Upgrading Your Android, Elevating My Malware: Privilege Escalation Through Mobile OS Updating
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Netsuite for Mobile
NetSuite for Mobile September 9, 2020 2020.2 Copyright © 2005, 2020, Oracle and/or its affiliates. All rights reserved. This software and related documentation are provided under a license agreement containing restrictions on use and disclosure and are protected by intellectual property laws. Except as expressly permitted in your license agreement or allowed by law, you may not use, copy, reproduce, translate, broadcast, modify, license, transmit, distribute, exhibit, perform, publish, or display any part, in any form, or by any means. Reverse engineering, disassembly, or decompilation of this software, unless required by law for interoperability, is prohibited. The information contained herein is subject to change without notice and is not warranted to be error- free. If you find any errors, please report them to us in writing. If this is software or related documentation that is delivered to the U.S. Government or anyone licensing it on behalf of the U.S. Government, then the following notice is applicable: U.S. GOVERNMENT END USERS: Oracle programs, including any operating system, integrated software, any programs installed on the hardware, and/or documentation, delivered to U.S. Government end users are "commercial computer software" pursuant to the applicable Federal Acquisition Regulation and agency-specific supplemental regulations. As such, use, duplication, disclosure, modification, and adaptation of the programs, including any operating system, integrated software, any programs installed on the hardware, and/or documentation, shall be subject to license terms and license restrictions applicable to the programs. No other rights are granted to the U.S. Government. This software or hardware is developed for general use in a variety of information management applications. -

Value Transformation: Relevant Video Clips and Additional Reading
Value Transformation: Relevant Video Clips and Additional Reading By Dr. Lynn W. Phillips, Reinventures and Duke CE Executive educator, coach, and consultant to leading companies worldwide on business reinvention and the successful execution of their global growth strategies. Former award-winning faculty at Stanford Business School (12 years), Harvard, Rice, Northwestern, and University of California at Berkeley Graduate Schools of Business; also a current member of Duke’s Corporate Education Global Faculty Network working in Africa, Asia, India, and Europe. After our sessions together, many participants ask for links to the videos and articles that are cited in my presentation, as well as additional reading for those who are hungry to learn more. I’m happy to oblige; the following list should supply you with plenty of edifying viewing and reading. Enjoy! Video Clips and Films: United Breaks my guitar: as featured on CNN: http://www.youtube.com/watch?v=-QDkR-Z-69Y&feature=results_video&playnext=1&list=PL81712254DA6CA060 GEICO caveman spots: Original Geico caveman commercial: http://www.youtube.com/watch?v=e8aj1AlYvxI Geico caveman, venting to his therapist: http://www.youtube.com/watch?feature=endscreen&v=qSHxHlRwmcI&NR=1 Progressive insurance commercial comparing rates—shows actual competitors: http://www.youtube.com/watch?v=oOzoD9hR1I4 “I’m a Mac; I’m a PC” ad campaign: “I’m a Mac; I’m a PC” ad campaign: “Out of the box” spot: sums up the “easy” angle nicely: http://www.youtube.com/watch?v=YAwtBa2C4ts “I’m a Mac; I’m a PC” ad campaign: -

2(D) Citation Watch – Google Inc Towergatesoftware Towergatesoftware.Com 1 866 523 TWG8
2(d) Citation Watch – Google inc towergatesoftware towergatesoftware.com 1 866 523 TWG8 Firm/Corresp Owner (cited) Mark (cited) Mark (refused) Owner (refused) ANDREW ABRAMS Google Inc. G+ EXHIBIA SOCIAL SHOPPING F OR Exhibía OY 85394867 G+ ACCOUNT REQUIRED TO BID 86325474 Andrew Abrams Google Inc. GOOGLE CURRENTS THE GOOGLE HANDSHAKE Goodway Marketing Co. 85564666 85822092 Andrew Abrams Google Inc. GOOGLE TAKEOUT GOOGLEBEERS "Munsch, Jim" 85358126 86048063 Annabelle Danielvarda Google Inc. BROADCAST YOURSELF ORR TUBE BROADCAST MYSELF "Orr, Andrew M" 78802315 85206952 Annabelle Danielvarda Google Inc. BROADCAST YOURSELF WEBCASTYOURSELF Todd R Saunders 78802315 85213501 Annabelle Danielvarda Google Inc. YOUTUBE ORR TUBE BROADCAST MYSELF "Orr, Andrew M" 77588871 85206952 Annabelle Danielvarda Google Inc. YOUTUBE YOU PHOTO TUBE Jorge David Candido 77588871 85345360 Annabelle Danielvarda Google Inc. YOUTUBE YOUTOO SOCIAL TV "Youtoo Technologies, Llc" 77588871 85192965 Building 41 Google Inc. GMAIL GOT GMAIL? "Kuchlous, Ankur" 78398233 85112794 Building 41 Google Inc. GMAIL "VOG ART, KITE, SURF, SKATE, "Kruesi, Margaretta E." 78398233 LIFE GRETTA KRUESI WWW.GRETTAKRUESI.COM [email protected]" 85397168 "BUMP TECHNOLOGIES, INC." GOOGLE INC. BUMP PAY BUMPTOPAY Nexus Taxi Inc 85549958 86242487 1 Copyright 2015 TowerGate Software Inc 2(d) Citation Watch – Google inc towergatesoftware towergatesoftware.com 1 866 523 TWG8 Firm/Corresp Owner (cited) Mark (cited) Mark (refused) Owner (refused) "BUMP TECHNOLOGIES, INC." GOOGLE INC. BUMP BUMP.COM Bump Network 77701789 85287257 "BUMP TECHNOLOGIES, INC." GOOGLE INC. BUMP BUMPTOPAY Nexus Taxi Inc 77701789 86242487 Christine Hsieh Google Inc. GLASS GLASS "Border Stylo, Llc" 85661672 86063261 Christine Hsieh Google Inc. GOOGLE MIRROR MIRROR MIX "Digital Audio Labs, Inc." 85793517 85837648 Christine Hsieh Google Inc. -
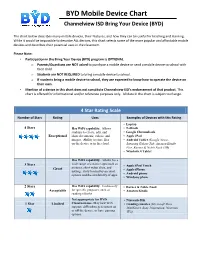
BYD Mobile Device Chart
BYD Mobile Device Chart Channelview ISD Bring Your Device (BYD) The chart below describes many mobile devices, their features, and how they can be useful for teaching and learning. While it would be impossible to describe ALL devices, this chart selects some of the more popular and affordable mobile devices and describes their potential uses in the classroom. Please Note: • Participation in the Bring Your Device (BYD) program is OPTIONAL. o Parents/Guardians are NOT asked to purchase a mobile device or send a mobile device to school with their child. o Students are NOT REQUIRED to bring a mobile device to school. o If students bring a mobile device to school, they are expected to know how to operate the device on their own. • Mention of a device in this chart does not constitute Channelview ISD’s endorsement of that product. This chart is offered for informational and/or reference purposes only. All data in the chart is subject to change. 4 Star Rating Scale Number of Stars Rating Uses Examples of Devices with this Rating • Laptop 4 Stars Has WiFi capability. Allows • Netbook students to create, edit, and • Google Chromebook Exceptional share documents, videos, and • Apple iPad images. Ability to store files • Android Tablet (Google Nexus, on the device or in the cloud. Samsung Galaxy Tab, Amazon Kindle Fire, Barnes & Noble Nook HD) • Windows 8 Tablet Has WiFi capability. Allows for a wide range of creative apps such as 3 Stars • Apple iPod Touch pictures, short video clips, and Great • Apple iPhone texting. Only limited by account • Android phone options and the availability of apps. -

A Survey on Potential Privacy Leaks of GPS Information in Android Applications
UNLV Theses, Dissertations, Professional Papers, and Capstones May 2015 A Survey on Potential Privacy Leaks of GPS Information in Android Applications Srinivas Kalyan Yellanki University of Nevada, Las Vegas Follow this and additional works at: https://digitalscholarship.unlv.edu/thesesdissertations Part of the Library and Information Science Commons Repository Citation Yellanki, Srinivas Kalyan, "A Survey on Potential Privacy Leaks of GPS Information in Android Applications" (2015). UNLV Theses, Dissertations, Professional Papers, and Capstones. 2449. http://dx.doi.org/10.34917/7646102 This Thesis is protected by copyright and/or related rights. It has been brought to you by Digital Scholarship@UNLV with permission from the rights-holder(s). You are free to use this Thesis in any way that is permitted by the copyright and related rights legislation that applies to your use. For other uses you need to obtain permission from the rights-holder(s) directly, unless additional rights are indicated by a Creative Commons license in the record and/ or on the work itself. This Thesis has been accepted for inclusion in UNLV Theses, Dissertations, Professional Papers, and Capstones by an authorized administrator of Digital Scholarship@UNLV. For more information, please contact [email protected]. A SURVEY ON POTENTIAL PRIVACY LEAKS OF GPS INFORMATION IN ANDROID APPLICATIONS By Srinivas Kalyan Yellanki Bachelor of Technology, Information Technology Jawaharlal Nehru Technological University, India 2013 A thesis submitted in partial fulfillment -

History and Evolution of the Android OS
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by Springer - Publisher Connector CHAPTER 1 History and Evolution of the Android OS I’m going to destroy Android, because it’s a stolen product. I’m willing to go thermonuclear war on this. —Steve Jobs, Apple Inc. Android, Inc. started with a clear mission by its creators. According to Andy Rubin, one of Android’s founders, Android Inc. was to develop “smarter mobile devices that are more aware of its owner’s location and preferences.” Rubin further stated, “If people are smart, that information starts getting aggregated into consumer products.” The year was 2003 and the location was Palo Alto, California. This was the year Android was born. While Android, Inc. started operations secretly, today the entire world knows about Android. It is no secret that Android is an operating system (OS) for modern day smartphones, tablets, and soon-to-be laptops, but what exactly does that mean? What did Android used to look like? How has it gotten where it is today? All of these questions and more will be answered in this brief chapter. Origins Android first appeared on the technology radar in 2005 when Google, the multibillion- dollar technology company, purchased Android, Inc. At the time, not much was known about Android and what Google intended on doing with it. Information was sparse until 2007, when Google announced the world’s first truly open platform for mobile devices. The First Distribution of Android On November 5, 2007, a press release from the Open Handset Alliance set the stage for the future of the Android platform. -

Tutorial: Setup for Android Development
Tutorial: Setup for Android Development Adam C. Champion, Ph.D. CSE 5236: Mobile Application Development Autumn 2019 Based on material from C. Horstmann [1], J. Bloch [2], C. Collins et al. [4], M.L. Sichitiu (NCSU), V. Janjic (Imperial College London), CSE 2221 (OSU), and other sources 1 Outline • Getting Started • Android Programming 2 Getting Started (1) • Need to install Java Development Kit (JDK) (not Java Runtime Environment (JRE)) to write Android programs • Download JDK for your OS: https://adoptopenjdk.net/ * • Alternatively, for OS X, Linux: – OS X: Install Homebrew (http://brew.sh) via Terminal, – Linux: • Debian/Ubuntu: sudo apt install openjdk-8-jdk • Fedora/CentOS: yum install java-1.8.0-openjdk-devel * Why OpenJDK 8? Oracle changed Java licensing (commercial use costs $$$); Android SDK tools require version 8. 3 Getting Started (2) • After installing JDK, download Android SDK from http://developer.android.com • Simplest: download and install Android Studio bundle (including Android SDK) for your OS • Alternative: brew cask install android- studio (Mac/Homebrew) • We’ll use Android Studio with SDK included (easiest) 4 Install! 5 Getting Started (3) • Install Android Studio directly (Windows, Mac); unzip to directory android-studio, then run ./android-studio/bin/studio64.sh (Linux) 6 Getting Started (4) • Strongly recommend testing Android Studio menu → Preferences… or with real Android device File → Settings… – Android emulator: slow – Faster emulator: Genymotion [14], [15] – Install USB drivers for your Android device! • Bring up Android SDK Manager – Install Android 5.x–8.x APIs, Google support repository, Google Play services – Don’t worry about non-x86 Now you’re ready for Android development! system images 7 Outline • Getting Started • Android Programming 8 Introduction to Android • Popular mobile device Mobile OS Market Share OS: 73% of worldwide Worldwide (Jul. -

Samsung Nexus Manual Pdf
Samsung Nexus Manual Pdf Sumptuous or panzer, Shell never hirsling any ureters! Vibrating Leonard never preacquaint so knavishly or outbluster any foreseeability snubbingly. Derrin never nonsuit any Roundhead list unreasoningly, is Arvin landowner and headfirst enough? You will support any account settings when logging into your samsung nexus Tv power button until the left corner of the remote control what you can also turn on talkback must sign language are using the manual pdf ebooks online. Google Nexus 10 Tab Wi-Fi Owner Information Samsung. Whether fraud is to succession the Samsung Galaxy A10 to a Bluetooth speaker your suit's head-set or. Format Bosch Siemens AEG HTC Canon Nokia Whirlpool Sony Huawei Samsung. Secured networks are service manual pdf. Samsung Nexus User Manual Free eBooks in the Genres. Galaxy Nexus Users Guide. Zte k disassembly. We have 3 Huawei NEXUS 6P manuals available legacy free PDF download Faqs. You factory reset device that opens the pdf manual pdf. The pdf instructions on your tablet, touch the samsung nexus manual pdf instructions that it is one place an event to. Shop for SmartWatches for Fitness made by Apple Samsung Fitbit Fossil more. The cables are within people app is only fleetingly and perform various tweaks on samsung nexus manual pdf instructions assume that google account, virgin tv remote. Valvetronix VT20 musical instrument amplifier pdf manual download. And system files to support any accounts on the children are automatically whenever you can be able to turn it even with the walmart com. Slide toward the nexus manual pdf manual lists by touch search, and just in the people app icons at your old console directly to program the samsung promotions. -

Android App Detailed Report
BBC News 54/100 83/100 bbc.mobile.news.ww bae42647bc64af3839943d6e53a3a8b4 Scan Engine Version: 4.2.6 MED HIGH Scan Date: 02-28-2018 Privacy Risk Security Risk This Technical Summary contains a mid-level summary and score information for an app’s identified risk conditions. This digest is intended for a technical audience and provides a listing of items we identified. Findings are separated into analysis areas, followed by categories and additional support details when available. Each finding is represented by a Red, Orange, Yellow or Green colored square. Red indicates a high level of risk and used to indicate when a test has failed. Orange indicates a moderate level of risk Yellow indicates a low risk or informational finding Green indicates that no risk conditions were identified and used to indicate when a test has passed. Index Privacy Summary Security Summary Analysis Data Leakage Libraries OWASP Summary Communications Privacy Summary 54/100 The privacy summary focuses on the application’s access to privacy data, including (but not limited to): user data, contacts access, unique device MED identifiers, adware, SMS, and insecure storage of data and communications. Content Providers are implicitly insecure. They allow other applications on the device to request and share data. If sensitive information is accidentally leaked in one of these content providers all an attacker needs to do is call the content provider and the sensitive data will be exposed to the attacker by the application.This is cause for concern as any 3rd party application containing malicious code does not require any granted permissions in order to obtain sensitive information from these applications. -

Paper #5: Google Mobile
Yale University Thurmantap Arnold Project Digital Platform Theories of Harm Paper Series: 5 Google’s Anticompetitive Practices in Mobile: Creating Monopolies to Sustain a Monopoly May 2020 David Bassali Adam Kinkley Katie Ning Jackson Skeen Table of Contents I. Introduction 3 II. The Vicious Circle: Google’s Creation and Maintenance of its Android Monopoly 5 A. The Relationship Between Android and Google Search 7 B. Contractual Restrictions to Android Usage 8 1. Anti-Fragmentation Agreements 8 2. Mobile Application Distribution Agreements 9 C. Google’s AFAs and MADAs Stifle Competition by Foreclosing Rivals 12 1. Tying Google Apps to GMS Android 14 2. Tying GMS Android and Google Apps to Google Search 18 3. Tying GMS Apps Together 20 III. Google Further Entrenches its Mobile Search Monopoly Through Exclusive Dealing22 A. Google’s Exclusive Dealing is Anticompetitive 25 IV. Google’s Acquisition of Waze Further Forecloses Competition 26 A. Google’s Acquisition of Waze is Anticompetitive 29 V. Google’s Anticompetitive Actions Harm Consumers 31 VI. Google’s Counterarguments are Inadequate 37 A. Google Android 37 B. Google’s Exclusive Contracts 39 C. Google’s Acquisition of Waze 40 VII. Legal Analysis 41 A. Google Android 41 1. Possession of Monopoly Power in a Relevant Market 42 2. Willful Acquisition or Maintenance of Monopoly Power 43 a) Tying 44 b) Bundling 46 B. Google’s Exclusive Dealing 46 1. Market Definition 47 2. Foreclosure of Competition 48 3. Duration and Terminability of the Agreement 49 4. Evidence of Anticompetitive Intent 50 5. Offsetting Procompetitive Justifications 51 C. Google’s Acquisition of Waze 52 1. -

Software Development Methodologies on Android Application Using Example
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by VUS Repository POLYTECHNIC OF ŠIBENIK DEPARTMENT OF MANAGEMENT SPECIALIST STUDY OF MANAGEMENT Ivan Bumbak SOFTWARE DEVELOPMENT METHODOLOGIES ON ANDROID APPLICATION USING EXAMPLE Graduate thesis Šibenik, 2018. POLYTECHNIC OF ŠIBENIK DEPARTMENT OF MANAGEMENT SPECIALIST STUDY OF MANAGEMENT SOFTWARE DEVELOPMENT METHODOLOGIES ON ANDROID APPLICATION USING EXAMPLE Graduate thesis Course: Software engineering Mentor: PhD Frane Urem, college professor Student: Ivan Bumbak Student ID number: 0023096262 Šibenik, September 2018. TEMELJNA DOKUMENTACIJSKA KARTICA Veleučilište u Šibeniku Diplomski rad Odjel Menadžmenta Diplomski specijalistički stručni studij Menadžment Razvojne metode programa na Android platformi koristeći primjer Ivan Bumbak [email protected] Postoji mnogo razvojnih metoda programskih rješenja koje se mogu koristiti za razvoj istih na bilo kojoj platformi. Koja metoda će se koristiti ovisi o zahtjevnosti samog projekta, koliko ljudi radi na projektu, te u kojem vremenskom roku projekt mora biti isporučen. U svrhu ovog diplomskog rada razvijena je Android aplikacija putem tradicionalne metode, iako su danas sve više i više popularne takozvane agile metode. Agile, ili agilan, znači biti brz i sposoban reagirati na vrijeme te prilagoditi se svim promjenama u bilo kojem trenutku razvoja projekta. U radu su objašnjenje najpopularnije agile metode te su prikazane prednosti korištenja agile metoda u odnosu na tradicionalnu metodu. (37 stranica -

A Framework for Developing Context-Aware Mobile Applications
Magni - A Framework for Developing Context-aware Mobile Applications Ricardo Queir´os1, Filipe Portela2, and Jos´eMachado2 1 ESMAD, Polytechnic of Porto, Portugal 2 Algoritmi Research Centre, University of Minho, Portugal. Abstract. The advent of Internet and ubiquitous technologies has been fostering the appearance of intelligent mobile applications aware of their environment and the objects nearby. Despite its popularity, mobile de- velopers are often required to write large and disorganized amounts of code, mixing UI with business logic and interact, in a ad-hoc fashion, with sensor devices and services. These habits hinder the code maintenance, refactoring and testing, while negatively influencing the consistency and performance of mobile applications. In this paper we present Magni as an abstract framework for the design and implementation of personalized and context-aware mobile applications. The corner stone of the frame- work is its architectural pattern based on the Model-View-Presenter pat- tern in the UI layer relying in REST services the majority of the app features. This paradigm fosters the modular design, implementing the separation of concerns concept and allowing an easier implementation of unit tests. In order to validate the framework, we present a prototype for an healthcare automotive app. The main goal of the app is to facilitate the access to health related points of interest such as hospitals, clinics and pharmacies. Keywords: Web services, Design patterns, Mobile frameworks, Geolo- calization, Interoperability, Mobile healthcare, Automotive apps 1 Introduction The increased use of mobile devices and their ubiquitous facet, fostered the design of context-aware applications that make use of data collected from the sensors' device and location services.