Design and Analysis of Decoy Systems for Computer Security
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

+P+-+K+- +-+-+-+- B -+-+P+-+ W -+-+-+-+ Zlw-+P+R +-+-+-Z- P+-+N+Q+ P+-+-+-+ +-+-+-+- Z-+K+-+- -+-+-TP+ Kwqs-Z-S +-+-+RM- +-+-+-+
Contents Symbols 4 Introduction 5 Part 1: The Basics 1 Pin 7 2 Deflection 16 3 Overload 23 4 Decoy 28 5 Double Attack 36 6 Knight Fork 44 7 Discovered Attack 50 8 Clearance 56 9 Obstruction 64 10 Removing the Defender 71 11 The Power of the Pawn 77 12 Back-Rank Mate 85 13 Stalemate 91 14 Perpetual Check and Fortresses 96 Part 2: Advanced Tactics 15 f7: Weak by Presumption 103 16 The Vulnerable Rook’s Pawn 111 17 Attacking the Fianchetto 118 18 The Mystery of the Opposite-Coloured Bishops 125 19 Chess Highways: Open Files 131 20 Trapping a Piece 141 21 Practice Makes Perfect 149 Solutions 158 Index of Players 188 Index of Composers 191 KNIGHT FORK 6 Knight Fork The knight is considered to be the least powerful White is now a queen and two rooks down – piece in chess (besides the pawn, of course). As a deficit of approximately 19 ‘pawns’. His only the great world champion Jose Raul Capablanca remaining piece is a knight. But a brave one... taught us, the other minor piece, the bishop, is 3 Ìe3+ Êf6 4 Ìxd5+ Êf5 5 Ìxe7+ Êf6 6 better in 90% of cases. However, due to its spe- Ìxg8+ (D) cific qualities the knight is a tremendously dan- gerous piece. It is nimble and its jumps can be -+-+-+N+ quite shocking. That is why a double attack by a +-+-+p+- knight is usually distinguished from other dou- B ble attacks and called a fork. -+-+nm-M +-+-z-+- A single knight may cause incredible dam- age in the right circumstances: -+-+-+-+ +-+-+PZ- -+-+-+q+ -+-+-+-+ +-+r+p+- +-+-+-+- W -+N+nm-M +-+rz-+- The knight has managed to remove most of Black’s army. -

The Wangling Wizards the Chess Problems of the Warton Brothers
The Wangling Wizards The chess problems of the Warton brothers Compiled by Michael McDowell ½ û White to play and mate in 3 British Chess Problem Society 2005 The Wangling Wizards Introduction Tom and Joe Warton were two of the most popular British chess problem composers of the twentieth century. They were often compared to the American "Puzzle King" Sam Loyd because they rarely composed problems illustrating formal themes, instead directing their energies towards hoodwinking the solver. Piquant keys and well-concealed manoeuvres formed the basis of a style that became known as "Wartonesque" and earned the brothers the nickname "the Wangling Wizards". Thomas Joseph Warton was born on 18 th July 1885 at South Mimms, Hertfordshire, and Joseph John Warton on 22 nd September 1900 at Notting Hill, London. Another brother, Edwin, also composed problems, and there may have been a fourth composing Warton, as a two-mover appeared in the August 1916 issue of the Chess Amateur under the name G. F. Warton. After a brief flourish Edwin abandoned composition, although as late as 1946 he published a problem in Chess . Tom and Joe began composing around 1913. After Tom’s early retirement from the Metropolitan Police Force they churned out problems by the hundred, both individually and as a duo, their total output having been estimated at over 2600 problems. Tom died on 23rd May 1955. Joe continued to compose, and in the 1960s published a number of joints with Jim Cresswell, problem editor of the Busmen's Chess Review , who shared his liking for mutates. Many pleasing works appeared in the BCR under their amusing pseudonym "Wartocress". -

Шахматных Задач Chess Exercises Schachaufgaben
Всеволод Костров Vsevolod Kostrov Борис Белявский Boris Beliavsky 2000 Шахматных задач Chess exercises Schachaufgaben РЕШЕБНИК TACTICAL CHESS.. EXERCISES SCHACHUBUNGSBUCH Шахматные комбинации Chess combinations Kombinationen Часть 1-2 разряд Part 1700-2000 Elo 3 Teil 1-2 Klasse Русский шахматный дом/Russian Chess House Москва, 2013 В первых двух книжках этой серии мы вооружили вас мощными приёмами для успешного ведения шахматной борьбы. В вашем арсенале появились двойной удар, связка, завлечение и отвлечение. Новый «Решебник» обогатит вас более изысканным тактическим оружием. Не всегда до короля можно добраться, используя грубую силу. Попробуйте обхитрить партнёра с помощью плаща и кинжала. Маскируйтесь, как разведчик, и ведите себя, как опытный дипломат. Попробуйте найти слабое место в лагере противника и в нужный момент уничтожьте защиту и нанесите тонкий кинжальный удар. Кстати, чужие фигуры могут стать союзниками. Умелыми манёврами привлеките фигуры противника к их королю, пускай они его заблокируют так, чтобы ему, бедному, было не вздохнуть, и в этот момент нанесите решающий удар. Неприятно, когда все фигуры вашего противника взаимодействуют между собой. Может, стоить вбить клин в их порядки – перекрыть их прочной шахматной дверью. А так ли страшна атака противника на ваши укрепления? Стоит ли уходить в глухую оборону? Всегда ищите контрудар. Тонкий промежуточный укол изменит ход борьбы. Не сгрудились ли ваши фигуры на небольшом пространстве, не мешают ли они друг другу добраться до короля противника? Решите, кому всё же идти на штурм королевской крепости, и освободите пространство фигуре для атаки. Короля всегда надо защищать в первую очередь. Используйте это обстоятельство и совершите открытое нападение на него и другие фигуры. И тогда жернова вашей «мельницы» перемелют всё вражеское войско. -

Ciena Carrier-Grade Ethernet As a Foundation for Campus Access
CARRIER-GRADE ETHERNET AS A FOUNDATION FOR CAMPUS ACCESS NETWORKS Introduction to Ethernet increase overall network reliability, targeting Existing campus access networks are constrained by dissimilar five- or six-9s availability using classic telecommunications and often stressed data networks—typically using numerous equipment supplier specifications to produce network legacy technologies such as ATM and Frame Relay. These elements with ultra-high reliability. In addition to increased disparate networks are becoming increasingly difficult to reliability, the scalability of carrier-grade Ethernet is several manage, leading to higher operational and maintenance costs. orders of magnitude higher than traditional Local Area Additionally, these legacy networks do not cater to the kinds Network (LAN) designs. of emerging real-time applications that are crucial for an Carrier-grade Ethernet technology has become widely effective Information and Communications Technology (ICT) adopted in the carrier and enterprise environments because environment, including VoIP, video, and cloud-based data of its ability to offer differentiated service at a highly attractive processing. These applications are all IP/Ethernet based, cost. Standards-based carrier Ethernet is defined by the Metro requiring a next-generation, highly resilient, scalable, and Ethernet Forum (MEF) and the Optical Interworking Forum packetized campus access network. (OIF) as a connection-oriented Layer 2 service. Carrier-grade To this end, many government agencies have embarked upon Ethernet enables the ability to offer bandwidth-assured, Layer modernization efforts that intend to transform ageing and 2 Virtual Private Networks (VPNs) with up to eight layers of legacy communications infrastructure into a consolidated, Quality of Service (QoS), allowing differentiated service next-generation network. -

Designing a Robust and Cost-Effective Campus Network
CAMPUS LAN Designing a Robust and Cost-Effective Campus Network Brocade is taking groundbreaking performance and reliability from the data center and extending it across the entire network all the way to the edge. Now, superior performance can be maximized across the entire campus network, giving you a more managed and efficient approach to growth. CAMPUS LAN DESIGN BRIEF CONTENTS Introduction........................................................................................................................................................................................................................................ 3 The Campus LAN............................................................................................................................................................3 Performance and Availability.........................................................................................................................................4 Security...........................................................................................................................................................................4 Management..................................................................................................................................................................4 Reducing Operational Expense.....................................................................................................................................4 Building a Tiered Campus Network ......................................................................................................................................................................................... -
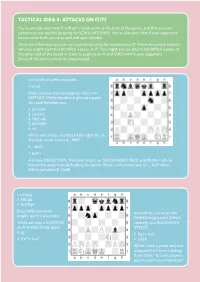
TACTICAL IDEA 4: ATTACKS on F7/F2
TACTICAL IDEA 4: ATTACKS ON f7/f2 You’ve already seen that f7 is Black’s weak point at the start of the game, and that you can sometimes win quickly by going for SCHOLAR’S MATE. You’ve also seen that if your opponent knows what to do you may well end up in trouble. There are other ways you can win quickly by using the weakness on f7. There are several reasons why you might want to SACRIFICE a piece on f7. You might also be able to SACRIFICE a piece at the other end of the board in order to capture on f7 and CHECKMATE your opponent. Some of the tactics are quite complicated. Let’s look at a few examples. 1. e4 c5 Black chooses the very popular SICILIAN DEFENCE. White decides to give up a pawn for rapid development. 2. d4 cxd4 3. c3 dxc3 4. Nxc3 d6 5. Bc4 Nf6 6. e5 White sets a trap, and Black falls right into it. The best move now is 6… Nfd7 6… dxe5 7. Bxf7+ A simple DEFLECTION. The black king is an OVERWORKED PIECE and White’s bishop forces him away from defending the queen. Black’s only move now is 7… Kxf7 when White just plays 8. Qxd8. 1. e4 Nc6 2. Nf3 d6 3. Bc4 Bg4 Black PINS the white Now White can move the knight, but it’s a mistake. PINNED knight with CHECK, White can play a SACRIFICE opening up a DISCOVERED on f7 to DECOY the black ATTACK. king. 5. -

Scholar'smate
SCHOLAR'S MATE SAMPLE ARTICLES CANADA'S CHESS MAGAZINE FOR KIDS CONTENTS Sample Articles Excerpts from different issues Actual magazines are 48 to 60 pages each. DEVELOPING ROOKS part 3 2 Kiril’s Klass June 2008 Make The Most Of Your 5 Point Pieces SPECIAL ED & SMART ALEC 3 Meet The Dudes February 2008 MATES 4 Mates In 1 & 2 Moves June 2008 LILY’S PUZZLER 5 Unusual Chess Problems June 2008 Switcheroos COMBO MOMBO 5 Spotlight On Decoys February 2008 Tactics With Rocky The Rook ADVENTURES OF CAPTAIN BEMO 6 Kiril's Korner February 2008 Voyage To The Top Of The World VOYAGE TO THE TOP OF THE WORLD SOLUTIONS 11 COMBO MOMBO ORDERING BACK ISSUES 11 DEVELOPING ROOKS part 3 Castling is the normal way to free a rook from the corner, but there are some positions where it is better to simply move the king up to the second rank. This DEVELOPING usually happens when the queens have been traded and the endgame is near. Then the king doesn’t need to ROOKS hide anymore. He can come out and fight like a man! PART 3 In this position, 1.O-O? frees the rook on h1 but leaves the white king out of play. 1...Rbc8! To get the advantage, the king must stay in the middle This lesson concludes our of the board and help the other series on activating rooks. white pieces challenge black’s 8 w4wdwdwd control of the open c-file. 7 dwdbiw0p 1.Kd2! Rbc8 2.Rhc1 6 wdw0w0wd One goal of good opening play is to “connect your The game might go 2...Rc3 5 0w4P0wdw rooks”. -

Campus Network Security and Management
International Journal of Emerging Trends & Technology in Computer Science (IJETTCS) Web Site: www.ijettcs.org Email: [email protected] Volume 3, Issue 6, November-December 2014 ISSN 2278-6856 CAMPUS NETWORK SECURITY AND MANAGEMENT 1S. Sudharsan, 2M. Naga Srinivas, 3G. Sai Shabareesh, P.Kiran Rao 1 Department of Computer science 2Department of Computer science 3Department of Computer science ABSTRACT organizations, and does not need to “span large This project is totally dedicated to the Network Engineer for geographical distances.” new and smart learning of the Network Structure. In this MAN (Metropolitan Area Network):- A MAN is concept it is possible for the networker to check the Network defined as a network that spans several LAN’s across a Structure of a company spread in the big campus area. The city-wide geographic area. The term “MAN” is less incoming & the outgoing traffic can be maintained along with prevalent than either LAN or WAN. Generally a network some security concepts as well. In this logic we use the is purely based on what TOPOLOGY it is using, generally multiple Routing Protocols in different areas of the company. a computer network topology is the way various The practical shows us the proper movement of the packet components of a network (like nodes, links, peripherals, from one part of the company to the other part of the etc) are arranged. Network topologies define the layout, company. The project comprises of the different Departments of a Campus spread in different buildings. Multiple Routing virtual shape or structure of network, not only physically protocols have been used in different branches of and all the but also logically. -

Nick Feamster
Nick Feamster Neubauer Professor [email protected] Department of Computer Science https://people.cs.uchicago.edu/˜feamster/ University of Chicago https://noise.cs.uchicago.edu/ 5730 South Ellis Avenue https://medium.com/@feamster/ Chicago, Illinois 60637 Research Interests My research focuses on networked computer systems, with an emphasis on network architecture and protocol design; network security, management, and measurement; routing; and anti-censorship techniques. The primary goal of my research is to design tools, techniques, and policies to help networks operate better, and to enable users of these networks (both public and private) to experience high availability and good end-to-end performance. The problems that I tackle often involve the intersection of networking technology and policy. I study problems in the pricing and economics of Internet interconnection, global Internet censorship and information control, the security and privacy implications of emerging technologies, and the performance of consumer, commercial, and enterprise networks. My research achieves impact through new design paradigms in network architecture, the release of open-source software systems, and data and evidence that can influence public policy discourse. Education Degree Year University Field Ph.D. 2005 Massachusetts Institute of Technology Computer Science Cambridge, MA Dissertation: Proactive Techniques for Correct and Predictable Internet Routing Sprowls Honorable Mention for best MIT Ph.D. dissertation in Computer Science Advisor: Hari Balakrishnan -

A Beginner's Guide to Coaching Scholastic Chess
A Beginner’s Guide To Coaching Scholastic Chess by Ralph E. Bowman Copyright © 2006 Foreword I started playing tournament Chess in 1962. I became an educator and began coaching Scholastic Chess in 1970. I became a tournament director and organizer in 1982. In 1987 I was appointed to the USCF Scholastic Committee and have served each year since, for seven of those years I served as chairperson or co-chairperson. With that experience I have had many beginning coaches/parents approach me with questions about coaching this wonderful game. What is contained in this book is a compilation of the answers to those questions. This book is designed with three types of persons in mind: 1) a teacher who has been asked to sponsor a Chess team, 2) parents who want to start a team at the school for their child and his/her friends, and 3) a Chess player who wants to help a local school but has no experience in either Scholastic Chess or working with schools. Much of the book is composed of handouts I have given to students and coaches over the years. I have coached over 600 Chess players who joined the team knowing only the basics. The purpose of this book is to help you to coach that type of beginning player. What is contained herein is a summary of how I run my practices and what I do with beginning players to help them enjoy Chess. This information is not intended as the one and only method of coaching. In all of my college education classes there was only one thing that I learned that I have actually been able to use in each of those years of teaching. -

Glossary of Chess
Glossary of chess See also: Glossary of chess problems, Index of chess • X articles and Outline of chess • This page explains commonly used terms in chess in al- • Z phabetical order. Some of these have their own pages, • References like fork and pin. For a list of unorthodox chess pieces, see Fairy chess piece; for a list of terms specific to chess problems, see Glossary of chess problems; for a list of chess-related games, see Chess variants. 1 A Contents : absolute pin A pin against the king is called absolute since the pinned piece cannot legally move (as mov- ing it would expose the king to check). Cf. relative • A pin. • B active 1. Describes a piece that controls a number of • C squares, or a piece that has a number of squares available for its next move. • D 2. An “active defense” is a defense employing threat(s) • E or counterattack(s). Antonym: passive. • F • G • H • I • J • K • L • M • N • O • P Envelope used for the adjournment of a match game Efim Geller • Q vs. Bent Larsen, Copenhagen 1966 • R adjournment Suspension of a chess game with the in- • S tention to finish it later. It was once very common in high-level competition, often occurring soon af- • T ter the first time control, but the practice has been • U abandoned due to the advent of computer analysis. See sealed move. • V adjudication Decision by a strong chess player (the ad- • W judicator) on the outcome of an unfinished game. 1 2 2 B This practice is now uncommon in over-the-board are often pawn moves; since pawns cannot move events, but does happen in online chess when one backwards to return to squares they have left, their player refuses to continue after an adjournment. -

High Availability Campus Network Design - Routed Access Layer Using EIGRP Or OSPF System Assurance Guide
High Availability Campus Network Design - Routed Access Layer using EIGRP or OSPF System Assurance Guide Cisco Validated Design Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com Tel: 408 526-4000 800 553-NETS (6387) Fax: 408 527-0883 The Cisco Validated Design Program consists of systems and solutions designed, tested, and documented to facilitate faster, more reliable, and more predictable customer deployments. For more information visit www.cisco.com/go/validateddesigns. ALL DESIGNS, SPECIFICATIONS, STATEMENTS, INFORMATION, AND RECOMMENDATIONS (COLLECTIVELY, "DESIGNS") IN THIS MANUAL ARE PRESENTED "AS IS," WITH ALL FAULTS. CISCO AND ITS SUPPLIERS DISCLAIM ALL WARRANTIES, INCLUDING, WITHOUT LIMITATION, THE WARRANTY OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT OR ARISING FROM A COURSE OF DEALING, USAGE, OR TRADE PRACTICE. IN NO EVENT SHALL CISCO OR ITS SUPPLIERS BE LIABLE FOR ANY INDIRECT, SPECIAL, CONSEQUENTIAL, OR INCIDENTAL DAMAGES, INCLUDING, WITHOUT LIMITATION, LOST PROFITS OR LOSS OR DAMAGE TO DATA ARISING OUT OF THE USE OR INABILITY TO USE THE DESIGNS, EVEN IF CISCO OR ITS SUPPLIERS HAVE BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES. THE DESIGNS ARE SUBJECT TO CHANGE WITHOUT NOTICE. USERS ARE SOLELY RESPONSIBLE FOR THEIR APPLICATION OF THE DESIGNS. THE DESIGNS DO NOT CONSTITUTE THE TECHNICAL OR OTHER PROFESSIONAL ADVICE OF CISCO, ITS SUPPLIERS OR PARTNERS. USERS SHOULD CONSULT THEIR OWN TECHNICAL ADVISORS BEFORE IMPLEMENTING THE DESIGNS.