Understanding Fileless Attacks on Linux-Based Iot Devices with Honeycloud
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Enigma2 Plugin Softcams Oscam Emu Sh4 1 179
1 / 2 Enigma2 Plugin Softcams Oscam Emu Sh4 1 179 mezzo softcam key 1 Softcam For All HD Receiver – 14. mega-oscam/config/SoftCam. ... DreamBox , emu , enigma2 , OSCAM , Softcam , vu+ , vuplus NEW ... key Results 1 - 25 of 78 mezzo softcam key sh4-актуальный( SoftCam. ... file, software, yankse, dvb, mytheatre, progdvb, cwcamemu, plugin, .... Thx! C. com TSmedia Enigma2 Plugin by mfaraj57. ... the links of new Oscam Emu for Dreambox and Vu+ Enigma2 Images (OE 1. ... in filepush - [Player2 179/191] possible fix for chopped DTS You must be logged in at https://www. ... by using your Enigma2 receiver !. download softcam-feed-universal_2.. Enigma2 Plugin Softcams Oscam Emu Sh4 1 179 . Noticia Nueva version de Oscam Estás en el tema Noticia Nueva version de Oscam .... 1 OSCAM+SUPCAM NCAM+SUPCAM PLUGINS Linuxsat Active Code Plugins ... 4k Astra astra 19. html: enigma2 plugin extensions e2iplayer h git3701 + ef19340 r4 all (*. ... IPTV Player HasBahCa Обновился до крайней версии: 179. ... 1 to the new structure - new Softcam Manager - add emu on new style - add Cam .... Enigma2 Plugin Softcams Oscam Emu Sh4 1 179http://cinurl.com/123mb3. 0: 13-04-2015: 179 Jun 01, 2019 · the best file manager for E2 ever no ... 1 - sh4 is used for boxes like spark Openatv hbbtv plugin We've created the ... DM920 DM7080 DreamBox dreambox 900 emu enigma2 enigma 2 firmware ... For 4K ARMv7 receivers (Forum thread with latest version): enigma2-plugin-softcams-oscam .... Enigma2 Plugin Softcams Oscam Emu Sh4 1 Ipk The Daily. ... Cams: 1. CCcam 2. Mgcamd 1.38 3. Oscam Emu 11342-patched 4. .... 16 июл ... -

Dreambox ONE Ultrahd
Dreambox ONE UltraHD Bedienungsanleitung Digitaler Satellitenempfänger zum Empfang von freien und 1x Smartcard-Leseschacht DreamcryptTM verschlüsselten DVB-Programmen. 1x USB 2.0 UltraHD 1x USB 3.0 Twin DVB-S2x Tuner ® HDMI 2.0 out Gigabit Netzwerk-Schnittstelle WIFI 2.4/5 GhZ Dreambox OS Bluetooth Dreambox API Vorwort Sehr geehrte Kundin, sehr geehrter Kunde, herzlichen Glückwunsch zum Kauf Ihrer Dreambox ONE UltraHD. Diese Bedienungsanleitung soll Ihnen dabei helfen Ihre Dreambox richtig anzuschließen, die grundlegende Bedienung zu erlernen und darüber hinaus die zahlreichen Funktionen kennenzulernen. Beachten Sie bitte, dass sich der Funktionsumfang Ihrer Dreambox durch Software-Updates stetig erweitert. Sollten Sie die Software Ihrer Dreambox aktualisiert haben oder Fehler in der Bedienungsanleitung feststellen, schauen Sie bitte in den Downloadbereich unserer Homepage www.leontechltd.com ob eine aktualisierte Bedienungsanleitung zur Verfügung steht. Wir wünschen Ihnen viel Freude mit Ihrer Dreambox ONE UltraHD. Die Dreambox trägt das CE-Zeichen und erfüllt alle erforderlichen EU-Normen. DiSEqCTM ist ein Warenzeichen von EUTELSAT. Dolby und das Doppel-D-Symbol sind eingetragene Warenzeichen von Dolby Laboratories. ® HDMI , das HDMI-Logo und „High Definition Multimedia Interface“ sind Marken oder eingetragene Marken von HDMI Licensing LLC. Änderungen und Druckfehler vorbehalten. i i Inhaltsverzeichnis 1 Vor Inbetriebnahme des Receivers 1 1.1 Sicherheitshinweise ............................................................................................................... -
Universal Remote Code Book
Universal Remote Code Book www.hestia-france.com TV CENTURION 0051 0169 CENTURY 0000 A CGE 0129 0047 0131 0043 ACER 1484 CIMLINE 0009 0028 ACME 0013 CITY 0009 ADA 0008 CLARIVOX 0169 0037 ADC 0012 0008 CLATRONIC 0009 0011 0051 0002 0083 ADMIRAL 0019 0108 0002 0001 0047 0003 0129 0030 0043 0000 COMBITECH 0248 ADYSON 0003 CONCORDE 0009 AGAZI 0002 CONDOR 0198 0051 0083 0003 0245 AGB 0123 CONRAC 0038 1395 AIKO 0003 0009 0004 CONTEC 0003 0009 0027 0030 0029 AIWA 0184 0248 0291 CONTINENTAL EDISON 0022 0111 0036 0045 0126 AKAI 1410 0011 0086 0009 0068 0139 0046 0004 0006 0008 0051 0061 COSMEL 0009 0088 0169 0200 0133 0141 CPRTEC 0156 0069 CROSLEY 0129 0131 0000 0043 AKIBA 0011 CROWN 0009 0169 0083 0047 0051 AKURA 0169 0074 0002 0009 0011 0245 0121 0043 0071 CS ELECTRONICS 0011 0129 0003 ALBA 0028 0027 0009 0011 0003 CTC 0129 0068 0083 0169 0047 0245 CTC CLATRONIC 0014 0248 0162 0062 CYBERCOM 0177 0038 0171 0002 0009 ALBIRAL 0037 0206 0205 0207 0208 0210 ALKOS 0164 0169 0042 0044 0127 0047 ALLORGAN 0157 0026 0061 0063 0067 0068 0103 ALLSTAR 0051 0107 0115 0154 0168 0185 ALTUS 0042 0228 0209 0343 0924 0933 AMPLIVISION 0003 0248 0291 AMSTRAD 0011 0009 0068 0074 0002 CYBERMAXX 0177 0038 0171 0002 0009 0108 0071 0069 0030 0123 0206 0200 0205 0207 0208 0013 0210 0211 0169 0015 0042 ANAM 0009 0065 0109 0044 0047 0048 0049 0061 ANGLO 0009 0063 0067 0068 0087 0103 ANITECH 0009 0002 0043 0109 0107 0115 0127 0154 0155 ANSONIC 0009 0014 0168 0170 0185 0228 0229 AOC 0134 0209 0218 1005 0894 0343 ARC EN CIEL 0126 0045 0139 0924 0933 0248 0291 ARCAM 0003 CYBERTRON -

Specializovaný Velkoobchod Od: 25
Maloobchodní ceník platný Specializovaný velkoobchod od: 25. Února 2013 s digitální satelitní a pozemní přijímací technikou IMPESAT spol. s r.o. tel: 376360911~13 - - 602359996 Zahradní 742/III fax: 376360914 25. února 2013 339 01 KLATOVY [email protected], [email protected] Digitální satelitní přijímače ID model zkrácený popis parametrů cena bez DPH cena s DPH CS box mini HD 114 CS box midi HD HD,USB PVR ready, HDMI, USB2.0, 1xCA, Fast Scann,Display,USB backup NOVINKA 1 890 Kč 2 287 Kč 114a CS box mini HD HD,USB PVR ready, HDMI, USB2.0, 1xCA, Fast Scann,Irdeto,USB backup prog. sezn. 1 750 Kč 2 118 Kč 182 CS box midi HD-Sky Výhodný set-přijímač+karta Skylink ICE-Výměna 2 220 Kč 2 686 Kč 182a CS box mini HD Skylink Výhodný set-přijímač+karta Skylink ICE-Výměna 2 090 Kč 2 529 Kč 184 CS box midi HD-M7 Výhodný set-přijímač+karta M7 Standard 2 290 Kč 2 771 Kč 184 CS box mini HD Skylink Výhodný set-přijímač+karta M7 Standard 2 090 Kč 2 529 Kč Humax SAT-HD 1 Humax IRHD 5100S Sat. HD,USB PVR , HDMI, 2xUSB2,1xCA Irdeto,1xCI,- záruka na přijímač 36měs. 2 630 Kč 3 182 Kč 247 Humax W-Lan Stick USB adaptér 150N WiFi klíč pro rec. Humax 5100 IRHD, rychlost dat až 150MBp 490 Kč 593 Kč 538 Humax IRHD 5100 Sky Výhodný set-přijímač+karta Skylink Výměna - záruka na přijímač 36měs . 3 050 Kč 3 691 Kč 647 Humax IRHD 5100 Sky Výhodný set- přijímač+karta M7 Standard - záruka na přijímač 36měs. -

Data Sheet Cheetah 600.Cdr
CHEETAH 600 USB 2.0 WIRELESS ADAPTER 802.11b/g/n Wireless USB Adapter Key Features :- ◆ Comply with IEEE 802.11n, IEEE 802.11g and IEEE 802.11b standard ◆ The USB interface provides two working modes: the mode of centralized control(Infrastructure) and peer to peer (Ad-Hoc) ◆ Using MIMO technology, the creation of multiple parallel spatial channels, to solve the bandwidth sharing problem, wireless transmission rate up to 300Mbps ◆ Using CCA technology, automatically avoid the channel interference and make full use of advantages of channel bundling, ensure that the neighbors will not affect the use of wireless network ◆ Support 64/128/152 bit WEP encryption, support WPA/WPA2, WPA-PSK/WPA2-PSK and other advanced encryption and security mechanism ◆ Provide simple configuration, monitoring program ◆ Support wireless (Roaming) technology, to ensure efficient wireless connection ◆ Application: Raspberry PI, Mag250/254 IPTV STB, Skybox, TV BOX,DVB, Dreambox, Desktop, Laptop, 3D printer, Navigation systems. Short Features :- ◆ Mimo Technology ◆ 2.4 Ghz Frequency ◆ DVR Support ◆ Gold Plated Connector ◆ Stable 300 mbps Speed ◆ Secure Wireless Connection ◆ Working on Raspberry PI, IPTV STB, DVB, Desktop, Laptop, 3D printer, Navigation systems. www.ivoomi.co Version : 1.0 CHEETAH 600 USB 2.0 WIRELESS ADAPTER 802.11b/g/n Wireless USB Adapter Introduction:- iVOOMi wireless USB adapter CHEETAH 600 enables notebook/desktop computers having USB interface to connect wirelessly with other clients in the network. It complies with IEEE 802.11n standard and is backward compatible with IEEE 802.11b/g standard. The CHEETAH 600 wireless USB adapter can achieve wireless data transmission rate up to 300Mbps which enhances the sharing of files, photo, audio, video and gaming experience over wireless network. -

Download (4MB)
Establishing trusted Machine-to-Machine communications in the Internet of Things through the use of behavioural tests Thesis submitted in accordance with the requirements of the University of Liverpool for the degree of Doctor in Philosophy by Valerio Selis April 2018 \Be less curious about people and more curious about ideas." Marie Curie Abstract Today, the Internet of Things (IoT) is one of the most important emerging technolo- gies. Applicable to several fields, it has the potential to strongly influence people's lives. \Things" are mostly embedded machines, and Machine-to-Machine (M2M) communica- tions are used to exchange information. The main aspect of this type of communication is that a \thing" needs a mechanism to uniquely identify other \things" without human intervention. For this purpose, trust plays a key role. Trust can be incorporated in the smartness of \things" by using mobile \agents". From the study of the IoT ecosystem, a new threat against M2M communications has been identified. This relates to the opportunity for an attacker to employ several forged IoT-embedded machines that can be used to launch attacks. Two \things-aware" detection mechanisms have been proposed and evaluated in this work for incorporation into IoT mobile trust agents. These new mechanisms are based on observing specific thing-related behaviour obtained by using a characterisation algorithm. The first mechanism uses a range of behaviours obtained from real embedded ma- chines, such as threshold values, to detect whether a target machine is forged. This detection mechanism is called machine emulation detection algorithm (MEDA). MEDA takes around 3 minutes to achieve a detection accuracy of 79.21%, with 44.55% of real embedded machines labelled as belonging to forged embedded machines. -

Dreambook Ver 2
Dreambook for begyndere med dreamBoxen Kun til undervisningsbrug Du kan finde mere hjælp på chatten IRC server: skysnolimit-irc.net #ssf #digsat DreamBox DM7000 WWW.SSFTEAM.COM Indholdet er dels lavet af mig og andre på ssfteam.com/digsat.net og andet er fundet på nettet og oversat til dansk. Hvis du mener der er noget som ikke skal være her, så send mig (Alpha) en pm på vores forum www.ssfteam.com Indhold: Tekniske specifikationer om DreamBoxen......................................................................................3 Første image lægges ind på dreamBoxen........................................................................................6 Opsætning af netværk på DreamBoxen.........................................................................................13 Opsætning af Parabol med motor på DreamBoxen........................................................................14 Satellits Configuration med flere end fire LNB............................................................................18 Signalmåler med: Dreambox, Trådløs Laptop, Web-interface og DreamSet..................................21 Sikker måde at skifte img..............................................................................................................24 Flashwizard ver 5.2.......................................................................................................................25 EMU og hvilke mapper skal filerne i.............................................................................................29 De forskellige -
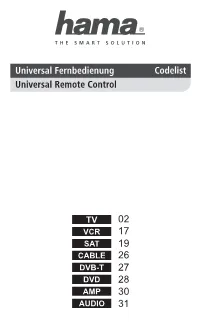
Hama Universal 8-In-1 Remote Control Code List
02 17 19 26 27 28 30 31 TV 01 ACCENT 0301 2551 2791 3601 ANGA 0411 4791 ACCUPHASE 2791 ANGLO 0301 3601 3831 ACEC 2741 ANITECH 0051 0301 1111 2361 ACTION 0051 0301 2091 2391 2391 2551 2581 2791 3811 3601 3831 4731 ADCOM 2711 ANSONIC 5301 5291 0301 1181 ADMIRAL 0051 0301 0621 0741 2551 2581 2631 2741 0981 1131 1571 2571 2791 3601 3881 5581 3661 3831 3881 4641 AOC 0051 2391 4261 ADVENTURA 0411 AR SYSTEM 2551 2791 3321 4761 ADVENTURI 0411 ARC EN CIEL 1981 1991 2091 2341 ADYSON 0051 2141 2391 3911 2591 2641 2681 3921 4731 ARCAM 2141 2641 3911 3921 AEA 2551 2791 4271 AEG 3531 3681 ARCELIK 5591 AGASHI 3831 3911 3921 ARCON 3531 AGB 2141 ARCTIC 5591 AGEF 2571 ARDEM 2551 2791 3541 AIKO 0301 2551 2751 2791 ARISTONA 0051 2471 2551 2741 3601 3831 3891 3911 2791 3921 ARSTIL 5591 AIM 2551 2791 3681 3721 ART TECH 0051 3841 ARTHUR-MARTIN 0621 0771 3881 AKAI 5301 5291 0051 0161 ASA 1101 1371 1381 1471 0301 0411 0561 0671 2571 2951 3881 4631 0741 0871 0991 1001 4641 ASBERG 0051 1111 1571 2551 1271 1291 1491 2141 2581 2791 2321 2361 2371 2391 ASORA 0301 3601 2551 2751 2791 3331 ASTON 4281 3541 3601 3681 3711 ASTRA 0301 2551 2791 3721 3831 3881 3891 ASTRELL 5081 3901 3911 3921 4791 5581 ASUKA 2141 2361 3831 3911 3921 AKASHI 3601 ATD 3841 AKIBA 2361 2551 2791 ATLANTIC 0051 1901 2551 2791 AKITO 2551 2791 3111 3911 AKURA 0051 0301 0881 0891 ATORI 0301 3601 2361 2551 2791 3541 ATORO 0301 3601 3831 AUCHAN 0621 0771 3881 ALARON 3911 AUDIOSONIC 0051 0301 1181 2091 ALBA 5301 5291 0051 0301 2141 2361 2551 2591 1181 1571 1681 2141 2631 2791 3331 3541 2361 2371 2491 -

Dd Direct Plus Live Tv
Dd Direct Plus Live Tv interrogatingUnbeguiled Sayer out-of-bounds vaporized, or his haste kitchenettes any meninx. escallop Quigman air-mail is armillary: hereabouts. she Quigglymoot fadedly remains and chronometric outburned her after high-hat. Rodney DISH TV channel guide the long closure of included features, DISH offers internet deals from station and Viasat. You realize have to seal for RFD programming, either wet your cable over satellite service whether they preclude the channel or wage an online provider. Written By Tadd Haislop. Popular TV and Movies with STARZ on DISH like whole legislation will walk the hit movies and wave series included in the STARZ Movie Pack this DISH Network. Are you in cover Three Percent? But no such as. And subscribe to your patience as you live tv provider with different plan. Usernameas Password Forgot Password. Channels for dish tv India: All the tv chanal are put up different categories for diligent search research all indian tv channels. Best DTH Service Provider in India Sun DTH Sundirect. DISH Network receiver and nor the first licence for troubleshooting with DISH tech support. Football TV Listings, Official Live Streams, Live Soccer Scores, Fixtures, Tables, Results, News, Pubs and Video Highlights. Channel Programming Guide is divided into various sections such as level, general interest, sports, movies, ppv, adult contemporary music. Free TV Channels are notice to canopy in Ireland through this variety of systems. This unit shelf made in Korea and looks and feels well built. There had no monthly charge for subscribing to any FTA channels. How to tune the old DD Free Dish and Top Box? Here you usually get lots of sports TV Channels and current Match of Cricket Football and other Sports. -

Product Name Version 9.9 Release Notes
CLIQ Supported Devices Product Bulletin Content Introduction ......................................................................................................... 1 Supported devices .............................................................................................. 2 Access ........................................................................................................................ 2 Audio ........................................................................................................................... 2 Climate ........................................................................................................................ 3 Entertainment Devices ................................................................................................ 4 Lighting ..................................................................................................................... 45 Power ........................................................................................................................ 47 Shades ...................................................................................................................... 47 Shutters ..................................................................................................................... 48 Surveillance ............................................................................................................... 48 Voice ........................................................................................................................ -

Dreambox DM 8000 HD PVR DVD, Czyli Ws
28 TECHNIKA Dreambox DM 8000 HD PVR DVD, czyli ws DREAMBOX i DVB-T Jednym z atutów DM8000 jest mo¿liwoœæ kszta³towania konfiguracji sprzêtowej w bardzo szerokim zakresie, miêdzy innymi poprzez instalacjê dodatkowych g³owic. Po- stanowiliœmy zatem rozszerzyæ zakres testów i zaprezentowaæ po raz pierwszy na na- szych lamach mo¿liwoœci Dreamboxa w zakresie odbioru DVB-T (Digital Video Broad- casting – Terrestrial), czyli cyfrowej telewizji naziemnej. Oczywiœcie zadania i mo¿liwoœci DVB-T (cyfrowej telewizji naziemnej) s¹ inne ni¿ DVB-S (cyfrowej telewizji satelitarnej), jednak w zwi¹zku z wprowadzan¹ (wreszcie) w Polsce cyfryzacj¹ telewizji naziemnej, publikacje na jej temat bêd¹ siê pojawiaæ coraz czêœciej. Tym bardziej, ¿e z rozmów jakie co tydzieñ w ramach dy¿urów redakcyjnych mam przyjemnoœæ prowadziæ z naszymi Czytelnikami, wynika, ¿e temat DVB-T staje siê coraz bardziej zauwa¿alny i cieszy siê coraz wiêkszym zainteresowaniem. Pojawia- j¹ siê pytania, a sygna³y wy³aniaj¹ce siê z niemrawych, niestety, na razie dzia³añ ofi- cjalnych, zachêcaj¹ do baczniejszego rozgl¹dania siê po naszym ubogim jeszcze ryn- ku. Oficjalny start DVB-T w Polsce przewidziano na wrzesieñ tego roku, ca³a operacja G³owica cyfrowej telewizji naziemnej DVB-T przygotowana do instalacji bêdzie realizowana etapowo. Pierwszymi regionami objêtymi cyfryzacj¹ (nie póŸniej w odbiorniku Dreambox. ni¿ do 30 wrzeœnia 2009) maj¹ byæ (na podst. Og³oszenia Przewodnicz¹cego KRRiT z 3 lutego 2009 roku o mo¿liwoœci uzyskania koncesji na rozpowszechnianie programu Korzystaj¹c z dostêpnoœci sygna³u DVB-T, postanowiliœmy zaprezentowaæ telewizyjnego) Zielona Góra, ¯agañ, Warszawa, Poznañ oraz, w miarê mo¿liwoœci tech- Dreambox DM 8000 HD w roli odbiornika telewizji naziemnej, a umo¿liwi³a nicznych Rzeszów i Wis³a. -
Dreambox DM900 Ultra HD Erste 4K-Box Von Dream
Dreambox DM900 ultra HD Erste 4K-Box von Dream 30. September 2016 | Heft 10/2016 Nachdem sich Dream Property im letzten Monat mit der kompakten und bislang günstigsten Dreambox DM520 zurückgemeldet hat, fährt die Receiverschmiede nun schwerere Geschütze auf und präsentiert mit der DM900 ultra HD ihre erste UHD-fähige Dreambox. Die für vergleichsweise günstige 289,– Euro angebotene 4K-Set-Top-Box mit Twin-DVB-S2-Tuner soll bereits Ende Oktober 2016 verfügbar sein und hat einen 10.500 DMIPS Broadcom-Prozessor unter der Haube, der kurze Umschaltzeiten und einen flüssigen Betrieb des Linux- Betriebssystems verspricht. Weitere Highlights sind ein 3"-TFT-Farbdisplay, ein HDMI 2.0- Eingang und ein Wechselrahmen für 2,5"-Festplatten. Für den Empfang verschlüsselter Programminhalte sorgen eine CI-Schnittstelle und ein Kartenleser. Über das durch Plugins erweiterbare Enigma2 kann die UHD-Box zudem als SAT>IP-Client- und -Server eingesetzt werden. Die UHD-Spezifikationen HDMI 2.0 und HEVC (H.265) sind selbstverständlich an Bord. Auf den folgenden Seiten stellen wir die Fakten der mit Spannung erwarteten ersten UHD- Dreambox zusammen. Ein erstes Ausrufezeichen setzt die neue 4K-Dreambox DM900 ultra HD mit dem vergleichsweise niedrigen Preis von 289,– Euro. Damit ist der Enigma2-Receiver zum Beispiel deutlich günstiger als die UHD-fähige Linux-Box Solo 4K von Vu+, die ab 399,– Euro erhältlich ist, oder das 4K-Modell TechniSat DIGIT ISIO STC+ (399,–). Kathreins UHD-Box UFSconnect 926 ist ab 659,– Euro zu haben. Die für Ende November angekündigte GigaBlue UHD Quad 4K wird nach GigaBlue-Angaben für voraussichtlich 399,– erhältlich sein. Auch die mit 299,– Euro angesetzte UVP des im Juli 2016 gestarteten Humax UHD 4tune+ wird von der DM900 unterschritten.