David Eargle
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
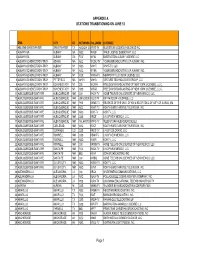
Appendix a Stations Transitioning on June 12
APPENDIX A STATIONS TRANSITIONING ON JUNE 12 DMA CITY ST NETWORK CALLSIGN LICENSEE 1 ABILENE-SWEETWATER SWEETWATER TX ABC/CW (D KTXS-TV BLUESTONE LICENSE HOLDINGS INC. 2 ALBANY GA ALBANY GA NBC WALB WALB LICENSE SUBSIDIARY, LLC 3 ALBANY GA ALBANY GA FOX WFXL BARRINGTON ALBANY LICENSE LLC 4 ALBANY-SCHENECTADY-TROY ADAMS MA ABC WCDC-TV YOUNG BROADCASTING OF ALBANY, INC. 5 ALBANY-SCHENECTADY-TROY ALBANY NY NBC WNYT WNYT-TV, LLC 6 ALBANY-SCHENECTADY-TROY ALBANY NY ABC WTEN YOUNG BROADCASTING OF ALBANY, INC. 7 ALBANY-SCHENECTADY-TROY ALBANY NY FOX WXXA-TV NEWPORT TELEVISION LICENSE LLC 8 ALBANY-SCHENECTADY-TROY PITTSFIELD MA MYTV WNYA VENTURE TECHNOLOGIES GROUP, LLC 9 ALBANY-SCHENECTADY-TROY SCHENECTADY NY CW WCWN FREEDOM BROADCASTING OF NEW YORK LICENSEE, L.L.C. 10 ALBANY-SCHENECTADY-TROY SCHENECTADY NY CBS WRGB FREEDOM BROADCASTING OF NEW YORK LICENSEE, L.L.C. 11 ALBUQUERQUE-SANTA FE ALBUQUERQUE NM CW KASY-TV ACME TELEVISION LICENSES OF NEW MEXICO, LLC 12 ALBUQUERQUE-SANTA FE ALBUQUERQUE NM UNIVISION KLUZ-TV ENTRAVISION HOLDINGS, LLC 13 ALBUQUERQUE-SANTA FE ALBUQUERQUE NM PBS KNME-TV REGENTS OF THE UNIV. OF NM & BD.OF EDUC.OF CITY OF ALBUQ.,NM 14 ALBUQUERQUE-SANTA FE ALBUQUERQUE NM ABC KOAT-TV KOAT HEARST-ARGYLE TELEVISION, INC. 15 ALBUQUERQUE-SANTA FE ALBUQUERQUE NM NBC KOB-TV KOB-TV, LLC 16 ALBUQUERQUE-SANTA FE ALBUQUERQUE NM CBS KRQE LIN OF NEW MEXICO, LLC 17 ALBUQUERQUE-SANTA FE ALBUQUERQUE NM TELEFUTURKTFQ-TV TELEFUTURA ALBUQUERQUE LLC 18 ALBUQUERQUE-SANTA FE CARLSBAD NM ABC KOCT KOAT HEARST-ARGYLE TELEVISION, INC. -

Brigham Young University-Hawaii
FOR IMMEDIATE RELEASE Contacts: Emilio Aleman Robin Hoffman Hitachi Kokusai Electric America, Ltd. Pipeline Communications 516.682.4406 973.746.6970 [email protected] [email protected] BRIGHAM YOUNG UNIVERSITY-HAWAII SELECTS FOUR HITACHI SK-HD1000 HD CAMERAS TO PRODUCE HD PROGRAMMING FOR ITS WEBSITE AND BYU-TV WOODBURY, NEW YORK, May 19, 2009 – Hitachi Kokusai Electric America, Ltd., a leading provider of affordable, high performance cameras, today announced that Brigham Young University-Hawaii (BYU-Hawaii)—an accredited, four-year undergraduate institution in Laie, HI—bought four Hitachi SK-HD1000 native 1080i HDTV studio/field production cameras to produce HD programming for its website (http://www.byuh.edu ) as well as for BYU Television. BYU-Hawaii and its sister colleges BYU (in Utah) and BYU-Idaho all produce their own programming—such as entertainment, documentaries, and educational programs. These shows are seen on BYU TV, the Brigham Young University-run TV network that reaches over 50 million homes nationwide on DirecTV, Dish Network, and cable systems, and a global audience via the Internet. While most of this programming has been done in SD, BYU-Hawaii bought the Hitachi SK-HD1000’s because the demand for HD is steadily increasing. ―Because of the superior price performance of the Hitachi SK-HD1000, we’ve been able to go hi-def four years sooner than we had planned. We could not have realized our goal to go hi-def so quickly without this camera because comparable competitors were cost-prohibitive,‖ said Lawrence Lau, manager of TV studios for BYU-Hawaii. ―Hitachi has also satisfied another key concern we had—reliability. -

The Salt Lake Tabernacle: a Witness to the Growth of God’S Kingdom
Chapter 5 The Salt Lake Tabernacle: A Witness to the Growth of God’s Kingdom Scott C. Esplin “ n great deeds something abides,” reminisced Joshua Lawrence IChamberlain, a famed Civil War colonel. “On great fields some- thing stays. Forms change and pass; bodies disappear, but spirits linger, to consecrate ground for the vision-place of souls. And reverent men and women from afar, and generations that know us not and that we know not of, heart-drawn to see where and by whom great things were suffered and done for them, shall come to this deathless field to ponder and dream; And lo! the shadow of a mighty presence shall wrap them in its bosom, and the power of the vision pass into their souls.”1 For Latter-day Saints, the historic Salt Lake Tabernacle has become one of those sacred sites—a consecrated hall where “something abides” and “spirits linger” and where modern visitors are wrapped in “the shadow of a mighty presence” while visions of the Restoration “pass into their souls.” President Gordon B. Hinckley summarized the influence the Scott C. Esplin is an assistant professor of Church history and doctrine at Brigham Young University. 69 Salt Lake City: The Place Which God Prepared Tabernacle has had on the Church: “The Spirit of the Lord has been in this structure. It is sacred unto us.”2 With the construction of larger and more modern conference halls, the Salt Lake Tabernacle stands today as a silent witness to its pioneer past. Having undergone significant transformations throughout its life, the building serves not only as a monument to pioneer greatness but also as an example of changes in the Church’s history. -

2020 Provo Campus
2020 Brigham Young University Annual Security and Fire Safety Reports ANNUAL SECURITY REPORT Contents ANNUAL SECURITY REPORT ........................................................................................................................... 1 Resource Phone Numbers ............................................................................................................................. 4 Message from Chris Autry ............................................................................................................................. 6 What Is the Clery Act? ................................................................................................................................... 7 Clery Act Annual Security Report Preparation .................................................................................................7 Collecting Crime Data and Reporting Procedures ........................................................................................... 8 Crime Log and Campus Warnings .....................................................................................................................8 2017-2019 Reported Crime Statistics ............................................................................................................. 9 BYU Campus Law Enforcement: BYU Police ................................................................................................. 11 BYU Police Mission Statement ...................................................................................................................... -

Dear East Legacy Season Ticket Holder: in Accordance With
Dear East Legacy Season Ticket Holder: In accordance with tax laws and regulations, Brigham Young University (BYU) is providing to you this good faith estimate of the value of goods and services which you were entitled to receive in connection with your payments for each East Legacy Chair seat at LaVell Edwards Stadium for the 2019 football season. As indicated in the enclosed Cougar Club Tax Disclosure Statement, your payments to BYU Athletics in 2019 are tax-deductible only to the extent that you did not receive a benefit, or the right to receive such a benefit, in return. Because of revisions to the Internal Revenue Code which became effective beginning January 1, 2018, any portion of your payment that entitles you to purchase priority seating is not tax- deductible. Amended IRC Section 170(l) provides in part as follows: “No deduction shall be allowed … if … the taxpayer receives (directly or indirectly) as a result of paying such amount the right to purchase tickets for seating at an athletic event in an athletic stadium of such institution.” Cougar Club Membership Dues Cougar Club members make contributions to BYU Athletics in order to be eligible to purchase tickets in the priority seating areas. For the 2019 season donors needed to have contributed $1,250 or more to be eligible to purchase East Legacy Chair Seating. With the change in IRC Section 170(l), this entire amount is not tax-deductible. Donations, or portions of donations, made in 2019 that are in excess of $1,250 may also not be tax-deductible if you received, or had the right to receive, additional Cougar Club benefits (such as club luncheons, press almanacs, membership gifts, etc.) The fair market values for such Cougar Club benefits are detailed in the enclosed Cougar Club Tax Disclosure Statement. -

Donald Philip Breakwell, Ph.D
Donald Philip Breakwell, Ph.D. Teaching Professor Department of Microbiology and Molecular Biology Brigham Young University 2060G LSB Provo, UT 84602 Telephone (801) 378-2378 Email: [email protected] Skype: donbreakwell2 Education Doctor of Philosophy, August 1992, Purdue University Master of Science, August 1988, Purdue University Bachelor of Science, August 1986, Brigham Young University Employment History 2015-present Assistant Dean, Director of Student Services, College of Life Sciences, Brigham Young University 2010-present Teaching Professor, Brigham Young University 2001-2010 Associate Teaching Professor, Brigham Young University; continuing faculty status granted, 2008 2000-2001 Temporary Associate Teaching Professor, Brigham Young University 1996-2000 Associate Professor, Snow College; tenure granted, 1996 1992-1996 Assistant Professor, Snow College 1992 Research Assistant, Michigan State University Honors and Awards Technology Transfer Award, 2016, Brigham Young University Karl G. Maeser Professional Faculty Excellence Award, 2015, Brigham Young University College of Life Sciences Teaching Excellence Award, 2008, Brigham Young University Alcuin Fellowship in General Education, 2003-2006, Brigham Young University Professional Service American Society for Microbiology 2009-2012, Editorial Board, Journal of Microbiology and Biology Education. American Society for Microbiology 2008-2009, Chair of Steering Committee, American Society for Microbiology Conference for Undergraduate Educators. American Society for Microbiology 2008-2010, -

EDUCATION in ZION We Move Forward Faithfully Into the Future Only by Understanding Our Past
EDUCATION IN ZION We move forward faithfully into the future only by understanding our past. Our founding stories reveal to us the higher purposes for which our forebears strove, and help us know the path that we should follow. Come unto me … and learn of me. —Matthew 11:28–29 I am the light, and the life, and the truth of the world. —Ether 4:12 I am the vine, ye are the branches: He that abideth in me, and I in him, the same bringeth forth much fruit. —John 15:5 I am the good shepherd: the good shepherd giveth his life for the sheep. —John 10:11 Feed my lambs. … Feed my sheep. —John 21:15–17 As Latter-day Saints, we believe Christ to be the Source of all light and truth, speaking through His prophets and enlightening and inspiring people everywhere. Therefore, we seek truth wherever it might be found and strive to shape our lives by it. In the Zion tradition, we share the truth freely so that every person might learn and grow and in turn strengthen others. From our faith in Christ and our love for one another, our commitment to education flows. Feed My Lambs, Feed My Sheep, by a BYU student, after a sculpture in the Vatican Library Hand-tufted wool rug, designed by a BYU student Circular skylight, Joseph F. Smith Building gallery [L] “Feed My Lambs … Feed My Sheep,” by a BYU student, after a sculpture in the Vatican Library [L] Hand-tufted wool rug, designed by a BYU student [L] Circular skylight, Joseph F. -

Article by Gordon B
Gordon B. Hinckley, right, of the Church Radio, Publicity and Mission Literature Committee, examining a 35mm film with his former mission president, Elder Joseph F. Merrill, center, of the Quorum of the Twelve Apostles. Hinckley and a cadre of other young multitasking enthusiasts were responsible for pioneering various forms of media and for establishing a culture in which slide shows, radio plays, exhibits, and cinema would be used in Church education and publicity. LDS Church Archives, © Intellectual Reserve, Inc. A History of Mormon Cinema: Second Wave V 45 The Second Wave: Home Cinema (1929–1953) The Second Wave differed from the First in various respects. For instance, by the 1930s the global film industry was well past its primitive pioneer era, and, within Mormonism, the increased sophistication of Second Wave films reflects this progress. In addition, technical advances (principally sound, but also color) renewed enthusiasm about the medium, both generally and among the Latter-day Saints. While this optimism did propel institutional and independent Mormon filmmaking toward some major projects, the decade of the 1930s—and to a lesser extent the 1940s— has generally been described for its lack of Mormon film production. Such a perception, however, does not give full credit to changes and growth in underlying areas of Mormon cinema that created a sustainable cinematic culture that would last throughout the ensuing years. Indeed, the 1930s and 1940s were decades in which both the mainstream film industry and the LDS Church itself reinvented the relationship between Mormonism and cinema. Due to Hollywood’s adoption of the Hays Production Code and the aforementioned loss of Mormonism’s sensationalism, mainstream depic- tions of Mormonism changed radically to the positive in the 1930s. -

Grizzly Football Game Day Program, October 4, 1952 University of Montana—Missoula
University of Montana ScholarWorks at University of Montana Grizzly Football Game Day Programs, 1914-2012 University of Montana Publications 10-4-1952 Grizzly Football Game Day Program, October 4, 1952 University of Montana—Missoula. Athletics Department Let us know how access to this document benefits ouy . Follow this and additional works at: https://scholarworks.umt.edu/grizzlyfootball_programs_asc Recommended Citation University of Montana—Missoula. Athletics Department, "Grizzly Football Game Day Program, October 4, 1952" (1952). Grizzly Football Game Day Programs, 1914-2012. 28. https://scholarworks.umt.edu/grizzlyfootball_programs_asc/28 This Program is brought to you for free and open access by the University of Montana Publications at ScholarWorks at University of Montana. It has been accepted for inclusion in Grizzly Football Game Day Programs, 1914-2012 by an authorized administrator of ScholarWorks at University of Montana. For more information, please contact [email protected]. 0FF»A L PROGRAM # TWENTY-FIVE CENTS IlLD • OCTOBER 1952 DOROTHY COLLINS, ‘The Sweetheart of Lucky Strike says: Be Happy- GO LUCKY! LUCKIES TASTE A Welcome from Your President The welcome sign is always out to friends and former students of Montana State University. You will observe that something new is being added to the campus, but you need never feel a stranger here. Particularly the m em bers of the classes of 1902 an d 1927, who are cele brating their Golden and Silver graduation anniversaries, will appreciate the changes to bo wrought by the present construction on the campus. It was in 1902 that the need for adequate living accommodations for women students inaugurated construction of Craig Hall, the first addition to the University's then two-buildng campus. -
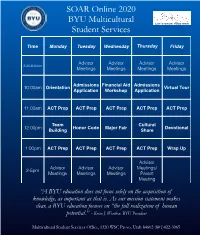
SOAR Online 2020 BYU Multicultural Student Services
SOAR Online 2020 Y BYU Multicultural Let’s grow together Student Services Time Monday Tuesday Wednesday Thursday Friday Advisor Advisor Advisor Advisor 8:30-9:30am Meetings Meetings Meetings Meetings Admissions Financial Aid Admissions 10:00am Orientation Virtual Tour Application Workshop Application 11:00am ACT Prep ACT Prep ACT Prep ACT Prep ACT Prep Team Cultural 12:00pm Honor Code Major Fair Devotional Building Share 1:00pm ACT Prep ACT Prep ACT Prep ACT Prep Wrap Up Advisor Advisor Advisor Advisor Meetings/ 2-5pm Meetings Meetings Meetings Parent Meeting “A BYU education does not focus solely on the acquisition of knowledge, as important as that is. As our mission statement makes clear, a BYU education focuses on “the full realization of human potential.” - Kevin J. Worthen, BYU President Multicultural Student Services Office, 1320 WSC Provo, Utah 84602 (801)422-3065 MY INFORMATION .................................................................................. 1 Identification ....................................................................................................... 1 SOAR 2020 ACT Instructors ........................................................................... 1 Personal Action Plan ......................................................................................... 2 FOUNDATIONAL DOCUMENTS .......................................................... 3 SOAR Mission & Objectives ........................................................................... 3 SOAR Standards ............................................................................................... -

Student Exchange Program
student exchange program whitmore global management center marriott school brigham young university 1 contents 5 : about the university 6 : marriott school of management 10 : marriott school student resources 12 : byu campus 17 : useful information 19 : byu culture 21 : recreation and entertainment 2 Dear student, It has never been more important to be connected to the global economy than it is today. In spite of the global economic crisis and slowdown in world trade, the future of international business is still bright. Now more than ever, you will likely work in the global economy. You might be working abroad or working in your home country for either a local multinational corporation or for a foreign-based company that is enter- ing your market. Whatever your future brings, it will be important for you to understand how to negotiate foreign languages and culture. It is one thing to study a language in school, but you also need to get used to different countries and cultures as well. Cultural is broad, and language is just one aspect. BYU is a great place to study, because over 70 percent of our students speak a second language and many have lived abroad for a year or more. In your classes, you will be able to interact with students from other countries but also with U.S. students with broad international experience. In any given class, you will have classmates with international experience in multiple countries in all regions of the world. These students have gained a knowledge of and love for the people, language, and culture of places where they have lived. -

2014 Traverse Mountain Health Consultation (HC)
Health Consultation TRAVERSE MOUNTAIN: THALLIUM IN DRINKING WATER LEHI, UTAH COUNTY, UTAH Prepared by Utah Department of Health DECEMBER 3, 2014 Prepared under a Cooperative Agreement with the U.S. DEPARTMENT OF HEALTH AND HUMAN SERVICES Agency for Toxic Substances and Disease Registry Division of Community Health Investigations Atlanta, Georgia 30333 Health Consultation: A Note of Explanation A health consultation is a verbal or written response from ATSDR or ATSDR’s Cooperative Agreement Partners to a specific request for information about health risks related to a specific site, a chemical release, or the presence of hazardous material. In order to prevent or mitigate exposures, a consultation may lead to specific actions, such as restricting use of or replacing water supplies; intensifying environmental sampling; restricting site access; or removing the contaminated material. In addition, consultations may recommend additional public health actions, such as conducting health surveillance activities to evaluate exposure or trends in adverse health outcomes; conducting biological indicators of exposure studies to assess exposure; and providing health education for health care providers and community members. This concludes the health consultation process for this site, unless additional information is obtained by ATSDR or ATSDR’s Cooperative Agreement Partner which, in the Agency’s opinion, indicates a need to revise or append the conclusions previously issued. You May Contact ATSDR Toll Free at 1-800-CDC-INFO or Visit our Home Page at: http://www.atsdr.cdc.gov HEALTH CONSULTATION TRAVERSE MOUNTAIN: THALLIUM IN DRINKING WATER LEHI, UTAH COUNTY, UTAH Prepared By: Environmental Epidemiology Program Office of Epidemiology Utah Department of Health Under a Cooperative Agreement with the Agency for Toxic Substances and Disease Registry Traverse Mountain / Lehi, Utah Health Consultation TABLE OF CONTENTS SUMMARY ...................................................................................................................................