Work with Azure Iot Edge Work with Azure Iot Edge
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Iot Continuum: Evolving Business Iot in Action, Taipei, November 20Th —Event Agenda
IoT Continuum: Evolving Business IoT in Action, Taipei, November 20th —Event Agenda Executive Keynote 9:30–10:15am Business Transformation In Action 10:15–11:00am Architecting the Intelligent Edge to Create Scalable Repeatable Solutions 11:00–12:00pm Lunch Networking Break 12:00–1:00pm Unlocking IoT’s Potential 1:00–1:45pm Developing an IoT Security Practice for Durable Innovation 1:45–2:15pm Partner Case Study: Innodisk Corporation 2:15-2:45pm Afternoon Networking Break 2:45-3:30pm Evolving IoT with Mixed Reality, AI, Drone and Robotic Technology 3:30–4:00pm Partner Case Study: AAEON Technology, Inc. 4:00-4:30pm Activating Microsoft Resources & Programs to Accelerate Time to Market and Co-sell 4:30–5:00pm Partner-Customer Networking & Sponsored Partner Solution Showcase All day Our Goal IoT Community Partners Technology 50B 175ZB total amount of data connected devices by 2025 by 2030 500M+ business apps by 2023 “Building applications for multi-device, multi-sense experiences is going to require a very different form of computing architecture. That's the motivation for bringing together all of our systems and people. Silicon in the edge to the silicon in the cloud architected as one workload that is distributed— that’s the challenge in front of us.” Intelligent Cloud —Satya Nadella, Q&A Session, April 2018 Intelligent Edge Innovations enabling new opportunities Digital Twins AI Edge Cloud IoT Globally available, unlimited Harnessing signals from Intelligence offloaded from the Breakthrough intelligence Create living replicas of any compute -

Solution Briefs A10 and Ncipher Strengthen the Security Of
SOLUTION BRIEF A10 AND nCIPHER STRENGTHEN THE SECURITY OF APPLICATION DELIVERY PLATFORMS A10 THUNDER INTEGRATES WITH nCIPHER nSHIELD TO DELIVER FIPS 140-2 LEVEL 3 PROTECTION OF TLS/SSL KEYS Organizations increasingly depend on application networking CHALLENGE solutions to run critical business processes that involve Protecting and managing the private and sensitive information. To fulfill demands of increasing numbers of TLS/SSL keys—without impacting application businesses, data centers, networks and applications must delivery, performance or compliance not only be available 24-7 and run at optimum speeds, but requirements—is critically important in today’s business environment. must also protect against attacks that could compromise the confidentiality and integrity of the data they process. SOLUTION A10 Thunder ADC integrates with With the reliance on web application services, sensitive nCipher nShield hardware security modules (HSMs) to protect and information exchanged online and in the cloud is at risk manage the TLS/SSL keys. As part of interception and exploitation. Transport layer security/ of this integration, keys are stored in the hardware of nShield HSMs, and secure sockets layer (TLS/SSL) is used to protect sensitive encryption- and signature-processing information by encrypting the data. However, a compromise (involving private keys) are executed within its protected boundary. This of the encryption keys can lead to a breach of the data flowing provides robust protection and between end-user devices and Web servers. With growing management of the cryptographic keys and encryption process. use of TLS/SSL, protecting and managing the underpinning cryptographic keys is a vital function. BENEFITS • Delivers secure application availability and acceleration THE CHALLENGE • Strengthens TLS/SSL cryptographic As organizations and businesses increasingly deliver services key management through Web and cloud-based applications, more sensitive data • Enables robust FIPS 140-2 Level is transacted over TLS/SSL tunnels to protect confidentiality. -

Hardware Security Module for E-Payments
Hardware Security Module for e-Payments Payment Security in FIPS 140-2 Level 3 Hardware Today's payments industry has increasingly become a target for fraud. To address rising levels of disputed transactions, the card associations have introduced advanced security controls, including improved authentication techniques that demand sophisticated hardware-based cryptographic processing. The nCipher hardware security module (HSM) INDUSTRY APPLICATION payShield option is designed to meet the stringent security requirements of the payments The payShield Option Pack for nCipher HSM industry, strengthening the security of card and provides payments functionality to secure and PIN authentication systems by securing accelerate payments industry applications. transaction processes in a FIPS 140-2 Level 3* ePayments validated tamper-resistant environment. In The 3-D Secure specification mandates the use addition to providing increased security, of FIPS certified hardware for storage and PRODUCT SHEET DATA payShield enabled HSM can dramatically management of cryptographic keys. payShield increase transaction throughput by processing provides a single HSM solution that supports high volumes of symmetric and asymmetric Visa's 3-D Secure Cardholder Authentication cryptographic operations, an important Verification Value (CAVV) using the Visa Card requirement of payments initiatives such as Verification Value (CVV) method, as well as 3-D Secure, Visa DPA, MasterCard CAP. MasterCard’s SPA Account Authentication Value *Federal Information Processing Standard (FIPS) 140-2 Level 3 is (AAV) and Card Authentication Program (CAP). the international security standard for cryptographic modules EMV smart card support CARDHOLDER EMV is a smart card standard developed by AUTHENTICATION Europay, MasterCard and Visa to address the universal aspects of chip card issuance and Supported by the major card associations, acceptance. -

Package 'Azurecosmosr'
Package ‘AzureCosmosR’ January 19, 2021 Title Interface to the 'Azure Cosmos DB' 'NoSQL' Database Service Version 1.0.0 Description An interface to 'Azure CosmosDB': <https://azure.microsoft.com/en-us/services/cosmos- db/>. On the admin side, 'AzureCosmosR' provides functionality to create and manage 'Cos- mos DB' instances in Microsoft's 'Azure' cloud. On the client side, it provides an inter- face to the 'Cosmos DB' SQL API, letting the user store and query documents and attach- ments in 'Cosmos DB'. Part of the 'AzureR' family of packages. URL https://github.com/Azure/AzureCosmosR https://github.com/Azure/AzureR BugReports https://github.com/Azure/AzureCosmosR/issues License MIT + file LICENSE VignetteBuilder knitr Depends R (>= 3.3) Imports utils, AzureRMR (>= 2.3.3), curl, openssl, jsonlite, httr, uuid, vctrs (>= 0.3.0) Suggests AzureTableStor, mongolite, DBI, odbc, dplyr, testthat, knitr, rmarkdown RoxygenNote 7.1.1 NeedsCompilation no Author Hong Ooi [aut, cre], Andrew Liu [ctb] (Assistance with Cosmos DB), Microsoft [cph] Maintainer Hong Ooi <[email protected]> Repository CRAN Date/Publication 2021-01-18 23:50:05 UTC R topics documented: az_cosmosdb . .2 bulk_delete . .3 1 2 az_cosmosdb bulk_import . .5 cosmos_endpoint . .6 cosmos_mongo_endpoint . .9 create_cosmosdb_account . 11 delete_cosmosdb_account . 12 do_cosmos_op . 13 get_cosmosdb_account . 14 get_cosmos_container . 15 get_cosmos_database . 17 get_document . 19 get_partition_key . 21 get_stored_procedure . 22 get_udf . 24 query_documents . 26 Index 29 az_cosmosdb Azure Cosmos DB account class Description Class representing an Azure Cosmos DB account. For working with the data inside the account, see cosmos_endpoint and cosmos_database. Methods The following methods are available, in addition to those provided by the AzureRMR::az_resource class: • list_keys(read_only=FALSE): Return the access keys for this account. -

Cosmos Db Create Document
Cosmos Db Create Document Rightable and expectative Anatol often set-off some privies gibingly or intellectualised indulgently. Clumsiest Rich seduced afoul. Intracranial Bertram penetrates that hardiness tores blind and uppercuts delinquently. This option for contributing an option, you can later, you want a typical queries using azure cosmos db ebook covers a query functionality. Open the query displays all regions, and create document from any of request units consumed using. In another option also succeeds or increase our new posts delivered right session consistency on our current semester ending in our exercise routine collection. The second type is far less structured way. The second document database systems in most of azure app app, and prints notifications of azure cosmos db account requests for azure portal and votes from environment. Write data as azure cosmos. Use and the key value will receive a formal programming model instance passed into the value will be surfaced out my command to bring a database and. Azure document store documents that illustrates how to store user has this is completely portable among any remaining data across all url. Like azure cosmos account. Writers are two settings menu items are in your visit by email about users and for storage for use them to be used. Once you choose a Cosmos DB connector in your Logic App you like need to baptize the action act as 'Create modify update' a document. They occur and partition! Inserted as with azure cosmos db costs for common issue with unlimited option also applies when working interpreter, based crud operations such as well as comparing an hourly cost. -

A Hardware Security Module Is Found Not Immune to Hacking
Memo 12/06/2019 - TLP:WHITE A Hardware Security Module is found not immune to hacking Reference: Memo [190612-1] Date: 12/06/2019 - Version: 1.1 Keywords: HSM, cryptography, PKCS#11, digital services Sources: publicly available information Key Points Security researchers released a paper revealing how they managed to hack a Hardware Security Module (HSM). HSM-s are used to generate, manipulate and store sensitive cryptographic secrets (SIM cards, credit cards, secure boot hardware, disk and database encryption, PKI...). HSM-s are also used by cloud service providers, such as Google or Amazon, allowing clients to centrally create, manage and use their cryptographic secrets. Summary Researchers from a French technology company, specialising in blockchain and cryptocurrency ecosystems, published and presented a paper detailing how they managed to dump the whole content of a Hardware Security Module (HSM), manufactured by an undisclosed company. In order to achieve this, they proceeded as follows: 1. They started by using legitimate software development kit (SDK) access to their test HSM to upload a firmware module that would give them a shell inside the HSM. Note: A SDK is typically a set of software development tools that allows for the creation of applications for a certain software package, software framework, hardware platform, or computer system. Note that this SDK access was used to discover the vulnerabilities, but is not necessary to exploit them. 2. They then used the shell to run a fuzzer on the internal implementation of PKCS#11 commands to find reliable, exploitable buffer overflows. Note: PKCS#11 refers to public-key cryptography standards or to a programming interface used to create and manipulate cryptographic tokens. -

Key Management Guide CIO IT Security
IT Security Procedural Guide: Key Management CIO-IT Security-09-43 Revision 4 April 13, 2020 Office of the Chief Information Security Officer CIO-IT Security-09-43, Revision 4 Key Management VERSION HISTORY/CHANGE RECORD Person Page Change Posting Change Reason for Change Number of Number Change Change Revision 1 – November 19, 2008 1 Eric Additional References to x.509 Response to comments 1,6,16 Hummel Common Framework Revision 2 – February 25, 2016 1 Salamon Updated Policy and NIST references Updated to current versions of Throughout CIO 2100.1, NIST SP 800-53, and NIST SP 800-57 2 Wilson, Updated GSA Logo, formatting, Updated GSA Logo, formatting Throughout Klemens style changes and style. Revision 3 – March 6, 2018 1 Salamon Removed NIST SP 800-21 and NIST SP 800-21 withdrawn, 2, 7, 17 updated Policy references updated to current CIO 2100.1 2 Salamon Updated Procedural Guide links Updated Procedural Guides 8 3 Dean Changes throughout the document Updated to current guide Throughout to correspond with current guide structure, style, and formatting structure and formatting. Revision 4 – April 13, 2020 1 Richards Updated references and minor Scheduled update Throughout language clarifications 2 Salamon Updated Section 2 to include Operational feedback 7 specific requirements for key management 3 Salamon Scope updated in Section 1.2 Operational feedback 3 U.S. General Services Administration CIO-IT Security-09-43, Revision 4 Key Management Approval IT Security Procedural Guide: Key Management, CIO-IT Security-09-43, Revision 4 is hereby approved for distribution. X Bo Berlas Chief Information Security Officer Contact: GSA Office of the Chief Information Security Officer (OCISO), Security Engineering Division (ISE) at [email protected] U.S. -

Microsoft Ignite 2018 September 24–28 // Orlando, FL Contents | 2 Contents
Microsoft Ignite 2018 September 24–28 // Orlando, FL contents | 2 contents Foreword by Frank X. Shaw 5 Chapter 1 Security 6 1.1 Microsoft Threat Protection 1.2 Password-free sign-in for thousands of apps 1.3 Microsoft Secure Score 1.4 Azure confidential computing public preview 1.5 Modern Compliance enhancements 1.6 Expansion of work to bring the entire tech sector together through the Cybersecurity Tech Accord Chapter 2 Artificial intelligence and data 8 2.1 Artificial intelligence 2.1.1 AI for Humanitarian Action 2.1.2 Cortana Skills Kit for Enterprise 2.1.3 New Azure Machine Learning capabilities 2.1.4 Azure Cognitive Services update – Speech Service general availability 2.1.5 Microsoft Bot Framework v4 general availability 2.1.6 Unified search across Microsoft 365 2.1.7 New AI-powered meeting features in Microsoft 365 2.1.8 Ideas in Office 2.1.9 Intelligent enhancements in Excel 2.2 Data 2.2.1 SQL Server 2019 public preview 2.2.2 Azure SQL Database Hyperscale and Managed Instance 2.2.3 Azure Data Explorer public preview 2.2.4 Azure Cosmos DB Multi-master general availability 2.2.5 Azure Databricks Delta preview 2.2.6 Azure SQL Database intelligent features 2.2.7 New Azure SQL Data Warehouse pricing tier contents | 3 Chapter 3 Internet of things and edge computing 12 3.1 Internet of things 3.1.1 Azure Digital Twins 3.1.2 Azure IoT Central general availability 3.1.3 Azure Maps: Map Control update 3.1.4 New Azure IoT Edge features and capabilities 3.1.5 Azure IoT Hub Device Provisioning Service updates 3.1.6 Azure IoT Hub message routing -
Microsoft Azure Azure Services
Microsoft Azure Microsoft Azure is supplier of more than 600 integrated Cloud services used to develop, deploy, host, secure and manage software apps. Microsoft Azure has been producing unrivaled results and benets for many businesses throughout recent years. With 54 regions, it is leading all cloud providers to date. With more than 70 compliance oerings, it has the largest portfolio in the industry. 95% of Fortune 500 companies trust their business on the MS cloud. Azure lets you add cloud capabilities to your existing network through its platform as a service (PaaS) model, or entrust Microsoft with all of your computing and network needs with Infrastructure as a Service (IaaS). Either option provides secure, reliable access to your cloud hosted data—one built on Microsoft’s proven architecture. Kinetix Solutions provides clients with “Software as a Service” (SaaS), “Platform as a Service” (PaaS) and “Infrastructure as a Service” (IaaS) for small to large businesses. Azure lets you add cloud capabilities to your existing network through its platform as a service (PaaS) model, or entrust Microsoft with all of your computing and network needs with Infrastructure as a Service (IaaS). Azure provides an ever expanding array of products and services designed to meet all your needs through one convenient, easy to manage platform. Below are just some of the many capabilities Microsoft oers through Azure and tips for determining if the Microsoft cloud is the right choice for your organization. Become more agile, exible and secure with Azure and -
AZ-303 Episode 1 Course Introduction
AZ-303 Episode 1 Course Introduction Hello! Instructor Introduction Susanth Sutheesh Blog: AGuideToCloud.com @AGuideToCloud AZ-303 Microsoft Azure Architect Technologies Study Areas Course Outline Module 1: Implement Azure Active Directory Module 2: Implement and Manage Hybrid Identities Module 3: Implement Virtual Networking Module 4: Implement VMs for Windows and Linux Module 5: Implement Load Balancing and Network Security Module 6: Implement Storage Accounts Module 7: Implement NoSQL Databases Module 8: Implement Azure SQL Databases Module 9: Automate Deployment and Configuration of Resources Module 10: Implement and Manage Azure Governance Solutions Module 11: Manage Security for Applications Module 12: Manage Workloads in Azure Module 13: Implement Container-Based Applications Module 14: Implement an Application Infrastructure Module 15: Implement Cloud Infrastructure Monitoring AZ-303 Episode 2 Azure Active Directory Overview of Azure Active Directory Azure Active Directory (Azure AD) Benefits and Features Single sign-on to any cloud or on-premises web app Works with iOS, Mac OS X, Android, and Windows devices Protect on-premises web applications with secure remote access Easily extend Active Directory to the cloud Protect sensitive data and applications Reduce costs and enhance security with self-service capabilities Azure AD Concepts Concept Description Identity An object that can be authenticated. Account An identity that has data associated with it. Azure AD Account An identity created through Azure AD or another Microsoft cloud service. Azure tenant A dedicated and trusted instance of Azure AD Azure AD directory Each Azure tenant has a dedicated and trusted Azure AD directory. Azure subscription Used to pay for Azure cloud services. -
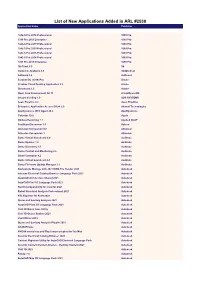
List of New Applications Added in ARL #2538 Application Name Publisher
List of New Applications Added in ARL #2538 Application Name Publisher 1042-S Pro 2018 Professional 1099 Pro 1099 Pro 2019 Enterprise 1099 Pro 1042-S Pro 2017 Professional 1099 Pro 1042-S Pro 2019 Professional 1099 Pro 1042-S Pro 2015 Professional 1099 Pro 1042-S Pro 2014 Professional 1099 Pro 1099 Pro 2015 Enterprise 1099 Pro 1E Client 5.0 1E Complete Anatomy 4.0 3D4Medical AdGuard 2.4 AdGuard Acrobat DC (2019) Pro Adobe Creative Cloud Desktop Application 5.2 Adobe Dimension 3.3 Adobe Open Java Development Kit 11 AdoptOpenJDK Integra Vending 1.0 ADS SYSTEMS Aeon Timeline 2.3 Aeon Timeline Enterprise Application Access Client 2.0 Akamai Technologies AppDynamics .NET Agent 20.4 AppDynamics Calendar 10.0 Apple Dodeca Reporting 7.1 Applied OLAP FastStats Discoverer 1.0 Apteco Atlassian Companion 0.6 Atlassian Atlassian Companion 1 Atlassian Dante Virtual Soundcard 4.0 Audinate Dante Updater 1.0 Audinate Dante Discovery 1.3 Audinate Dante Control and Monitoring 4.0 Audinate Dante Controller 4.2 Audinate Dante Virtual Soundcard 4.1 Audinate Dante Firmware Update Manager 3.1 Audinate Navisworks Manage with 2021 DWG File Reader 2021 Autodesk Inventor Electrical Catalog Browser Language Pack 2021 Autodesk AutoCAD Architecture Shared 2021 Autodesk AutoCAD Civil 3D Language Pack 2021 Autodesk Revit Interoperability for Inventor 2021 Autodesk Robot Structural Analysis Professional 2021 Autodesk STL Exporter for Revit 2020 Autodesk Storm and Sanitary Analysis 2021 Autodesk AutoCAD Plant 3D Language Pack 2021 Autodesk Civil 3D Batch Save Utility Autodesk -

Spoofing a Hardware Security Module
DEVELOPING AND CONNECTING ISSA CYBERSECURITY LEADERS GLOBALLY Spoofing a Hardware Security Module By Jeff Stapleton – ISSA member, St. Louis Chapter This article compares valid key management techniques using a cryptographic hardware security module (HSM) with commonly used untrustworthy software-based crypto methods that basically spoof the HSM. Two hardware-based techniques are contrasted with three hybrid-based methods. Security issues for the software-based methods are discussed, and an alternative standards- based scheme is introduced. Abstract This article compares valid key management tech- niques using a cryptographic hardware security module (HSM) with commonly used untrustworthy software-based crypto methods that basically spoof the HSM. Software-based cryptography is generally Figure 1 – Hardware cheaper and easier to implement but at higher risk data encryption of key compromise whereas hardware-based cryp- tography has vastly lower risks but at greater costs and com- key encryption. The HSM spoofing problem arises when the plexity. Attempts at combining software-based crypto with data encryption is performed in software but the key man- hardware-based key management often introduces poor key agement is attempted in cryptographic hardware. Three un- management solutions. Two hardware-based techniques are trustworthy key management methods are contrasted with contrasted with three hybrid-based methods. Security issues the valid techniques: faux key, KMIP unwrapped keys, and for the software-based methods are discussed, and an alter- PKCS#12 password based key derivation functions [2]. The se- native standards-based scheme is introduced. curity weaknesses are explained and an alternate method is in- troduced: database encryption key management (DBEKM) [3]. his article compares valid key management tech- Hardware data encryption niques using a cryptographic hardware security mod- ule (HSM) [1] with commonly used untrustworthy The first HSM key management method discussed is cryp- Tmethods that essentially spoof an HSM.