Useris Guide
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

C1541-Manual
USER'S GUIDE STATEMENT This equipment generates and uses rad io frequency energy. If it is not. proper! installed and used in strict accordance with the manufacturer's instructions, thi equipment may interfere with radio and television reception . This m~chine ha been tested and found to comply with the limits for a Class B computing device peripheral in accordance with the specifications in Subpart 1 5 . of FCC Rul.es which are designed to provide reasonable protection against such interference 1n residential installation. If you suspect interference, you can test this equipment by COMMODORE turning it off and on. If you determine that there is interference with .radio or televi sion reception, try one or more of the following measures to correct 1t: .,541 • reorient the receiving antenna e move the computer away from the receiver . DISK DRIVE • change the relative positions of the computer equipment and the receiver . • plug the computer into a different outlet so that the computer and the receive· are on different branch circuits I USER'S GUIDE If necessary, consult your Commodore dealer or an e.xperienced radio / telev is ~o technician for additional suggestions. You may also wish to consult the following booklet, which was prepared by the Federal Communications Commission: " How to identify and Resolve Radio-TV Interference Problems" This booklet i available from the U.S. Government Printing Office, Washington, D.C. 20402, A Friendly Introduction to Your 1541 Diak Drive Stock No. 004-000-00345-4 ." IMPORTANT: Shield interface cable must be used according to FCC 14.8380. FOR USERS IN UK Second Edition WARNING : THIS APPARATUS MUST BE EARTHED! by Jim & Ellen Btraama IMPORTANT. -
Commodore 64 - Wikipedia
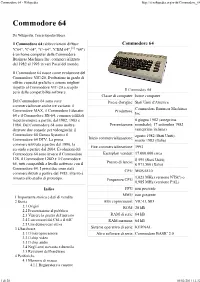
Commodore 64 - Wikipedia http://it.wikipedia.org/wiki/Commodore_64 Da Wikipedia, l'enciclopedia libera. Il Commodore 64 (abbreviazioni diffuse: Commodore 64 "C64", "C-64", "C=64", "CBM 64",[1] "64") è un home computer della Commodore Business Machines Inc. commercializzato dal 1982 al 1993 in vari Paesi del mondo. Il Commodore 64 nasce come evoluzione del Commodore VIC-20. Evoluzione in grado di offrire capacità grafiche e sonore migliori rispetto al Commodore VIC-20 a scapito Il Commodore 64 però della compatibilità software. Classe di computer: home computer Del Commodore 64 sono state Paese d'origine: Stati Uniti d'America commercializzate anche tre varianti: il Commodore Business Machines Commodore MAX, il Commodore Educator Produttore: Inc. 64 e il Commodore SX-64, commercializzati rispettivamente a partire dal 1982, 1983 e 6 giugno 1982 (anteprima 1984. Dal Commodore 64 sono inoltre Presentazione: mondiale); 17 settembre 1982 derivate due console per videogiochi: il (anteprima italiana) Commodore 64 Games System e il agosto 1982 (Stati Uniti); Inizio commercializzazione: Commodore 64 DTV. La prima marzo 1983 (Italia) commercializzata a partire dal 1990, la Fine commercializzazione: 1993 seconda a partire dal 2004. Evoluzioni del Commodore 64 sono invece il Commodore Esemplari venduti: 17.000.000 circa 128, il Commodore 128D e il Commodore $ 595 (Stati Uniti); Prezzo di lancio: 65, tutti compatibili a livello software con il ₤ 973.500 (Italia) Commodore 64. I primi due sono stati CPU: MOS 6510 commercilizzati a partire dal 1985, il -

Guide to Disc Formats
Guide To Disc Formats Written by Gerald J Holdsworth The technical background, in an easy to understand guide, for the Acorn and Watford Disc Filing Systems, Acorn Advanced Disc Filing System, Commodore 1541/1571/1581 and Commodore Amiga. Guide To Disc Formats Introduction 5 Acknowledgements 6 Note on Sinclair/Amstrad Format 7 Acorn Disc Filing System 8 Introduction 8 Specifications 8 Double Sided Interleaving 8 Maps 8 Catalogue information 8 Catalogue Information - Watford DFS 9 File entries (sector 0/2) 9 File details (sector 1/3) 9 File Order 10 Forbidden Characters 10 Identifying a DFS Image 10 Single Sided Images 10 Double Sided Images 11 Watford DFS 11 Acorn Advanced Disc Filing System 12 Introduction 12 Double Sided Interleaving 12 Maps 13 Old Map 13 Calculating the Checksums 13 New Map 13 Zone Header 13 Disc Record (zone 0 only) 13 Calculating Zone_Check 14 Allocation Bytes and Indirect Addresses 15 Example, using the same disc 16 Multi-zone discs 17 Example 18 Start and End of Search 19 So why these figures? 19 Where to Start 20 Directories 21 Header (Old & New) 21 Header (Big) 21 Tail (Old) 21 Tail (New) 21 Tail (Big) 22 What It All Means 22 StartMasSeq and EndMasSeq 22 StartName and EndName 22 DirLastMark 22 DirCheckByte 22 DirNameLen 23 DirSize, DirEntries and DirNameSize 23 Boot Block 23 Defect List 23 Hardware-dependent Information 23 Partial Disc Record 23 Boot Block Checksum 24 The Directory Entries 24 Entries (Old & New) 24 Page 2 written by Gerald Holdsworth [email protected] www.geraldholdsworth.co.uk 8 February -

CONTENTS Blue Reader Sogwap Softwares Excellent Program for Transferring Files Between C Page Item 64/C 128 and MS-Dos Based Machines
geoNEWSthe Journal of geoCLUB Issue 68 April 1997 EDITOR’S COMMENTS This Issue brings Part 2 of the Big CONTENTS Blue Reader Sogwap Softwares excellent program for transferring files between C Page Item 64/C 128 and MS-Dos based machines. The concluding part will be published in the May issue. 2 Library Review Another continuing saga is Terry & Sharon reproduced on pages 9 to 12 named as CMD :2. It may seem to the casual reader that the author 4 What To Do... and geoClub are praising CMD very highly. As Sharon Chambers perhaps the only supplier left to the serious C64 user it is perhaps just praise. Far too many CBM Message From... supplier have found user support very lacking GeoNut culminating it their demise. Even the original manufacturer has failed to support the very 5 Big Blue Reader people who put them where they were. CMD in Michael Miller continuing to support the C64 user deserves all the good publicity they can get. 9 C.M.D. :2 Dale Sidebottom Page 4 has a tip from Sharon on gluing back together that most important part of any plastic item that is always the one that breaks. Accompanying this is a message from geoNut with regard to a copyright free disk based LoadStar that should be available from the Library by the time you read this. Published by:- Frank Cassidy See you all in May — Happy Geosing 55, High Bank Road Droylsden (^frank Manchester M43 6FS PAGE 1 The April Disk Review Terry Watts Sharon Chambers 3, Rutland Avenue, 41, Albert Street, Borrowash, Cl HQ Crewe, Derby. -

Commodore 64 - Wikipedia
Commodore 64 - Wikipedia http://it.wikipedia.org/wiki/Commodore_64 Commodore 64 Da Wikipedia, l'enciclopedia libera. Il Commodore 64 ( C64 , C=64 , CBM 64 , Commodore 64 64 ) è stato un home computer molto popolare negli anni ottanta. Il nome adottato dalla casa costruttrice, la Commodore Business Machine, fu inizialmente Vic-30, ma prima della distribuzione venne cambiato in Commodore 64. Indice 1 Introduzione Classe di computer: Home computer 2 Storia Produttore: Commodore 2.1 Origini 2.2 Vincere la guerra del mercato Presentazione: Agosto 1982 2.3 I successori del C64 e il 64C Fine commercializzazione: Aprile 1994 2.4 Una demoscene attiva 3 L'hardware CPU: MOS Technology 6510 3.1 Il microprocessore 1.02 MHz (versione NTSC) Frequenza CPU: 3.2 Il chip video 0.985 MHz (versione PAL) 3.3 Il chip audio RAM di serie: 64 KB 3.4 Negli anni '90 e 2000 3.5 Revisioni dell'hardware Sistema operativo di serie: Commodore BASIC 2.0 4 Periferiche 4.1 Memorie di massa 4.1.1 Registratore a cassette 4.1.2 Drive per floppy disk 4.2 Comunicazione via seriale 4.3 Altre periferiche 5 Software 5.1 Sistema operativo 6 Varianti 6.1 Il case del primo modello 6.2 Commodore 64 - Prima versione 6.3 Commodore 64 - Seconda versione 6.4 Commodore MAX 6.5 Commodore SX-64 Executive 6.6 Commodore Educator 64 6.7 Commodore 64 Golden Edition 6.8 Commodore 64C 6.9 Commodore 64 "ALDI" 6.10 Commodore 64G 6.11 Commodore C64GS 6.12 Commodore C64DX (C65) 6.13 Commodore C64DTV 6.14 Commodore 64 (il ritorno) 7 Easter eggs e "patterns": i lati nascosti del Commodore 64 8 Nei media 1 di 19 19/06/2010 15.41 Commodore 64 - Wikipedia http://it.wikipedia.org/wiki/Commodore_64 9 Note 10 Voci correlate 11 Altri progetti 12 Collegamenti esterni 12.1 Emulatori Introduzione Il Commodore 64 risulta essere il modello di computer più venduto al mondo, record che si trova anche nel Guinness dei primati: nel 1986 furono venduti più di 10 milioni di esemplari in tutto il mondo. -

Commodore VIC 1541 Floppy Drive Users Manual
. II U n. : VIC-154'1 I [ill [)] g 11II II II 11II III III III 11II II a II .. II !I'" n " II i" i., I II n :d:j ~ commodore COMPUTER VIC-1541 SINGLE DRIVE FLOPPY DISK USER'S MANUAL P/N 1540031-02 ~ commodore COMPUTER WARNING: This equipment has been certified to comply with the limits for I!, Class B computing device, pursuant to Subpart J of Part 15 of FCC Rules. Only computers certified to comply with the Class B limits may be attached to this printer. Operation with noncertified computers is likely to result in interference to radio and TV reception," This warning is valid for the equipment which has the following FCC label on its rear. CERTIFIED TO COMPLY WITH CLASS B LIMITS. PART 15 OF FCC RULES SEE INSTRUCTIONS IF INTERFERENCE TO RADIO RECEPTION IS SUS- PECTED. The information in this manual has been reviewed and is believed to be entirely reliable. No responsibility, however, is assumed for inaccuracies. The material in this manual is for information purposes only, and is subject to change without lIotice. @Commodore BusinessMachines, Inc., September 1981 "All rights reserved." Table of Contents Page 1. General Description .............. 3 2. Unpacking and Connecting . 6 Contents of Box . 6 Connection of Cables 7 PoweringOn ........ 7 Insertion of I)jskette . 8 Usingwith VlC 20 or Commodore 64 . 8 3. UsingPrograms.............. 9 Loading Pre-packaged Software 9 LOAD . 9 Directoryof Disk . 9 Pattern Matching & Wild Cards 11 SAVE . 12 SAVE and replace. 13 VERIFY.. .. .. .. 13 DOS Support Program 14 4. Disk Commands . 14 OPEN ANDPRINT # 14 NEW .. -

Big Blue Reader® 128/64
SOGWAP Software •(Ii presents BIG BLUE READER® 128/64 Commodore® <=> IBM® PC ' File Transfer Utility For the Commodore 128 and 64 Requires the 1571/1581 Disk Drive BIG BLUE READER 128/64 TABLE OF CONTENTS Introduction and Thank You 1 System Requirements BIG BLUE READER 128/64 Features 2-3 Getting Started 3 Loading BBR 128 Loading BBR 64 MAIN MENU Options 4-9 LOAD DIR (Directory) 5 C128 Ahernate Display 6 COPY Files 6-7 PRINT Files 7 DISKCMDS 7-8 Big Blue Reader 128 SET-UP Program 19 Big Blue Reader 128 Options 8-9 VIEW DIRECTORY TIME & DATE UTILITIES CHANGE DRIVE 110 (C64 & C128) FORMAT MS-DOS DISK 1571 SPEED-UP UtIlity Programs 10-11 Big Blue Format 1581 MS-DOS Format Big Blue Backup Examine File AddlHonal Notes 11-14 READ.ME Files File types Foreign MFM CP/M Formats 17xx RAM Expansion Modules 1571 ROM Upgrade 1581 Disk Drive Using Two Disk Drives Help and Trouble-Shooting 14-15 Conversion Tips ASCII Files 16 Big Blue Reader 128/64 - Disk Formats 17 -18 BIG BLUE READER 128/64 Copyright 1986-90 by Michael R. Miller SOGWAP Software Thank you for your purchase of Big Blue Reader 128/64. Your purchase of this software allows us to continue to develop and produce high quality software. Big Blue Reader 128164 is a unique and powerful Commodore 1571 and 1581 disk utility designed to quickly and easily transfer word processing, text, ASCD, and binary files between standard Commodore 64/128 and IBM PC compatible MS-DOS disks. The enhanced Big Blue Reader 128 gives additional support for: True Burst mode file transfers, 2MHz microprocessor speed, the extra RAM including 17xx RAM expansion, 40 and 80 column displays, reading MS-DOS subdirectories, CI28 CP/M file transfers and much more. -

CMD FD Series User's Manual
Djsk Drives User's Manual For all FD Series Models Copyright Notice Copyright © 1992 by Creative Micro Designs, Inc. Fourth Edition, First Printing, October, 1993 All rights reserved. No part of this document may be reproduced, in any form or by any means either manually or electronically without written permission from Creative Micro Designs, Inc. The FD Disk Operating System (FD-DOS) is protected under International and United States Copyright Laws, and may not be copied, in whole or in part, without prior written permission from Creative Micro Designs, Inc. JiffyDOSTM, RAMLinkTM, FD-2000TM, FD-4000TM, and HD Series™ are trademarks of Creative Micro Designs, Inc. Commodore 64®, 64CTM, SX- 64™, C-128™, C-128-DTM, 154FM, 1541-CTM, 1541-IITM, 1571™, and 1581™ are trademarks or registered trademarks of Commodore Electronics Limited. Amiga™ is a trademark of Commodore Amiga. GEOSTM, GEOS deskTopTM, GEORAMTM, and Berkeley Softworks™ are trademarks of Berkeley Softworks. CP/M® is a registered trademark of Digital Research Corporation. IBM® is a registered trademark of International Business Machines. Table of Contents Section 1: General Information ,( Introduction ................................................................................... ~ 1 Features ......................................................................................... 1 Orders ........................................................................................... 2 Technical Assistance and Information .................................................. 2 Section -
Computing & IT Acronyms and Abbreviation.Xlsx
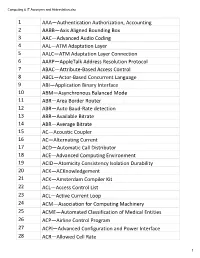
Computing & IT Acronyms and Abbreviation.xlsx 1 AAA—Authentication Authorization, Accounting 2 AABB—Axis Aligned Bounding Box 3 AAC—Advanced Audio Coding 4 AAL—ATM Adaptation Layer 5 AALC—ATM Adaptation Layer Connection 6 AARP—AppleTalk Address Resolution Protocol 7 ABAC—Attribute-Based Access Control 8 ABCL—Actor-Based Concurrent Language 9 ABI—Application Binary Interface 10 ABM—Asynchronous Balanced Mode 11 ABR—Area Border Router 12 ABR—Auto Baud-Rate detection 13 ABR—Available Bitrate 14 ABR—Average Bitrate 15 AC—Acoustic Coupler 16 AC—Alternating Current 17 ACD—Automatic Call Distributor 18 ACE—Advanced Computing Environment 19 ACID—Atomicity Consistency Isolation Durability 20 ACK—ACKnowledgement 21 ACK—Amsterdam Compiler Kit 22 ACL—Access Control List 23 ACL—Active Current Loop 24 ACM—Association for Computing Machinery 25 ACME—Automated Classification of Medical Entities 26 ACP—Airline Control Program 27 ACPI—Advanced Configuration and Power Interface 28 ACR—Allowed Cell Rate 1 Computing & IT Acronyms and Abbreviation.xlsx 29 ACR—Attenuation to Crosstalk Ratio 30 AD—Active Directory 31 AD—Administrative Domain 32 ADC—Analog-to-Digital Converter 33 ADC—Apple Display Connector 34 ADB—Apple Desktop Bus 35 ADCCP—Advanced Data Communications Control Procedures 36 ADO—ActiveX Data Objects 37 ADSL—Asymmetric Digital Subscriber Line 38 ADT—Abstract Data Type 39 AE—Adaptive Equalizer 40 AES—Advanced Encryption Standard 41 AF—Anisotropic Filtering 42 AFP—Apple Filing Protocol 43 AGP—Accelerated Graphics Port 44 AH—Active Hub 45 AI—Artificial -

Downloading Utilities, Sharing New Custom Programs and Files, and Pursuing Other Related Interests
Shaun M. Trujillo. Living Legacies: Recovering Data from 5¼” Floppy Disk Storage Media for the Commodore 64. A Master‟s Paper for the M.S. in I.S. degree. November, 2011. 97 pages. Advisor: Christopher Lee In an attempt to investigate the challenges of recovering and preserving digital objects from legacy systems this case study focuses on working with a particular storage medium and computing hardware. This study illustrates the physical and representational challenges that result from recovering data created with a Commodore 64 computer and stored on 5¼” floppy disks. A system for classifying types of digital objects found in the sample of recovered data was developed. This study contributes to the discourse of collecting institutions engaged in digital preservation and provides examples of ad hoc solutions for working through the challenges of recovering meaningful information from legacy systems. The issues that come to light in this study can be extended beyond the context of the Commodore 64 to include other types of digital resources and computing artifacts that will potentially cross the archival threshold in the near future. Headings: Data recovery (Computer science) Digital curation Personal archives Emulators (Computer programs) Commodore 64 (Computer) LIVING LEGACIES: RECOVERING DATA FROM 5¼” FLOPPY DISK STORAGE MEDIA FOR THE COMMODORE 64 by Shaun M. Trujillo A Master‟s paper submitted to the faculty of the School of Information and Library Science of the University of North Carolina at Chapel Hill in partial fulfillment of the requirements for the degree of Master of Science in Information Science. Chapel Hill, North Carolina November 2011 Approved by _______________________________________ Dr. -

Disk Reference Manual D9090 D9060 8250 8050 4040 2031
COMMODORE DISK REFERENCE MANUAL FOR D9090 D9060 8250 8050 4040 2031 NOTICE The information in this manual has been reviewed and is believed to be entirely reliable. However, Commodore assumes no responsibility for any inaccuracies. This is a preliminary manual v»*iich is provided for information purposes only and is subject to change without notice. It is being provided now, in preliminary form, so as not to delay introduction of new disk-storage products. A more complete and comprehensive version of this manual is being prepared and will be available soon. TABLE OF CCKTENTS Page Chapter 1 Introduction 5 General Information 5 Description D9090 & D9060 5 Description 8250 5 Description 8050 6 Description 4040 6 Description 2031 6 Preparing to use the Disk Unit 6 Unpacking the Disk Unit 6 Connecting the Disk Unit to the Computer 7 Performing the Power-On Test 7 Handling Diskettes 8 Disk Unit Specifications 9 Chapter 2 Learning How to Use Your Disk Drive 10 Conventions Used 11 Prerequisites 12 Files 12 The Disk Operating System (DOS) 12 The Block Availability Map (BAM) 13 Communicating with DOS 13 File Name Pattern Matching 14 Disk Maintenance Commands 15 Var iable Command Parameters 15 Command Abbreviations 16 HEADER 16 INITIALIZE 16 DIRECTORY/CATALOG 17 COLLECT 18 COPY <. 18 CONCAT 19 RENAME 19 SCRATCH 19 Chapter 3 Basic Commands for File Handling 21 Data File Coimiands 22 DSAVE (Writing a Program to a disk) 22 DLOAD (Reading a program from a disk) 22 DOPEN 23 DOLOSE 23 PRINT# 24 INPUT* 25 GET# 25 RECORD* 26 Chapter Advanced 4 Disk Progranming 27 Overview of DOS Versions 28 '.'.'.'.'. -

PDF: Warpspeed Manual with Schematics
CONGRATULATIONS! You now own the most useful and complete cartridge utility ever produced for the Commodore 64 and 128 computers: the Warp Speed™ Fast DOS Cartridge from Cinemaware. It contains the fastest Commodore-compatible DOS ever produced, allowing you to format disks, load, save, verify, and copy files up to ten times faster than before! In addition, Warp Speed includes: a full-featured machine language computer-and-disk-drive monitor/assembler, with up/down scrolling and an integrated sector editor; an expanded DOS wedge for convenience when using a disk drive; complete support for two or more disk drives, including a 30-second two-drive copier for making convenient backups of your unprotected disks; a reset button; and an "unnew" feature to restore BASIC programs, for recovering control of your computer when you experience a "crash". All Warp Speed functions work identically on the 64 and 128 in both 40- and 80-column modes, and are fully compatible with most commercial software, including many heavily protected programs that are incompatible with other cartridge utilities. They also work with most compatible disk drives, including the new Commodore 1581 floppy drives and several of the new hard disk drives available, as well as the MSD dual drive popular with many developers. Whether you are a beginner, a serious hacker, or a professional developer, you will find Warp Speed an indispensable aid which you may never remove from your computer once you have plugged it in! Fast Load/Save/Verify When the Warp Speed cartridge is inserted into the expansion port of your computer, the fast disk access routines are automatically engaged during all disk loads and saves.