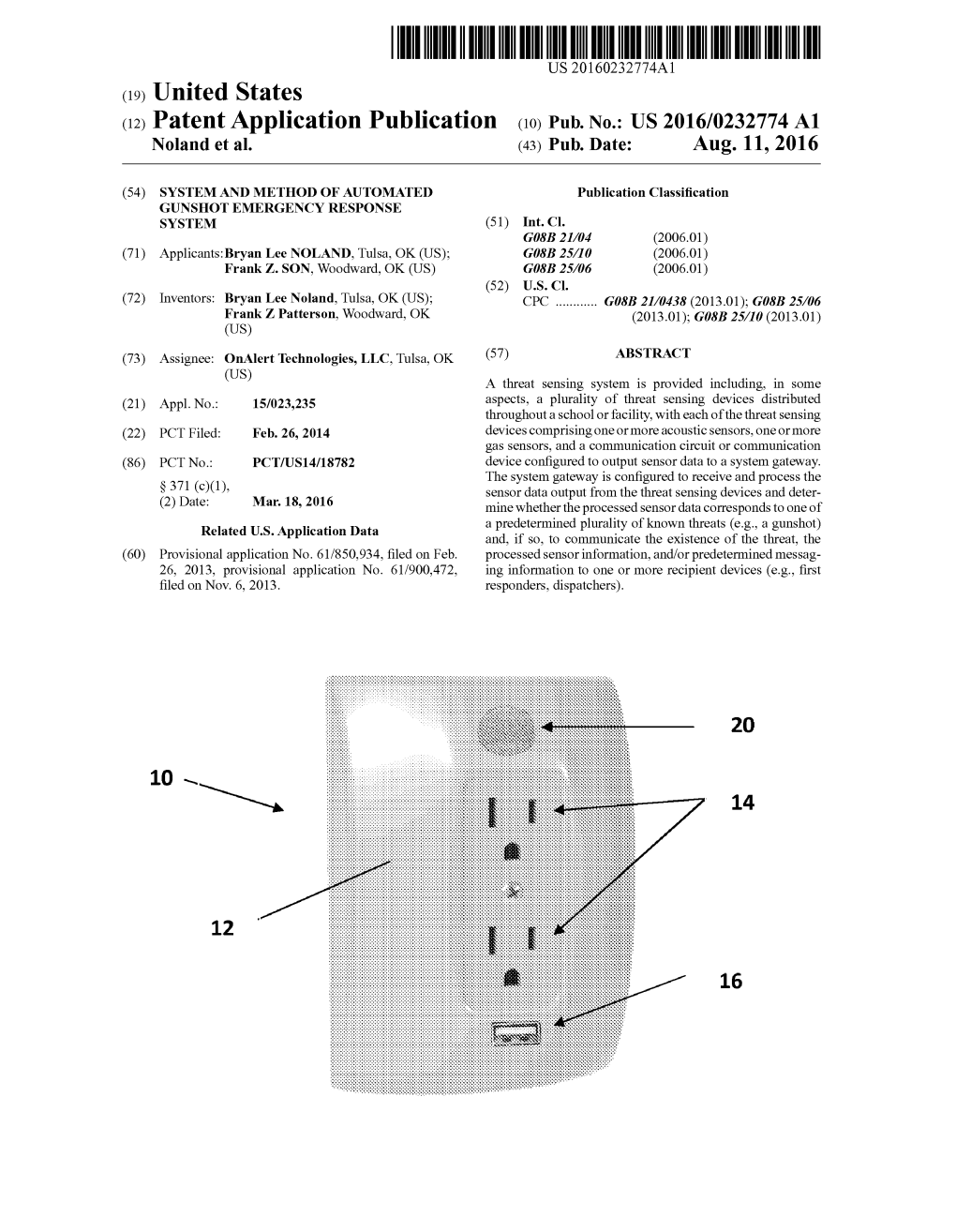
US 2016/0232774 A1 Noland Et Al
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

018-19 Southeast O.I.S. 4/30/19
ABRIDGED SUMMARY OF CATEGORICAL USE OF FORCE INCIDENT AND FINDINGS BY THE LOS ANGELES BOARD OF POLICE COMMISSIONERS OFFICER-INVOLVED SHOOTING – 018-19 Division Date Duty-On (X) Off () Uniform-Yes (X) No () Southeast 4/30/19 Officer(s) Involved in Use of Force Length of Service __ Officer C 16 years, 10 months Officer D 9 months Officer H 2 years Officer I 6 years, 11 months Officer K 10 years Officer L 10 years, 11 months Officer P 25 years, 8 months Officer O 7 years, 8 months Officer U 10 years, 1 month Reason for Police Contact Officers responded to a radio call of a “415 Man with a Gun.” The comments of the call indicated that the Subject was a male, under the influence of alcohol and possible narcotics, standing on top of a vehicle, talking to himself and waving a handgun. As the officers arrived at scene, the Subject pointed a handgun at the officers and fired several times in their direction, resulting in an Officer-Involved Shooting (OIS). The Subject then proned himself behind the open driver’s side door of the vehicle parked in his driveway. Approximately five minutes later, the Subject pointed the handgun at the officers, resulting in a second OIS. Subject(s) Deceased (X) Wounded () Non-Hit () Subject: Male, 47 years of age. Board of Police Commissioners’ Review This is a brief summary designed only to enumerate salient points regarding this Categorical Use of Force incident and does not reflect the entirety of the extensive investigation by the Los Angeles Police Department (Department) or the deliberations by the Board of Police Commissioners (BOPC). -

Firearms/Chemical Agents Version 2.5
CALIFORNIA COMMISSION ON PEACE OFFICER STANDARDS AND TRAINING Basic Course Workbook Series Student Materials Learning Domain 35 Firearms/Chemical Agents Version 2.5 THE MISSION OF THE CALIFORNIA COMMISSION ON PEACE OFFICER STANDARDS AND TRAINING IS TO CONTINUALLY ENHANCE THE PROFESSIONALISM OF CALIFORNIA LAW ENFORCEMENT IN SERVING ITS COMMUNITIES Basic Course Workbook Series Student Materials Learning Domain 35 Firearms/Chemical Agents Version 2.5 Copyright ©2005 California Commission on Peace Officer Standards and Training All rights reserved. Published 1999 Revised July 2005 Correction May 2015 This publication may not be reproduced, in whole or in part, in any form or by any means electronic or mechanical or by any information storage and retrieval system now known or hereafter invented, without prior written permission of the California Commission on Peace Officer Standards and Training, with the following exception: California law enforcement or dispatch agencies in the POST program, POST-certified training presenters, and presenters and students of the California basic course instructional system are allowed to copy this publication for non-commercial use. All other individuals, private businesses and corporations, public and private agencies and colleges, professional associations, and non-POST law enforcement agencies in-state or out-of- state may purchase copies of this publication, at cost, from POST as listed below: From POST’s Web Site: www.post.ca.gov Go to Ordering Student Workbooks POST COMMISSIONERS Sandra Hutchens – Chair -

Reloading Cartridges
A Brief Synopsis of Metallic Cartridge Reloading Principals By: C. Guenther Reloading cartridges is something that requires a solid attention to detail and a limited use of “extrapolation”, meaning we try to reduce the amount of guesswork necessary when producing safe-to-use cartridges. That said, reloading cartridges yourself lends itself to a variability which is never encountered in factory loaded ammunition and allows for some experimentation. However, in general, we try to limit experimentation where the most dangerous attribute of hand loaded ammunition is concerned, mainly pressure. Pressure within a cartridge is affected by a multitude of factors and can go from well within safety limits to massively overpressure and dangerous with a few seemingly inconsequential changes to a recipe A brief synopsis of how pressure works within a gun barrel might seem a little elementary, but it is necessary to understand in order to properly apply the load data and understand what it is doing. But in general, the attributes most associated with raising or lowering pressure are: ❖ Powder (quantity and burn rate) ❖ Primer ❖ Seating Depth (case capacity) ❖ Bullet construction ❖ Bullet bearing surface POWDER Very broadly, powder burns (it does not explode if we can help it), generates pressures (sometimes of the magnitude of up to 70,000psi), which forces a projectile into the barrel and continues generating pressure until all the powder is consumed or the bullet has left the barrel. In practice, even the slowest powders are completely consumed within the first few inches of barrel. (A fact that would be disputed by most, but is evident when studying muzzle flash, see: Hiemerl, Joseph.The Muzzle Flash of Guns and Rockets) There are only two broad powder types available to consumer reloaders: Black Powder (and it’s substitutes), and smokeless powder. -

The Effects of Physical Flash Hole Deviations on Factory-Grade Rifle Ammunition
Scholars' Mine Masters Theses Student Theses and Dissertations Spring 2015 The effects of physical flash hole deviations on factory-grade rifle ammunition Nicolaas Martin Schrier Follow this and additional works at: https://scholarsmine.mst.edu/masters_theses Part of the Explosives Engineering Commons Department: Recommended Citation Schrier, Nicolaas Martin, "The effects of physical flash hole deviations on factory-grade rifle ammunition" (2015). Masters Theses. 7416. https://scholarsmine.mst.edu/masters_theses/7416 This thesis is brought to you by Scholars' Mine, a service of the Missouri S&T Library and Learning Resources. This work is protected by U. S. Copyright Law. Unauthorized use including reproduction for redistribution requires the permission of the copyright holder. For more information, please contact [email protected]. THE EFFECTS OF PHYSICAL FLASH HOLE DEVIATIONS ON FACTORY- GRADE RIFLE AMMUNITION by NICOLAAS MARTIN SCHRIER A THESIS Presented to the Faculty of the Graduate School of the MISSOURI UNIVERSITY OF SCIENCE AND TECHNOLOGY In Partial Fulfillment of the Requirements for the Degree MASTER OF SCIENCE IN EXPLOSIVES ENGINEERING 2015 Approved by Paul Worsey, Advisor Gillian Worsey Jason Baird iii ABSTRACT The objective of this research is to determine the effect of dimensional and positional changes of the primer flash hole on the performance of factory-grade rifle ammunition. The studied variables were flash hole diameter, offset from center, and orientation of the offset in the primer pocket. Cartridge performance was quantified by measuring muzzle velocity, chamber pressure, and target grouping size (precision). Five different flash hole diameters were tested for both the Remington .223 and Winchester .308 calibers: 1.4mm, 2.0mm (the Fiocchi standard), 2.4mm, 2.8mm, and 3.0mm. -

Engineering Design Handbook Guns Series Muzzle Devices.Pdf
UNCLASSIFIED AD NUMBER AD838748 LIMITATION CHANGES TO: Approved for public release; distribution is unlimited. FROM: Distribution authorized to U.S. Gov't. agencies and their contractors; Administrative/Operational Use; MAY 1968. Other requests shall be referred to Army Materiel Command, Alexandria, VA. AUTHORITY USAMC ltr 22 Jul 1971 THIS PAGE IS UNCLASSIFIED AM Lp - AMC PAMPHLET ENGINEERING DESIGN HANDBOOK GUNS SERIES MUZZLE DEVICES 3 0 SF' lC£8 ' m® -WY SUM * ©?V BOT DKTHTIJ HEADQUARTERS, U.S. ARMY MATERIEL COMMAND MAY 1968 REDSTONE SCIENTIFIC INFORMATION CENTER nun 5 0510 00231346 5 FTEADQUARTERS UNITED STATES ARMY MATERIEL COMMAND WASHINGTON, D.C. 20315 AMC PAMPHLET 17 May 1968 No. 706-251 ENGINEERING DESIGN HANDBOOK GUNS SERIES MUZZLE DEVICES This pamphlet is published for the information and guidance of all concerned. (AMCRD-R) FOR THE COMMANDER: OFFICIAL : CLARENCE J. LANG Major General, USA Chief of Staff Chief. Administrative Office DISTRIBUTION Special AMCP 706-251 PREFACE The Engineering Design Handbook Series of the Army Materiel Command is a coordinated series of handbooks containing basic in- formation and fundamental data useful in the design and develop- ment of Army materiel and systems. The handbooks are authorita- tive reference books of practical information and quantitative facts helpful in the design and development of Army materiel so that it will meet the tactical and the technical needs of the Armed Forces. This handbook is one cf a series on Guns and presents informa- tion on the fundamental operating principles and design of muzzle devices. Because of higher priorities assigned in the past to other activities, progress in the design of bore evacuators, noise suppres- sors, and smoke suppressors was not shared with that of muzzle brakes, blast deflectors, and flash suppressors. -

Flash Suppressor Means Any Device That Reduces Or Redirects Muzzle Flash from the Shooter's Field
Department of Justice Regulations for Assault Weapons and Large Capacity Magazines FINAL STATEMENT OF REASONS Hearing Dates: February 24, 2000, Sacramento, California February 28, 2000, Los Angeles, California UPDATE OF INITIAL STATEMENT OF REASONS Section 978.10 - Title and Scope There is no information to be updated. This section was adopted as originally proposed. Section 978.20 - Definitions of Terms Used to Identify Assault Weapons Section 978.20 further defines terms used in Penal Code section 12276.1 to describe the characteristics that identify a firearm as an assault weapon. The six terms (Section 978.20 (a-f)) initially identified in this section are addressed separately relative to the revisions made to each of the original definitions proposed by the Department and subsequently noticed and modified. 978.20(a) - Detachable Magazine The proposed definition as originally noticed to the public defined a detachable magazine as “any magazine that can be readily removed without the use of tools.” During the initial public comment period (December 31, 1999 through February 28, 2000), comments were received that caused the Department to make revisions to the definition. Comments expressed concern about the use of the term “magazine,” which is often erroneously used to describe clips that are used to load ammunition into a fixed magazine. Recognizing that to be true, the Department changed the word “magazine” to the statutory term “ammunition feeding device” (PC section 12276.1(c)(1)). The Department also added the phrase “without disassembly of the firearm action” as a result of public comment stating that there are firearms with fixed magazines that can be field stripped (disassembled in the field) without using any tools (such as the M1 Garand). -

Winchester Reloading Manuals
15th Edition Reloader’s Manual What’s it take to manufacture the world’s finest ammunition? The world’s finest components. Winchester understands the demands of shooters and hunters want- ing to develop the “perfect load.” You can rest assured that every Winchester ammu- nition component is made to meet and exceed the most demanding requirements and performance standards in the world– yours. Winchester is the only manufacturer which backs up its data with over 125 years of experience in manufacturing rifle, handgun and shotshell ammunition.The data in this booklet are the culmination of very extensive testing which insures the reloader the best possible results. This 15th edition contains more than 150 new recipes, including AA Plus® Ball Powder® propellant, WAA12L wad, 9x23 Winchester and 454 Casull. This information is presented to furnish the reloader with current data for reloading shotshell and centerfire rifle and handgun ammunition. It is not a textbook on how to reload, but rather a useful reference list of recommended loads using Winchester® components. TABLE OF CONTENTS Warnings Read Before using Data. 2 Components Section. 6 Shotshell Reloading. 12 Shotshell Data. 17 Powder Bushing Information. 25 Metallic Cartridge Reloading. 33 Rifle Data. 35 Handgun Data. 42 Ballistic Terms and Definitions. 51 TRADEMARK NOTICE AA Plus, AA, Action Pistol, Fail Safe, Lubalox, Lubaloy, Silvertip, Super-Field, Super-Lite, Super-Match, Super-Target, Super-X, Xpert and Winchester are registered trademarks of Olin Corporation. Magnum Rifle, and Upland, are trademarks of Olin Corporation. Ball Powder is a registered trademark of Primex Technologies, Inc. © 1997 Winchester Group, Olin Corporation, East Alton, IL 62024 1 WARNINGS Read before using data The shotshell and metallic cartridge data in this booklet supersede all previous data published for Ball Powder® smokeless propellants. -

GUNS Magazine January 1970
JANUARY 1970 75c HUNTING • SHOOTING • ADVENTURE WIN A 1111e1t 111 tile 111et11m1 1/eltl SAVAGE 99 RIFLE (Details Inside) DREAM GUNS of 1970 world 's finest combination for the world's finest rifles. Buy Redfield. Get performance. The real beauty of a Redfield Rifle Scope is in See your dealer or gunsmith or write for free its performance. Whether it is the craftsman 32-page full-color catalog. who makes it, or the shooter who uses it, per formance is the one thing that matters. At the moment of truth, Redfield can be depended upon. There is a Redfield Rifle Scope for every shooting purpose ... big game, varmint, target, benchrest or plinking. The outstanding feature of each is that invisible, built-in extra that imparts pride, confidence, dependability and satisfaction for the marksman -and as Redfield sures the ultimate in accuracy, Redfield 5800 EAST JEW ELL AVE • DENVER. COLORADO 80222 Scopes and Mounts are acknowledged the SIGHTING EQUI PMENT NOT SUBJ ECT T O THE FEDERAL GUN CONTROL ACT OF l!iUS8 ELECTRONICS ANNOUNCES DART® THE ALL NEW COPYRIGHT 1969 DART ELECTRONICS U.S. PAT . PEND. GOLDSEYE ®SERIES NEW PROFESSIONAL METAL LOCATOR OUT PERFORMS MODEL XL ONLY Fully Transistorized Easily detects buried 1970 MODEL Comes complete, ready to use. coins, relics, gold, silver, New powerful circuit for maxi· copper and all other metals. Works mum sensitivity. Has both loud· speaker and earphone. Uses in· through dirt, sand, rock, wood, water, expensive 9 volt battery. Licht· etc. New solid state circuit assures weight: only 2 pounds. maximum performance. WITH MODEL VIEW-METER XXL New Vlew·Meter model detects objects on the fringe of debtct· able depths, NEW means more sensitivity. -

Gunshot Wounds Practical Aspects of Firearms, Ballistics, and Forensic Techniques Second Edition
Gunshot Wounds Practical Aspects of Firearms, Ballistics, and Forensic Techniques Second Edition by Vincent J. M. DiMaio, M.D. ©1999 CRC Press LLC Library of Congress Cataloging-in-Publication Data Catalog record is available from the Library of Congress. This book contains information obtained from authentic and highly regarded sources. Reprinted material is quoted with permission, and sources are indicated. A wide variety of references are listed. Reasonable efforts have been made to publish reliable data and information, but the author and the publisher cannot assume responsibility for the validity of all materials or for the consequences of their use. Neither this book nor any part may be reproduced or transmitted in any form or by any means, electronic or mechanical, including photocopying, microfilming, and recording, or by any information storage or retrieval system, without prior permission in writing from the publisher. The consent of CRC Press LLC does not extend to copying for general distribution, for promotion, for creating new works, or for resale. Specific permission must be obtained in writing from CRC Press LLC for such copying. Direct all inquiries to CRC Press LLC, 2000 Corporate Blvd., N.W., Boca Raton, Florida 33431. Trademark Notice: Product or corporate names may be trademarks or registered trademarks, and are only used for identification and explanation, without intent to infringe. © 1999 by CRC Press LLC No claim to original U.S. Government works International Standard Book Number 0-8493-8163-0 Printed in the United -
Flowchart.Recentpdf
California Rifle Identification Flowchart Violates PC § 12020 (c)(2) Short Barreled Rifle . Measured from bolt YES face to the end of the barrel or a permanently installed muzzle device. © Brought to you by: * California Legally Registered Assault Weapons can have an overall Calguns.net 2nd Amendment forum & Calguns Foundation length of 26 inches or more, other rifles are covered below (30 inches) • www.calguns.net • www.calgunsfoundation.org • NO . * Roberti -Roos Asault Weapons Control Act of 1989 The registration deadline for assault weapons listed in the Roberti-Roos ban was March 31, 1992. * Senate Bill 23 (SB-23) YES The registration deadline for assault weapons as " defined by characteristics " in SB-23 was December 31, 2000. NO The registration deadline for assault weapons as defined by Penal Code section 12276(e) " AK and AR-15 series" assault weapons was January 23, 2001. * .50 BMG Restrictions and Registration YES YES Violates PC § 12276 (e) The registration deadline for ".50 BMG rifles" was April 30, 2006. ** Check Side B for info NO NO YES Violates PC § 12276 Violates PC § 12276.1 (a)(1)(A-F) ** Check Side B for info NO YES YES NO Violates PC § 12280 Single-shot & semi-auto .50 YES BMG "shoulder-fired" rifles included. NO NO NO Violates NO Violates PC § 12276.1 (a)(3) PC § 12276.1 (a)(2) YES The rifle's overall length is measured with the stock in the YES YES collapsed/ folded position. (if equipped). NO NO Version 1.1 - Side A (02/05/2011) YES The 3 categories of an assault weapon in California Appendix A Appendix B Appendix C Roberti-Roos AW list AR Series AK Series Category 1 - are firearms listed on the original Roberti-Roos assault weapons list PC section 12276 (a), (b), and (c). -

ERDC TR-07-1, Characterization and Fate of Gun and Rocket Propellant
ERDC TR-07-1 ERDC TR-07-1 Strategic Environmental Research and Development Program Characterization and Fate of Gun and Rocket Propellant Residues on Testing and Training Ranges: Interim Report 1 Thomas F. Jenkins, Judith C. Pennington, Guy Ampleman, January 2007 Sonia Thiboutot, Michael R. Walsh, Emmanuela Diaz, Katerina M. Dontsova, Alan D. Hewitt, Marianne E. Walsh, Susan R. Bigl, Susan Taylor, Denise K. MacMillan, Jay L. Clausen, Dennis Lambert, Nancy M. Perron, Marie Claude Lapointe, Sylvie Brochu, Marc Brassard, Rob Stowe, Roccio Farinaccio, Annie Gagnon, Andre Marois, Denis Gilbert, Dominic Faucher, Sally Yost, Charlotte Hayes, Charles A. Ramsey, Richard J. Rachow, Jon E. Zufelt, Charles M. Collins, Arthur B. Gelvin, and Stephanie P. Saari Engineer Research Engineer Research Center and Development Approved for public release; distribution is unlimited. Strategic Environmental Research and ERDC TR-07-1 Development Program January 2007 Characterization and Fate of Gun and Rocket Propellant Residues on Testing and Training Ranges: Interim Report 1 Thomas F. Jenkins, Michael R. Walsh, Alan D. Hewitt, Marianne E. Walsh, Susan R. Bigl, Susan Taylor, Jay L. Clausen, Dennis Lambert, Nancy M. Perron, Richard J. Rachow, Jon E. Zufelt, Charles M. Collins, Arthur B. Gelvin, and Stephanie P. Saari Cold Regions Research and Engineering Laboratory U.S. Army Engineer Research and Development Center 72 Lyme Road Hanover, NH 03755-1290 Judith C. Pennington, Katerina M Dontsova, Sally Yost, Charlotte Hayes, and Denise K. MacMillan Environmental Laboratory U.S. Army Engineer Research and Development Center 3909 Halls Ferry Road Vicksburg, MS 39180-6199 Guy Ampleman, Sonia Thiboutot, Emmanuela Diaz, Marie Claude Lapointe, Sylvie Brochu, Marc Brassard, Rob Stowe, Roccio Farinaccio, Annie Gagnon, Andre Marois, Denis Gilbert, and Dominic Faucher Defence R&D Canada–Valcartier 2459 Pie-XI Blvd North Québec, Quebec G3J 1X5 CANADA Charles A. -

Firearms, Ammunition and Related Terminology Within the Disciplines Of
Firearms, ammunition and related terminology Within the disciplines of firearms training, and the interdependent subject of ammunition and the related, there exists a myriad of terms, phrases, and “buzz words” that have been persistent for decades. Many of these are commonly misused, as in they are generalizations or “slang”, and are not specific enough for accurate use or don’t technically represent what they should. In addition to this, many terms, phrases or “buzz words” have overlapping usage. They may be generally applicable in a variety of circumstances, but only employed with complete accuracy in a small number of specific instances. The reasoning behind this article is to dispel some myths and take an indigenously confusing topic, which has propagated much consternation over the years, and simplify or streamline it into an easily understandable format. It would be virtually impossible to list every word or short subject matter in an article of this scope. What I have attempted to do is assemble the most common areas of difficulty and focus on them alone. This snapshot highlights the ones I feel essentially important to us as trainers. ACP: the letters stand for Automatic Colt Pistol. Adjustable sights: Refers to sights that are moveable in incremental adjustments to change projectile impact on the target. They can be adjustable for windage (horizontal impact) or elevation (vertical impact). Alibi: allowing a shooter to make up for lost or non-discharged rounds due to problems with the functioning of a weapon. Assault rifle: the meaning of this term has changed over the years and is much a matter of perception.