Experience Report: an Empirical Study of PHP Security Mechanism Usage
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

SEO Footprints
SEO Footprints Brought to you by: Jason Rushton Copyright 2013 Online - M a r k e t i n g - T o o l s . c o m Page 1 Use these “Footprints” with your niche specific keywords to find Backlink sources. Some of the footprints below have already been formed into ready made search queries. TIP* If you find a footprint that returns the results you are looking for, there is no need to use the rest in that section. For example if I am looking for wordpress sites that allow comments and the search query “powered by wordpress” “YOUR YOUR KEYWORDS” returns lots of results there is no need to use all of the others that target wordpress sites as a lot of them will produce similar results. I would use one or two from each section. You can try them out and when you find one you like add it to your own list of favourites. Blogs “article directory powered by wordpress” “YOUR YOUR KEYWORDS” “blog powered by wordpress” “YOUR YOUR KEYWORDS” “blogs powered by typepad” “YOUR YOUR KEYWORDS” “YOURYOUR KEYWORDS” inurl:”trackback powered by wordpress” “powered by blogengine net 1.5.0.7” “YOUR YOUR KEYWORDS” “powered by blogengine.net” “YOUR YOUR KEYWORDS” “powered by blogengine.net add comment” “YOUR YOUR KEYWORDS” “powered by typepad” “YOUR YOUR KEYWORDS” “powered by wordpress” “YOUR YOUR KEYWORDS” “powered by wordpress review theme” “YOUR YOUR KEYWORDS” “proudly powered by wordpress” “YOUR YOUR KEYWORDS” “remove powered by wordpress” “YOUR YOUR KEYWORDS” Copyright 2013 Online - M a r k e t i n g - T o o l s . -

Mitigating SQL Injection Attacks on Legacy Web Applications
You shall not pass: Mitigating SQL Injection Attacks on Legacy Web Applications Rasoul Jahanshahi Adam Doupé Manuel Egele [email protected] [email protected] [email protected] Boston University Arizona State University Boston University ABSTRACT four most popular web apps (i.e., Wordpress, Joomla, Drupal, and SQL injection (SQLi) attacks pose a significant threat to the security Magento) increased by 267% compared to the prior year. of web applications. Existing approaches do not support object- There has been a great deal of research into identifying SQLi oriented programming that renders these approaches unable to vulnerabilities and defending against SQLi attacks on web apps. protect the real-world web apps such as Wordpress, Joomla, or Proposed approaches used various techniques such as static anal- Drupal against SQLi attacks. ysis [10, 11, 20, 22, 35], dynamic analysis [3, 6, 15, 21, 24, 25, 37], We propose a novel hybrid static-dynamic analysis for PHP or a mix of static-dynamic analysis [5, 17, 28]. While static analy- web applications that limits each PHP function for accessing the sis approaches can be promising, static analysis cannot determine database. Our tool, SQLBlock, reduces the attack surface of the whether input sanitization is performed correctly or not [34]. If the vulnerable PHP functions in a web application to a set of query sanitization function does not properly sanitize user-input, SQLi descriptors that demonstrate the benign functionality of the PHP attacks can still happen. Moreover, to the best of our knowledge, function. prior static analysis approaches for finding SQLi vulnerabilities in We implement SQLBlock as a plugin for MySQL and PHP. -

Appendix a the Ten Commandments for Websites
Appendix A The Ten Commandments for Websites Welcome to the appendixes! At this stage in your learning, you should have all the basic skills you require to build a high-quality website with insightful consideration given to aspects such as accessibility, search engine optimization, usability, and all the other concepts that web designers and developers think about on a daily basis. Hopefully with all the different elements covered in this book, you now have a solid understanding as to what goes into building a website (much more than code!). The main thing you should take from this book is that you don’t need to be an expert at everything but ensuring that you take the time to notice what’s out there and deciding what will best help your site are among the most important elements of the process. As you leave this book and go on to updating your website over time and perhaps learning new skills, always remember to be brave, take risks (through trial and error), and never feel that things are getting too hard. If you choose to learn skills that were only briefly mentioned in this book, like scripting, or to get involved in using content management systems and web software, go at a pace that you feel comfortable with. With that in mind, let’s go over the 10 most important messages I would personally recommend. After that, I’ll give you some useful resources like important websites for people learning to create for the Internet and handy software. Advice is something many professional designers and developers give out in spades after learning some harsh lessons from what their own bitter experiences. -

Snuffleupagus Documentation
Snuffleupagus Documentation Release stable Sebastien Blot & Julien Voisin Aug 29, 2021 Contents 1 Documentation 3 1.1 Features..................................................3 1.2 Installation................................................ 11 1.3 Configuration............................................... 14 1.4 Download................................................. 22 1.5 Changelog................................................ 23 1.6 FAQ.................................................... 29 1.7 Propaganda................................................ 33 1.8 Cookies.................................................. 35 2 Greetings 39 i ii Snuffleupagus Documentation, Release stable Snuffleupagus is a PHP7+ and PHP8+ module designed to drastically raise the cost of attacks against websites. This is achieved by killing entire bug classes and providing a powerful virtual-patching system, allowing the administrator to fix specific vulnerabilities without having to touch the PHP code. Contents 1 Snuffleupagus Documentation, Release stable 2 Contents CHAPTER 1 Documentation 1.1 Features Snuffleupagus has a lot of features that can be divided in two main categories: bug-classes killers and virtual-patching. The first category provides primitives to kill various bug families (like arbitrary code execution via unserialize for example) or raise the cost of exploitation. The second category is a highly configurable system to patch functions in php itself. 1.1.1 Bug classes killed or mitigated system injections The system function executes an external -

Locating Exploits and Finding Targets
452_Google_2e_06.qxd 10/5/07 12:52 PM Page 223 Chapter 6 Locating Exploits and Finding Targets Solutions in this chapter: ■ Locating Exploit Code ■ Locating Vulnerable Targets ■ Links to Sites Summary Solutions Fast Track Frequently Asked Questions 223 452_Google_2e_06.qxd 10/5/07 12:52 PM Page 224 224 Chapter 6 • Locating Exploits and Finding Targets Introduction Exploits, are tools of the hacker trade. Designed to penetrate a target, most hackers have many different exploits at their disposal. Some exploits, termed zero day or 0day, remain underground for some period of time, eventually becoming public, posted to newsgroups or Web sites for the world to share. With so many Web sites dedicated to the distribution of exploit code, it’s fairly simple to harness the power of Google to locate these tools. It can be a slightly more difficult exercise to locate potential targets, even though many modern Web application security advisories include a Google search designed to locate potential targets. In this chapter we’ll explore methods of locating exploit code and potentially vulnerable targets.These are not strictly “dark side” exercises, since security professionals often use public exploit code during a vulnerability assessment. However, only black hats use those tools against systems without prior consent. Locating Exploit Code Untold hundreds and thousands of Web sites are dedicated to providing exploits to the gen- eral public. Black hats generally provide exploits to aid fellow black hats in the hacking community.White hats provide exploits as a way of eliminating false positives from auto- mated tools during an assessment. Simple searches such as remote exploit and vulnerable exploit locate exploit sites by focusing on common lingo used by the security community. -
![Arxiv:2102.03131V1 [Cs.CR] 5 Feb 2021 Extensions Are Available Within Systems Like Wordpress Or Called Joomla](https://docslib.b-cdn.net/cover/3542/arxiv-2102-03131v1-cs-cr-5-feb-2021-extensions-are-available-within-systems-like-wordpress-or-called-joomla-903542.webp)
Arxiv:2102.03131V1 [Cs.CR] 5 Feb 2021 Extensions Are Available Within Systems Like Wordpress Or Called Joomla
Over 100 Bugs in a Row: Security Analysis of the Top-Rated Joomla Extensions Marcus Niemietz, Mario Korth, Christian Mainka, Juraj Somorovsky fi[email protected] Hackmanit GmbH Abstract like WordPress and Joomla. There exists a family of tools Nearly every second website is using a Content Manage- which, inter alia, allow researchers and penetration testers to ment System (CMS) such as WordPress, Drupal, and Joomla. scan CMS software (e.g., WPScan [4], JoomScan [10]) for These systems help to create and modify digital data, typically well-known issues. Although community-based projects like within a collaborative environment. One common feature is to Joomla make use of tools like static source code scanners, it enrich their functionality by using extensions. Popular exten- seems to be a non-trivial task to detect well-known vulnerabil- sions allow developers to easily include payment gateways, ities such as XSS and SQLi, as shown by security researches backup tools, and social media components. multiple times [29]. To provide an example, Joomla intro- Due to the extended functionality, it is not surprising that duced the usage of the code analysis tool RIPS in June 2018 such an expansion of complexity implies a bigger attack sur- [7, 16]. Although RIPS is explicitly designed to detect web face. In contrast to CMS core systems, extensions are usu- vulnerabilities like XSS, Joomla has officially announced 30 ally not considered during public security audits. However, security vulnerabilities within the first half year of 2019, and a Cross-Site Scripting (XSS) or SQL injection (SQLi) at- 12 of them were XSS issues [17]. -

Snuffleupagus
» SnuFfLEupAGus A ghostly elephant, in your php stack, killing bug classes, defeating attacks, and virtual-patching what is remaining. 1 / 106 » Bonjour 2 / 106 » I'm sorry 3 / 106 » Good evening We're glad to be here We're working at the same (French¹) company In the security team. It's called NBS System And it's a hosting company, you know, for websites. ¹ Hence our lovely accent. 4 / 106 » What are we trying to solve? We're hosting a lot of various php applications, using CMS written by super- duper creative people, and we'd like to prevent our customers from being pwned. 5 / 106 » What we were doing so far We have a lot of os-level hardening (grsecurity ♥) We have some custom IDS We have a (cool) WAF called naxsi But not everything is patchable with those, and we can not² touch the PHP code. ¹ And to be honest, we don't want to. 6 / 106 » Some words about php Its syntax draws upon C, Java, and Perl, and is easy to learn. The main goal of the language is to allow web developers to write dynamically generated web pages quickly, but you can do much more with PHP. — the php documentation 7 / 106 » Still words about php Well, there were other factors in play there. htmlspecialchars was a very early function. Back when PHP had less than 100 functions and the function hashing mechanism was strlen(). In order to get a nice hash distribution of function names across the various function name lengths names were picked specifically to make them fit into a specific length bucket. -
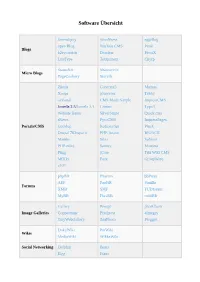
Software Übersicht
Software Übersicht Serendipity WordPress eggBlog open Blog Nucleus CMS Pixie Blogs b2evolution Dotclear PivotX LifeType Textpattern Chyrp StatusNet Sharetronix Micro Blogs PageCookery Storytlr Zikula Concrete5 Mahara Xoops phpwcms Tribiq ocPortal CMS Made Simple ImpressCMS Joomla 2.5/Joomla 3.1 Contao Typo3 Website Baker SilverStripe Quick.cms sNews PyroCMS ImpressPages Portals/CMS Geeklog Redaxscript Pluck Drupal 7/Drupal 8 PHP-fusion BIGACE Mambo Silex Subrion PHP-nuke Saurus Monstra Pligg jCore Tiki Wiki CMS MODx Fork GroupWare e107 phpBB Phorum bbPress AEF PunBB Vanilla Forums XMB SMF FUDforum MyBB FluxBB miniBB Gallery Piwigo phpAlbum Image Galleries Coppermine Pixelpost 4images TinyWebGallery ZenPhoto Plogger DokuWiki PmWiki Wikis MediaWiki WikkaWiki Social Networking Dolphin Beatz Elgg Etano Jcow PeoplePods Oxwall Noahs Classifieds GPixPixel Ad Management OpenX OSClass OpenClassifieds WebCalendar phpScheduleIt Calenders phpicalendar ExtCalendar BlackNova Traders Word Search Puzzle Gaming Shadows Rising MultiPlayer Checkers phplist Webmail Lite Websinsta maillist OpenNewsletter Mails SquirrelMail ccMail RoundCube LimeSurvey LittlePoll Matomo Analytics phpESP Simple PHP Poll Open Web Analytics Polls and Surveys CJ Dynamic Poll Aardvark Topsites Logaholic EasyPoll Advanced Poll dotProject Feng Office Traq phpCollab eyeOSh Collabtive Project PHProjekt The Bug Genie Eventum Management ProjectPier TaskFreak FlySpray Mantis Bug tracker Mound Zen Cart WHMCS Quick.cart Magento Open Source Point of Axis osCommerce Sale TheHostingTool Zuescart -

Pipenightdreams Osgcal-Doc Mumudvb Mpg123-Alsa Tbb
pipenightdreams osgcal-doc mumudvb mpg123-alsa tbb-examples libgammu4-dbg gcc-4.1-doc snort-rules-default davical cutmp3 libevolution5.0-cil aspell-am python-gobject-doc openoffice.org-l10n-mn libc6-xen xserver-xorg trophy-data t38modem pioneers-console libnb-platform10-java libgtkglext1-ruby libboost-wave1.39-dev drgenius bfbtester libchromexvmcpro1 isdnutils-xtools ubuntuone-client openoffice.org2-math openoffice.org-l10n-lt lsb-cxx-ia32 kdeartwork-emoticons-kde4 wmpuzzle trafshow python-plplot lx-gdb link-monitor-applet libscm-dev liblog-agent-logger-perl libccrtp-doc libclass-throwable-perl kde-i18n-csb jack-jconv hamradio-menus coinor-libvol-doc msx-emulator bitbake nabi language-pack-gnome-zh libpaperg popularity-contest xracer-tools xfont-nexus opendrim-lmp-baseserver libvorbisfile-ruby liblinebreak-doc libgfcui-2.0-0c2a-dbg libblacs-mpi-dev dict-freedict-spa-eng blender-ogrexml aspell-da x11-apps openoffice.org-l10n-lv openoffice.org-l10n-nl pnmtopng libodbcinstq1 libhsqldb-java-doc libmono-addins-gui0.2-cil sg3-utils linux-backports-modules-alsa-2.6.31-19-generic yorick-yeti-gsl python-pymssql plasma-widget-cpuload mcpp gpsim-lcd cl-csv libhtml-clean-perl asterisk-dbg apt-dater-dbg libgnome-mag1-dev language-pack-gnome-yo python-crypto svn-autoreleasedeb sugar-terminal-activity mii-diag maria-doc libplexus-component-api-java-doc libhugs-hgl-bundled libchipcard-libgwenhywfar47-plugins libghc6-random-dev freefem3d ezmlm cakephp-scripts aspell-ar ara-byte not+sparc openoffice.org-l10n-nn linux-backports-modules-karmic-generic-pae -

In Support of DITA)
Collaborative Focus Areas project (in support of DITA) In addition to the requirements already defined which are specific to this project, I have compiled a list of standard measures for evaluating any Free and Open Source Software (FOSS) technology. FOSS Technology Requirements 1. Community How viable is the community supporting the product? Are there independent contributors? How active are mailing lists, web sites? Is the community healthy, friendly and welcoming to newcomers? 2. Low Entry Barrier How easy is it to get started? Is the product a turn-key solution with immediate value after download? How consistent is the documentation, how hard is it to familiarize oneself with the codebase? 3. Product Maturity How robust is the underlying code? Are sound software engineering practices in use? Is the architecture clean and consistent? Are changes to the code regression-tested? 4. Industrial Strength How much does the product scale? How flexible and stable is the product, how well does it perform? Is it secure? 5. Off The Shelf Components How much does the product make use of standard components? Is the architecture modular to accomodate external code? 6. Feature Set Does the product have a conservative feature set, or does it have many bells and whistles? 7. Standards Compliance How much does the product use and interoperate with standards? 8. Usability Is the user interface understandable for non-technical persons? Is it consistent? Does it follow usability best practice? 9. Platform How well does the application fit into our infrastructure? 10. Security What is the profile and track record of the community vis-a-vis security best-practices? How often is the project listed in security vulnerability alerts, and what is the response time? 11. -

A Static Vulnerability Analysis Tool for PHP
PHPWander: A Static Vulnerability Analysis Tool for PHP Pavel Jurásek Thesis submitted for the degree of Master in Informatics: Programming and Networks 60 credits Department of Informatics Faculty of mathematics and natural sciences UNIVERSITY OF OSLO Spring 2018 PHPWander: A Static Vulnerability Analysis Tool for PHP Pavel Jurásek © 2018 Pavel Jurásek PHPWander: A Static Vulnerability Analysis Tool for PHP http://www.duo.uio.no/ Printed: Reprosentralen, University of Oslo PHPWander: A Static Vulnerability Analysis Tool for PHP Pavel Jurásek 16th May 2018 ii Contents 1 Introduction 1 I Background 3 2 Security vulnerabilities 5 2.1 Injections . .5 2.2 Cross-site scripting (XSS) . .6 2.3 Command injection . .7 2.4 Code injection . .7 2.5 Path traversal . .8 2.6 Other vulnerabilities . .8 3 PHP Language 9 3.1 History and description . .9 3.2 Typing . .9 3.3 Predefined variables . 10 3.4 Object-oriented aspects in PHP . 10 3.5 Class autoloading . 11 4 Static analysis 13 4.1 Data flow analysis . 13 4.2 Taint analysis . 14 4.2.1 Tainting method . 14 4.2.2 Control flow graphs . 14 4.3 Data flow sensitivities . 15 4.3.1 Flow sensitivity . 15 4.3.2 Context sensitivity . 16 4.4 SSA form . 16 4.5 Static analysis tools for PHP . 17 4.5.1 Code improvement tools . 17 4.5.2 Security checking tools . 18 II Development 19 5 Development phase 21 5.1 Architecture . 21 iii 5.2 Design decisions . 21 5.2.1 Configuration . 21 5.2.2 Software foundations . 23 5.2.3 Implementation details . -

Openstackでnecが実現する 「OSSクラウド」の世界
OpenStackでNECが実現する 「OSSクラウド」の世界 2013年3月12日 日本電気株式会社 プラットフォームマーケティング戦略本部 OSS推進室 技術主幹 高橋 千恵子 目次 ▐ OSSの動向 ▐ NECのOSS/Linux事業 ▐ OSSプラットフォームへの取り組み 高可用Linuxプラットフォーム OSSミドルウェアの活用 ▐ OSSクラウド OpenStackへの取り組み OSSクラウドソリューション ~沖縄クラウドサービス基盤~ OpenFlow+OpenStack ▐ 最後に ●本資料に掲載された社名、商品名は各社の商標または登録商標です。 Page 1 © NEC Corporation 2013 OSSの動向 Page 2 © NEC Corporation 2013 OSSコミュニティによるプロジェクト ▐ 全般 ・・・・・SaaS型アプリケーションが増加/著名OSSのベンダー配布、有償サポートや買収が進む OSS定点観測は、freecode.com にて実施。 ▐ インフラ系・・・仮想化やクラウド基盤関係のOSSが注目される/システム、ネット管理OSSの伸びがある サイトでの人気度(300以上)で順位付け。 OSSプロジェクトは2012.4時点で32.4万件。 ▐ デプロイメント系・・PostgreSQL、mySQLが高人気 これらのDB管理、DBクラスタリングOSSも伸びている ビジネス用途を中心に表示。 ▐ アプリ系・・・・SaaS型グループウェアOSS、ソフトウェア分類を越えた統合的な著名OSSの伸びがある コンシューマ・プライベート系は除く。 コンテンツアプリケーション •PHProject [GW] エンジニ コラボレーティブ •EGroupware CRM ERM SCM • Dokuwiki [Wiki] • jGnash アリング • WebGUI [CMF] • phpBB [GW] •OBM [GW] • Enterprise CRM and ア • Tiki Tiki CMS Groupware • ProcessMaker • CorneliOS [CMS] • Ariadne Groupware System • Task Juggler [PM] • Blender オペレーション • TinyMCE [DCM] • XODA • Simple Groupware [GW] プ • OpenWebMail[webmail]• Teamwork [GW] • Dolibarr • Achievo [PM] • mxGraph 製造管理 • Drupal [CMS] • mnoGoSerch • LedgerSMB • white_dune • eZpublish [publish FW]• Managing • ZIm [blog] • Plans [GW] • The Apache Open リ • Tine2.0 [CRM&GW] • GnuCash • Jgraph • OTRS • XWiki [Wiki] • Midgard • Zimbra [GW] for Business • Elastix • GroupOffice [GW] • Twiki [KB] • TUTOS[ERP&PM] • graphviz • FUDForum • OpenSearch Project コンシューマ 系 • SquirrelMail [Webmail] • Time Trex • BRL-CAD • Asterisk • Plone CMS Server • Citadel [bbs] •