Learning from the Lessons Behind the Numbers Hendi Yogi Prabowo University of Wollongong
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Catholic Education Office GENERAL EMPLOYEE APPLICATION FORM
15 Johnson Street FORBES NSW 2871 Telephone: 02 6853 9300 www.wf.catholic.edu.au Catholic Education Office Diocese of Wilcannia-Forbes GENERAL EMPLOYEE APPLICATION FORM (PLEASE COMPLETE THIS FORM AND SUBMIT ORIGINAL TO PRINCIPAL/CEO) APPLICATIONS FOR PERMANENT AND TEMPORARY POSITIONS SHOULD BE SUPPORTED BY A LETTER ADDRESSING THE CRITERIA/POSITION REQUIREMENTS FOUND IN THE ADVERTISEMENT SECTION A – PERSONAL DETAILS Surname: Given Name/s: Title: Former Names: (if applicable): Date of Birth: Religion: Current Parish: Permanent Address: Postcode: Address For Correspondence: Postcode: Home phone: Work phone: Mobile: E-mail: Nationality: Australian Yes No If no, are you eligible to work in Australia ? ________________________________ Origin: Are you Aboriginal or Torres Strait Islander? Aboriginal Torres Strait Islander Both I AM INTERESTED IN APPLYING FOR (tick all that apply): Classroom and Learning Support Services Administration Services Operational Services - Maintenance/Grounds Cleaner Permanent Full-time Part-time Casual Temporary COMPLETE BELOW ONLY IF APPLYING FOR PERMANENT/TEMPORARY POSITIONS: Position(s) applying for: Name of School: Address of School: I became aware of this position by: CEO Website Newspaper Other ___________________________ Refer to Employment Collection Notice – Annexure C “Faith Learning and Transformation in Jesus Christ” Version 1 SECTION B – EDUCATION EDUCATION: School(s) Attended Years of Attendance Certificate(s) Awarded OTHER QUALIFICATIONS: (including current incomplete courses): Name and Location of Institution Years of Attendance Award Conferred Date Conferred SECTION C – EMPLOYMENT EMPLOYMENT (in reverse order from most recent employer – no further back than 15 years): Positions Held Reason for Resignation From To Name and Address of Employment or Termination Page 2 Version 1 SECTION D – WORKING WITH CHILDREN CHECK Teaching positions are child-related work, and legislation requires preferred applicants to be subject to a Working with Children Check (WWCC) for paid employees. -

Identity Crime and Misuse in Australia 2017
AIC reports 10 National Identity Security Strategy Identity crime and misuse in Australia 2017 Penny Jorna Russell G Smith Australian Institute of Criminology Identity crime and misuse in Australia 2017 © Australian Institute of Criminology 2018 ISSN (Online) 2206-7930 Apart from any fair dealing for the purpose of private study, research, criticism or review, as permitted under the Copyright Act 1968 (Cth), no part of this publication may in any form or by any means (electronic, mechanical, microcopying, photocopying, recording or otherwise) be reproduced, stored in a retrieval system or transmitted without prior written permission. Inquiries should be addressed to the publisher. Published by the Australian Institute of Criminology GPO Box 1936 Canberra ACT 2601 Tel: (02) 6268 7166 Email: [email protected] Website: aic.gov.au Please note: Minor revisions are occasionally made to publications after release. The online versions available on the AIC website will always include any revisions. Disclaimer: This research report does not necessarily reflect the policy position of the Australian Government. General editor: Dr Rick Brown, Deputy Director, Australian Institute of Criminology Edited and typeset by the Australian Institute of Criminology A full list of publications in the AIC Reports series can be found on the Australian Institute of Criminology website at aic.gov.au ii Contents vii Acknowledgements 30 Prosecution of identity crime and related viii Acronyms and abbreviations offences ix Abstract 34 Self-reported victimisation -

NATIONAL POLICE CHECKING SERVICE (NPCS) APPLICATION/CONSENT FORM Risk Group Pty Ltd Individuals
NATIONAL POLICE CHECKING SERVICE (NPCS) APPLICATION/CONSENT FORM Risk Group Pty Ltd Individuals Please select appropriate box only: Reference No. Employee Contractor/Consultant Volunteer Other (Please specify) SECTION 1: PERSONAL INFORMATION - Use BLOCK LETTERS and black ink to complete this form. Mark checkboxes with an X. Names by which I am, or have been, known If more room is required, please list in the space provided at Section 6 on page 3 Family Name (Primary) First Name (Primary) Middle Names Aliases (Family Name first) Previous Names Maiden Name Birth Details Date of Birth Country State/Territory (dd/mm/yyyy) of Birth of Birth Suburb/Town Gender Male Female Unknown/Other of Birth Australian Licences Driver's Licence No. State/Territory Firearms Licence No. State/Territory Contact Details Phone Home ( ) Mobile Work ( ) Email Permanent Residential Address Over Last Five Years If more room is required, please list in the space provided at Section 6 on page 3. If full details of previous addresses are unavailable, details of town(s) and If actual dates are unavailable, details of state(s)/territory(ies) of residence will suffice. year of residence will suffice. CURRENT No./Street Period of Residence: Suburb P'code Year From State/ Country Territory PREVIOUS (IF APPLICABLE) No./Street Period of Residence: Suburb P'code Year From State/ Year To Territory Country PREVIOUS (IF APPLICABLE) No./Street Period of Residence: Suburb P'code Year From State/ Territory Country Year To Copyright ©2016 Risk Group Pty Ltd Individuals Form v3.0 All rights reserved Page 1 SECTION 2: PROOF OF IDENTITY (100-POINT CHECK) When applying for a national police history check you must provide proof of your identity with your application. -

Preventing Another Australia Card Fail Unlocking the Potential of Digital Identity
Embargoed until 11.59pm, 17 October 2018 AEST. Media may report 18 October 2018. Preventing another Australia Card fail Unlocking the potential of digital identity Fergus Hanson Policy Brief Report No. 9/2018 Embargoed until 11.59pm, 17 October 2018 AEST. Media may report 18 October 2018. About the author Fergus Hanson is the head of the ASPI International Cyber Policy Centre. He is the author of Internet wars and has published widely on a range of cyber and foreign policy topics. He was a visiting fellow at the Brookings Institution and a Professional Fulbright Scholar based at Georgetown University working on the uptake of new technologies by the US Government. He has worked for the UN, was a program director at the Lowy Institute and served as a diplomat at the Australian Embassy in The Hague. He has been a fellow at Cambridge University’s Lauterpacht Research Centre for International Law and the Centre for Strategic and International Studies, Pacific Forum. He has published widely in Australian and international media. What is ASPI? The Australian Strategic Policy Institute (ASPI) was formed in 2001 as an independent, non‑partisan think tank. Its core aim is to provide the Australian Government with fresh ideas on Australia’s defence, security and strategic policy choices. ASPI is responsible for informing the public on a range of strategic issues, generating new thinking for government and harnessing strategic thinking internationally. ASPI International Cyber Policy Centre The ASPI International Cyber Policy Centre’s mission is to shape debate, policy and understanding on cyber issues, informed by original research and close consultation with government, business and civil society. -

Marie Johnson
Marie Johnson 2015 European Digital Identity Conference Managing Director and Chief Digital Officer 15 – 16 April 2015 The Netherlands Centre for Digital Business www.centre-for-digital-business.com themes… o Did we not see the digital era coming? o Digital Government and digital identity Historical perspective o The Machinery of Government & the economy Individuals – Businesses -Things o Proof of identity, payments…and politics o The rise of the platforms of the 21st Century …and the obsolescence of silos Digital Identity in Australia…. Digital Identity in Australia…. Identity Crime 2014... Financial Systems Report Inquiry …what’s happened in the past 30 years? …did we not see the digital era coming? o Economic impact - $1.6 billion every year. o Australia does not have a single over- arching technology strategy in place. o Limited use of the Document Verification Service by Government agencies o Has not yet developed a detailed approach for the future of digital o Fraudulent identity credentials – cheap identities and easy to obtain o Recommended - national strategy for federated-style model of trusted digital identities. Digital Identity in Australia…. a history: Australian Government digital & identity strategies 2014 Australia 1996 2000 2001 2006 2007 2008 2009 Card 1987 Visa Reliance 2014 Pricing Framework Transformation 2009 2010 2011 2011 2012 2013 2013 NCOA 2014 Digital Identity in Australia…. 1987 – the Australia Card o A national system of identification. o Main purpose: prevent losses to revenue through taxation system and through payment of Commonwealth Government benefits. o Estimated additional AUD$800 million (1987) revenue collected within 3 years o Thirteen Government agencies would use the Australia Card identity. -

Fahcsia Letterhead Template
Proof of Identity The Department may ask you to provide proof of your identity for the Business Services Wage Assessment Tool Scheme. To provide proof of your identity to the Department, you must provide Proof of Identity documents that meet the 100 point check. This is done by providing certified documents from the list on the attached pages. One of the documents from the list must contain a photograph. Together, these documents must, as a minimum, also provide evidence of your date of birth and signature. If your name used in one document is different from that shown on the other documents provided, evidence of the name change is also to be provided (for example, Marriage or Change of Name Certificate, or divorce papers issued by the Family Court). These documents DO NOT count towards the 100 points. Please do not send us your original documents. Certified copies must be signed by the appropriately qualified certifying person and they should also write the following information on the identity documents. “I certify this is a true and unaltered copy of the original” Name: Position: Date: Further information is available at Attachment B Certifying Documents. (Link) Document Explanation/Description Points Citizenship Certificate Australian citizenship certificate in your name/former 70 name. Australian Passport Current Australian passport in your name/former name. 70 (current) Australian Birth Original Australian birth certificate or birth extract in your 70 Certificate name/former name. Certificate of Evidence Certificate of Evidence of Residence Status (Form 283) 70 of Resident Status issued by the Department of Immigration and Multicultural Affairs, showing your name/former name. -
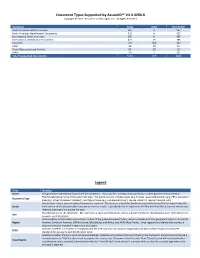
Document Types Supported by Assureid™ V4.4.4260.0 Legend
Document Types Supported by AssureID™ V4.4.4260.0 Copyright © 2016 - AssureTec Technologies, Inc. All Rights Reserved. Summary Total ICAO Non-ICAO North American Driver's Licenses 967 0 967 North American Identification Documents 425 6 419 International Driver's Licenses 387 0 387 International Identification Documents 425 39 386 Passports 743 604 139 Visas 59 49 10 Travel Documents and Permits 83 50 33 Other 103 1 102 Total Supported Documents 3192 749 2443 Legend Term Meaning Issuer The government jurisdiction that issued the document. This could be a country, state, province, or other government jurisdiction The full descriptive name of the document type. The name typically includes issuer (e.g. France), issuer abbreviation (e.g. FRA), document Document Type class (e.g. driver’s license or passport), and type of issue (e.g. commercial driver’s license, under 21, learner’s permit, etc.) Jurisdictions release new versions of documents regularly. The Series is a label that has been assigned by AssureTec to uniquely identify Series each version of the document (also known as series or issue). Typically the Series represents the first year that the document version was released, but that is not always the case The physical size of the document. ID1 represents a card-sized document such as a driver’s license or identification card. ID3 represents a Size passport-sized document Certain editions of AssureID only include a subset of the global document library, which is divided into four geographic regions: NA=North Region America, SA=South America, EMEA=Europe, Middle East, and Africa, and APAC=Asia-Pacific. -

The Identity Project : an Assessment of the UK Identity Cards Bill and It's Implications
LSE Research Online Report The identity project : an assessment of the UK Identity Cards Bill and it's implications Research coordinators : Simon Davies, Ian Hosein & Edgar A. Whitley LSE has developed LSE Research Online so that users may access research output of the School. Copyright © and Moral Rights for the papers on this site are retained by the individual authors and/or other copyright owners. Users may download and/or print one copy of any article(s) in LSE Research Online to facilitate their private study or for non-commercial research. You may not engage in further distribution of the material or use it for any profit-making activities or any commercial gain. You may freely distribute the URL (http://eprints.lse.ac.uk) of the LSE Research Online website. You may cite this version as: Davies, Simon; Hosein, Ian & Whitley, Edgar A. (2005). The identity project : an assessment of the UK Identity Cards Bill and it's implications [online]. London: LSE Research Online. Available at: http://eprints.lse.ac.uk/archive/00000684 This is a copy of a report produced for the Identity Project by the Department of Information Systems © 2005 London School of Economics and Political Science Original available at http://is2.lse.ac.uk/IDcard/default.htm http://eprints.lse.ac.uk Contact LSE Research Online at: [email protected] The Identity Project an assessment of the UK Identity Cards Bill and its implications The Identity Project An assessment of the UK Identity Cards Bill and its implications Project Management by Hosted and -

Identity Cards: the Major Issues (Current Issues Brief, No. 1, 1985-86)
ISSN 0726-3244 G Commonwealth of Austral ia 1985 The views expressed in this paper are those of the author and do not necessarily reflect those of the Legislative Research Service, or the Department of the Par1iamentary Library. Pub1 ished by the Department of the Par1 iamentary Library, July 1985. Printed by C.J. THOMI~SON,Commonwealth Government Printer, Canberril CONTE~T$ The Australia Card Proposal 3 The Type of Identity Card 5 Uses and A~vantages of Identl'ty Cards 6 Comments Supporting the Introduction of Identity Cards 7 Arguments Against Identity Cards: Phi 'sosophical 8 Case Study - possible wider uses of specific purpose cards 11 The Dehumanising Effect 12 Arguments Against I~~~~~i~yCards: ~~a~t~cal12 Costs 12 Forgeries 13 Specific Purpose Identity Cards 13 Social Security Fraud 14 Concl usi on 14 Methods of Identifying Social Welfare Recipients in Selected Countries 17 Arguments Related to Tax Evasion (Michael Peacock) 18 -1 Identity Cards - The Major Issues INTRODUCTION One of the hardy perennials of Australian politics and public debate is the issue of whether or not Australian citizens should be issued with identity cards. Every so often someone in the community calls for identity or ID cards to be issued, describing them as the answer to a parti cul ar probl em. This paper seeks to contribute to the current debate by presenting same of the major issues. The first part identifies the factors which have generated the present public debate. Then follows an outline of the Commmonwealth's proposals for a national identification scheme, called the Australia Card. -

Australia's Proposed ID Card: Still Quacking Like a Duck
University of New South Wales University of New South Wales Faculty of Law Research Series Year 2007 Paper 1 Australia’s Proposed ID Card: Still Quacking Like A Duck Graham Greenleaf∗ ∗University of New South Wales This working paper is hosted by The Berkeley Electronic Press (bepress) and may not be commer- cially reproduced without the permission of the copyright holder. http://law.bepress.com/unswwps-flrps/art1 Copyright c 2007 by the author. Australia’s Proposed ID Card: Still Quacking Like A Duck Graham Greenleaf Abstract Almost twenty years ago, Australia rejected the attempts of the Hawke Labor Gov- ernment to introduce a national ID card system, the ‘Australia Card’. Australia in 2006 is debating the proposed introduction of what the conservative Howard government calls a ‘health and social services Access Card’. It is therefore infor- mative to compare the current proposal with that of 20 years ago. No matter what the government prefers to call it, if it has a sufficient ‘family resemblance’ to the one ‘ID card’ and ID system that we knew – and most people loathed - then it is one. The purpose of this paper is principally to explore that issue: if the ‘Australia Card’ was a national ID card scheme, then is the 2006 ‘Access Card’ proposal also one according to the same criteria? Such a comparison is also a useful way to ex- plain what is proposed in the ‘Access Card’ proposals, by providing a comparison with what was technically feasible 20 years ago, compared with the significant changes in the new smart-card based proposal. -

Roger Clarke's 'Australia Card' 12/11/03, 10:06 AM
Roger Clarke's 'Australia Card' 12/11/03, 10:06 AM Just Another Piece of Plastic for your Wallet: The 'Australia Card' Scheme Roger Clarke Principal, Xamax Consultancy Pty Ltd , Canberra © Xamax Consultancy Pty Ltd , 1987 Published in Prometheus 5,1 (June 1987). Republished in Computers & Society 18,1 (January 1988), together with an important Addendum, published in Computers & Society 18,3 (July 1988) This document is at http://www.anu.edu.au/people/Roger.Clarke/DV/OzCard.html Abstract During 1985-86 the Federal Government developed a proposal for a national identification scheme. Following increasing public concern about the scheme's implications, the Australia Card Bill was defeated in the Senate in November 1986. This paper outlines the proposal, and comments on its technical features, its economics, and its implications. Background During early 1985 the Federal Government embarked upon a campaign to address the problems of widespread tax evasion and tax avoidance. The Draft White Paper on Tax Reform which was released in the lead-up to the ill-fated Tax Summit in July 1985 mentioned, in a few words, the possibility of a 'national identification system'. It appears that a tax lobbyist, Eric Risstrom, President of the Tax Payers' Association, had suggested the idea directly to the Prime Minister, Bob Hawke, in March. The idea struck a chord in the upper echelons of a public service beset with the problems of administering large-scale welfare, tax and social control programmes in a country whose law and customs traditionally provide considerable scope to the individual. It was publicly floated by a senior tax official shortly afterwards, and discussed by Caucus in April-May. -

Reshaping the Welfare State in Australia
The Journal of Sociology & Social Welfare Volume 21 Issue 3 September Article 11 September 1994 From Entitlement to Contract: Reshaping the Welfare State in Australia Richard Weatherley University of Washington Follow this and additional works at: https://scholarworks.wmich.edu/jssw Part of the Social Work Commons Recommended Citation Weatherley, Richard (1994) "From Entitlement to Contract: Reshaping the Welfare State in Australia," The Journal of Sociology & Social Welfare: Vol. 21 : Iss. 3 , Article 11. Available at: https://scholarworks.wmich.edu/jssw/vol21/iss3/11 This Article is brought to you by the Western Michigan University School of Social Work. For more information, please contact [email protected]. From Entitlement to Contract: Reshaping the Welfare State in Australia RICHARD WEATHERLEY University of Washington Australia has sought to contain social welfare expenditures through more stringent targeting of benefits, increased scrutiny of applicants, and by requiring more vigorous job search and trainingactivities. The changes implemented since the Labor Party assumed office in 1983 represent the most sweeping restructuringof the Australian welfare state in 50 years. They mark a shift from an individualistic, rights-based view of welfare state entitlements to one stressing reciprocal obligations. This article examines the origin and implications of this reshaping of Australia's welfare state programs. It considers the dilemmas of enforcing work- related obligations and other compliance measures in an era of persistent, high unemployment. As the Clinton administration ponders it's committment to welfare reform, it might well consider the experience of Aus- tralia. Like many other industrialized nations, a lagging econ- omy has prompted a reassessment of Australia's welfare state programs and services.