Readme for Clamtk
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Resurrect Your Old PC
Resurrect your old PCs Resurrect your old PC Nostalgic for your old beige boxes? Don’t let them gather dust! Proprietary OSes force users to upgrade hardware much sooner than necessary: Neil Bothwick highlights some great ways to make your pensioned-off PCs earn their keep. ardware performance is constantly improving, and it is only natural to want the best, so we upgrade our H system from time to time and leave the old ones behind, considering them obsolete. But you don’t usually need the latest and greatest, it was only a few years ago that people were running perfectly usable systems on 500MHz CPUs and drooling over the prospect that a 1GHz CPU might actually be available quite soon. I can imagine someone writing a similar article, ten years from now, about what to do with that slow, old 4GHz eight-core system that is now gathering dust. That’s what we aim to do here, show you how you can put that old hardware to good use instead of consigning it to the scrapheap. So what are we talking about when we say older computers? The sort of spec that was popular around the turn of the century. OK, while that may be true, it does make it seem like we are talking about really old hardware. A typical entry-level machine from six or seven years ago would have had something like an 800MHz processor, Pentium 3 or similar, 128MB of RAM and a 20- 30GB hard disk. The test rig used for testing most of the software we will discuss is actually slightly lower spec, it has a 700MHz Celeron processor, because that’s what I found in the pile of computer gear I never throw away in my loft, right next to my faithful old – but non-functioning – Amiga 4000. -
Android Euskaraz Windows Euskaraz Android Erderaz Windows Erderaz GNU/LINUX Sistema Eragilea Euskeraz Ubuntu Euskaraz We
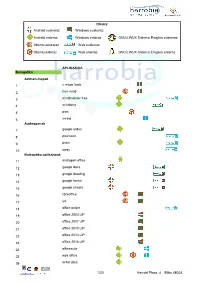
Oharra: Android euskaraz Windows euskaraz Android erderaz Windows erderaz GNU/LINUX Sistema Eragilea euskeraz Ubuntu euskaraz Web euskaraz Ubuntu erderaz Web erderaz GNU/LINUX Sistema Eragilea erderaz APLIKAZIOA Bulegotika Adimen-mapak 1 c maps tools 2 free mind 3 mindmeister free 4 mindomo 5 plan 6 xmind Aurkezpenak 7 google slides 8 pow toon 9 prezi 10 sway Bulegotika-aplikazioak 11 andropen office 12 google docs 13 google drawing 14 google forms 15 google sheets 16 libreoffice 17 lyx 18 office online 19 office 2003 LIP 20 office 2007 LIP 21 office 2010 LIP 22 office 2013 LIP 23 office 2016 LIP 24 officesuite 25 wps office 26 writer plus 1/20 Harrobi Plaza, 4 Bilbo 48003 CAD 27 draftsight 28 librecad 29 qcad 30 sweet home 31 timkercad Datu-baseak 32 appserv 33 dbdesigner 34 emma 35 firebird 36 grubba 37 kexi 38 mysql server 39 mysql workbench 40 postgresql 41 tora Diagramak 42 dia 43 smartdraw Galdetegiak 44 kahoot Maketazioa 45 scribus PDF editoreak 46 master pdf editor 47 pdfedit pdf escape 48 xournal PDF irakurgailuak 49 adobe reader 50 evince 51 foxit reader 52 sumatraPDF 2/20 Harrobi Plaza, 4 Bilbo 48003 Hezkuntza Aditzak lantzeko 53 aditzariketak.wordpress 54 aditz laguntzailea 55 aditzak 56 aditzak.com 57 aditzapp 58 adizkitegia 59 deklinabidea 60 euskaljakintza 61 euskera! 62 hitano 63 ikusi eta ikasi 64 ikusi eta ikasi bi! Apunteak partekatu 65 flashcard machine 66 goconqr 67 quizlet 68 rincon del vago Diktaketak 69 dictation Entziklopediak 70 auñamendi eusko entziklopedia 71 elhuyar zth hiztegi entziklopedikoa 72 harluxet 73 lur entziklopedia tematikoa 74 lur hiztegi entziklopedikoa 75 wikipedia Esamoldeak 76 AEK euskara praktikoa 77 esamoldeapp 78 Ikapp-zaharrak berri Estatistikak 79 pspp 80 r 3/20 Harrobi Plaza, 4 Bilbo 48003 Euskara azterketak 81 ega app 82 egabai 83 euskal jakintza 84 euskara ikasiz 1. -

Managing a World of Things: a Report on APNOMS2017
Managing a World of Things: A Report on APNOMS2017 Myung-Sup Kim, Haruo Oishi, Jiun- Long Huang, Hongtaek Ju, Kiyohito Yoshihara, Chih-Wei Yi & Taesang Choi Journal of Network and Systems Management ISSN 1064-7570 J Netw Syst Manage DOI 10.1007/s10922-018-9472-1 1 23 Your article is protected by copyright and all rights are held exclusively by Springer Science+Business Media, LLC, part of Springer Nature. This e-offprint is for personal use only and shall not be self-archived in electronic repositories. If you wish to self- archive your article, please use the accepted manuscript version for posting on your own website. You may further deposit the accepted manuscript version in any repository, provided it is only made publicly available 12 months after official publication or later and provided acknowledgement is given to the original source of publication and a link is inserted to the published article on Springer's website. The link must be accompanied by the following text: "The final publication is available at link.springer.com”. 1 23 Author's personal copy Journal of Network and Systems Management https://doi.org/10.1007/s10922-018-9472-1 REPORT Managing a World of Things: A Report on APNOMS2017 Myung‑Sup Kim1 · Haruo Oishi2 · Jiun‑Long Huang3 · Hongtaek Ju4 · Kiyohito Yoshihara5 · Chih‑Wei Yi3 · Taesang Choi6 Received: 19 October 2017 / Revised: 12 August 2018 / Accepted: 17 August 2018 © Springer Science+Business Media, LLC, part of Springer Nature 2018 Abstract This article presents a report on APNOMS2017, which was held on Sept. 27–29, 2017 in Seoul, Korea. -

Journal Volume 32 – 2008
Issues in Religion and Psychotherapy Journal of the Association of Mormon Counselors & Psychotherapists 2008 volume 32 Issues in Religion and Psychotherapy Editor Rachel E. Crook Lyon, PhD Brigham Young University Associate Editor John M. Rector, PhD Brigham Young University–Idaho Lane Fischer, PhD Brigham Young University Consulting Editor Sharon J. Black, MA Brigham Young University Editorial Board Victor B. Cline, PhD S. Brent Scharman, PhD Salt Lake City, Utah LDS Family Services Susan L. Ericksen, RN, MS, LMFT Russ Seigenberg, PhD Utah State University Logan, Utah Melissa K. Goates Jones, PhD Thomas D. Sevy, MSW Brigham Young University Taylorsville, Utah Michael D. Howard, EdD Marilyn J. Simpson, PsyD Jacksonville, North Carolina Pepperdine University Timothy B. Smith, PhD Ronald W. Jacques, EdD Brigham Young University Brigham Young University–Idaho Ian S. Kellems, PhD Esben S. Strodl, PhD West Virginia University Queensland University of Technology P. Scott Richards, PhD Wendy Ulrich, PhD Brigham Young University Alpine, Utah Assistant to the Editor Candilyn Newell, BA Brigham Young University Issues in Religion and Psychotherapy is published biannually by the Association of Mormon Counselors and Psychotherapists and is archived at http://www.amcap.net. Subscription prices are $35.00 per year for members (paid as part of Association dues). Single issues are available for $20.00. Subscriptions and changes of address should be sent to: AMCAP, AMCAP P.O. Box 225 Kaysville, UT 84037 or email [email protected]. Periodical postage paid at Salt Lake City, Utah, and additional entries. Contributors need not be members of the Association of Mormon Counselors and Psychotherapists. All manuscripts, books for review, and other editorial matter should be sent to: Rachel E. -

Antivirus Software Before It Can Detect Them
Computer virus A computer virus is a computer program that can copy itself and infect a computer without the permission or knowledge of the owner. The term "virus" is also commonly but erroneously used to refer to other types of malware, adware, and spyware programs that do not have the reproductive ability. A true virus can only spread from one computer to another (in some form of executable code) when its host is taken to the target computer; for instance because a user sent it over a network or the Internet, or carried it on a removable medium such as a floppy disk, CD, DVD, or USB drive. Viruses can increase their chances of spreading to other computers by infecting files on a network file system or a file system that is accessed by another computer.[1][2] The term "computer virus" is sometimes used as a catch-all phrase to include all types of malware. Malware includes computer viruses, worms, trojan horses, most rootkits, spyware, dishonest adware, crimeware, and other malicious and unwanted software), including true viruses. Viruses are sometimes confused with computer worms and Trojan horses, which are technically different. A worm can exploit security vulnerabilities to spread itself to other computers without needing to be transferred as part of a host, and a Trojan horse is a program that appears harmless but has a hidden agenda. Worms and Trojans, like viruses, may cause harm to either a computer system's hosted data, functional performance, or networking throughput, when they are executed. Some viruses and other malware have symptoms noticeable to the computer user, but many are surreptitious. -
Serious Games Advergaming, Edugaming, Training and More
Serious games Advergaming, edugaming, training and more Project manager Laurent Michaud [email protected] M83708 – June 2008 Author Julian Alvarez, PhD Science of Communication and Information Contributor Laurent Michaud, Head of the digital leisure division Copyright IDATE 2008, BP 4167, 34092 Montpellier Cedex 5, France Tous droits réservés – Toute reproduction, stockage All rights reserved. None of the contents of this ou diffusion, même partiel et par tous moyens, y publication may be reproduced, stored in a retrieval compris électroniques, ne peut être effectué sans system or transmitted in any form, including accord écrit préalable de l'IDATE. electronically, without the prior written permission of IDATE. ISBN 978-2-84822-169-4 Executive Summary Serious Games Advergaming, edugaming, training and more This study outlines the characteristics, uses and different genres of serious game. It examines the challenges involved in the design, development and distribution of various types of titles, while analysing the outlook for the industry and its growth drivers. 600 million to one billion potential Defining serious gaming Areas addressed users worldwide. There is a huge variety of ways to classify Today, serious games are employed in a At the end of 2007, the global video serious gaming. However, accepting the wide variety of sectors. game industry was worth 30 billion ambiguities and possible challenges in- Defence: one of the most important USD. At the same time, the serious herent in this, this study defines serious areas in terms of client investment and gaming market was estimated to be gaming as follows: orders. Serious games are also used by worth between 1.5 and 10+ billion The purpose of a serious game is to armies in Europe, though less widely than USD. -

Fedora 14 User Guide
Fedora 14 User Guide Using Fedora 14 for common desktop computing tasks Fedora Documentation Project User Guide Fedora 14 User Guide Using Fedora 14 for common desktop computing tasks Edition 1.0 Author Fedora Documentation Project [email protected] Copyright © 2010 Red Hat, Inc. and others. The text of and illustrations in this document are licensed by Red Hat under a Creative Commons Attribution–Share Alike 3.0 Unported license ("CC-BY-SA"). An explanation of CC-BY-SA is available at http://creativecommons.org/licenses/by-sa/3.0/. The original authors of this document, and Red Hat, designate the Fedora Project as the "Attribution Party" for purposes of CC-BY-SA. In accordance with CC-BY-SA, if you distribute this document or an adaptation of it, you must provide the URL for the original version. Red Hat, as the licensor of this document, waives the right to enforce, and agrees not to assert, Section 4d of CC-BY-SA to the fullest extent permitted by applicable law. Red Hat, Red Hat Enterprise Linux, the Shadowman logo, JBoss, MetaMatrix, Fedora, the Infinity Logo, and RHCE are trademarks of Red Hat, Inc., registered in the United States and other countries. For guidelines on the permitted uses of the Fedora trademarks, refer to https://fedoraproject.org/wiki/ Legal:Trademark_guidelines. Linux® is the registered trademark of Linus Torvalds in the United States and other countries. Java® is a registered trademark of Oracle and/or its affiliates. XFS® is a trademark of Silicon Graphics International Corp. or its subsidiaries in the United States and/or other countries. -

Official User's Guide
Official User Guide Linux Mint 18 Cinnamon Edition Page 1 of 52 Table of Contents INTRODUCTION TO LINUX MINT ......................................................................................... 4 HISTORY............................................................................................................................................4 PURPOSE...........................................................................................................................................4 VERSION NUMBERS AND CODENAMES.....................................................................................................5 EDITIONS...........................................................................................................................................6 WHERE TO FIND HELP.........................................................................................................................6 INSTALLATION OF LINUX MINT ........................................................................................... 8 DOWNLOAD THE ISO.........................................................................................................................8 VIA TORRENT...................................................................................................................................9 Install a Torrent client...............................................................................................................9 Download the Torrent file.........................................................................................................9 -

Linux Security Review 2015
Linux Security Review 2015 www.av-comparatives.org AV-Comparatives Linux Security Review Language: English May 2015 Last revision: 26 th May 2015 www.av-comparatives.org -1- Linux Security Review 2015 www.av-comparatives.org Contents Introduction ....................................................................................................................... 3 Reviewed products ............................................................................................................... 4 Malware for Linux systems ..................................................................................................... 5 Linux security advice ............................................................................................................ 6 Items covered in the review .................................................................................................. 7 Avast File Server Security ...................................................................................................... 8 AVG Free Edition for Linux.................................................................................................... 11 Bitdefender Antivirus Scanner for Unices ................................................................................ 13 Clam Antivirus for Linux ....................................................................................................... 17 Comodo Antivirus for Linux .................................................................................................. 20 Dr.Web Anti-virus for -

Xfce: the Missing Manual Documentation Release 0.1
Xfce: The Missing Manual Documentation Release 0.1 Joji Antony Jun 18, 2017 Contents 1 What is Xfce? 3 2 Why not use other lightweight environments ?5 3 What is your point? 7 4 Caveats of this document 9 5 How to install Xfce? 11 5.1 Linux................................................... 11 5.2 Installing Xfce on FreeBSD....................................... 21 5.3 Installing Xfce 4.12 on NetBSD..................................... 21 6 Components of Xfce 23 6.1 Xfce4 Settings Manager......................................... 23 6.2 Xfce Panel................................................ 23 6.3 Xfdesktop................................................ 24 6.4 Xfwm4.................................................. 24 6.5 Thunar.................................................. 24 7 Some goodies available with Xfce 25 7.1 Xfce Terminal Emulator......................................... 25 7.2 Mousepad................................................ 25 8 Using your keyboard shortcuts wisely 27 9 Scrolling 29 10 Indices and tables 31 i ii Xfce: The Missing Manual Documentation, Release 0.1 This is an unofficial user manual for Xfce, the lightweight desktop environment. This document is not meant to be comprehensive, and only attempts to cover the basics to get you up and running. Contents Contents 1 Xfce: The Missing Manual Documentation, Release 0.1 2 Contents CHAPTER 1 What is Xfce? Xfce is a lightweight desktop environment built for simplicity and efficiency. Xfce takes up far less space than other desktop environments such as KDE, GNOME, Unity etc and is very responsive. Xfce philosophy is to get out of your way and let you complete your work efficiently and easily. Xfce project has a high emphasis on stability meaning that core functionality does not change frequently causing you to re-learn your workflow. 3 Xfce: The Missing Manual Documentation, Release 0.1 4 Chapter 1. -

COMPLETE GUIDE to INSTALL UBUNTU LINUX with OPENBOX Ubuntuopenbox.Com/Udemy
UbuntuOpenbox.com Copyright © 2016 by Dat H. Nguyen UDEMY COURSE MATERIAL COMPLETE GUIDE TO INSTALL UBUNTU LINUX WITH OPENBOX UbuntuOpenbox.com/udemy Section 3 – Install Ubuntu Operating System 1. Repositories: A repository is a server storing packages that are suitable to be installed right away (packages as well as all of their dependencies) /etc/apt/source.list file will have a list of repository addresses. *PPA: A Personal Package Archives (PPA) is a repository maintained by an individual or an independent group; as oppose to the official repository maintained by Ubuntu. 2. Update apt information (from source.list file) sudo apt-get update It will go to the addresses listed in the /apt/etc/source.list file and update the information about what are on there (which packages are on there) and what have been changed (what the current packages’ versions are). You need to execute this command whenever you want to install any package. 3. Install packages sudo apt-get install [packages' name] For example: sudo apt-get install firefox openbox will install both firefox and openbox at the same time. 4. Remove packages sudo apt-get remove firefox * remove packages and all their configuration file. sudo apt-get remove --purge firefox 5. nano to edit text file sudo nano /directory/to/text/file Navigate through the text file using up/down/left/right keys. * shortcut keys: “Ctrl + X” to exit nano, “Y” to save and “N” to abort the saving. Section 4 – Install Openbox And Configure It Last updated in February, 2016 1 of 7 UbuntuOpenbox.com Copyright © 2016 by Dat H. -

Software Libre Y Educación: Guadalinex (Debian)
Software Libre y Educacion:´ Guadalinex (Debian) y aplicaciones didacticas´ M´as software educativo para Guadalinex Juan Alonso - Ferm´ın Rubio - Paco Villegas 22 de mayo de 2005 ´Indice general 1. Instalaci´on de programas 5 1.1. Instalaci´ona partir del c´odigo fuente. 5 1.2. Instalaci´ona partir de binarios . 8 1.3. En formato Debian . 9 2. Textos 12 2.1. Ficheros en formato dvi, ps y pdf. 12 2.1.1. Formato dvi . 12 2.1.2. Formato PostScript . 13 2.1.3. Formato pdf . 14 2.2. LATEX........................................... 17 2.2.1. Segmentaci´onsil´abica (hypenation) . 17 2.2.2. Comencemos . 18 2.2.3. Utilidades para LateX . 21 2.2.4. LATEX2Html . 26 2.3. LYX............................................ 27 2.3.1. Introducci´on . 27 2.3.2. Instalaci´onde LYX................................ 29 2.3.3. Comenzamos . 29 2.3.4. Notas y Referencias . 40 2.3.5. Tablas, figuras y flotantes . 45 2.3.6. Dando formato final al documento . 54 2.3.7. Modo matem´atico . 56 2.3.8. Minip´aginas . 68 2.3.9. Exportar a HTML: LATEX2HTML . 70 2.4. Otros ........................................... 71 2.4.1. Abiword . 71 2.4.2. Vi no, gvim . 72 3. Gr´aficos. v´ıdeo y sonido 74 3.1. Image Magick . 74 3.2. xfig............................................. 76 3.3. Qcad............................................ 78 3.4. Blender . 79 3.5. Sodipodi.......................................... 80 3.6. Visor gr´afico GQview . 82 3.7. Xine............................................ 83 3.8. Kino............................................ 85 3.9. Audacity . 87 1 Thales-CICA 2005 ´INDICE GENERAL P´agina 2 4.