Beyond Encoding: a Critical Look at the Terminology of Text Graphics
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

UC Santa Barbara UC Santa Barbara Electronic Theses and Dissertations
UC Santa Barbara UC Santa Barbara Electronic Theses and Dissertations Title A Web of Extended Metaphors in the Guerilla Open Access Manifesto of Aaron Swartz Permalink https://escholarship.org/uc/item/6w76f8x7 Author Swift, Kathy Publication Date 2017 Peer reviewed|Thesis/dissertation eScholarship.org Powered by the California Digital Library University of California UNIVERSITY OF CALIFORNIA Santa Barbara A Web of Extended Metaphors in the Guerilla Open Access Manifesto of Aaron Swartz A dissertation submitted in partial satisfaction of the requirements for the degree Doctor of Philosophy in Education by Kathleen Anne Swift Committee in charge: Professor Richard Duran, Chair Professor Diana Arya Professor William Robinson September 2017 The dissertation of Kathleen Anne Swift is approved. ................................................................................................................................ Diana Arya ................................................................................................................................ William Robinson ................................................................................................................................ Richard Duran, Committee Chair June 2017 A Web of Extended Metaphors in the Guerilla Open Access Manifesto of Aaron Swartz Copyright © 2017 by Kathleen Anne Swift iii ACKNOWLEDGEMENTS I would like to thank the members of my committee for their advice and patience as I worked on gathering and analyzing the copious amounts of research necessary to -

Alpha • Bravo • Charlie
ALPHA • BRAVO • CHARLIE Inspired by Alpha, Bravo, Charlie (published by Phaidon) these Perfect activity sheets introduce young people to four different nautical codes. There are messages to decode, questions to answer for curious and some fun facts to share with friends and family. 5-7 year olds FLAG IT UP These bright, colorful flags are known as signal flags. There is one flag for each letter of the alphabet. 1. What is the right-hand side of a ship called? Use the flags to decode the answer! 3. Draw and color the flag that represents the first letter of your name. 2. Draw and color flags to spell out this message: SHIP AHOY SH I P AHOY FUN FACT Each flag also has its own To purchase your copy of meaning when it's flown by 2. Alpha, Bravo, Charlie visit phaidon.com/childrens2016 itself. For example, the N flag by STARBOARD 1. itself means "No" or "Negative". Answers: ALPHA OSCAR KILO The Phonetic alphabet matches every letter with a word so that letters can’t be mixed up and sailors don’t get the wrong message. 1. Write in the missing first letters from these words in the Phonetic alphabet. What word have you spelled out? Write it in here: HINT: The word for things that are transported by ship. 2. Can you decode the answer to this question: What types of cargo did Clipper ships carry in the 1800s? 3. Use the Phonetic alphabet to spell out your first name. FUN FACT The Phonetic alphabet’s full name is the GOLD AND WOOL International Radiotelephony Spelling Alphabet. -
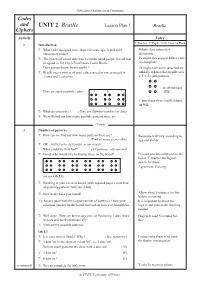
UNIT 2 Braille
Mathematics Enhancement Programme Codes and UNIT 2 Braille Lesson Plan 1 Braille Ciphers Activity Notes T: Teacher P: Pupil Ex.B: Exercise Book 1 Introduction T: What code, designed more than 150 years ago, is still used Whole class interactive extensively today? discussion. T: The system of raised dots which enables blind people to read was Ps might also suggest Morse code designed in 1833 by a Frenchman, Louis Braille. or semaphore. Does anyone know how it works? Ps might have some ideas but are T: Braille uses a system of dots, either raised or not, arranged in unlikely to know that Braille uses 3 rows and 2 columns. a 32× configuration. on whiteboard Here are some possible codes: ape (WB). T puts these three Braille letters on WB. T: What do you notice? (They use different numbers of dots) T: We will find out how many possible patterns there are. 10 mins 2 Number of patterns T: How can we find out how many patterns there are? Response will vary according to (Find as many as possible) age and ability. T: OK – but let us be systematic in our search. What could we first find? (All patterns with one dot) T: Good; who would like to display these on the board? P(s) put possible solutions on the board; T stresses the logical search for these. Agreement. Praising. (or use OS 2.1) T: Working in your exercise books (with squared paper), now find all possible patterns with just 2 dots. T: How many have you found? Allow about 5 minutes for this before reviewing. -

Unicode/IDN Security Mark Davis President, Unicode Consortium Chief SW Globalization Arch., IBM the Unicode Consortium
Unicode/IDN Security Mark Davis President, Unicode Consortium Chief SW Globalization Arch., IBM The Unicode Consortium Software globalization standards: define properties and behavior for every character in every script Unicode Standard: a unique code for every character Common Locale Data Repository: LDML format plus repository for required locale data Collation, line breaking, regex, charset mapping, … Used by every major modern operating system, browser, office software, email client,… Core of XML, HTML, Java, C#, C (with ICU), Javascript, … Security ~ Identity System A X = x System B X ≠ x IDN You get an email about your paypal.com account, click on the link… You carefully examine your browser's address box to make sure that it is actually going to http://paypal.com/ … But actually it is going to a spoof site: “paypal.com” with the Cyrillic letter “p”. You (System A) think that they are the same DNS (System B) thinks they are different Examples: Letters Cross-Script p in Latin vs p in Cyrillic In-Script Sequences rn may appear at display sizes like m ! + ा typically looks identical to # so̷s looks like søs Rendering Support ä with two umlauts may look the same as ä with one el is actually e + l Examples: Numbers Western 0 1 2 3 4 5 6 7 8 9 Bengali ৺৺৺৺৺৺৺৺৺৺ Oriya ୱୱୱୱୱୱୱୱୱୱ Thus ৺ୱ = 42 Syntax Spoofing http://example.org/1234/not.mydomain.com http://example.org/1234/not.mydomain.com / = fraction-slash Also possible without Unicode: http://example.org--long-and-obscure-list-of- characters.mydomain.com UTR -

Network Working Group D. Goldsmith Request for Comments: 1641 M
Network Working Group D. Goldsmith Request for Comments: 1641 M. Davis Category: Experimental Taligent, Inc. July 1994 Using Unicode with MIME Status of this Memo This memo defines an Experimental Protocol for the Internet community. This memo does not specify an Internet standard of any kind. Distribution of this memo is unlimited. Abstract The Unicode Standard, version 1.1, and ISO/IEC 10646-1:1993(E) jointly define a 16 bit character set (hereafter referred to as Unicode) which encompasses most of the world's writing systems. However, Internet mail (STD 11, RFC 822) currently supports only 7- bit US ASCII as a character set. MIME (RFC 1521 and RFC 1522) extends Internet mail to support different media types and character sets, and thus could support Unicode in mail messages. MIME neither defines Unicode as a permitted character set nor specifies how it would be encoded, although it does provide for the registration of additional character sets over time. This document specifies the usage of Unicode within MIME. Motivation Since Unicode is starting to see widespread commercial adoption, users will want a way to transmit information in this character set in mail messages and other Internet media. Since MIME was expressly designed to allow such extensions and is on the standards track for the Internet, it is the most appropriate means for encoding Unicode. RFC 1521 and RFC 1522 do not define Unicode as an allowed character set, but allow registration of additional character sets. In addition to allowing use of Unicode within MIME bodies, another goal is to specify a way of using Unicode that allows text which consists largely, but not entirely, of US-ASCII characters to be represented in a way that can be read by mail clients who do not understand Unicode. -

Negotiating Ludic Normativity in Facebook Meme Pages
in ilburg apers ulture tudies 247 T P C S Negotiating Ludic Normativity in Facebook Meme Pages by Ondřej Procházka Tilburg University [email protected] December 2020 This work is licensed under a Creative Commons Attribution-NoDerivatives 4.0 International License. To view a copy of this license, visit http://creativecommons.org/licenses/by-nd/4.0/ Negotiating ludic normativity in Facebook meme pages Negotiating ludic normativity in Facebook meme pages PROEFSCHRIFT ter verkrijging van de graad van doctor aan Tilburg University, op gezag van de rector magnificus, prof. dr. W.B.H.J. van de Donk, in het openbaar te verdedigen ten overstaan van een door het college voor promoties aangewezen commissie in de Portrettenzaal van de Universiteit op maandag 7 december 2020 om 16.00 uur door Ondřej Procházka geboren te Kyjov, Tsjechië Promotores: prof. J.M.E. Blommaert prof. A.M. Backus Copromotor: dr. P.K. Varis Overige leden van de promotiecommissie: prof. A. Georgakopoulou prof. A. Jaworski prof. A.P.C. Swanenberg dr. R. Moore dr. T. Van Hout ISBN 978-94-6416-307-0 Cover design by Veronika Voglová Layout and editing by Karin Berkhout, Department of Culture Studies, Tilburg University Printed by Ridderprint BV, the Netherlands © Ondřej Procházka, 2020 The back cover contains a graphic reinterpretation of the material from the ‘Faceblock’ article posted by user ‘Taha Banoglu’ on the Polandball wiki and is licensed under the Creative Commons Attribution- Share Alike License. All rights reserved. No other parts of this publication may be reproduced, stored in a retrieval system, or transmitted, in any form or by any other means, electronic, mechanical, photocopying, recording, or otherwise, without permission of the author. -

Multimedia Data and Its Encoding
Lecture 14 Multimedia Data and Its Encoding M. Adnan Quaium Assistant Professor Department of Electrical and Electronic Engineering Ahsanullah University of Science and Technology Room – 4A07 Email – [email protected] URL- http://adnan.quaium.com/aust/cse4295 CSE 4295 : Multimedia Communication prepared by M. Adnan Quaium 1 Text Encoding The character by character encoding of an alphabet is called encryption. As a rule, this coding must be reversible – the reverse encoding known as decoding or decryption. Examples for a simple encryption are the international phonetic alphabet or Braille script CSE 4295 : Multimedia Communication prepared by M. Adnan Quaium 2 Text Encoding CSE 4295 : Multimedia Communication prepared by M. Adnan Quaium 3 Morse Code Samuel F. B. Morse and Alfred Vail used a form of binary encoding, i.e., all text characters were encoded in a series of two basic characters. The two basic characters – a dot and a dash – were short and long raised impressions marked on a running paper tape. Word borders are indicated by breaks. CSE 4295 : Multimedia Communication prepared by M. Adnan Quaium 4 Morse Code ● To achieve the most efficient encoding of the transmitted text messages, Morse and Vail implemented their observation that specific letters came up more frequently in the (English) language than others. ● The obvious conclusion was to select a shorter encoding for frequently used characters and a longer one for letters that are used seldom. CSE 4295 : Multimedia Communication prepared by M. Adnan Quaium 5 7 bit ASCII code CSE 4295 : Multimedia Communication prepared by M. Adnan Quaium 6 Unicode Standard ● The Unicode standard assigns a number (code point) and a name to each character, instead of the usual glyph. -

Mad-Assembler 1.8.5 Thebe / Madteam
MadAssembler 1.8.5 Thebe / Madteam (02/21/2009) INTRODUCTION Introduction Compilation Differences and similarities between XASM and MADS Similarities The differences and opportunities DIRECTIONS Switch assembly Exit codes File structure. LST File structure. LAB File structure. H Sparta DOS X Construction of Sparta DOS XFiles, Atari DOS Programming Sparta DOS X Mnemonics 6502 65816 DETECTION CPU MEMORY BANKS Virtual Hardware CODE RELOKOWALNY Block relokowalny External Symbols Public Symbols Linking TYPES Structural Declaration of a structured type Defining the structural data Enumerated Enumerated type declaration Defining the enumeration data HISTORY SYNOPSIS Comments Combining multiple rows into one row Combining multiple mnemonics Expressions Numbers Operators Labels Local Global Temporary Local style MAE Control assemble Change options assemble Conditional assembling Interrupt assemble Assembling at zero Macro commands Pseudo orders Defining block SDX Defining the symbol SDX Defining data Directive Defining replicates (. REPT) Defining the symbol SDX (. SYMBOL) Directive generating code 6502 Define iterations (# WHILE) Define the decision (# IF) Tables Array declaration Macros Declaration Macros Calling macros Procedures The declaration procedure Procedure call Parameters of the procedure Local Area Declaration of local area INTRODUCTION Introduction MadAssembler (MADS) is a 32 bit application, written in Delphi. Most assemblers written in C, so in order not to repeat I have used Delphi and 7.0). The assumption of MADS is addressed to users QA XASM, FA. QA has been borrowed f rom the syntax of XASM some macro commands and syntax changes in FA handling syn tax Sparta DOS X (SDX). Has made possible the use of additional characters in th e names of labels. -

Fast Rendering of Image Mosaics and ASCII Art
Volume 0 (1981), Number 0 pp. 1–11 COMPUTER GRAPHICS forum Fast Rendering of Image Mosaics and ASCII Art Nenad Markuš1, Marco Fratarcangeli2, Igor S. Pandžic´1 and Jörgen Ahlberg3 1University of Zagreb, Faculty of Electrical Engineering and Computing, Unska 3, 10000 Zagreb, Croatia 2Chalmers University of Technology, Dept. of Applied IT, Kuggen, Lindholmsplatsen 1, SE-412 96 Göteborg, Sweden 3Linköping University, Dept. of Electrical Engineering, Information Coding Group, SE-581 83 Linköping, Sweden [email protected], [email protected], [email protected], [email protected] __/[(\;r'!IfJtLL3i}7/_\\r[((}j11](j3ltlljj{7j]_j_\3nu&j__\_!/\/_|_(_,_7&Url37r|v/=<>_ ___<|\;"__3fJtCv3C<>__<|r]c7r71]](j3jtCljjC7js_[<r3vu&r__\_=^=\<{_|_,.<wfJjv()>/__7\_ __{_}="__<4@nYl03jrr><<\_\7?csC*(j33tJo~C7Cj[*C_(c/lVTfr_^^^^<!_</(\_,`3ULt**)|<~=_ay \>r_}!"__<IFfYCJ3jC|><<\)77>csC*Cj33Jjov7oCr7<j}rc7lVTn>_^^^^~!_</(\_,`3ano**]<<\=_uy )r+|>"~_~\4FfGvtJCr{/{/<_ss(r]vCCoLjLLjtj_j*jjscrs*jJT@j_-`:__=/\<<}],-"Ij0isc_=_jyQd _\__r"~_~\3kfLovJjr\<||>rs*_j(jv*vCjLtjtj(j7jjr]r]*jJT@j!-.-_^__\</<C,,`YYjii]\=_jmdd >\=="_!=`(5PfJ*tj*r_|<\<s(*j*ivjcIVuaGjujvCos*{j(r(3vaAjr__-;_;~=\><7r,."YLjjr/_aED^k !_=="__="/4PfJotjvrr<r(rsj*j*ivj*JeneIYjjvrss*rj7r13jaAtr__~;~__=/\<3i,.^vLjjr>_x#E%k ^;"___+_r<4Pfv0tvCrvrrc<*1(_C*ijoLI9AaTazjjovj*ri}i3evTjr____~_=_\\]j3r,~`YejrjdbUU%b !_^"_____\4yfLYtllr_rrr[*7*jCjjjvLYfAaT&Ljjjji*rr*r3vefjr__;__!=_+/_*vr,``YLjrj#bUx%m _="_jr-^,\5kaf<r3rr[/\r/r](Cv\jv*77?\""_/7vLjjj_sjCo3n$tr<\_==!___/_3li_,`^v\xm#Ujqmb "="_jr~^_\3khYj*v_*|)r<r77*vvjjt*777\^:_^7vLtjjc*iCvYuAtr<>_==r___sj3vi_,`^0jxK#UhhmE -

Display Programming Guide
Serial text [Data] display Programming Guide [ Version 3.4 Firmware ] Issue 7 22 July 2014 This guide applies to the following models: BA488C - Panel mounted, Intrinsically Safe BA484D - Field mounted, Intrinsically Safe BA688C - Panel mounted, Safe Area BA684D - Field mounted, Safe Area Contents Introduction........................................................................................................................................................................1 What’s in this Programming Guide..............................................................................................................................1 What’s in the Instruction Manuals...............................................................................................................................1 What’s in the Modbus Interface Guide.........................................................................................................................1 Other sources of information........................................................................................................................................1 Enhanced Features........................................................................................................................................................2 Instrument Features...........................................................................................................................................................3 Display............................................................................................................................................................................3 -

Unicode Compression: Does Size Really Matter? TR CS-2002-11
Unicode Compression: Does Size Really Matter? TR CS-2002-11 Steve Atkin IBM Globalization Center of Competency International Business Machines Austin, Texas USA 78758 [email protected] Ryan Stansifer Department of Computer Sciences Florida Institute of Technology Melbourne, Florida USA 32901 [email protected] July 2003 Abstract The Unicode standard provides several algorithms, techniques, and strategies for assigning, transmitting, and compressing Unicode characters. These techniques allow Unicode data to be represented in a concise format in several contexts. In this paper we examine several techniques and strategies for compressing Unicode data using the programs gzip and bzip. Unicode compression algorithms known as SCSU and BOCU are also examined. As far as size is concerned, algorithms designed specifically for Unicode may not be necessary. 1 Introduction Characters these days are more than one 8-bit byte. Hence, many are concerned about the space text files use, even in an age of cheap storage. Will storing and transmitting Unicode [18] take a lot more space? In this paper we ask how compression affects Unicode and how Unicode affects compression. 1 Unicode is used to encode natural-language text as opposed to programs or binary data. Just what is natural-language text? The question seems simple, yet there are complications. In the information age we are accustomed to discretization of all kinds: music with, for instance, MP3; and pictures with, for instance, JPG. Also, a vast amount of text is stored and transmitted digitally. Yet discretizing text is not generally considered much of a problem. This may be because the En- glish language, western society, and computer technology all evolved relatively smoothly together. -

User Manual Contents
USER MANUAL CONTENTS WELCOME TO ATTACK OF THE PETSCII ROBOTS.......................................................................................3 COMMODORE PET..................................................................................................................................5 COMMODORE 64...................................................................................................................................6 GRAPHIC MODES ON C64.......................................................................................................................7 COMMODORE VIC 20..............................................................................................................................8 USING A SUPER NINTENDO CONTROLLER................................................................................................9 COMPARISON OF GRAPHIC MODES........................................................................................................10 HOW TO PLAY......................................................................................................................................12 TROUBLE SHOOTING............................................................................................................................12 SEARCHING FOR ITEMS.........................................................................................................................14 WEAPONS AND ITEMS..........................................................................................................................15