Voting Systems for Social Choice ∗
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Simulating Quantum Field Theory with a Quantum Computer
Simulating quantum field theory with a quantum computer John Preskill Lattice 2018 28 July 2018 This talk has two parts (1) Near-term prospects for quantum computing. (2) Opportunities in quantum simulation of quantum field theory. Exascale digital computers will advance our knowledge of QCD, but some challenges will remain, especially concerning real-time evolution and properties of nuclear matter and quark-gluon plasma at nonzero temperature and chemical potential. Digital computers may never be able to address these (and other) problems; quantum computers will solve them eventually, though I’m not sure when. The physics payoff may still be far away, but today’s research can hasten the arrival of a new era in which quantum simulation fuels progress in fundamental physics. Frontiers of Physics short distance long distance complexity Higgs boson Large scale structure “More is different” Neutrino masses Cosmic microwave Many-body entanglement background Supersymmetry Phases of quantum Dark matter matter Quantum gravity Dark energy Quantum computing String theory Gravitational waves Quantum spacetime particle collision molecular chemistry entangled electrons A quantum computer can simulate efficiently any physical process that occurs in Nature. (Maybe. We don’t actually know for sure.) superconductor black hole early universe Two fundamental ideas (1) Quantum complexity Why we think quantum computing is powerful. (2) Quantum error correction Why we think quantum computing is scalable. A complete description of a typical quantum state of just 300 qubits requires more bits than the number of atoms in the visible universe. Why we think quantum computing is powerful We know examples of problems that can be solved efficiently by a quantum computer, where we believe the problems are hard for classical computers. -

Geometric Algorithms
Geometric Algorithms primitive operations convex hull closest pair voronoi diagram References: Algorithms in C (2nd edition), Chapters 24-25 http://www.cs.princeton.edu/introalgsds/71primitives http://www.cs.princeton.edu/introalgsds/72hull 1 Geometric Algorithms Applications. • Data mining. • VLSI design. • Computer vision. • Mathematical models. • Astronomical simulation. • Geographic information systems. airflow around an aircraft wing • Computer graphics (movies, games, virtual reality). • Models of physical world (maps, architecture, medical imaging). Reference: http://www.ics.uci.edu/~eppstein/geom.html History. • Ancient mathematical foundations. • Most geometric algorithms less than 25 years old. 2 primitive operations convex hull closest pair voronoi diagram 3 Geometric Primitives Point: two numbers (x, y). any line not through origin Line: two numbers a and b [ax + by = 1] Line segment: two points. Polygon: sequence of points. Primitive operations. • Is a point inside a polygon? • Compare slopes of two lines. • Distance between two points. • Do two line segments intersect? Given three points p , p , p , is p -p -p a counterclockwise turn? • 1 2 3 1 2 3 Other geometric shapes. • Triangle, rectangle, circle, sphere, cone, … • 3D and higher dimensions sometimes more complicated. 4 Intuition Warning: intuition may be misleading. • Humans have spatial intuition in 2D and 3D. • Computers do not. • Neither has good intuition in higher dimensions! Is a given polygon simple? no crossings 1 6 5 8 7 2 7 8 6 4 2 1 1 15 14 13 12 11 10 9 8 7 6 5 4 3 2 1 2 18 4 18 4 19 4 19 4 20 3 20 3 20 1 10 3 7 2 8 8 3 4 6 5 15 1 11 3 14 2 16 we think of this algorithm sees this 5 Polygon Inside, Outside Jordan curve theorem. -

Introduction to Computational Social Choice
1 Introduction to Computational Social Choice Felix Brandta, Vincent Conitzerb, Ulle Endrissc, J´er^omeLangd, and Ariel D. Procacciae 1.1 Computational Social Choice at a Glance Social choice theory is the field of scientific inquiry that studies the aggregation of individual preferences towards a collective choice. For example, social choice theorists|who hail from a range of different disciplines, including mathematics, economics, and political science|are interested in the design and theoretical evalu- ation of voting rules. Questions of social choice have stimulated intellectual thought for centuries. Over time the topic has fascinated many a great mind, from the Mar- quis de Condorcet and Pierre-Simon de Laplace, through Charles Dodgson (better known as Lewis Carroll, the author of Alice in Wonderland), to Nobel Laureates such as Kenneth Arrow, Amartya Sen, and Lloyd Shapley. Computational social choice (COMSOC), by comparison, is a very young field that formed only in the early 2000s. There were, however, a few precursors. For instance, David Gale and Lloyd Shapley's algorithm for finding stable matchings between two groups of people with preferences over each other, dating back to 1962, truly had a computational flavor. And in the late 1980s, a series of papers by John Bartholdi, Craig Tovey, and Michael Trick showed that, on the one hand, computational complexity, as studied in theoretical computer science, can serve as a barrier against strategic manipulation in elections, but on the other hand, it can also prevent the efficient use of some voting rules altogether. Around the same time, a research group around Bernard Monjardet and Olivier Hudry also started to study the computational complexity of preference aggregation procedures. -

Are Condorcet and Minimax Voting Systems the Best?1
1 Are Condorcet and Minimax Voting Systems the Best?1 Richard B. Darlington Cornell University Abstract For decades, the minimax voting system was well known to experts on voting systems, but was not widely considered to be one of the best systems. But in recent years, two important experts, Nicolaus Tideman and Andrew Myers, have both recognized minimax as one of the best systems. I agree with that. This paper presents my own reasons for preferring minimax. The paper explicitly discusses about 20 systems. Comments invited. [email protected] Copyright Richard B. Darlington May be distributed free for non-commercial purposes Keywords Voting system Condorcet Minimax 1. Many thanks to Nicolaus Tideman, Andrew Myers, Sharon Weinberg, Eduardo Marchena, my wife Betsy Darlington, and my daughter Lois Darlington, all of whom contributed many valuable suggestions. 2 Table of Contents 1. Introduction and summary 3 2. The variety of voting systems 4 3. Some electoral criteria violated by minimax’s competitors 6 Monotonicity 7 Strategic voting 7 Completeness 7 Simplicity 8 Ease of voting 8 Resistance to vote-splitting and spoiling 8 Straddling 8 Condorcet consistency (CC) 8 4. Dismissing eight criteria violated by minimax 9 4.1 The absolute loser, Condorcet loser, and preference inversion criteria 9 4.2 Three anti-manipulation criteria 10 4.3 SCC/IIA 11 4.4 Multiple districts 12 5. Simulation studies on voting systems 13 5.1. Why our computer simulations use spatial models of voter behavior 13 5.2 Four computer simulations 15 5.2.1 Features and purposes of the studies 15 5.2.2 Further description of the studies 16 5.2.3 Results and discussion 18 6. -

On the Distortion of Voting with Multiple Representative Candidates∗
The Thirty-Second AAAI Conference on Artificial Intelligence (AAAI-18) On the Distortion of Voting with Multiple Representative Candidates∗ Yu Cheng Shaddin Dughmi David Kempe Duke University University of Southern California University of Southern California Abstract voters and the chosen candidate in a suitable metric space (Anshelevich 2016; Anshelevich, Bhardwaj, and Postl 2015; We study positional voting rules when candidates and voters Anshelevich and Postl 2016; Goel, Krishnaswamy, and Mu- are embedded in a common metric space, and cardinal pref- erences are naturally given by distances in the metric space. nagala 2017). The underlying assumption is that the closer In a positional voting rule, each candidate receives a score a candidate is to a voter, the more similar their positions on from each ballot based on the ballot’s rank order; the candi- key questions are. Because proximity implies that the voter date with the highest total score wins the election. The cost would benefit from the candidate’s election, voters will rank of a candidate is his sum of distances to all voters, and the candidates by increasing distance, a model known as single- distortion of an election is the ratio between the cost of the peaked preferences (Black 1948; Downs 1957; Black 1958; elected candidate and the cost of the optimum candidate. We Moulin 1980; Merrill and Grofman 1999; Barbera,` Gul, consider the case when candidates are representative of the and Stacchetti 1993; Richards, Richards, and McKay 1998; population, in the sense that they are drawn i.i.d. from the Barbera` 2001). population of the voters, and analyze the expected distortion Even in the absence of strategic voting, voting systems of positional voting rules. -
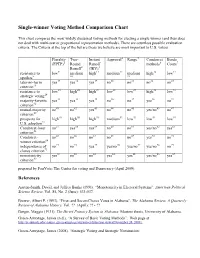
Single-Winner Voting Method Comparison Chart
Single-winner Voting Method Comparison Chart This chart compares the most widely discussed voting methods for electing a single winner (and thus does not deal with multi-seat or proportional representation methods). There are countless possible evaluation criteria. The Criteria at the top of the list are those we believe are most important to U.S. voters. Plurality Two- Instant Approval4 Range5 Condorcet Borda (FPTP)1 Round Runoff methods6 Count7 Runoff2 (IRV)3 resistance to low9 medium high11 medium12 medium high14 low15 spoilers8 10 13 later-no-harm yes17 yes18 yes19 no20 no21 no22 no23 criterion16 resistance to low25 high26 high27 low28 low29 high30 low31 strategic voting24 majority-favorite yes33 yes34 yes35 no36 no37 yes38 no39 criterion32 mutual-majority no41 no42 yes43 no44 no45 yes/no 46 no47 criterion40 prospects for high49 high50 high51 medium52 low53 low54 low55 U.S. adoption48 Condorcet-loser no57 yes58 yes59 no60 no61 yes/no 62 yes63 criterion56 Condorcet- no65 no66 no67 no68 no69 yes70 no71 winner criterion64 independence of no73 no74 yes75 yes/no 76 yes/no 77 yes/no 78 no79 clones criterion72 81 82 83 84 85 86 87 monotonicity yes no no yes yes yes/no yes criterion80 prepared by FairVote: The Center for voting and Democracy (April 2009). References Austen-Smith, David, and Jeffrey Banks (1991). “Monotonicity in Electoral Systems”. American Political Science Review, Vol. 85, No. 2 (June): 531-537. Brewer, Albert P. (1993). “First- and Secon-Choice Votes in Alabama”. The Alabama Review, A Quarterly Review of Alabama History, Vol. ?? (April): ?? - ?? Burgin, Maggie (1931). The Direct Primary System in Alabama. -

Legislature by Lot: Envisioning Sortition Within a Bicameral System
PASXXX10.1177/0032329218789886Politics & SocietyGastil and Wright 789886research-article2018 Special Issue Article Politics & Society 2018, Vol. 46(3) 303 –330 Legislature by Lot: Envisioning © The Author(s) 2018 Article reuse guidelines: Sortition within a Bicameral sagepub.com/journals-permissions https://doi.org/10.1177/0032329218789886DOI: 10.1177/0032329218789886 System* journals.sagepub.com/home/pas John Gastil Pennsylvania State University Erik Olin Wright University of Wisconsin–Madison Abstract In this article, we review the intrinsic democratic flaws in electoral representation, lay out a set of principles that should guide the construction of a sortition chamber, and argue for the virtue of a bicameral system that combines sortition and elections. We show how sortition could prove inclusive, give citizens greater control of the political agenda, and make their participation more deliberative and influential. We consider various design challenges, such as the sampling method, legislative training, and deliberative procedures. We explain why pairing sortition with an elected chamber could enhance its virtues while dampening its potential vices. In our conclusion, we identify ideal settings for experimenting with sortition. Keywords bicameral legislatures, deliberation, democratic theory, elections, minipublics, participation, political equality, sortition Corresponding Author: John Gastil, Department of Communication Arts & Sciences, Pennsylvania State University, 232 Sparks Bldg., University Park, PA 16802, USA. Email: [email protected] *This special issue of Politics & Society titled “Legislature by Lot: Transformative Designs for Deliberative Governance” features a preface, an introductory anchor essay and postscript, and six articles that were presented as part of a workshop held at the University of Wisconsin–Madison, September 2017, organized by John Gastil and Erik Olin Wright. -

Single Transferable Vote Resists Strategic Voting
Single Transferable Vote Resists Strategic Voting John J. Bartholdi, III School of Industrial and Systems Engineering Georgia Institute of Technology, Atlanta, GA 30332 James B. Orlin Sloan School of Management Massachusetts Institute of Technology, Cambridge, MA 02139 November 13, 1990; revised April 4, 2003 Abstract We give evidence that Single Tranferable Vote (STV) is computation- ally resistant to manipulation: It is NP-complete to determine whether there exists a (possibly insincere) preference that will elect a favored can- didate, even in an election for a single seat. Thus strategic voting under STV is qualitatively more difficult than under other commonly-used vot- ing schemes. Furthermore, this resistance to manipulation is inherent to STV and does not depend on hopeful extraneous assumptions like the presumed difficulty of learning the preferences of the other voters. We also prove that it is NP-complete to recognize when an STV elec- tion violates monotonicity. This suggests that non-monotonicity in STV elections might be perceived as less threatening since it is in effect “hid- den” and hard to exploit for strategic advantage. 1 1 Strategic voting For strategic voting the fundamental problem for any would-be manipulator is to decide what preference to claim. We will show that this modest task can be impractically difficult under the voting scheme known as Single Transferable Vote (STV). Furthermore this difficulty pertains even in the ideal situation in which the manipulator knows the preferences of all other voters and knows that they will vote their complete and sincere preferences. Thus STV is apparently unique among voting schemes in actual use today in that it is computationally resistant to manipulation. -
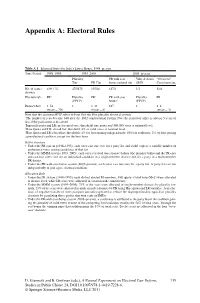
Appendix A: Electoral Rules
Appendix A: Electoral Rules Table A.1 Electoral Rules for Italy’s Lower House, 1948–present Time Period 1948–1993 1993–2005 2005–present Plurality PR with seat Valle d’Aosta “Overseas” Tier PR Tier bonus national tier SMD Constituencies No. of seats / 6301 / 32 475/475 155/26 617/1 1/1 12/4 districts Election rule PR2 Plurality PR3 PR with seat Plurality PR (FPTP) bonus4 (FPTP) District Size 1–54 1 1–11 617 1 1–6 (mean = 20) (mean = 6) (mean = 4) Note that the acronym FPTP refers to First Past the Post plurality electoral system. 1The number of seats became 630 after the 1962 constitutional reform. Note the period of office is always 5 years or less if the parliament is dissolved. 2Imperiali quota and LR; preferential vote; threshold: one quota and 300,000 votes at national level. 3Hare Quota and LR; closed list; threshold: 4% of valid votes at national level. 4Hare Quota and LR; closed list; thresholds: 4% for lists running independently; 10% for coalitions; 2% for lists joining a pre-electoral coalition, except for the best loser. Ballot structure • Under the PR system (1948–1993), each voter cast one vote for a party list and could express a variable number of preferential votes among candidates of that list. • Under the MMM system (1993–2005), each voter received two separate ballots (the plurality ballot and the PR one) and cast two votes: one for an individual candidate in a single-member district; one for a party in a multi-member PR district. • Under the PR-with-seat-bonus system (2005–present), each voter cast one vote for a party list. -

Randnla: Randomized Numerical Linear Algebra
review articles DOI:10.1145/2842602 generation mechanisms—as an algo- Randomization offers new benefits rithmic or computational resource for the develop ment of improved algo- for large-scale linear algebra computations. rithms for fundamental matrix prob- lems such as matrix multiplication, BY PETROS DRINEAS AND MICHAEL W. MAHONEY least-squares (LS) approximation, low- rank matrix approxi mation, and Lapla- cian-based linear equ ation solvers. Randomized Numerical Linear Algebra (RandNLA) is an interdisci- RandNLA: plinary research area that exploits randomization as a computational resource to develop improved algo- rithms for large-scale linear algebra Randomized problems.32 From a foundational per- spective, RandNLA has its roots in theoretical computer science (TCS), with deep connections to mathemat- Numerical ics (convex analysis, probability theory, metric embedding theory) and applied mathematics (scientific computing, signal processing, numerical linear Linear algebra). From an applied perspec- tive, RandNLA is a vital new tool for machine learning, statistics, and data analysis. Well-engineered implemen- Algebra tations have already outperformed highly optimized software libraries for ubiquitous problems such as least- squares,4,35 with good scalability in par- allel and distributed environments. 52 Moreover, RandNLA promises a sound algorithmic and statistical foundation for modern large-scale data analysis. MATRICES ARE UBIQUITOUS in computer science, statistics, and applied mathematics. An m × n key insights matrix can encode information about m objects ˽ Randomization isn’t just used to model noise in data; it can be a powerful (each described by n features), or the behavior of a computational resource to develop discretized differential operator on a finite element algorithms with improved running times and stability properties as well as mesh; an n × n positive-definite matrix can encode algorithms that are more interpretable in the correlations between all pairs of n objects, or the downstream data science applications. -

Mechanism, Mentalism, and Metamathematics Synthese Library
MECHANISM, MENTALISM, AND METAMATHEMATICS SYNTHESE LIBRARY STUDIES IN EPISTEMOLOGY, LOGIC, METHODOLOGY, AND PHILOSOPHY OF SCIENCE Managing Editor: JAAKKO HINTIKKA, Florida State University Editors: ROBER T S. COHEN, Boston University DONALD DAVIDSON, University o/Chicago GABRIEL NUCHELMANS, University 0/ Leyden WESLEY C. SALMON, University 0/ Arizona VOLUME 137 JUDSON CHAMBERS WEBB Boston University. Dept. 0/ Philosophy. Boston. Mass .• U.S.A. MECHANISM, MENT ALISM, AND MET AMA THEMA TICS An Essay on Finitism i Springer-Science+Business Media, B.V. Library of Congress Cataloging in Publication Data Webb, Judson Chambers, 1936- CII:J Mechanism, mentalism, and metamathematics. (Synthese library; v. 137) Bibliography: p. Includes indexes. 1. Metamathematics. I. Title. QA9.8.w4 510: 1 79-27819 ISBN 978-90-481-8357-9 ISBN 978-94-015-7653-6 (eBook) DOl 10.1007/978-94-015-7653-6 All Rights Reserved Copyright © 1980 by Springer Science+Business Media Dordrecht Originally published by D. Reidel Publishing Company, Dordrecht, Holland in 1980. Softcover reprint of the hardcover 1st edition 1980 No part of the material protected by this copyright notice may be reproduced or utilized in any form or by any means, electronic or mechanical, including photocopying, recording or by any informational storage and retrieval system, without written permission from the copyright owner TABLE OF CONTENTS PREFACE vii INTRODUCTION ix CHAPTER I / MECHANISM: SOME HISTORICAL NOTES I. Machines and Demons 2. Machines and Men 17 3. Machines, Arithmetic, and Logic 22 CHAPTER II / MIND, NUMBER, AND THE INFINITE 33 I. The Obligations of Infinity 33 2. Mind and Philosophy of Number 40 3. Dedekind's Theory of Arithmetic 46 4. -

A Mathematical Analysis of Student-Generated Sorting Algorithms Audrey Nasar
The Mathematics Enthusiast Volume 16 Article 15 Number 1 Numbers 1, 2, & 3 2-2019 A Mathematical Analysis of Student-Generated Sorting Algorithms Audrey Nasar Let us know how access to this document benefits ouy . Follow this and additional works at: https://scholarworks.umt.edu/tme Recommended Citation Nasar, Audrey (2019) "A Mathematical Analysis of Student-Generated Sorting Algorithms," The Mathematics Enthusiast: Vol. 16 : No. 1 , Article 15. Available at: https://scholarworks.umt.edu/tme/vol16/iss1/15 This Article is brought to you for free and open access by ScholarWorks at University of Montana. It has been accepted for inclusion in The Mathematics Enthusiast by an authorized editor of ScholarWorks at University of Montana. For more information, please contact [email protected]. TME, vol. 16, nos.1, 2&3, p. 315 A Mathematical Analysis of student-generated sorting algorithms Audrey A. Nasar1 Borough of Manhattan Community College at the City University of New York Abstract: Sorting is a process we encounter very often in everyday life. Additionally it is a fundamental operation in computer science. Having been one of the first intensely studied problems in computer science, many different sorting algorithms have been developed and analyzed. Although algorithms are often taught as part of the computer science curriculum in the context of a programming language, the study of algorithms and algorithmic thinking, including the design, construction and analysis of algorithms, has pedagogical value in mathematics education. This paper will provide an introduction to computational complexity and efficiency, without the use of a programming language. It will also describe how these concepts can be incorporated into the existing high school or undergraduate mathematics curriculum through a mathematical analysis of student- generated sorting algorithms.