The Logtalk Handbook Release V3.51.0-B01
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

New Inheritance Models That Facilitate Source Code Reuse in Object-Oriented Programming
NEW INHERITANCE MODELS THAT FACILITATE SOURCE CODE REUSE IN OBJECT- ORIENTED PROGRAMMING By HISHAM M. AL-HADDAD Bachelor of Science Yarmouk University lrbid, Jordan 1986 Master of Science Northrop University Los Angeles, California 1988 Submitted to the Faculty of the Graduate College of the Oklahoma State University in partial fulfillment of the requirements for the degree of DOCTOR OF PHILOSOPHY July, 1992 Oklahoma Statt.' Ur1iv. Library NEW INHERITANCE MODELS THAT FACILITATE SOURCE CODE REUSE IN OBJECT- ORIENTED PROGRAMMING C/ wU::r-~ B I A~c;p .... _.-~ Dean of the Graduate CoUege ii PREFACE Code reusability is a primary objective in the development of software systems. The object-oriented programming methodology is one of the areas that facilitate the development of software systems by allowing and promoting code reuse and modular designs. Object-oriented programming languages (OOPLs) provide different facilities to attain efficient reuse and reliable extension of existing software components. Inheritance is an important language feature that is conducive to reusability and extensibility. Various OOPLs provide different inheritance models based on different interpretations of the inheritance notion. Therefore, OOPLs have different characteristics derived from their respective inheritance models. This dissertation is concerned with solutions for three major problems that limit the utilization of inheritance for code reusability. The range of object-oriented applications and thus the usage of object-oriented programming in general is also discussed. The three major problems are: 1) the relationship between inheritance and other related issues such as encapsulation, access techniques, visibility of inheritance, and subtyping; 2) the hierarchical structure imposed by inheritance among classes; and 3) the accessibility of previous versions of the modified methods defmed in classes located at higher levels of the inheritance structure than the parent classes. -
Attachment A
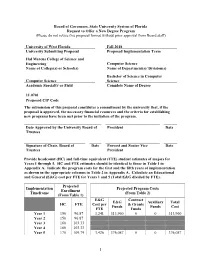
Board of Governors, State University System of Florida Request to Offer a New Degree Program (Please do not revise this proposal format without prior approval from Board staff) University of West Florida Fall 2018 University Submitting Proposal Proposed Implementation Term Hal Marcus College of Science and Engineering Computer Science Name of College(s) or School(s) Name of Department(s)/ Division(s) Bachelor of Science in Computer Computer Science Science Academic Specialty or Field Complete Name of Degree 11.0701 Proposed CIP Code The submission of this proposal constitutes a commitment by the university that, if the proposal is approved, the necessary financial resources and the criteria for establishing new programs have been met prior to the initiation of the program. Date Approved by the University Board of President Date Trustees Signature of Chair, Board of Date Provost and Senior Vice Date Trustees President Provide headcount (HC) and full-time equivalent (FTE) student estimates of majors for Years 1 through 5. HC and FTE estimates should be identical to those in Table 1 in Appendix A. Indicate the program costs for the first and the fifth years of implementation as shown in the appropriate columns in Table 2 in Appendix A. Calculate an Educational and General (E&G) cost per FTE for Years 1 and 5 (Total E&G divided by FTE). Projected Implementation Projected Program Costs Enrollment Timeframe (From Table 2) (From Table 1) E&G Contract E&G Auxiliary Total HC FTE Cost per & Grants Funds Funds Cost FTE Funds Year 1 150 96.87 3,241 313,960 0 0 313,960 Year 2 150 96.87 Year 3 160 103.33 Year 4 160 103.33 Year 5 170 109.79 3,426 376,087 0 0 376,087 1 Note: This outline and the questions pertaining to each section must be reproduced within the body of the proposal to ensure that all sections have been satisfactorily addressed. -

The Circle Meta-Model
Document:P2062R0 Revises: (original) Date: 01-11-2020 Audience: SG7 Authors: Wyatt Childers ([email protected]) Andrew Sutton ([email protected]) Faisal Vali ([email protected]) Daveed Vandevoorde ([email protected]) The Circle Meta-model Introduction During the November 2019 meeting in Belfast, some of the SG7 participants enthusiastically mentioned Circle1 as providing a more intuitive compile-time programming model and suggested that SG7 investigate overhauling the de-facto SG7 approach (P1240+P17332) to follow Circle's general approach (to reflection and metaprogramming). This paper describes a framework for understanding metaprogramming systems and provides a high-level overview of some of Circle's main characteristics, contrasting them to P1240's approach augmented with an injection mechanism along the lines of P1717. While we appreciate some of Circle’s powerful capabilities, we also raise some concerns with its underlying model and provide arguments in support of P1240’s choices as being a more suitable fit for C++’s evolution. The Dimensions of Reflective Programming In P0633, we identified three “dimensions” of compile-time reflective metaprogramming: 1. Control: How are compile-time computations effected/interpreted? What are metaprograms? 2. Reflection: How are source constructs are made available as data for use in metaprograms? 3. Synthesis: How can “code” be generated from a programmatic representation? 1 https://www.circle-lang.org/ Circle is an impressive project: Sean Baxter developed a brand new C++17-like front end on top of LLVM, incorporating a variety of new compile-time capabilities that align closely with SG7's goals. For Sean’s motivations, see https://github.com/seanbaxter/circle/blob/master/examples/README.md#why-i-wrote-circle. -

Generic Programming
Generic Programming July 21, 1998 A Dagstuhl Seminar on the topic of Generic Programming was held April 27– May 1, 1998, with forty seven participants from ten countries. During the meeting there were thirty seven lectures, a panel session, and several problem sessions. The outcomes of the meeting include • A collection of abstracts of the lectures, made publicly available via this booklet and a web site at http://www-ca.informatik.uni-tuebingen.de/dagstuhl/gpdag.html. • Plans for a proceedings volume of papers submitted after the seminar that present (possibly extended) discussions of the topics covered in the lectures, problem sessions, and the panel session. • A list of generic programming projects and open problems, which will be maintained publicly on the World Wide Web at http://www-ca.informatik.uni-tuebingen.de/people/musser/gp/pop/index.html http://www.cs.rpi.edu/˜musser/gp/pop/index.html. 1 Contents 1 Motivation 3 2 Standards Panel 4 3 Lectures 4 3.1 Foundations and Methodology Comparisons ........ 4 Fundamentals of Generic Programming.................. 4 Jim Dehnert and Alex Stepanov Automatic Program Specialization by Partial Evaluation........ 4 Robert Gl¨uck Evaluating Generic Programming in Practice............... 6 Mehdi Jazayeri Polytypic Programming........................... 6 Johan Jeuring Recasting Algorithms As Objects: AnAlternativetoIterators . 7 Murali Sitaraman Using Genericity to Improve OO Designs................. 8 Karsten Weihe Inheritance, Genericity, and Class Hierarchies.............. 8 Wolf Zimmermann 3.2 Programming Methodology ................... 9 Hierarchical Iterators and Algorithms................... 9 Matt Austern Generic Programming in C++: Matrix Case Study........... 9 Krzysztof Czarnecki Generative Programming: Beyond Generic Programming........ 10 Ulrich Eisenecker Generic Programming Using Adaptive and Aspect-Oriented Programming . -

Code Reuse and Refactoring: Going Agile on Complex Products
Code Reuse and Refactoring: Going Agile on Complex Products Using enterprise Software Version Management to coordinate complex products, seamlessly support Git developers, and solve refactoring problems. Table of Contents Component-Based Development __________________________________________________ 1 CBD Product Model ______________________________________________________________ 1 The Repository Model ____________________________________________________________ 2 Managing CBD in Git _____________________________________________________________ 2 Setting Up the CBD Model _____________________________________________________ 2 Incorporating Non-Software Components ____________________________________ 3 Updating Component Baselines ________________________________________________ 3 Submitting Patches to Components _____________________________________________ 4 Developer View _______________________________________________________________ 4 Refactoring: In Practice ________________________________________________________ 4 Refactoring: Developer Impact _________________________________________________ 4 Managing CBD in Perforce Software Version Management and Perforce Git Fusion ______ 5 Setting Up the CBD Model _____________________________________________________ 5 Incorporating Non-Software Components ____________________________________ 5 Updating Component Baselines ________________________________________________ 5 Submitting Patches to Components _____________________________________________ 5 Developer View _______________________________________________________________ -

Comparative Studies of Programming Languages; Course Lecture Notes
Comparative Studies of Programming Languages, COMP6411 Lecture Notes, Revision 1.9 Joey Paquet Serguei A. Mokhov (Eds.) August 5, 2010 arXiv:1007.2123v6 [cs.PL] 4 Aug 2010 2 Preface Lecture notes for the Comparative Studies of Programming Languages course, COMP6411, taught at the Department of Computer Science and Software Engineering, Faculty of Engineering and Computer Science, Concordia University, Montreal, QC, Canada. These notes include a compiled book of primarily related articles from the Wikipedia, the Free Encyclopedia [24], as well as Comparative Programming Languages book [7] and other resources, including our own. The original notes were compiled by Dr. Paquet [14] 3 4 Contents 1 Brief History and Genealogy of Programming Languages 7 1.1 Introduction . 7 1.1.1 Subreferences . 7 1.2 History . 7 1.2.1 Pre-computer era . 7 1.2.2 Subreferences . 8 1.2.3 Early computer era . 8 1.2.4 Subreferences . 8 1.2.5 Modern/Structured programming languages . 9 1.3 References . 19 2 Programming Paradigms 21 2.1 Introduction . 21 2.2 History . 21 2.2.1 Low-level: binary, assembly . 21 2.2.2 Procedural programming . 22 2.2.3 Object-oriented programming . 23 2.2.4 Declarative programming . 27 3 Program Evaluation 33 3.1 Program analysis and translation phases . 33 3.1.1 Front end . 33 3.1.2 Back end . 34 3.2 Compilation vs. interpretation . 34 3.2.1 Compilation . 34 3.2.2 Interpretation . 36 3.2.3 Subreferences . 37 3.3 Type System . 38 3.3.1 Type checking . 38 3.4 Memory management . -

A Model of Inheritance for Declarative Visual Programming Languages
An Abstract Of The Dissertation Of Rebecca Djang for the degree of Doctor of Philosophy in Computer Science presented on December 17, 1998. Title: Similarity Inheritance: A Model of Inheritance for Declarative Visual Programming Languages. Abstract approved: Margaret M. Burnett Declarative visual programming languages (VPLs), including spreadsheets, make up a large portion of both research and commercial VPLs. Spreadsheets in particular enjoy a wide audience, including end users. Unfortunately, spreadsheets and most other declarative VPLs still suffer from some of the problems that have been solved in other languages, such as ad-hoc (cut-and-paste) reuse of code which has been remedied in object-oriented languages, for example, through the code-reuse mechanism of inheritance. We believe spreadsheets and other declarative VPLs can benefit from the addition of an inheritance-like mechanism for fine-grained code reuse. This dissertation first examines the opportunities for supporting reuse inherent in declarative VPLs, and then introduces similarity inheritance and describes a prototype of this model in the research spreadsheet language Forms/3. Similarity inheritance is very flexible, allowing multiple granularities of code sharing and even mutual inheritance; it includes explicit representations of inherited code and all sharing relationships, and it subsumes the current spreadsheet mechanisms for formula propagation, providing a gradual migration from simple formula reuse to more sophisticated uses of inheritance among objects. Since the inheritance model separates inheritance from types, we investigate what notion of types is appropriate to support reuse of functions on different types (operation polymorphism). Because it is important to us that immediate feedback, which is characteristic of many VPLs, be preserved, including feedback with respect to type errors, we introduce a model of types suitable for static type inference in the presence of operation polymorphism with similarity inheritance. -

Sub-Method Structural and Behavioral Reflection Marcus Denker
Sub-method Structural and Behavioral Reflection Marcus Denker To cite this version: Marcus Denker. Sub-method Structural and Behavioral Reflection. Computer Science [cs]. Universität Bern, 2008. English. tel-00555937 HAL Id: tel-00555937 https://tel.archives-ouvertes.fr/tel-00555937 Submitted on 14 Jan 2011 HAL is a multi-disciplinary open access L’archive ouverte pluridisciplinaire HAL, est archive for the deposit and dissemination of sci- destinée au dépôt et à la diffusion de documents entific research documents, whether they are pub- scientifiques de niveau recherche, publiés ou non, lished or not. The documents may come from émanant des établissements d’enseignement et de teaching and research institutions in France or recherche français ou étrangers, des laboratoires abroad, or from public or private research centers. publics ou privés. Sub-method Structural and Behavioral Reflection Inauguraldissertation der Philosophisch-naturwissenschaftlichen Fakultät der Universität Bern vorgelegt von Marcus Denker von Deutschland Leiter der Arbeit: Prof. Dr. O. Nierstrasz Institut für Informatik und angewandte Mathematik Von der Philosophisch-naturwissenschaftlichen Fakultät angenommen. Bern, 26.05.2008 Der Dekan: Prof. Dr. P. Messerli This dissertation is available as a free download from http://scg.unibe.ch Copyright © 2008 Marcus Denker. The contents of this dissertation are protected under Creative Commons Attribution-ShareAlike 3.0 Unported license. You are free: to Share — to copy, distribute and transmit the work to Remix — to adapt the work Under the following conditions: Attribution. You must attribute the work in the manner specified by the author or licensor (but not in any way that suggests that they endorse you or your use of the work). -

Beginning SOLID Principles and Design Patterns for ASP.NET Developers — Bipin Joshi Beginning SOLID Principles and Design Patterns for ASP.NET Developers
THE EXPERT’S VOICE® IN .NET DEVELOPMENT Beginning SOLID Principles and Design Patterns for ASP.NET Developers — Bipin Joshi Beginning SOLID Principles and Design Patterns for ASP.NET Developers Bipin Joshi Beginning SOLID Principles and Design Patterns for ASP.NET Developers Bipin Joshi 301 Pitruchhaya Thane, India ISBN-13 (pbk): 978-1-4842-1847-1 ISBN-13 (electronic): 978-1-4842-1848-8 DOI 10.1007/978-1-4842-1848-8 Library of Congress Control Number: 2016937316 Copyright © 2016 by Bipin Joshi This work is subject to copyright. All rights are reserved by the Publisher, whether the whole or part of the material is concerned, specifically the rights of translation, reprinting, reuse of illustrations, recitation, broadcasting, reproduction on microfilms or in any other physical way, and transmission or information storage and retrieval, electronic adaptation, computer software, or by similar or dissimilar methodology now known or hereafter developed. Exempted from this legal reservation are brief excerpts in connection with reviews or scholarly analysis or material supplied specifically for the purpose of being entered and executed on a computer system, for exclusive use by the purchaser of the work. Duplication of this publication or parts thereof is permitted only under the provisions of the Copyright Law of the Publisher's location, in its current version, and permission for use must always be obtained from Springer. Permissions for use may be obtained through RightsLink at the Copyright Clearance Center. Violations are liable to prosecution under the respective Copyright Law. Trademarked names, logos, and images may appear in this book. Rather than use a trademark symbol with every occurrence of a trademarked name, logo, or image we use the names, logos, and images only in an editorial fashion and to the benefit of the trademark owner, with no intention of infringement of the trademark. -

Software Reusability: Approaches and Challenges
International Journal of Research and Innovation in Applied Science (IJRIAS) |Volume VI, Issue V, May 2021|ISSN 2454-6194 Software Reusability: Approaches and Challenges Moko Anasuodei1, Ojekudo, Nathaniel Akpofure2 1Department of Computer Science and Informatics, Faculty of Science, Federal University Otuoke, Nigeria 2Department of Computer Science, Faculty of Natural and Applied Sciences, Ignatius Ajuru University of Education, Nigeria Abstract: Software reuse is used to aid the software phases. Software engineering has been more centered on development process which in recent times can improve the original development which gives an optimal software at a resulting quality and productivity of software development, by faster and less costly price, a design process based on assisting software engineers throughout various software systemic reusable is now recognized. engineering phases to enhance the quality of software, provide quick turnaround time for software development using few Software reuse reduces efforts and cost, because software people, tools, and methods, which creates a good software development costs can be extremely high, but they are quality by enhancing integration of the software system to shared, such that the cost of reuse can be extremely low. provide a competitive advantage. This paper examines the One major advantage of software reuse suggested by concept of software reuse, the approaches to be considered for keswani et al (2014) explains that there is a significant need software reuse, which is broadly shared into three categories: component-based software reuse, domain engineering and for the number of bugs to be reduced during software software product lines, architecture-based software reuse and development process, such that instead of developing an challenges that affect the software reuse development process. -

Directly Reflective Meta-Programming
Directly Reflective Meta-Programming ∗ Aaron Stump Computer Science and Engineering Washington University in St. Louis St. Louis, Missouri, USA [email protected] Abstract Existing meta-programming languages operate on encodings of pro- grams as data. This paper presents a new meta-programming language, based on an untyped lambda calculus, in which structurally reflective pro- gramming is supported directly, without any encoding. The language fea- tures call-by-value and call-by-name lambda abstractions, as well as novel reflective features enabling the intensional manipulation of arbitrary pro- gram terms. The language is scope safe, in the sense that variables can neither be captured nor escape their scopes. The expressiveness of the language is demonstrated by showing how to implement quotation and evaluation operations, as proposed by Wand. The language's utility for meta-programming is further demonstrated through additional represen- tative examples. A prototype implementation is described and evaluated. Keywords: lambda calculus, reflection, meta-programming, Church en- coding, Mogensen-Scott encoding, Wand-style fexprs, alpha equivalence, language implementation. 1 Introduction This paper presents a new meta-programming language called Archon, in which programs can operate directly on other programs as data. Existing meta- programming languages suffer from defects such as encoding programs at too low a level of abstraction, or in a way that bloats the encoded program terms. Other issues include the possibility for variables either to be captured or escape their static scopes. Archon rectifies these defects by trading the complexity of the reflective encoding for additional programming constructs. We adopt ∗This work is supported by funding from the U.S. -
![[Lirmm-00862477, V1] Bridging the Gap Between Component-Based Design and Implementation with a Reflective Programming Language](https://docslib.b-cdn.net/cover/8348/lirmm-00862477-v1-bridging-the-gap-between-component-based-design-and-implementation-with-a-reflective-programming-language-1008348.webp)
[Lirmm-00862477, V1] Bridging the Gap Between Component-Based Design and Implementation with a Reflective Programming Language
Design and Implementation of a reflective Component-based programming and modeling language Bridging the Gap between Component-based Design and Implementation with a Reflective Programming Language Petr Spacek Christophe Dony Luc Fabresse Chouki Tibermacine Universite´ Lille Nord de France LIRMM, CNRS and Montpellier II University Ecole des Mines de Douai 161, rue Ada 941 rue Charles Bourseul 34392 Montpellier Cedex 5 France 59508 DOUAI Cedex France spacek,dony,tibermacin @lirmm.fr [email protected] { } Abstract General Terms Languages, Reflection, Metamodeling Component-based Software Engineering studies the design, Keywords Component, Programming, Modeling, Archi- development and maintenance of software constructed upon tecture, Reflection, Reflexive, Meta-model, Constraints, sets of connected components. Existing component-based Transformations models are frequently transformed into non-component- based programs, most of the time object-oriented, for run- time execution and then many component-related concepts, 1. Introduction e.g. explicit architecture, vanish at the implementation stage. Research works on component-based software engineering The main reason why is that with objects the component- (CBSE) have brought many advances on how to achieve related concepts are treated implicitly and therefore the orig- complex software development by reusing and assembling inal intentions and qualities of the component-based design components. The current trend is to explicitly express ar- are hidden. This paper presents a reflective component-based chitectures of software solutions, to reason about them, to programming and modeling language, which proposes the verify them and to transform them. However it appears following original contributions: 1) Components are seen that component-orientation has been more studied at de- as objects in which requirements, architecture descriptions, sign stage, with modeling languages and ADLs [10, 16, 22] connection points, etc.