Reversing and Exploiting an Apple Firmware Update
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Macbook Pro Built-In Keyboard Mapping in Windows
MacBook Pro built-in keyboard mapping in Windows Summary Learn how Boot Camp maps Microsoft Windows functions and special keys to the MacBook Pro built-in keyboard, as well as which keys to use for various functions. Note : MacBook built-in keyboards are similar to MacBook Pro built-in keyboards, but there are some differences (such as Keyboard Illumination keys, which are not on a MacBook keyboard). However, the majority of this article applies to MacBook keyboards as well. Sample MacBook Pro built-in keyboard Products Affected Boot Camp, Microsoft Windows XP, Microsoft Window Vista Key mappings for Microsoft Windows features Below is a chart of keyboard functions specific to Microsoft Windows, and equivalent key combinations as they are mapped to Apple keyboards by the Apple Keyboard Support driver. Function PC keyboard MacBook Pro built-in keyboard Print Screen Print active -- window Scroll Lock Pause/Brea -- k Backspace delete Insert -- Number lock Alt (Option) Enter AltGr / Alt GR (Right Alt key) Forward delete Applications -- Windows logo (Start menu) Key mappings for Boot Camp features Some keys are only available on a keyboard designed for Apple computers. They are either named differently or simply not available on a Windows-compatible keyboard. Your Apple keyboard provides certain keys that are not available on Windows/PC keyboards. Function PC keyboard MacBook Pro built-in keyboard Brightness down -- Brightness up -- Volume down -- Volume up -- Mute -- Media eject -- Media eject secondary optical drive -- Delete -- Fn (Function) -- Display Mode Toggle -- Keyboard Illumination Toggle (MacBook Pro) -- Decrease Keyboard Illumination -- Increase Keyboard Illumination -- Numeric keypad mappings Apple external and built-in keyboards provide the same functionality as Microsoft-compatible numeric keypads. -

Mac Mini User Guide
Congratulations, you and your Mac mini were made for each other. Say hello to your Mac mini. www.apple.com/macmini Finder Mail iCal and Address Book Browse your files like Manage all your email Keep your schedule and you browse your music accounts in one place. your contacts in sync. with Cover Flow. Mac Help Mac Help Mac Help mail isync finder Mac OS X Leopard www.apple.com/macosx Time Machine Quick Look Spotlight Safari Automatically Instantly preview Find anything Experience the web back up and your files. on your Mac. with the fastest restore your files. Mac Help Mac Help browser in the world. Mac Help quick look spotlight Mac Help time machine safari iLife ’09 www.apple.com/ilife iPhoto iMovie GarageBand iWeb Organize and Make a great- Learn to play. Create custom search your looking movie in Start a jam session. websites and publish photos by faces, minutes or edit Record and mix them anywhere with places, or events. your masterpiece. your own song. a click. iPhoto Help iMovie Help GarageBand Help iWeb Help photos movie record website Contents Chapter 1: Ready, Set Up, Go 10 What’s in the Box 11 Setting Up Your Mac mini 18 Putting Your Mac mini to Sleep or Shutting It Down Chapter 2: Life with Your Mac mini 22 What’s on the Front of Your Mac mini 24 What’s on the Back of Your Mac mini 26 Getting Answers Chapter 3: Problem, Meet Solution 32 Problems That Prevent You from Using Your Mac mini 34 Reinstalling the Software That Came with Your Mac mini 35 Other Problems 36 Using Apple Hardware Test 37 Problems with Your Internet Connection -

Mac OS X Desktop.Pdf
Apple Training Series Mac OS X Support Essentials v10.6 Kevin M. White Apple Training Series: Mac OS X Support Essentials v10.6 Kevin M. White Copyright © 2010 by Apple Inc. Published by Peachpit Press. For information on Peachpit Press books, contact: Peachpit Press 1249 Eighth Street Berkeley, CA 94710 510/524-2178 510/524-2221 (fax) www.peachpit.com To report errors, please send a note to [email protected]. Peachpit Press is a division of Pearson Education. Apple Training Series Editor: Rebecca Freed Production Editors: Danielle Foster, Becky Winter Copyeditor: Peggy Nauts Tech Editor: Gordon Davisson Apple Editor: Shane Ross Proofreader: Suzie Nasol Compositor: Danielle Foster Indexer: Valerie Perry Cover design: Mimi Heft Cover illustrator: Kent Oberheu Notice of Rights All rights reserved. No part of this book may be reproduced or transmitted in any form by any means, electronic, mechanical, photocopying, recording, or otherwise, without the prior written permission of the publisher. For infor- mation on getting permission for reprints and excerpts, contact [email protected]. Notice of Liability The information in this book is distributed on an “As Is” basis without warranty. While every precaution has been taken in the preparation of the book, neither the author nor Peachpit shall have any liability to any person or entity with respect to any loss or damage caused or alleged to be caused directly or indirectly by the instructions contained in this book or by the computer software and hardware products described in it. Trademarks Many of the designations used by manufacturers and sellers to distinguish their products are claimed as trademarks. -

Macworld’S Mresell Service
iTUNES TIPS: GET TO KNOW iTUNES 12 THE WORLD’S BEST-SELLING APPLE MAGAZINE MARCH 2015 MAC TRICKS 10 AMAZING THINGS YOU DIDN’T KNOW YOUR MAC COULD DO Best iPhone games MacBook Air 14 TOP FREE GAMES FOR iOS vs Mac mini Which low-cost Mac is best for you? + 2.8GHz Mac mini NEW REVIEW Sell your iPad, iPhone, MacBook or iMac with Macworld’s mResell service Did you get a new Apple device for Christmas? Macworld would like to introduce you to mResell, an Apple-trusted site that helps you sell your old Apple products. Our service will help you get a great price in a safe and secure way. But don’t just take our word for it – get an instant, no obligation quote now. Enter your Apple serial number now: mresell.macworld.co.uk mResell.indd 126 15/12/2014 16:29 Contents MARCH 2015 7 Spotlight: David Price Apple vs Samsung 20 8 News Apple’s best ever quarter 12 Best-value Mac If you’re looking for a low-cost Mac we’ll help you choose 20 10 amazing Mac tricks Bet you didn’t know your Mac did this 24 Set up a new Mac We show you how to get started 26 10 apps for a new Mac Enhance your user experience 30 15 iTunes tips & tricks Get more out of iTunes 12 33 Mac security options 12 Four essential security tools 34 Ask the iTunes Guy We demystify artwork and wishlists 36 Apple Watch revolution Taptics, haptics and the body fantastic 38 10 fascinating Apple facts Test your Apple knowledge 39 Lessons for Apple Seven lessons Apple could learn from Microsoft 40 Group test: Smart heating 41 Tado Smart Thermostat 44 Hive Active Heating 46 Nest Learning Thermostat 54 48 Heat Genius 54 Group test: Cameras 55 Canon EOS 7D Mark II 55 Fujifilm X-T1 56 Kodak PixPro S-1 56 Nikon D810 57 Olympus OM-D E-M10 57 Panasonic Lumix DMC-GH4 40 58 Samsung NX1 58 Sony A7 Mark II MARCH 2015 MACWORLD 3 003_004 Contents MAR15.indd 3 03/02/2015 16:15 Contents 60 contact.. -

Montclair Public Schools Public Board Meeting Held On
.. MONTCLAIR PUBLIC SCHOOLS PUBLIC BOARD MEETING HELD ON TUESDAY, FEBRUARY 20, 2018 AT 6:00 PM GEORGE INNESS ANNEX ATRIUM 141 PARK STREET, MONTCLAIR, NEW JERSEY Minutes/Public Board Meeting Tuesday, February 20, 2018 Page 1 MINTUES OF THE PUBLIC BOARD MEETING HELD TUESDAY, FEBRUARY 20, 2018 AT 6:00 PM GEORGE INNESS ANNEX ATRIUM 141 PARK STREET, MONTCLAIR, NEW JERSEY A. STATEMENTS 1. Meeting Notice at 6:00 pm Let the minutes reflect that adequate notice of this meeting has been approved in the following manner: 1. On Thursday, December 7, 2017, notice of this meeting was posted on the public bulletin board in the first floor main hall of the Board of Education building, 22 Valley Road and filed with the Township Clerk. The time, date and location of this meeting were accurately set forth therein. 2. On Thursday, December 14, 2017, notice of this meeting was posted in the Montclair Times. The date, time and location of this meeting were accurately set forth therein. 3. On Saturday, December 16, 2017, notice of this meeting was posted in the Herald News. The date, time and location of this meeting were accurately set forth therein. “Please be advised that this meeting is considered a public meeting under the law and may be taped, broadcast, used or reproduced in ways and in mediums beyond the control of the Board of Education. Individual statements and opinions expressed are solely those of the speakers and do not necessarily represent the Montclair Board of Education. Please keep in mind that if you directly disclose personally identifiable information or personally sensitive data regarding yourself or others during this public meeting, this information may be collected and used by others. -

Apple Publications Style Guide December 2009
Apple Publications Style Guide December 2009 style n. 1. The way in which something is said, done, expressed, or performed: a style of speech and writing. 2. The combination of distinctive features of literary or artistic expression, execution, or performance characterizing a particular person, group, school, or era. 3. Sort; type: a style of furniture. 4. A quality of imagination and individuality expressed in one’s actions and tastes: does things with style. 5a. A com- fortable and elegant mode of existence: living in style. b. A mode of living: the style of the very rich. 6a. The fashion of the moment, especially of dress; vogue. b. A par- ticular fashion: the style of the 1920s. 7. A customary manner of presenting printed material, including usage, punctuation, spelling, typography, and arrangement. 8. A form of address; a title. 9a. An implement used for etching or engraving. b. A slen- der pointed writing instrument used by the ancients on wax tablets. 10. The needle of a phonograph. 11 . The gnomon of a sundial. 12 . Botany The usually slender part of a pistil, situated between the ovary and the stigma. 13 . Zoology A slender, tubular, or bristlelike process: a cartilaginous style. 14 . Medicine A surgical probing instru- ment; a stylet. 15. Obsolete A pen. —tr. v. styled, styl•ing, styles 1. To call or name; designate: George VI styled his brother Duke of Windsor. 2. To make consistent with rules of style: style a manuscript. 3. To give style to: style hair. [Middle English, from Old French, from Latin stylus, stilus, spike, pointed instrument used for writing, style. -

Ilounge 2010 Buyers' Guide
©2012 SwitchEasy Limited, All Rights Reserved. U.S. and International Patents pending. iPhone5 is registered trademarks of Apple Computer Inc. 2013 Welcome to the Guide. IPHONE + IPOD BUYERS’ GUIDE After a slow and uneven 2011, Apple roared back in 2012, launching a wide array of significantly redesigned devices. The iPod, iPhone, and iPad families all saw major screen revisions, including two taller iPods, one elongated iPhone, and a quadrupled-resolution iPad. Then, just before the holidays, Apple debuted the 7.9” iPad mini, and replaced the 9.7” iPad again - just because it could. Going into 2013, the lineup looks almost completely different than it did a year earlier, except for three iPods that have been left largely untouched. If you’re reading this Guide, you’re probably looking for buying advice, and that’s why we’re here - to give you an impartial and honest look at the world of Apple devices, accessories, apps, and games. Following our tradition, iLounge’s editors have spent the past year testing hundreds of new products, selecting the best and most noteworthy ones for our new 2013 iPhone + iPod Buyers Guide. Independently assembled, our Guide is a sight to behold. We hope you enjoy it. The 2013 iPhone + iPod Buyers’ Guide is published by iLounge, Inc. and is Copyright © 2004-2012. All rights reserved. No part of this guide may be reproduced, sold, rented, or transmitted in any form, or by any means whatsoever, without the prior written consent of the publisher. Unauthorized sale of this guide is prohibited, and by accessing this guide, you agree not to violate these restrictions. -

Bluetooth Keyboard Commands with Voiceover on the Ipad Ios 9.2
Bluetooth Keyboard Commands with VoiceOver on the iPad iOS 9.2 Chapter 3: General Navigation using Bluetooth Keyboard Commands (Quick Nav is ON) Module Objectives • 3.1 Mainstream Bluetooth Keyboard Shortcut Keys • 3.2 Review Basic Bluetooth Keyboard Navigation Commands • 3.3 Jiggle & Interacting with App Folders using Bluetooth Keyboarding Commands • Jiggle Mode and Creating an App Folder • Remove App From Folder • Rename Existing App Folder • 3.4 Display the Search Screen, Notification Center and Control Center using Bluetooth Keyboard Commands • Search Screen • Notification Center • Control Center • 3.5 Navigating between Open Apps with Bluetooth Keyboard Commands • 3.6 Speech On/Off • 3.7 Screen Curtain On/Off • 3.8 Siri • 3.9 Keyboard Hints – Additional Bluetooth Keyboard Commands The Bluetooth Keyboard Commands with VoiceOver on the iPad manual is being shared on the Paths to Technology website with permission From SAS Institute Inc. Chapter 3: General Navigation Copyright © 2016 SAS Institute Inc. Cary, NC USA. All Right Reserved. 1 Bluetooth Keyboard Overview This section reviews and expands general navigation – moving around the iPad’s Home screens – using a Bluetooth keyboard. For general navigation, Quick Nav is On. Participants should already be Familiar with navigating the iPad’s Home screens with VoiceOver gestures. It is more eFFicient to use a Bluetooth keyboard rather than the on-screen keyboard. The Bluetooth keyboard can drive the iPad, especially when using the shortcut keyboard commands. Additional Bluetooth keyboard commands, such as moving between open apps and creating folders will also be discussed. All activities in Chapter 3 will have Quick Nav On. Bluetooth Keyboard Recommendation When purchasing a Bluetooth keyboard For your iPad or other iOS devices, make sure that the keyboard has arrow keys so you can use the “Quick Nav” feature with VO. -
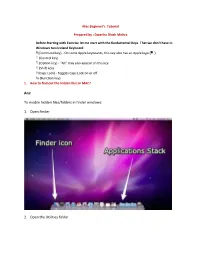
Beginner's Tutorial
Mac Beginner’s Tutorial Prepared by : Dwarika Dhish Mishra Before Starting with Exercise let me start with the fundamental Keys. That we don’t have in Windows two Iceland Keyboard (Command key) - On some Apple keyboards, this key also has an Apple logo ( ) (Control key) (Option key) - "Alt" may also appear on this key (Shift key) (Caps Lock) - Toggles Caps Lock on or off fn (Function key) 1. How to find out the hidden files in MAC? Ans: To enable hidden files/folders in finder windows: 1. Open Finder 2. Open the Utilities folder 3. Open a terminal window 4. Copy and paste the following line in: defaults write com.apple.Finder AppleShowAllFiles YES ( Remember this is case sensitive commands so be careful) 5. Press return 6. Now hold ‘alt’ on the keyboard and right click on the Finder icon 7. Click on Re-launch You should find you will now be able to see any hidden files or folders 8. Once you finish the task then write the above command again on Terminal and Replace YES with NO and return 2. Keyboard Shortcut Ans: Reference 3. Shutdown the OS from terminal command. Ans : 1- Open the finder 2- Go to Application -> Utility 3- Click on Terminal 4- A white window will open {if we write man shutdown then it will show the detail of shutdown options} 5- Write shutdown (for more shutdown options write man shutdown) and enter 6- A pop up window will appear and click on shutdown 4. How to enable right click for mouse? Ans: To configure the right mouse button on the Mighty Mouse, select System Preferences from the Apple menu, and then select Keyboard & Mouse. -

Mac Mini Were Made for Each Other
Congratulations, you and your Mac mini were made for each other. Say hello to your Mac mini. www.apple.com/macmini Finder Mail iCal Browse your files the Manage all your email Keep your schedule in sync. way you browse your accounts in one place. Mac Help music with Cover Flow. Mac Help calendar Mac Help mail finder Mac OS X Snow Leopard www.apple.com/macosx Time Machine Quick Look Spotlight Safari Automatically Instantly preview Find anything Experience the web back up and your files. on your Mac. with the fastest restore your files. Mac Help Mac Help browser in the world. Mac Help quick look spotlight Mac Help time machine safari iLife ’11 www.apple.com/ilife iPhoto iMovie GarageBand Turn your Make a great- Create a great- photos into looking movie sounding song something in minutes. with ease. amazing. iMovie Help GarageBand Help iPhoto Help movie record photos Contents Chapter 1: Ready, Set Up, Go 10 What’s in the Box 11 Setting Up Your Mac mini 18 Putting Your Mac mini to Sleep or Shutting It Down Chapter 2: Life with Your Mac mini 22 What’s on the Front of Your Mac mini 24 What’s on the Back of Your Mac mini 26 Using the Apple Remote 28 Using SD Cards 28 Getting Answers Chapter 3: Boost Your Memory 34 Installing Memory Chapter 4: Problem, Meet Solution 44 Problems That Prevent You from Using Your Mac mini 46 Reinstalling the Software That Came with Your Mac mini 47 Resetting Your Password 48 Using Disk Utility Contents 5 48 Other Problems 50 Using Apple Hardware Test 50 Problems with Your Internet Connection 53 Problems with AirPort -

Use Your Imac As a Display with Target Display Mode
Use your iMac as a display with Target Display Mode support.apple.com/en-us/HT204592 Target Display Mode lets you use the built-in display on a supported iMac as an external display for another Mac. To use your iMac as a display in Target Display Mode, connect it to another Mac using the correct cable (see System Requirements below). Then press Command-F2 on the keyboard connected to your iMac. When you're done, press Command-F2 again. System Requirements You need the following to use Target Display Mode: See the list below for iMac models that support Target Display Mode, the type of cable you need to connect that model of iMac, and the kind of port you need on your other Mac. iMac models you can use Cable Port you need as a display you need on your other Mac iMac (27-inch, Late 2009) Mini DisplayPort to Mini Mini DisplayPort or DisplayPort Thunderbolt iMac (27-inch, Mid 2010) Mini DisplayPort to Mini Mini DisplayPort or DisplayPort Thunderbolt iMac (Mid 2011-Mid 2014) Thunderbolt Thunderbolt 1/4 iMac (Retina 5K, 27-inch, Late 2014) and later iMac models can't be used as Target Display Mode displays. Use Target Display Mode Follow these steps to start using your iMac as a display: 1. Make sure that your iMac is turned on, and the other Mac is logged in to a macOS user account. 2. Connect the Mini DisplayPort or Thunderbolt cable between the two computers. 3. Press Command-F2 on the keyboard of the iMac that you want to use as a display. -

March 2015 Purchasing Cards
Eagle County School District Master Transaction Consolidation Transaction Search - Company UMB, 03/03/2015 to 04/01/2015 Mapped Cards Tran Date Account Company Unit Supplier Narrative Details Amount USD 3/2/2015 XXXX-XXXX-XXXX-0052 AVON ELEMENTARY Wm Supercenter #1199 optical mouses 71.73 3/5/2015 XXXX-XXXX-XXXX-0052 AVON ELEMENTARY Smartsign crossing guard sign 136.00 3/27/2015 XXXX-XXXX-XXXX-0052 AVON ELEMENTARY City-Market #0426 student reward treats 26.94 3/18/2015 XXXX-XXXX-XXXX-0201 AVON ELEMENTARY Wal-Mart #1199 classroom supplies waterclr, paint 66.13 3/18/2015 XXXX-XXXX-XXXX-0326 AVON ELEMENTARY The Home Depot #1525 maint supplies, security camera 85.25 3/27/2015 XXXX-XXXX-XXXX-0326 AVON ELEMENTARY Wal-Mart #1199 break room water filter system 50.94 3/4/2015 XXXX-XXXX-XXXX-0581 AVON ELEMENTARY Wal-Mart #1199 parent teacher conference expense 43.90 3/4/2015 XXXX-XXXX-XXXX-0581 AVON ELEMENTARY Qdoba #0700 parent teacher conferences expense 257.50 3/11/2015 XXXX-XXXX-XXXX-0581 AVON ELEMENTARY Wal-Mart #1199 supplies expos 10.95 3/11/2015 XXXX-XXXX-XXXX-0581 AVON ELEMENTARY Wm Supercenter #1199 supplies 11.57 3/11/2015 XXXX-XXXX-XXXX-0581 AVON ELEMENTARY Wal-Mart #1199 refund on purchase -11.57 3/11/2015 XXXX-XXXX-XXXX-0581 AVON ELEMENTARY Bookworm Of Edwards books for students 111.45 3/20/2015 XXXX-XXXX-XXXX-0581 AVON ELEMENTARY Demco Inc library supplies 76.52 3/18/2015 XXXX-XXXX-XXXX-0920 AVON ELEMENTARY Academic Therapy Publi therapy publications 116.00 3/18/2015 XXXX-XXXX-XXXX-0920 AVON ELEMENTARY Classroom Supply Mart classroom