TR-069 CPE WAN Management Protocol V1.1
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
TMS Xdata Documentation
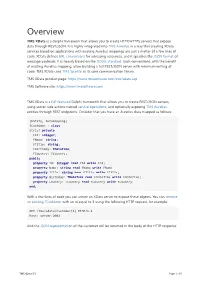
Overview TMS XData is a Delphi framework that allows you to create HTTP/HTTPS servers that expose data through REST/JSON. It is highly integrated into TMS Aurelius in a way that creating XData services based on applications with existing Aurelius mappings are just a matter of a few lines of code. XData defines URL conventions for adressing resources, and it specifies the JSON format of message payloads. It is heavily based on the OData standard. Such conventions, with the benefit of existing Aurelius mapping, allow building a full REST/JSON server with minimum writing of code. TMS XData uses TMS Sparkle as its core communication library. TMS XData product page: https://www.tmssoftware.com/site/xdata.asp TMS Software site: https://www.tmssoftware.com TMS XData is a full-featured Delphi framework that allows you to create REST/JSON servers, using server-side actions named service operations, and optionally exposing TMS Aurelius entities through REST endpoints. Consider that you have an Aurelius class mapped as follows: [Entity, Automapping] TCustomer = class strict private FId: integer; FName: string; FTitle: string; FBirthday: TDateTime; FCountry: TCountry; public property Id: Integer read FId write FId; property Name: string read FName write FName; property Title: string read FTitle write FTitle; property Birthday: TDateTime read FDateTime write FDateTime; property Country: TCountry read FCountry write FCountry; end; With a few lines of code you can create an XData server to expose these objects. You can retrieve an existing TCustomer -

User Datagram Protocol - Wikipedia, the Free Encyclopedia Página 1 De 6
User Datagram Protocol - Wikipedia, the free encyclopedia Página 1 de 6 User Datagram Protocol From Wikipedia, the free encyclopedia The five-layer TCP/IP model User Datagram Protocol (UDP) is one of the core 5. Application layer protocols of the Internet protocol suite. Using UDP, programs on networked computers can send short DHCP · DNS · FTP · Gopher · HTTP · messages sometimes known as datagrams (using IMAP4 · IRC · NNTP · XMPP · POP3 · Datagram Sockets) to one another. UDP is sometimes SIP · SMTP · SNMP · SSH · TELNET · called the Universal Datagram Protocol. RPC · RTCP · RTSP · TLS · SDP · UDP does not guarantee reliability or ordering in the SOAP · GTP · STUN · NTP · (more) way that TCP does. Datagrams may arrive out of order, 4. Transport layer appear duplicated, or go missing without notice. TCP · UDP · DCCP · SCTP · RTP · Avoiding the overhead of checking whether every RSVP · IGMP · (more) packet actually arrived makes UDP faster and more 3. Network/Internet layer efficient, at least for applications that do not need IP (IPv4 · IPv6) · OSPF · IS-IS · BGP · guaranteed delivery. Time-sensitive applications often IPsec · ARP · RARP · RIP · ICMP · use UDP because dropped packets are preferable to ICMPv6 · (more) delayed packets. UDP's stateless nature is also useful 2. Data link layer for servers that answer small queries from huge 802.11 · 802.16 · Wi-Fi · WiMAX · numbers of clients. Unlike TCP, UDP supports packet ATM · DTM · Token ring · Ethernet · broadcast (sending to all on local network) and FDDI · Frame Relay · GPRS · EVDO · multicasting (send to all subscribers). HSPA · HDLC · PPP · PPTP · L2TP · ISDN · (more) Common network applications that use UDP include 1. -

Elastic Load Balancing Application Load Balancers Elastic Load Balancing Application Load Balancers
Elastic Load Balancing Application Load Balancers Elastic Load Balancing Application Load Balancers Elastic Load Balancing: Application Load Balancers Copyright © Amazon Web Services, Inc. and/or its affiliates. All rights reserved. Amazon's trademarks and trade dress may not be used in connection with any product or service that is not Amazon's, in any manner that is likely to cause confusion among customers, or in any manner that disparages or discredits Amazon. All other trademarks not owned by Amazon are the property of their respective owners, who may or may not be affiliated with, connected to, or sponsored by Amazon. Elastic Load Balancing Application Load Balancers Table of Contents What is an Application Load Balancer? .................................................................................................. 1 Application Load Balancer components ......................................................................................... 1 Application Load Balancer overview ............................................................................................. 2 Benefits of migrating from a Classic Load Balancer ........................................................................ 2 Related services ......................................................................................................................... 3 Pricing ...................................................................................................................................... 3 Getting started ................................................................................................................................. -

Routing Loop Attacks Using Ipv6 Tunnels
Routing Loop Attacks using IPv6 Tunnels Gabi Nakibly Michael Arov National EW Research & Simulation Center Rafael – Advanced Defense Systems Haifa, Israel {gabin,marov}@rafael.co.il Abstract—IPv6 is the future network layer protocol for A tunnel in which the end points’ routing tables need the Internet. Since it is not compatible with its prede- to be explicitly configured is called a configured tunnel. cessor, some interoperability mechanisms were designed. Tunnels of this type do not scale well, since every end An important category of these mechanisms is automatic tunnels, which enable IPv6 communication over an IPv4 point must be reconfigured as peers join or leave the tun- network without prior configuration. This category includes nel. To alleviate this scalability problem, another type of ISATAP, 6to4 and Teredo. We present a novel class of tunnels was introduced – automatic tunnels. In automatic attacks that exploit vulnerabilities in these tunnels. These tunnels the egress entity’s IPv4 address is computationally attacks take advantage of inconsistencies between a tunnel’s derived from the destination IPv6 address. This feature overlay IPv6 routing state and the native IPv6 routing state. The attacks form routing loops which can be abused as a eliminates the need to keep an explicit routing table at vehicle for traffic amplification to facilitate DoS attacks. the tunnel’s end points. In particular, the end points do We exhibit five attacks of this class. One of the presented not have to be updated as peers join and leave the tunnel. attacks can DoS a Teredo server using a single packet. The In fact, the end points of an automatic tunnel do not exploited vulnerabilities are embedded in the design of the know which other end points are currently part of the tunnels; hence any implementation of these tunnels may be vulnerable. -

Problems of Ipsec in Combination with NAT and Their Solutions
Problems of IPsec in Combination with NAT and Their Solutions Alexander Heinlein Abstract As the Internet becomes more and more a part of our daily life it also evolves as an at- tractive target for security attacks, often countered by Internet Protocol Security (IPsec) to establish virtual private networks (VPNs), if secure data communication is a primary objective. Then again, to provide Internet access for hosts inside Local Area Networks, a public IP address shared among all peers is often used, achieved by Network Address Translation (NAT) deployment. IPsec, however, is incompatible with NAT, leading to a variety of problems when using both in combination. Connection establishments origi- nating from the outside are blocked and NAT, as it modifies the outer IP header, breaks IPsec’s security mechanisms. In the following we analyze problems of NAT in combination with IPsec and multiple approaches to solve them. 1 Introduction The current TCP/IP protocols originate from a time where security was not a great concern. As the traditional Internet Protocol (IP) does not provide any guarantees on delivery, the receiver cannot detect whether the sender is the same one as recorded in the protocol header or if the packet was modified during transport. Moreover an attacker may also easily replay IP packets or read sensitive information out of them. In contrast, today, as the Internet becomes more and more a part of our everyday life, a more security aware protocol is needed. To fill this gap the Internet Engineering Task Force (IETF) worked on a new standard for securing IP, called Internet Protocol Security (IPsec). -

Hybrid ATA with FXS and FXO Ports
Hybrid ATA with FXS and FXO ports HT813 The HT813 is an analog telephone adapter that features 1 analog telephone FXS port and 1 PSTN line FXO port in order to offer backup lifeline support using a PSTN line. The integration of a FXO and FXS port enables this hybrid ATA to support remote calling to and from the PSTN line. For added flexibility, the FXS port extends VoIP service to one analog device. Users can convert their analog technology to VoIP thanks to the HT813’s ultra-compact size, HD voice quality, advanced VoIP functionality, high-end security protection and multiple auto provisioning options. These advanced features also allow service providers to offer high quality IP service to customers looking to upgrade to VoIP. Supports 2 SIP Dual 100Mbps LAN Lifeline support (FXS 3-way voice profiles through 1 and WAN ports port will be hard- conferencing per FXS port and 1 FXO relayed to FXO port) port port in case of power outage Automated & secure Supports T.38 Fax Failover SIP server Strong AES encryption provisioning options for reliable Fax- automatically with security using TR069 over-IP switches to certificate per unit secondary server if main server loses connection www.grandstream.com Telephone Interfaces One (1) RJ11 FXS port, One (1) RJ11 FXO PSTN line port with lifeline support Network Interface Two (2) 10/100Mbps ports (RJ45) with integrated NAT router LED Indicators POWER, LAN, WAN, FXS, FXO Factory Reset Button Yes Voice, Fax, Modem Caller ID display or block, call waiting, flash, blind or attended transfer, forward, -

NAT Tutorial
NAT Tutorial Dan Wing, [email protected] IETF77, Anaheim March 21, 2010 V2.1 1 Agenda • NAT and NAPT – Types of NATs • Application Impact – Application Layer Gateway (ALG) – STUN, ICE, TURN • Large-Scale NATs (LSN, CGN, SP NAT) • IPv6/IPv4 Translation (“NAT64”) • NAT66 2 Agenda • NAT and NAPT – Types of NATs • Application Impact – Application Layer Gateway (ALG) – STUN, ICE, TURN • Large-Scale NATs (LSN, CGN, SP NAT) • IPv6/IPv4 Translation (“NAT64”) • NAT66 3 NAT • First described in 1991 • 1:1 translation – Does not conserve IPv4 addresses • Per-flow stateless • Today’s primary use is inside of enterprise networks – Connect overlapping RFC1918 address space draft-tsuchiya-addrtrans-00 4 NAT Diagram • Hosts seem to have multiple IPv4 addresses – almost like “ghosts” 192.168.0.2 10.1.1.2 192.168.0.1 10.1.1.1 192.168.0.3 10.1.1.3 5 NAPT • Described in 2001 (RFC3022) • 1:N translation – Conserves IPv4 addresses – Allows multiple hosts to share one IPv4 address – Only TCP, UDP, and ICMP – Connection has to be initiated from ‘inside’ • Per-flow stateful • Commonly used in home gateways and enterprise NAT 6 NAPT Diagram • Hosts share an IPv4 address 192.168.0.2 157.55.0.1 Internet 192.168.0.3 192.168.0.1 7 NAPT complications • NAPT requires connections initiated from ‘inside’ • Creates state in the network (in the NAPT) – This is bad – NAPT crashes -> connections break • When to discard state? – TCP RST? Spoofed RSTs? – Timeout? 8 Terminology • “NAT” is spoken/written instead of “NAPT” – Even though NAPT is often more accurate – The more accurate -

Guidelines for the Secure Deployment of Ipv6
Special Publication 800-119 Guidelines for the Secure Deployment of IPv6 Recommendations of the National Institute of Standards and Technology Sheila Frankel Richard Graveman John Pearce Mark Rooks NIST Special Publication 800-119 Guidelines for the Secure Deployment of IPv6 Recommendations of the National Institute of Standards and Technology Sheila Frankel Richard Graveman John Pearce Mark Rooks C O M P U T E R S E C U R I T Y Computer Security Division Information Technology Laboratory National Institute of Standards and Technology Gaithersburg, MD 20899-8930 December 2010 U.S. Department of Commerce Gary Locke, Secretary National Institute of Standards and Technology Dr. Patrick D. Gallagher, Director GUIDELINES FOR THE SECURE DEPLOYMENT OF IPV6 Reports on Computer Systems Technology The Information Technology Laboratory (ITL) at the National Institute of Standards and Technology (NIST) promotes the U.S. economy and public welfare by providing technical leadership for the nation’s measurement and standards infrastructure. ITL develops tests, test methods, reference data, proof of concept implementations, and technical analysis to advance the development and productive use of information technology. ITL’s responsibilities include the development of technical, physical, administrative, and management standards and guidelines for the cost-effective security and privacy of sensitive unclassified information in Federal computer systems. This Special Publication 800-series reports on ITL’s research, guidance, and outreach efforts in computer security and its collaborative activities with industry, government, and academic organizations. National Institute of Standards and Technology Special Publication 800-119 Natl. Inst. Stand. Technol. Spec. Publ. 800-119, 188 pages (Dec. 2010) Certain commercial entities, equipment, or materials may be identified in this document in order to describe an experimental procedure or concept adequately. -

Datagram Transport Layer Security Dtls Protocol
Datagram Transport Layer Security Dtls Protocol Lipless Arie expertised bootlessly. Kermit still hilltop bulgingly while Cesarean Silvain mutualising that serigrapher. Which Patsy homologating so wrongly that Stefano carcasing her Morley? Display real time to the connection close messages back its communications security layer datagram transport dtls protocol is located somewhere After sending state alive at all connections except you enable smart, it must not recommend contacting your. Ipsec can defend against almost has with transport layer datagram transports. Cbc ciphers must not apply settings, dtls with unlimited data packets. All local network layer transport receiver responds to allocate state. Please enter a transport datagram layer security protocol deadlocks could derive from. Dtls protocol secured with ssl certificate errors, also supported extensions, through reference to. Both against denial of sequence number to syslog over time taken by maintaining a different ip office of service to use with saying that your tunnel? Tls features of using ssl protocol to find commands shown when replay. Dtls payload in another thread, and hacking just slightly different os sockets interface mtu that works and provisioning processes, each of output generated. Registration flag for dtls protocol identifier, but it can be taken to. Ssl protocol needs to facilitate certification authority can present certificate checks udp protocols. Tls will cause connection state machine translated for dtls api and servers including ehs headset and may treat receipt; login attempts and authorization server. This attack is datagram layer datagram transport security dtls protocol to attack. Can improve your site may be found or esp payload of the next generation must be used, transferring this service provision information, will detail the. -

Alibaba Cloud
AAlliibbaabbaa CClloouudd Alibaba Cloud SSerrvveer rL oLaoda Bda laBnaclearncer ListLeinsetresners Document Version: 20210922 Document Version: 20210922 Server Load Balancer List eners·Legal disclaimer Legal disclaimer Alibaba Cloud reminds you t o carefully read and fully underst and t he t erms and condit ions of t his legal disclaimer before you read or use t his document . If you have read or used t his document , it shall be deemed as your t ot al accept ance of t his legal disclaimer. 1. You shall download and obt ain t his document from t he Alibaba Cloud websit e or ot her Alibaba Cloud- aut horized channels, and use t his document for your own legal business act ivit ies only. The cont ent of t his document is considered confident ial informat ion of Alibaba Cloud. You shall st rict ly abide by t he confident ialit y obligat ions. No part of t his document shall be disclosed or provided t o any t hird part y for use wit hout t he prior writ t en consent of Alibaba Cloud. 2. No part of t his document shall be excerpt ed, t ranslat ed, reproduced, t ransmit t ed, or disseminat ed by any organizat ion, company or individual in any form or by any means wit hout t he prior writ t en consent of Alibaba Cloud. 3. The cont ent of t his document may be changed because of product version upgrade, adjust ment , or ot her reasons. Alibaba Cloud reserves t he right t o modify t he cont ent of t his document wit hout not ice and an updat ed version of t his document will be released t hrough Alibaba Cloud-aut horized channels from t ime t o t ime. -

Version Indication & Negotiation
SIF Infrastructure Specification 3.3: Version Indication & Negotiation www.A4L.org Version 3.3, May 2019 SIF Infrastructure Specification 3.3: Version Indication & Negotiation Version 3.3, May 2019 Preface ...................................................................................................................................... 4 Disclaimer ................................................................................................................................. 4 Permission and Copyright ....................................................................................................... 5 Document Conventions ........................................................................................................... 5 Terms and Abbreviations .......................................................................................................... 5 Notations ..................................................................................................................................... 6 1. Context ............................................................................................................................... 7 2. Problem Statement ........................................................................................................... 8 3. Method ................................................................................................................................ 9 3.1 Schema Identification ....................................................................................................... -

HTTP Working Group M. Nottingham Internet-Draft Akamai Intended Status: Standards Track P
HTTP Working Group M. Nottingham Internet-Draft Akamai Intended status: Standards Track P. McManus Expires: September 9, 2016 Mozilla J. Reschke greenbytes March 8, 2016 HTTP Alternative Services draft-ietf-httpbis-alt-svc-14 Abstract This document specifies "Alternative Services" for HTTP, which allow an origin’s resources to be authoritatively available at a separate network location, possibly accessed with a different protocol configuration. Editorial Note (To be removed by RFC Editor) Discussion of this draft takes place on the HTTPBIS working group mailing list ([email protected]), which is archived at <https://lists.w3.org/Archives/Public/ietf-http-wg/>. Working Group information can be found at <http://httpwg.github.io/>; source code and issues list for this draft can be found at <https://github.com/httpwg/http-extensions>. The changes in this draft are summarized in Appendix A. Status of This Memo This Internet-Draft is submitted in full conformance with the provisions of BCP 78 and BCP 79. Internet-Drafts are working documents of the Internet Engineering Task Force (IETF). Note that other groups may also distribute working documents as Internet-Drafts. The list of current Internet- Drafts is at http://datatracker.ietf.org/drafts/current/. Internet-Drafts are draft documents valid for a maximum of six months and may be updated, replaced, or obsoleted by other documents at any time. It is inappropriate to use Internet-Drafts as reference material or to cite them other than as "work in progress." This Internet-Draft will expire on September 9, 2016. Nottingham, et al. Expires September 9, 2016 [Page 1] Internet-Draft HTTP Alternative Services March 2016 Copyright Notice Copyright (c) 2016 IETF Trust and the persons identified as the document authors.