A Single NT Hash Can Be Used to Access Almost Any Data Which Resides in a Windows Domain Environment
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Windows 7 Operating Guide
Welcome to Windows 7 1 1 You told us what you wanted. We listened. This Windows® 7 Product Guide highlights the new and improved features that will help deliver the one thing you said you wanted the most: Your PC, simplified. 3 3 Contents INTRODUCTION TO WINDOWS 7 6 DESIGNING WINDOWS 7 8 Market Trends that Inspired Windows 7 9 WINDOWS 7 EDITIONS 10 Windows 7 Starter 11 Windows 7 Home Basic 11 Windows 7 Home Premium 12 Windows 7 Professional 12 Windows 7 Enterprise / Windows 7 Ultimate 13 Windows Anytime Upgrade 14 Microsoft Desktop Optimization Pack 14 Windows 7 Editions Comparison 15 GETTING STARTED WITH WINDOWS 7 16 Upgrading a PC to Windows 7 16 WHAT’S NEW IN WINDOWS 7 20 Top Features for You 20 Top Features for IT Professionals 22 Application and Device Compatibility 23 WINDOWS 7 FOR YOU 24 WINDOWS 7 FOR YOU: SIMPLIFIES EVERYDAY TASKS 28 Simple to Navigate 28 Easier to Find Things 35 Easy to Browse the Web 38 Easy to Connect PCs and Manage Devices 41 Easy to Communicate and Share 47 WINDOWS 7 FOR YOU: WORKS THE WAY YOU WANT 50 Speed, Reliability, and Responsiveness 50 More Secure 55 Compatible with You 62 Better Troubleshooting and Problem Solving 66 WINDOWS 7 FOR YOU: MAKES NEW THINGS POSSIBLE 70 Media the Way You Want It 70 Work Anywhere 81 New Ways to Engage 84 INTRODUCTION TO WINDOWS 7 6 WINDOWS 7 FOR IT PROFESSIONALS 88 DESIGNING WINDOWS 7 8 WINDOWS 7 FOR IT PROFESSIONALS: Market Trends that Inspired Windows 7 9 MAKE PEOPLE PRODUCTIVE ANYWHERE 92 WINDOWS 7 EDITIONS 10 Remove Barriers to Information 92 Windows 7 Starter 11 Access -

Administrative Guide for Windows 10 and Windows Server Fall Creators Update (1709)
Operational and Administrative Guidance Microsoft Windows 10 and Windows Server Common Criteria Evaluation for Microsoft Windows 10 and Windows Server Version 1903 (May 2019 Update) General Purpose Operating System Protection Profile © 2019 Microsoft. All rights reserved. Microsoft Windows 10 GP OS Administrative Guidance Copyright and disclaimer The information contained in this document represents the current view of Microsoft Corporation on the issues discussed as of the date of publication. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information presented after the date of publication. This document is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS OR IMPLIED, AS TO THE INFORMATION IN THIS DOCUMENT. Complying with all applicable copyright laws is the responsibility of the user. This work is licensed under the Creative Commons Attribution-NoDerivs-NonCommercial VLicense (which allows redistribution of the work). To view a copy of this license, visithttp://creativecommons.org/licenses/by-nd-nc/1.0/ or send a letter to Creative Commons, 559 Nathan Abbott Way, Stanford, California 94305, USA. Microsoft may have patents, patent applications, trademarks, copyrights, or other intellectual property rights covering subject matter in this document. Except as expressly provided in any written license agreement from Microsoft, the furnishing of this document does not give you any license to these patents, trademarks, copyrights, or other intellectual property. The example companies, organizations, products, people and events depicted herein are fictitious. No association with any real company, organization, product, person or event is intended or should be inferred. -

Introduction to Windows 7
[Not for Circulation] Introduction to Windows 7 This document provides a basic overview of the new and enhanced features of Windows 7 as well as instructions for how to request an upgrade. Windows 7 at UIS Windows 7 is Microsoft’s latest operating system. Beginning in the fall of 2010, UIS will upgrade all classroom and lab PCs to Windows 7. Any new PC that is ordered will automatically come installed with Windows 7. To request an upgrade, contact the Technology Support Center (TSC) at 217/206-6000 or [email protected]. The TSC will evaluate your machine to see if it’s capable of running Windows 7. (Your computer needs a dual core processor and at least 2 GB of RAM.) Please note that University licensing does NOT cover distribution of Windows 7 for personally owned computers. However, it is available for a discounted price via the WebStore at http://webstore.illinois.edu. What to Consider Before Upgrading There is no direct upgrade path from Windows XP to Windows 7. Therefore, the TSC will take your computer, save your files, and install Windows 7 on a clean hard drive. Please budget a couple days for this process. In some cases, you may have older devices that will not work with Windows 7. While many vendors are providing and will continue to provide drivers for their hardware, in some cases, printers, scanners, and other devices that are more than 5 years old may have issues running on Windows 7. To check the compatibility of your devices with Windows 7, visit the Microsoft Windows 7 Compatibility Center at http://www.microsoft.com/windows/compatibility/windows-7/en-us/default.aspx. -
Performing a Windows 7 Upgrade from Windows Vista
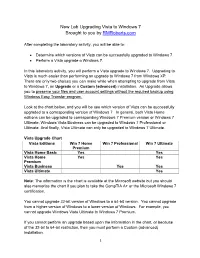
New Lab Upgrading Vista to Windows 7 Brought to you by RMRoberts.com After completing the laboratory activity, you will be able to: Determine which versions of Vista can be successfully upgraded to Windows 7. Perform a Vista upgrade o Windows 7. In this laboratory activity, you will perform a Vista upgrade to Windows 7. Upgrading to Vista is much easier than performing an upgrade to Windows 7 from Windows XP. There are only two choices you can make while when attempting to upgrade from Vista to Windows 7, an Upgrade or a Custom (advanced) installation. An Upgrade allows you to preserve your files and user account settings without the required backup using Windows Easy Transfer program. Look at the chart below, and you will be see which version of Vista can be successfully upgraded to a corresponding version of Windows 7. In general, both Vista Home editions can be upgraded to corresponding Windows 7 Premium version or Windows 7 Ultimate. Windows Vista Business can be upgraded to Windows 7 Professional or Ultimate. And finally, Vista Ultimate can only be upgraded to Windows 7 Ultimate. Vista Upgrade Chart Vista Editions Win 7 Home Win 7 Professional Win 7 Ultimate Premium Vista Home Basic Yes Yes Vista Home Yes Yes Premium Vista Business Yes Yes Vista Ultimate Yes Note: The information is the chart is available at the Microsoft website but you should also memorize the chart if you plan to take the CompTIA A+ or the Microsoft Windows 7 certification. You cannot upgrade 32-bit version of Windows to a 64-bit version. -
Intel® HD Graphics 5300 12 4.4 2.0 Yes Yes
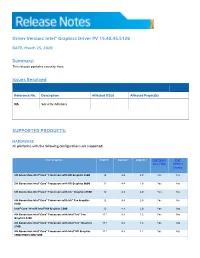
Driver Version: Intel® Graphics Driver PV 15.40.45.5126 DATE: March 25, 2020 Summary: This release contains security fixes. Issues Resolved Reference No. Description Affected OS(s) Affected Project(s) NA Security Advisory SUPPORTED PRODUCTS: HARDWARE All platforms with the following configurations are supported: Intel® Graphics1 DirectX*2 OpenGL* OpenCL* Intel® Quick Intel® Sync Video Wireless Display 5th Generation Intel® Core™ Processors with HD Graphics 5500 12 4.4 2.0 Yes Yes 5th Generation Intel® Core™ Processors with HD Graphics 6000 12 4.4 2.0 Yes Yes 5th Generation Intel® Core™ Processors with Iris™ Graphics 6100 12 4.4 2.0 Yes Yes 5th Generation Intel® Core™ Processors with Iris™ Pro Graphics 12 4.4 2.0 Yes Yes 6200 Intel® Core™ M with Intel® HD Graphics 5300 12 4.4 2.0 Yes Yes 4th Generation Intel® Core™ Processors with Intel® Iris™ Pro 11.1 4.3 1.2 Yes Yes Graphics 5200 4th Generation Intel® Core™ Processors with Intel® Iris™ Graphics 11.1 4.3 1.2 Yes Yes 5100 4th Generation Intel® Core™ Processors with Intel® HD Graphics 11.1 4.3 1.2 Yes Yes 5000/4600/4400/4200 Intel® Pentium® and Celeron® Processors with Intel® HD Graphics 11.1 4.3 1.2 Yes Yes based on 4th and 5th Generation Intel® Core™ Pentium®, Celeron®, and Atom™ processors based on Braswell and 12 4.3 2.0 Yes Yes CherryTrail. SOFTWARE On 4th Generation Intel Core processors and related Pentium/Celeron: • Microsoft Windows 10® 64-bit, 32-bit* *32-bit support is limited to particular SKU’s. -

© Iquila Ltd 2018-2019 - 1
Rev-1 Joining a Client PC to a Domain Controller using iQuila Server Setup 1. Install the iQuila client software on your windows domain controller server (please note if you have more than one domain controller, you must install the iQuila client software on each domain controller in your network.) 2. Assign a static IP address to the iQuila virtual network adaptor. (Please see Help Document for using Static IP addresses) 3. Go to Control Panel then select view network status and tasks, select change adaptor settings, right click on the iQuila network adaptor (VPN – VPN Client) and client properties. 4. Select Internet protocol version v (TCP/IPv4) and click properties. Select use the following IP address and enter an IP address in your given range, i.e. 192.168.30.9. Enter your given subnet mask i.e. 255.255.255.0 Leave the default gateway setting blank Under the DNS section select use the preferred DNS server address and enter the same address as you entered for the IP address 192.168.30.9 Click ok to save IP address and click on the exit the adaptor properties window. © iQuila Ltd 2018-2019 - www.iquila.com 1 Client Setup 1. Install the iQuila client software on the client computers that you would like to join to the domain and ensure they have registered with the iQuila Cloud server. 2. You now need to set the DNS server address on the iQuila virtual adaptor or contact iQuila support and request the change of DNS address in your Virtual DHCP Server settings. -

Contents About the Author
Auditing Microsoft Domain Environment Contents About the Author.........................................................................................................................2 About The Microsoft Domain Environments:............................................................................3 About Auditing:...........................................................................................................................4 Gaining First User:......................................................................................................................5 Enumerating AD Users and Groups With Gained User:.............................................................8 Checking Common Vulnerabilities:..........................................................................................12 Gaining First Shell:...................................................................................................................13 Migrating Into A Process:.........................................................................................................15 Pass The Hash:..........................................................................................................................17 Dump Everything From Domain Controller:............................................................................18 Auditing Microsoft Domain Environment 1 Auditing Microsoft Domain Environment About the Author Engin Demirbilek, Computer Engineering Student Penetration Tester in Turkey at SiberAsist Cyber Security Consultancy. -

Appendix a – Microsoft Windows
Revision 4.6.0 (February 23, 2021) Appendix A – Microsoft Windows Please Read and Heed Appendix Z in order to properly configure RingCentral Meetings. Microsoft Windows, by default, resets the DSCP value of all transmitted packets to BestEffort (0). You must take positive action forcing Windows to tag RingCentral traffic with proper DSCP values. Please note that the traffic going TO RingCentral will be marked, but you must implement proper QoS in the remainder of your network to take advantage of the markings and to set the DSCP values on return traffic as it ingresses your network. This is only one element of a proper QoS implementation. This is particularly critical if you are using WiFi. Wireless Access Points depend on the DSCP marking of traffic in order to enable WMM prioritization of voice/video traffic. Without this marking a busy wireless network will not support voice / video traffic effectively. A special PowerShell script has been developed to automatically generate the QoS policy rules, removing the tedious task of manually entering the large quantity of individual rules. The script supports two action variants based on the Windows environment. 1. Windows 10 clients that are not part of a domain (must be run on each client machine using the 'Administrator' account). All required elements if a NetQosPolicy are generated. The script must be executed on each client computer!!! 2. Domain-based Windows networks (must be run on a domain controller using the 'Administrator' account). A default group QoS policy will be generated. The script should only be executed once for the entire domain. -

Active Directory with Powershell
Active Directory with PowerShell Learn to configure and manage Active Directory using PowerShell in an efficient and smart way Uma Yellapragada professional expertise distilled PUBLISHING BIRMINGHAM - MUMBAI Active Directory with PowerShell Copyright © 2015 Packt Publishing All rights reserved. No part of this book may be reproduced, stored in a retrieval system, or transmitted in any form or by any means, without the prior written permission of the publisher, except in the case of brief quotations embedded in critical articles or reviews. Every effort has been made in the preparation of this book to ensure the accuracy of the information presented. However, the information contained in this book is sold without warranty, either express or implied. Neither the author, nor Packt Publishing, and its dealers and distributors will be held liable for any damages caused or alleged to be caused directly or indirectly by this book. Packt Publishing has endeavored to provide trademark information about all of the companies and products mentioned in this book by the appropriate use of capitals. However, Packt Publishing cannot guarantee the accuracy of this information. First published: January 2015 Production reference: 1200115 Published by Packt Publishing Ltd. Livery Place 35 Livery Street Birmingham B3 2PB, UK. ISBN 978-1-78217-599-5 www.packtpub.com Credits Author Project Coordinator Uma Yellapragada Sageer Parkar Reviewers Proofreaders David Green Simran Bhogal Ross Stone Stephen Copestake Nisarg Vora Martin Diver Ameesha Green Commissioning Editor Paul Hindle Taron Pereira Indexer Acquisition Editor Hemangini Bari Sonali Vernekar Production Coordinator Content Development Editor Aparna Bhagat Prachi Bisht Cover Work Technical Editor Aparna Bhagat Saurabh Malhotra Copy Editors Heeral Bhatt Pranjali Chury Gladson Monteiro Adithi Shetty About the Author Uma Yellapragada has over 11 years of experience in the IT industry. -

Students,Faculty & Staff Guide for Windows 7
iM Students,Faculty & Staff Guide for Windows 7 Prepared by Information Technology Division Lehman College, CUNY March 22, 2014 This document was originally prepared by Dickinson College. It was modified and adapted for use at Lehman College with the permission of Dickinson College. Introduction to Windows 7 Table of Contents Windows 7 Taskbar ...................................................................................................................................... 2 Show Desktop ............................................................................................................................................... 2 Start Menu..................................................................................................................................................... 3 Pin ................................................................................................................................................................. 4 Jump Lists ..................................................................................................................................................... 4 Snap .............................................................................................................................................................. 5 Windows Search ........................................................................................................................................... 6 Library (the new My Documents area & more) ........................................................................................... -

Understanding the Windows SMB NTLM Authentication Weak Nonce Vulnerability
Understanding the Windows SMB NTLM Authentication Weak Nonce Vulnerability Hernan Ochoa Agustin Azubel [email protected] [email protected] Understanding the Windows SMB NTLM Authentication Weak Nonce Vulnerability Presentation goals: ‣ Describe the vulnerability in detail ‣ Explain & demonstrate exploitation • Three different exploitation methods ‣ Clear up misconceptions ‣ Determine vulnerability scope, severity and impact ‣ Share Conclusions BlackHat USA 2010 Understanding the Windows SMB NTLM Authentication Weak Nonce Vulnerability Vulnerability Information ‣ Flaws in Windows’ implementation of NTLM - attackers can access SMB service as authorized user - leads to read/write access to files, SMB shared resources in general and remote code execution ‣ Published February 2010 ‣ CVE-2010-0231, BID 38085 ‣ Advisory with Exploit Code: • http://www.hexale.org/advisories/OCHOA-2010-0209.txt ‣ Addressed by MS10-012 BlackHat USA 2010 Understanding the Windows SMB NTLM Authentication Weak Nonce Vulnerability Why talk about this vulnerability? ‣ Major 14-year old vulnerability affecting Windows Authentication Mechanism! - Basically, all Windows versions were affected (NT4, 2000, XP, 2003, Vista, 2008, 7) - Windows NT 4 released in ∼1996 - Windows NT 3.1 released in ∼1993 (∼17 years ago) - All this time, we assumed it was working correctly.. but it wasn’t... - Flew under the radar... BlackHat USA 2010 Understanding the Windows SMB NTLM Authentication Weak Nonce Vulnerability Why talk about this vulnerability? ‣ Interesting vulnerability, not your common buffer overflow - Issues in the Pseudo-Random Number Generator (PRNG) - Challenge-response protocol implementation issues - Replay attacks - Attack to predict challenges is interesting BlackHat USA 2010 Understanding the Windows SMB NTLM Authentication Weak Nonce Vulnerability Why talk about this vulnerability? ‣ There’s a lesson to be learned.. -

Microsoft Windows 7 Has Reached Its End of Life Your Critical Operations Are at Risk of Costly Downtime Or Outage
— INDUSTRIAL AUTOMATION Microsoft Windows 7 has reached its End of Life Your critical operations are at risk of costly downtime or outage Beginning January 14, 2020, Microsoft will no longer support Windows 7, Windows Server 2008 and 2008 R2. As a result, many ABB products and services will be impacted. To keep your systems secure, you must invest in a plan to upgrade your control systems. Know what “End of Life” means Understand how it impacts you “End of Life” means Microsoft will discontinue all If you choose to continue using Windows 7, Windows support and will no longer provide software or Server 2008 and 2008 R2 even after support is security updates for Windows 7, Windows Server 2008 discontinued, the operating system will still work. and 2008 R2. The Windows 7 “End of Life” is similar to However, running unsupported operating systems that of previous Microsoft operating systems. will make ABB control systems vulnerable to cyber The lifecycle begins when a product is released and threats. Microsoft will no longer provide technical ends when it’s no longer supported. Knowing key support, software updates and security updates dates in this lifecycle helps you make informed needed to keep your systems secure. Purchasing and decisions about when to update, upgrade or make supporting replacement Windows 7 Workstations other changes to your software. and 2008 Server hardware will become challenging, and affected ABB distributed control systems software will move to the Limited Lifecycle Phase. Version End of support Comments Microsoft