Dissertation Final May 2012
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

13 Jean A. Cholka Joined Us in January 1999 As Vice President
Jean A. Cholka joined us in January 1999 as Vice President—Human Resources and served as Vice President—Delivery from October 2000 to April 2001, President—Kanbay North America from April 2001 to January 2003,Vice President—Global Client Management from January 2003 to January 2005 and Executive Vice President—Marketing, Sales and Strategy from January 2005 to November 2005. Since November 2005, Ms. Cholka has served as Chief People Officer. Cyprian D’Souza, see the section of this proxy statement entitled “Board of Directors—Board Structure and Composition.” Roy K. Stansbury joined us in 1994 as Executive Vice President and was responsible for our North American delivery organization from January 1998 to August 2000. Mr. Stansbury has managed our relationships with HSBC and Morgan Stanley since September 2000 and in January 2005 assumed the role of ExecutiveVice President—Global HSBC Services. In March 2006, Mr. Stansbury was appointed Executive Vice President—Global Client Services. Prior to joining us, Mr. Stansbury was employed by Dupont Asia Pacific from 1986 to 1994, where he was responsible for high-performance work systems. Aparna U. Katre joined us in 1996 as Projects Manager and served as General Manager—Delivery from 1998 to 2000. Ms. Katre served as Vice President and Chief Process Officer from April 2001 to December 2004. Since January 2005, Ms. Katre has served as Executive Vice President—Global Business Innovation. Laurence M. Gordon joined us in November 2005 as Executive Vice President—Global Sales and Marketing.Prior to joining us, Mr. Gordon served as Vice President of Global Marketing at Cognizant Technology Solutions from 1999 to 2005. -
2021 List of Attendees As of 08/26/21
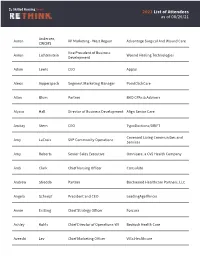
2021 List of Attendees as of 08/26/21 Andersen, Aaron VP Marketing - West Region Advantage Surgical And Wound Care CWCMS Vice President of Business Aaron Lichtenstein Wound Healing Technologies Development Adam Lewis CEO Apploi Alexis Aipperspach Segment Marketing Manager PointClickCare Allan Blum Partner BKD CPAs & Advisors Alyssa Hall Director of Business Development Align Senior Care Amitay Stern CEO TypoDuctions/DRIFT Covenant Living Communities and Amy LaCroix SVP Community Operations Services Amy Roberts Senior Sales Executive Omnicare, a CVS Health Company Andi Clark Chief Nursing Officer Consulate Andrew Sfreddo Partner Birchwood Healthcare Partners, LLC Angela Schnepf President and CEO LeadingAge Illinois Annie Erstling Chief Strategy Officer Forcura Ashley Kohls Chief Director of Operations-WI Bedrock Health Care Aveeshi Lev Chief Marketing Officer Villa Healthcare 2021 List of Attendees as of 08/26/21 Barry Carr Manager Ignite Medical Resorts BEN VOLPE Vice President SABER HEALTHCARE Bill Chase VP of Business Development Monarch Healthcare Management Bill Weisberg President Saber Healthcare Bob Ratini Market Vice President Optum Boris Sheynin Vice President Gericare Associates, SC Brandy Gregory Regional Nurse Consultant BRIA Health Services Senior Vice President - Brent Holman-Gomez Originations/Operations/Asset Cambridge Realty Capital Companies Management Brian Carrillo Senior Director, Sales Apploi Brian Cloch CEO Transitional Care Management Brian Wallace Founder NowSourcing Senior Director, Corporate Caleb Hemmer American Health Partners Development Carolyn Swiger VP Marketing - East Region Advantage Surgical & Wound Care Executive Vice President, Business Cathy Fratello SAIVA Development Chaim Mandelbaum CEO Beacon Healthcare Group 2021 List of Attendees as of 08/26/21 Chanda Robson VP OF REIMBURSEMENT SABER HEALTHCARE Cheryl Crooks Sr. -

Denis G. Hamilton, Ph.D. 100 Rockafeller Road Room 2142 Piscataway, NJ 08854 [email protected]
Denis G. Hamilton, Ph.D. 100 Rockafeller Road Room 2142 Piscataway, NJ 08854 [email protected] ACADEMIC & PROFESSIONAL EXPERIENCE Rutgers University, Rutgers Business School Sep 2009 – Present Department of Management & Global Business, Newark & New Brunswick, NJ Assistant Professor of Professional Practice Director of Management Education – New Brunswick Taught at both undergraduate and MBA level (over 30 courses). Courses include Strategic Management, Business Policy & Strategy, Managing Growing Ventures, International Business, and Introduction to Management Student ratings (4.6 on 5.0 scale) are consistently well above department averages while grading distributions conform with department guidelines for all courses. Developed the department’s unique, large section (400+ students) Introduction to Management course and the Managing Growing Ventures course. Also developed hybrid (partially on-line) versions of Business Policy & Strategy and Introduction to Management courses Winner of Student Governing Board “Best Management Professor” Award - 2014 Winner of Dean’s 2013 Ph.D. student teaching award Research focus areas are business/technology strategy and international business AIG (American International Group, Inc.) May 2007—Feb 2009 Global Headquarters – New York, NY Divisional Senior Vice President, Corporate Operations & Systems AIG Business Process Officer Recruited to AIG through executive search to develop and manage AIG Global Shared Services network for AIG worldwide Operations and to lead global quality initiatives as chief process officer. Leader of Operations Excellence Steering Committees consisting of senior executives from AIG business units. Teams identified core quality improvement focus areas. Responsible for leading design and implementation of these initiatives through the Business Process Office working in collaboration with Business Unit COOs. Built Global Shared Services model to deliver improved quality/efficiency. -

Insights from Commonwealth Bank of Australia
Mechanisms for Creating Successful BPM Governance: Insights from Commonwealth Bank of Australia Wasana Bandara1, John C Merideth2, Angsana Techatassanasoontorn3, Paul Mathiesen1, Dan O’Neill2 1 Information Systems School, Queensland University of Technology, Australia 2 Enterprise Systems, Commonwealth Bank, Australia 3 Faculty of Business, Economics and Law, Auckland University of Technology Abstract. This case comprehensively documents the journey of Commonwealth Bank of Australia’s (CBA) approach to develop effective BPM governance that pene- trates the whole organization. The ‘right’ BPM Governance approach was essen- tial to progress with their enterprise-wide Business Process Management (BPM) efforts. This rich case study of one of the largest banks in the Australian Finance sector demonstrates a range of governance mechanisms taken to achieve effective BPM governance across the organization. Their journey suggests that both verti- cal governance and horizontal coordination mechanisms with a dedicated unit on process excellence are necessary to achieve transformation toward a process-cen- tric organization. The learnings from this case study can be applied by other or- ganizations when designing and executing their BPM governance efforts. Keywords: Business Process Management, governance, process governance, process owners, enterprise-wide, end-to-end processes, case study 1 Introduction Business Process Management (BPM) governance refers to the guiding principles that define roles and responsibilities in decision making (Rosemann & Vom Brocke, 2015). BPM governance often entails various mechanisms including vertical structures used to organize and manage activities as well as lateral relations, processes, and rules for coordinating and control across business process activities (Markus & Jacobson, 2015). It is imperative to recognize that different business process governance mechanisms have advantages and disadvantages. -

Business Process Management and the COO Revolution
February 4, 2014 Extreme Competition Peter Fingar Business Process Management and the COO Revolution This month’s Column is adapted from the book, The COO Revolution: Reinventing Customer-Facing Processes for Moments of Truth: http://www.mkpress.com/COO Did you ever wonder about the replacement for Apple’s legendary CEO, Steve Jobs? It was the COO, Timothy Cook. What? The Chief Operating Officer became the CEO of one of the most profitable companies in history? Cook joined Apple in 1998, and is credited with pulling Apple out of manufacturing by closing factories and warehouses around the world. This helped the company reduce inventory levels and streamline its supply chain to match the efficiency of Dell, dramatically increasing margins. Cook has been quoted as saying, “You kind of want to manage it like you’re in the dairy business. If it gets past its freshness date, you have a problem.” Cook exemplifies the new reality of “intelligent business operations” in the customer- driven enterprise that operates in the “now.” Companies need to connect the dots between the COO and the Chief Marketing Officer (CMO) in a way that is unusual and powerful. The primary role of the modern COO should be that of delivering customer experiences that delight! And that’s a true revolution in the role of the COO. While traditional back-office and middle-office functions will certainly not go away, COOs should pivot and also focus on the front office. This expanded role is made possible by advanced business process management technology. This new-found ability to leverage smarter process management can transform your business into a dynamic, real-time, customer-driven enterprise. -

The Role of a Chief Executive Officer
The Role of a Chief Executive Officer An extended look into the role & responsibilities of a CRO Provided by: Contents 1 Chief Revenue Officer Role within the Corporate Hierarchy 1 1.1 Chief revenue officer ......................................... 1 1.1.1 Roles and functions ...................................... 1 1.1.2 The CRO profile ....................................... 1 1.1.3 References .......................................... 2 1.2 Corporate title ............................................. 2 1.2.1 Variations ........................................... 2 1.2.2 Corporate titles ........................................ 4 1.2.3 See also ............................................ 8 1.2.4 References .......................................... 9 1.2.5 External links ......................................... 9 1.3 Senior management .......................................... 9 1.3.1 Positions ........................................... 10 1.3.2 See also ............................................ 11 1.3.3 References .......................................... 11 2 Areas of Responsibility 12 2.1 Revenue ................................................ 12 2.1.1 Business revenue ....................................... 12 2.1.2 Government revenue ..................................... 13 2.1.3 Association non-dues revenue ................................. 13 2.1.4 See also ............................................ 13 2.1.5 References .......................................... 13 2.2 Revenue management ........................................ -

“Political Views of Tech People” Methodology
“Political views of tech people” Niels Selling, Institute for Futures Studies [email protected] Methodology Last updated: 2019-09-23 1. Sample selection 1.1. Selection of firms The population consists of the 842 American corporations that appeared at least once between 2007 and 2014 on the Forbes Global 2000 list, an annual ranking of the 2000 largest public enterprises in the world. 2. Data & Operationalization 2.1. Corporations An “AI firm” is defined as a company that primarily operates in the technology sector and, at the same time, is a big player in AI research and development. The stipulation of these two criteria is consistent with the aim of the analysis, which is to study corporations whose AI development is a core activity. For this reason, the definition excludes non-tech corporations that invest heavily in AI R&D, such as General Motors, and tech-firms that are relatively minor players in the AI domain. First, the NAICS classification system was used to determine whether a corporation is a tech firm or not. NAICS codes are constructed to denote varying levels of specificity. The two first digits designate the broadest business sector, the first three the subsector, the first four the industry group, the first five the industry. The full six-digit sequence is the national industry. Table 1 contains a list of the tech relevant NAICS codes. The NAICS codes of firms were collected from Compustat. A company whose primary NAICS code corresponds to any of those listed in Table 1 was classified as a “tech firm.” Table 1: NAICS codes associated with tech firms. -

C10585 Elec AR P01-25 Tp
24 Electrocomponents plc 2 1 3 The Board 1 R A Lawson MA MBA, Non-Executive Chairman 3 J L Hewitt MA FCA MBA, Deputy Chairman and Group Finance Director Bob Lawson, 57, joined as Group Managing Director in April 1991 and Jeff Hewitt, 54, joined as Group Finance Director in November 1996 was the Group Chief Executive from April 1992 until his retirement from Unitech plc where he was Finance Director. He joined Unitech in in July 2001 when he was appointed Chairman Designate. He held 1991 from Coats Viyella plc where he was Group Strategy Director this position until his appointment as Non-Executive Chairman in and a Divisional Chairman. He has worked for The Boston Consulting November 2001. He is a qualified engineer with a business degree Group and Arthur Andersen & Co. He is also a Non-Executive Director and has worked in several United Kingdom and continental groups. of The Roxboro Group plc. He was Sales Director of RS Components Limited from 1979 to 1987 (Chairman of the Treasury Committee)(b)(c) and then spent five years as Managing Director of Vitec Group plc. He is Non-Executive Chairman of Hays plc. 4 R B Butler FCIS, Chief Process Officer (Chairman of the Nomination Committee)(a) Richard Butler, 42, joined the Group as Company Secretary in August 1987 from Bowthorp Holdings plc, now Spirent plc. He was 2 I Mason MBA, Group Chief Executive appointed to the Board in July 2000 and is responsible for the Group Ian Mason, 40, joined the Group in February 1995 as Director of operational processes. -

BUSINESS TRANSFORMATION & OPERATIONAL EXCELLENCE WORLD SUMMIT & INDUSTRY AWARDS – HIGHLY CONFIDENTIAL DRAFT PROGRAM Co
BUSINESS TRANSFORMATION & OPERATIONAL EXCELLENCE WORLD SUMMIT & INDUSTRY AWARDS – HIGHLY CONFIDENTIAL DRAFT PROGRAM Confirmed Speakers: William Owad Joseph Spadaford Zac Jacobson Hillary Wilson SVP, Operational Excellence EVP, Chief Operations Strategy Senior Director, Business Excellence Director, Process Improvement & Cardinal Health Officer and Customer Insights Project Management Computershare eBay Boehringer Ingelheim Gary Peterson Eric Pope Bob Abel Dalton Li Executive Vice President, Supply VP, Operations Senior Director - Global Process and Vice President Chain & Production US Synthetics Capabilty Excellence MassMutual O.C. Tanner Company Walmart Dennis Raymer Alex Jones Solomon Dadebo Jack Reismiller VP, Operational Excellence Lean Transformation Leader Head of PBC, Process Systems Eng., EVP Quality & Continuous Baylor Scott & White Healthcare Intel Product Mgmt, Ops Excellence & Improvement - Global Process Productivity at Global HyCO, Excellence Praxair Rolls Royce Jason Morwick Angel Garcia Jeff Porada Richard Morris Director, Business Improvement & Global Continuous Improvement Director of Lean Six Sigma VP Product Project Integration Quality Leader Jabil BMW Manufacturing Co., LLC Wyndham Vacation Ownership Catalent Stephan Blasilli Tze Chao Chiam Srisu Subrahmanyam Anil Nair Head of Corporate Initiatives Associate Director, Research VP, Global Engineering Sr. Director, Global Quality, EHS & EDP Renewables Informatics Ingram Micro Continuous Improvement Christiana Care Health Systems Ingram Micro Ashutosh Pandey Bernard -

Governance and Nominating Committee Terms of Reference
HIGH ARCTIC ENERGY SERVICES INC. GOVERNANCE AND NOMINATING COMMITTEE TERMS OF REFERENCE The Board of Directors (the “Board”) of High Arctic Services Inc. (the “Corporation”), to assist in its oversight responsibilities, has established the Corporate Governance and Nominating Committee of the Board (the “Committee”) and approved these Terms of Reference (“ToR”) which set out the roles, composition, meeting requirements, duty of the chair, responsibilities, functions and other matters concerning the Committee. 1. Role 1. 1 The purpose of the Committee is to identify individuals qualified to become members of the Board of Directors consistent with criteria approved by the Board, to recommend to the Board nominees for election to the Board at each annual meeting of shareholders or to fill vacancies on the Board and to address related matters. The Committee shall also develop and recommend to the Board corporate governance principles applicable to the Corporation and be responsible for leading the annual review of the performance of the Board. In this role the Committee functions to enhance Board of Director effectiveness through self- reflection, independence, relationship oversight and effective processes and tools. This includes the Board’s relationship with management to foster a collegial and productive work environment. 2. Composition 2. 1 The Committee shall consist of not less than three and not more than six members. 2. 2 Each member of the Committee shall be elected annually from among the members of the Board to hold office for the ensuing year or until their successors are elected. Committee members may be removed at any time by the Board. -

Information Influencer, Strategy Shaper the Changing Profile of the CIO in Asia-Pacific
INFORMATION INFLUENCER, STRATEGY SHAPER The changing profile of the CIO in Asia-Pacific A report from The Economist Intelligence Unit Sponsored by Information influencer, strategy shaper The changing profile of the CIO in Asia-Pacific ABOUT THIS RESEARCH Information influencer, strategy shaper: The - Manufacturing (electrical and electronic changing profile of the CIO in Asia-Pacific is a manufacturing, computer hardware, report from The Economist Intelligence Unit, consumer goods, consumer electronics, sponsored by Dell. It documents how chief pharmaceuticals) information officers (CIOs) in the Asia-Pacific region are taking on functional roles above and n Company size: 61% of the profiled CIOs work beyond information technology (IT). in firms with more than 500 employees. This report draws on two main sources for its The Economist Intelligence Unit also examined research and findings: the career paths of seven CIOs in Asia-Pacific by drawing on LinkedIn data and other publicly In November 2015 The Economist Intelligence available career information such as employee Unit analysed 4,577 LinkedIn profiles of CIOs profiles on their company website. The CIOs are, in Asia-Pacific to understand the different listed in order of surname: functional roles they have played during their careers. The analysis provides hints about how n VVR Babu, former CIO of Indian conglomerate ITC the role of the CIO is evolving and how the nature of the evolution differs across country markets, n Angela Farrar-Tilley, CIO, Spar Australia company sizes, industries and career spans. n David Gledhill, head of group technology and n Geography: The profiled CIOs include operations, DBS Bank 2,891 based in Australia/New Zealand, 222 in China, 945 in India, 180 in Japan n Anoop Handa, founder and managing and 339 in Singapore. -

Policy Division Administrative Division Office of Legal Representation
Jim Justice Governor State of West Virginia Dana F. Eddy Executive Director Allan McVey Cabinet Secretary Department of Administration Donald L. Stennett Crystal L. Walden Senior Deputy Director Deputy Director Policy Administrative Office of Legal Division Division Representation Dana F. Eddy Donald L. Stennett Crystal L. Walden Chief Executive Officer Chief Operating Officer Director Brenda K. Thompson Appointed Counsel Appellate Advocacy Habeas Corpus General Counsel Services Division Division Jonathan W. Friley Chief Process Officer Mark A. Doyle LeeAnn M. Doyle Matthew D. Brummond Justin M. Collin Chief Financial Officer Director Appellate Counsel Managing Attorney Public Defender Heather E. Atkins Financial Criminal Law Andrew R. Shumate Robert F. Evans Lora G. Walker Corporation Accounting Tech & Lead Division Research Center* General Counsel Appellate Counsel Staff Attorney Resource Center* Processor Stephanne C. Thornton Mark A. Doyle Pamela R. Clark Lea J. Melton James W. Light Vacant Mark W. Browning Criminal Justice Director Coordinator Accounting Tech Accounting Tech Appellate Counsel Staff Attorney Specialist Lisa D. Knell Teresa G. Asbury Jessica M. Hudnall Rosa M. McFarland Sarah E. Saul Karissa P. Blackburn OVS Help Desk OVS Auditor Coordinator Accounting Tech Paralegal Staff Attorney Coordinator Lee A. Carper Rhonda E. Ashworth Jordan R. Gunnoe Vacant Officer Manager Secretary Staff Attorney Blake Collias Gordon J. Simmons Administrative Investigator * See reverse side for Resource Center org chart Assistant Riley White Paralegal RESOURCE CENTER PUBLIC DEFENDER CORPORATION CRIMINAL LAW RESEARCH CENTER (CLRC) RESOURCE CENTER (PDCRC) .