts. Aug 08, Luke Ryan rated it really liked it. The target was Coventry, a manufacturing city in the heart of England with a beautiful medieval centre. Given the intensity of the raid, casualties were limited by the fact that a large number of Coventrians "trekked" out of the city at night to sleep in nearby towns or villages following the earlier air raids. It also provided the push America needed to join Britain in the war. Scientist Reginald Victor Jones , who led the British side in the Battle of the Beams , wrote that "Enigma signals to the X-beam stations were not broken in time" and that he was unaware that Coventry was the intended target. -
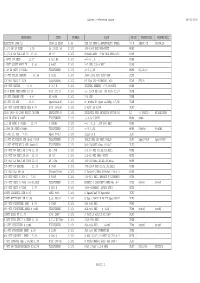
Subject Reference Dbase 09-05-2006
Subject reference dbase 09-05-2006 ONDERWERP TYPE NUMMER BIJZ GROEP TREFWOORD1 TREFWOORD2 ELECTRON 1958.12 1958.12 ELEC Z 46 TEK CX GEVR L,KWANTONETC KUBEL TS-N KERST CX LW,KW,LO 0,5/1 KW LW SEND 2.39 As 33/A1 34 Z 101 100-1000 KHZ MOB+FEST MOBS 0,7/1,4 KW SEND AS 60 10.40 AS 60 Z 101 FRUEHE AUSF 3-24 MHZ MOB+FEST MOBS 1 KWTT KW SEND 11.37 S 521 Bs Z 101 =+/-G 1,5.... MOBS 1 KWTT SHORT WAVE TR 5.36 S 486F Z 101 3-7 UND 2,5-6 MHZ MOBS 1 kW KW SEND S 521Bs TELEFUNKEN Z 172 +/-G 1,2K MOBS G1,2K+/- 10 WTT TELEF SENDER 10.34 S 318H Z 101 1500-3333 KHZ GUSS GEH SCHS 100 WTT SEND S 317H TELEFUNKEN Z 172 RS 31g 100-800METER alt SCHS S317H 100 WTT SENDER 4.33 S 317 H Z 101 UNIVERS SENDER 377-3000KHZ MOBS 15 W EINK SEND EMPF 10.35 Stat 272 B Z 101 +/- 15 W SE 469 SE 5285 F1/37 TRSE 15 WTT KARREN STN 4.40 SE 469A Z 101 3-5 MHZ TRSE 15 WTT KW STN 10.35 Spez804/445 Z 101 S= 804Bs E= Spez 445dBg 3-7,5M TRSE 150 WTT LANGW SENDE ANL 8.39 Stat 1006aF Z 101 S 427F SA 429F FLFU 1898-1938 40 JAAR RADIO IN NED SWIERSTRA R. Z 143 INLEGVEL VAN SWIERSTA PRIVE'38 LI 40 RADIO!! WILHELMINA 1kW KW SEND S 486F TELEFUNKEN Z 172 +/-2,5-7,5MHZ MOBS S486 1,5 LW SEND S 366Bs 11.37 S 366Bs Z 101 =+/- G1,5...100-600 KHZ MOBS 1,5kW LW SEND S366Bs TELEFUNKEN Z 172 +/-G 1,5L MOBS S366Bs S366BS 20 WTT FL STN 3.35 Spez 378mF Z 101 TELEF D B FLFU 20 WTT FLUGZEUG STN Spez 378nF TELEFUNKEN Z 172 URALT ANL LW FEST FREQU FLFU Spez378nF Spez378NF 20 WTT MITTELWELL GER Stat901 TELEFUNKEN Z 172 500-1500KHZ Stat 901A/F FLFU 200 WTT KW SEND AS 1008 11.39 AS 1008 Z 101 2,5-10 MHZ A1,A2,A3,HELL -

Ham Radio Magazine 1989
THE BATTLE OF THE BEAMS PART 1 By D. V. Pritchard, G4G VO, 55 Walker DL,Leigh on Beacon Dijhnen. Light Beacon after dark. Knickebein from Sea, Essex SS9 3QT, England 0600hr on 3159 Shortly afterwards, acooperative prisoner said that Knick- ebein was a beam so narrow and exact that two of them could pinpoint a target with an accuracy of less than a kilometer. He 1940...Now, nearly 50 years from those near-disastrous also added that Knickebein was in some ways similar to X- days, how many of us remember (or even know of) the debt Gergt, assuming that we were familiar with both systems! of gratitude owed to one man who confounded the radio From the wreck of another Heinkel, a diary was rushed to experts and overcame officialdom to earn Churchill's praise Jones. It read: March 5. Two-thirds of flight on leave. Afternoon as the man who "broke the bloody beams" - who went on training on Knickebein, collapsible boats, etc. to unravel the secrets of German radar and Hitler's "V By this time, the cryptographers at Bletchley Park had per- weapons," the V1 pilotless flying bomb (the 'tfoodlebug'] and formed a near miracle by breaklng the German Enigma code. the V2 rocket? One of the intercepted messagesfrom a German aircraft was sent to Jones: Knickebein, Kleve, is confirmed at position 53O24' north and lowest. This meant that the aircraft had orn in London in 1911, R. V. Jones was educated at reported receiving the beam a few miles south of Retford in St. -

Some Principles of Cyber Warfare Using Corbett to Understand War in the Early Twenty–First Century
Corbett Paper No 19 Some Principles of Cyber Warfare Using Corbett to Understand War in the Early Twenty–First Century Richard M. Crowell The Corbett Centre for Maritime Policy Studies January 2017 Some Principles of Cyber Warfare Using Corbett to Understand War in the Early Twenty–First Century Richard M. Crowell Key Points: Corbett’s theory of maritime warfare is used to illustrate how forces that move through cyberspace, content and code, have similar characteristics to forces moving through the maritime domain: fluidity of movement, omni–directional avenues of approach and the necessity to make shore (reach a human or machine destination) to be useable. • The relationship between the information environment (IE) and cyberspace as a key part of information-age war is described with a particular focus on how decision- making and control of machines takes place at the nexus of the dimensions of the IE. • The use, and rapid adaptation of, cyber force to influence human decision-making and compel machines to work independent of their owner’s intent is explored. • Cyberspace and cyber warfare are defined in ways that provide commanders, subordinates, and political leaders with a common framework. • Principles of cyber warfare are presented with examples from recent conflicts to illustrate the concepts of cyber control, cyber denial, and disputed cyber control. Dick Crowell is an associate professor in the Joint Military Operations Department at the US Naval War College. He specializes in information operations and cyberspace operations. A retired US Navy pilot, he served at sea and ashore for thirty years. He is a senior associate of the Center on Irregular Warfare and Armed Groups (CIWAG) and founding member of the Center for Cyber Conflict Studies (C3S). -

RV Jones on the Intelligence War and The
As heirs and successors to so much of our military aviation history it is fitting that the first issue of ‘Proceedings’ should be dedicated to to whom the Chairman and Committee of the Royal Air Force Historical Society tender their grateful thanks for sponsoring this inaugural issue. 1 THE PROCEEDINGS OF THE ROYAL AIR FORCE HISTORICAL SOCIETY Issue No. 1 — January 1987 Committee Members Chairman: Air Marshal Sir Frederick B Sowrey KCB CBE AFC General Secretary: Post vacant – volunteer required Membership Secretary: Group Captain H Neubroch OBE FBIM Treasurer: A S Bennell MA BLitt Programme Air Commodore J G Greenhill FBIM Sub-Committee: Air Commodore H A Probert MBE MA Group Captain A G Hicks MA CEng MIERE MRAeS T C G James CMG MA Publications Alec S C Lumsden MRAeS Sub Committee: A Richardson P G Rolfe ISO Members: Group Captain M van der Veen MA CEng MIMechE MIEE MBIM S Cox BA MA 2 CONTENTS Page 1. Editor’s Notes 4 Correspondence Membership Future meetings Questions answered Vacancy for General Secretary Book reviews 2. Introduction to inaugural lecture 8 3. The Intelligence war and the Royal Air Force 9 4. Question time 27 5. Book Review 33 6. Contact w anted 35 7. Sponsors of the Society 36 8. Acknowledgements 37 9. Committee members 38 10. Constitution 41 11. Future programmes 42 The opinions expressed in this publication are those of the authors concerned, and are not necessarily those held by the Royal Air Force Historical Society or any member of the committee. 3 EDITOR’S NOTES With the publication of this first issue of ‘Proceedings’ the Society’s first operation is completed. -

REVIEW Volume 10 Number 1 Spring 2007
Royal Air Force A I R P O W E R REVIEW Volume 10 Number 1 Spring 2007 Relearning Air-Land Co-operation Wg Cdr Harv Smyth US Weaponization of Space Wg Cdr Johnny Stringer RAF Nuclear Deterrence in the Cold War Mr Paul Graham Legal and Moral Challenges for Today’s Air Commanders Wg Cdr Andy Myers Electronic Warfare and the Night Bomber Offensive Wg Cdr Rob O’Dell RAF Historic Book Review Gp Capt Neville Parton 96 97 Photo: RAF AHB A Boeing Fortress B Mk III electronic warfare aircraft of RAF Bomber Command To What Extent Did Royal Air Force Employment of Electronic Warfare Contribute to the Outcome of the Strategic Night Bomber Offensive of World War II? By Sqn Ldr Rob O’Dell RAF The war in the air is a technological war technical operations. In particular, the which cannot be won by a technologically night bomber offensive of World War II inferior fighting force, however high its moral saw the first intensive employment of or dauntless its resolution’ Electronic Warfare (EW), precipitating a (Luftwaffe 158 victory ace, race for technical supremacy arguably Colonel Johannes Steinhoff.2) unprecedented in the history of warfare. Introduction Many contemporary studies of the Royal During World War II offensive strategic Air Force (RAF) bomber offensive have air power evolved from principles little suggested that the campaign was of changed from the German Gotha raids little relevance to the final collapse of of World War I to highly complex and Germany. Indeed, RAF ‘area bombing’ 98 99 of German cities has sometimes been The campaign is examined in 4 stages. -

Royal Air Force Historical Society Journal 41
1 ROYAL AIR FORCE HISTORICAL SOCIETY JOURNAL 41 2 The opinions expressed in this publication are those of the contributors concerned and are not necessarily those held by the Royal Air Force Historical Society. First published in the UK in 2008 by the Royal Air Force Historical Society All rights reserved. No part of this book may be reproduced or transmitted in any form or by any means, electronic or mechanical including photocopying, recording or by any information storage and retrieval system, without permission from the Publisher in writing. ISSN 1361 4231 Printed by Advance Book Printing Unit 9 Northmoor Park Church Road Northmoor OX29 5UH 3 ROYAL AIR FORCE HISTORICAL SOCIETY President Marshal of the Royal Air Force Sir Michael Beetham GCB CBE DFC AFC Vice-President Air Marshal Sir Frederick Sowrey KCB CBE AFC Committee Chairman Air Vice-Marshal N B Baldwin CB CBE FRAeS Vice-Chairman Group Captain J D Heron OBE Secretary Group Captain K J Dearman FRAeS Membership Secretary Dr Jack Dunham PhD CPsychol AMRAeS Treasurer J Boyes TD CA Members Air Commodore H A Probert MBE MA *J S Cox Esq BA MA *Dr M A Fopp MA FMA FIMgt *Group Captain N Parton BSc (Hons) MA MDA MPhil CEng FRAeS RAF *Wing Commander A J C Walters BSc MA FRAeS RAF Wing Commander C Cummings Editor & Publications Wing Commander C G Jefford MBE BA Manager *Ex Officio 4 CONTENTS EDITOR’s NOTE 6 ERRATA 6 20 October 1986. THE INTELLIGENCE WAR AND THE 7 ROYAL AIR FORCE by Professor R V Jones CB CBE FRS. -

From Axis Surprises to Allied Victories from AFIO's the INTELLIGENCER
Association of Former Intelligence Officers From AFIO's The Intelligencer 7700 Leesburg Pike, Suite 324 Journal of U.S. Intelligence Studies Falls Church, Virginia 22043 Web: www.afio.com, E-mail: [email protected] Volume 22 • Number 3 • $15 single copy price Winter 2016-17 ©2017, AFIO The Bleak Years: 1939 – Mid-1942 GUIDE TO THE STUDY OF INTELLIGENCE The Axis powers repeatedly surprised Poland, Britain, France, and others, who were often blinded by preconceptions and biases, in both a strategic and tactical sense. When war broke out on September 1, 1939, the Polish leadership, ignoring their own intelligence, lacked an appreciation of German mili- tary capabilities: their cavalry horses were no match From Axis Surprises to Allied for German Panzers. British Prime Minister Neville Chamberlain misread Hitler’s intentions, unwilling to Victories accept the evidence at hand. This was the consequence of the low priority given to British intelligence in the The Impact of Intelligence in World War II period between wars.3 Near the end of the “Phony War” (September 3, 1939 – May 10, 1940) in the West, the Germans engi- By Peter C. Oleson neered strategic, tactical, and technological surprises. The first came in Scandinavia in early April 1940. s governments declassify old files and schol- ars examine the details of World War II, it is Norway Aapparent that intelligence had an important The April 9 German invasion of Norway (and impact on many battles and the length and cost of this Denmark) was a strategic surprise for the Norwegians catastrophic conflict. As Nigel West noted, “[c]hanges and British. -
Published by the Leicestershire Archaeological and Historical Society
No 49 (2013) Published by the Leicestershire Archaeological and Historical Society LEICESTERSHIRE ARCHAEOLOGICAL AND HISTORICAL SOCIETY Founded in 1855 Join the County's Premier Archaeological and Historical Society..... .....if you have an interest in archaeology, local history, churches, historic buildings, heraldry, history or any other topic concerned with Leicestershire's past. Individual Membership costs only £20 a year and this entitles you to: • Your own copy of ‘Transactions’, the Society’s major annual reference work for Leicestershire • Your own copy of the ‘Leicestershire Historian’ with the best essays and articles from local researchers, and a major review of recent local publications • Two Newsletters every year to keep you informed about all that’s happening locally • Free access to a fine collection of resources in the Society’s Library in the Guildhall • Attend a season of fascinating talks and lectures for free • Access to visits, history fairs, guided walks and special events Family Membership for two or more family members at one address costs £25, Student Membership costs £6 Full members receive all Society publications, students members receive the two Newletters If you would like to join the Society, or require further details, please contact The Honorary Membership Secretary, Matthew Beamish, LAHS c/o ULAS, School of Archaeology & Ancient History, University of Leicester, University Road, Leicester. LE1 7RH Tel. 0116 2525234 Email [email protected] www.le.ac.uk/lahs ‘Connecting history, heritage and archaeology groups across Leicestershire and Rutland’ Editor: Joyce Lee. All contributions should be sent to the Editor, 72 Shanklin Drive, Leicester. LE2 3QA Email [email protected] Reviews Editor: Cynthia Brown, Leicestershire Archaeological and Historical Society, The Guildhall, Guildhall Lane, Leicester. -

Know the Past ...Shape the Future
FALL 2019 - Volume 66, Number 3 WWW.AFHISTORY.ORG know the past .....Shape the Future The Air Force Historical Foundation Founded on May 27, 1953 by Gen Carl A. “Tooey” Spaatz MEMBERSHIP BENEFITS and other air power pioneers, the Air Force Historical All members receive our exciting and informative Foundation (AFHF) is a nonprofi t tax exempt organization. Air Power History Journal, either electronically or It is dedicated to the preservation, perpetuation and on paper, covering: all aspects of aerospace history appropriate publication of the history and traditions of American aviation, with emphasis on the U.S. Air Force, its • Chronicles the great campaigns and predecessor organizations, and the men and women whose the great leaders lives and dreams were devoted to fl ight. The Foundation • Eyewitness accounts and historical articles serves all components of the United States Air Force— Active, Reserve and Air National Guard. • In depth resources to museums and activities, to keep members connected to the latest and AFHF strives to make available to the public and greatest events. today’s government planners and decision makers information that is relevant and informative about Preserve the legacy, stay connected: all aspects of air and space power. By doing so, the • Membership helps preserve the legacy of current Foundation hopes to assure the nation profi ts from past and future US air force personnel. experiences as it helps keep the U.S. Air Force the most modern and effective military force in the world. • Provides reliable and accurate accounts of historical events. The Foundation’s four primary activities include a quarterly journal Air Power History, a book program, a • Establish connections between generations.