Malwarebytes Windows Firewall Control User Guide Version 6.7.0.0 August 22, 2021
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Lab Report: 7.1.6 Configure Windows Defender
Lab Report: 7.1.6 Configure Windows Defender Your Performance Your Score: 0 of 6 (0%) Pass Status: Not Passed Elapsed Time: 12 seconds Required Score: 100% Task Summary Perform a full scan once per week Hide Details Perform the scan on Saturday Perform the scan at midnight (12:00 am) Perform a full system scan Check for updates before scanning Configure default actions to take Hide Details Remove severe alert items Remove high alert items Remove medium alert items Allow low alert items Apply recommended actions to items detected during a scan Configure advanced options Hide Details Scan email Scan removable drives Display items from all users of this computer Perform a quick scan Explanation In this lab, your task is to configure Windows Defender as follows: Automatic scanning setting: Frequency: Saturday Approximate time: 12:00 am Type: Full scan (A quick scan checks the areas of the computer that spyware is likely to affect, and a full scan checks all files and programs on the computer) Check for updated definitions before scanning: Enabled Default actions settings: Severe alert items: Remove High alert items: Remove Medium alert items: Remove Low alert items: Allow Apply recommended actions: Enabled Advanced settings: Scan email: Enabled Scan removable drives: Enabled Administrator settings: Display items from all users of this computer: Enabled Complete this lab as follows: 1. Right-click Start > Control Panel. 2. In the top right corner under View by, select Small icons from the drop-down list. 3. Select Windows Defender. 4. Select Tools. 5. Under Settings, select Options. 6. Make sure Automatically scan my computer (recommended) is selected to allow Windows Defender to scan the computer automatically. -

Checks to Avoid Malware Protect Your Laptop with Security Essentials
What is Malware? Malware is software that can infect you computer and can be a virus or malicious software that can harm & slow your system or try to steal your personal information. To help avoid malware follow the check list below. Checks to avoid Malware Check you have updated Antivirus software installed such as Microsoft Security Essentials Install and run an Anti-Malware program such as Malwarebytes Uninstall any Peer 2 Peer software such as Limewire or Vuze Be careful with email attachments and never respond to mails asking for your password Protect your Laptop with Security Essentials Microsoft Security Essentials is a free antivirus software product for Windows Vista, 7 & 8. It pro- vides protection against different types of malware such as computer virus, spyware, rootkits, trojans & other malicious software. Download & install Security Essentials from the following link http:// www.microsoft.com/security_essentials/ Clear Infections using Malwarebytes Malware bytes is free to download & install from http://www.malwarebytes.org Once installed it is recommended that you run a Full Scan of your laptop to check for any malware that may reside on the system. Once complete, follow the on screen instructions to finish removing any threats found. You should regularly run updates and scans to ensure your system remains clean. It is also advisable to scan external storage devices such as USB keys as they can spread infections. If the above criteria are fully met, ISS staff at the service desk on the ground floor of the library are happy to investigate problems on your laptop For more information go to http://www.dcu.ie/iss ISS online service desk: https://https://iss.servicedesk.dcu.ie Follow ISS on Twitter @ISSservice . -

Mitigating Service Account Credential Theft on Windows
Mitigating Service Account Credential Theft on Windows Reducing the risk of automated authentication against untrusted endpoints Version 1.0.0 Last Updated: 2014-09-16 Mitigating Service Account Credential Theft on Windows Disclaimer This document is for informational purposes only. The authors make no warranties, express, implied, or statutory as to the information in the document. This document is provided "as-is". Information and views expressed in this document, including URLs and other Internet website references, may change without notice. You bear the risk of using it. This document is provided under the Creative Commons Attribution 4.0 International (CC BY 4.0) license. The names of actual companies and products mentioned herein may be the trademarks of their respective owners. Authors HD Moore Joe Bialek Ashwath Murthy Rapid7 Microsoft Palo Alto Networks Contents Executive Summary ................................................................................................................................................................ 1 Introduction ............................................................................................................................................................................ 2 Attacks .................................................................................................................................................................................... 2 Kerberos ............................................................................................................................................................................. -

Testing Anti-Virus in Linux: How Effective Are the Solutions Available for Desktop Computers?
Royal Holloway University of London ISG MSc Information Security thesis series 2021 Testing anti-virus in Linux: How effective are the solutions available for desktop computers? Authors Giuseppe Raffa, MSc (Royal Holloway, 2020) Daniele Sgandurra, Huawei, Munich Research Center. (Formerly ISG, Royal Holloway.) Abstract Anti-virus (AV) programs are widely recognized as one of the most important defensive tools available for desktop computers. Regardless of this, several Linux users consider AVs unnec- essary, arguing that this operating system (OS) is “malware-free”. While Windows platforms are undoubtedly more affected by malicious software, there exist documented cases of Linux- specific malware. In addition, even though the estimated market share of Linux desktop sys- tems is currently only at 2%, it is certainly possible that it will increase in the near future. Considering all this, and the lack of up-to-date information about Linux-compatible AV solutions, we evaluated the effectiveness of some anti-virus products by using local installations, a well- known on-line malware scanning service (VirusTotal) and a renowned penetration testing tool (Metasploit). Interestingly, in our tests, the average detection rate of the locally-installed AV programs was always above 80%. However, when we extended our analysis to the wider set of anti-virus solutions available on VirusTotal, we found out that the average detection rate barely reached 60%. Finally, when evaluating malicious files created with Metasploit, we verified that the AVs’ heuristic detection mechanisms performed very poorly, with detection rates as low as 8.3%.a aThis article is published online by Computer Weekly as part of the 2021 Royal Holloway informa- tion security thesis series https://www.computerweekly.com/ehandbook/Royal-Holloway-Testing-antivirus- efficacy-in-Linux. -

Windows Server Security Best Practices
Windows Server Security – Best Practices v.3.0.5 Windows Server Security Best Practices Revised – February 7, 2020 Version 2.0.0 ______________________________________________________________________________________ Page 1 of 10 Windows Server Security – Best Practices v.3.0.5 Initial Document Created by: 2009 Windows Server Security Best Practices Committee Document Creation Date: August 21, 2009 Revision Revised by: 2019 Windows Server Security Best Practices Committee Revision Date: February 7, 2020 Version Number: 2.0.0 Acknowledgments The final release document is a collaborative work between the following committee members: Freddie Lewis Khushbu Desai Theodore McDonald Tanya Sootes Usage The ever-changing nature of information technology prevents this document from being entirely inclusive but should serve as a general guideline. This document is not intended to supersede or replace policy. Please feel free to query the Windows Server Team ([email protected]) or the Systems Administrator Group ([email protected]) for additional guidance. ______________________________________________________________________________________ Page 2 of 10 Windows Server Security – Best Practices v.3.0.5 Table of Contents Initial Document 2 Revision 2 Acknowledgments 2 Usage 2 1. Security Best Practices 5 1.1. User Environment 5 1.1.1. Server Account Control 5 1.1.2. Administrator and Equivalents 5 1.1.3. Delegating Control 5 1.1.4. Password Policy 5 1.2. File and Print Serving 5 1.2.1. Folder and NTFS Permissions 5 1.2.2. Print Management 6 1.3. Remote Access 6 1.3.1. Remote Desktop 6 1.3.2. Off-Campus Access 6 1.4. OS Configuration and Maintenance 6 1.4.1. -

Highly Predictive Blacklisting
We Introduce the Highly predIc- tive Blacklist (HPB) service, which is now Jian Zhang, Philli P P o rr a S , a n d JohanneS ullRich integrated into the DShield.org portal [1]. The HPB service employs a radically differ- ent approach to blacklist formulation than that of contemporary blacklist formulation highly predictive strategies. At the core of the system is a ranking scheme that measures how closely blacklisting related an attack source is to a blacklist con- Jian Zhang is an assistant professor in the depart- sumer, based on both the attacker’s history ment of computer science at Louisiana State and the most recent firewall log produc- University. His research interest is in developing new machine-learning methods for improving tion patterns of the consumer. Our objec- cybersecurity. tive is to construct a customized blacklist [email protected] per repository contributor that reflects the Phillip Porras is a Program Director of systems se- most probable set of addresses that may curity research in the Computer Science Laboratory attack the contributor in the near future. at SRI International. His research interests include malware and intrusion detection, high-assurance We view this service as a first experimental computing, network security, and privacy-preserv- ing collaborative systems. step toward a new direction in high-quality [email protected] blacklist generation. As Chief Research Officer for the SANS Institute, For nearly as long as we have been detecting mali- Johannes Ullrich is currently responsible for the SANS Internet Storm Center (ISC) and the GIAC cious activity in networks, we have been compil- Gold program. -

Hostscan 4.8.01064 Antimalware and Firewall Support Charts
HostScan 4.8.01064 Antimalware and Firewall Support Charts 10/1/19 © 2019 Cisco and/or its affiliates. All rights reserved. This document is Cisco public. Page 1 of 76 Contents HostScan Version 4.8.01064 Antimalware and Firewall Support Charts ............................................................................... 3 Antimalware and Firewall Attributes Supported by HostScan .................................................................................................. 3 OPSWAT Version Information ................................................................................................................................................. 5 Cisco AnyConnect HostScan Antimalware Compliance Module v4.3.890.0 for Windows .................................................. 5 Cisco AnyConnect HostScan Firewall Compliance Module v4.3.890.0 for Windows ........................................................ 44 Cisco AnyConnect HostScan Antimalware Compliance Module v4.3.824.0 for macos .................................................... 65 Cisco AnyConnect HostScan Firewall Compliance Module v4.3.824.0 for macOS ........................................................... 71 Cisco AnyConnect HostScan Antimalware Compliance Module v4.3.730.0 for Linux ...................................................... 73 Cisco AnyConnect HostScan Firewall Compliance Module v4.3.730.0 for Linux .............................................................. 76 ©201 9 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. -

Page 1 of 3 Virustotal
VirusTotal - Free Online Virus, Malware and URL Scanner Page 1 of 3 VT Community Sign in ▼ Languages ▼ Virustotal is a service that analyzes suspicious files and URLs and facilitates the quick detection of viruses, worms, trojans, and all kinds of malware detected by antivirus engines. More information... 0 VT Community user(s) with a total of 0 reputation credit(s) say(s) this sample is goodware. 0 VT Community VT Community user(s) with a total of 0 reputation credit(s) say(s) this sample is malware. File name: wsusoffline71.zip Submission date: 2011-11-01 08:16:44 (UTC) Current status: finished not reviewed Result: 0 /40 (0.0%) Safety score: - Compact Print results Antivirus Version Last Update Result AhnLab-V3 2011.10.31.00 2011.10.31 - AntiVir 7.11.16.225 2011.10.31 - Antiy-AVL 2.0.3.7 2011.11.01 - Avast 6.0.1289.0 2011.11.01 - AVG 10.0.0.1190 2011.11.01 - BitDefender 7.2 2011.11.01 - CAT-QuickHeal 11.00 2011.11.01 - ClamAV 0.97.3.0 2011.11.01 - Commtouch 5.3.2.6 2011.11.01 - Comodo 10625 2011.11.01 - Emsisoft 5.1.0.11 2011.11.01 - eSafe 7.0.17.0 2011.10.30 - eTrust-Vet 36.1.8650 2011.11.01 - F-Prot 4.6.5.141 2011.11.01 - F-Secure 9.0.16440.0 2011.11.01 - Fortinet 4.3.370.0 2011.11.01 - GData 22 2011.11.01 - Ikarus T3.1.1.107.0 2011.11.01 - Jiangmin 13.0.900 2011.10.31 - K7AntiVirus 9.116.5364 2011.10.31 - Kaspersky 9.0.0.837 2011.11.01 - McAfee 5.400.0.1158 2011.11.01 - McAfee-GW-Edition 2010.1D 2011.10.31 - Microsoft 1.7801 2011.11.01 - NOD32 6591 2011.11.01 - Norman 6.07.13 2011.10.31 - nProtect 2011-10-31.01 2011.10.31 - http://www.virustotal.com/file -scan/report.html?id=874d6968eaf6eeade19179712d53 .. -

Key Benefits Core Technologies and Technical Features
Advanced threat prevention Malwarebytes Endpoint Security is an innovative platform that delivers powerful multi- layered defense for smart endpoint protection. Malwarebytes Endpoint Security enables small and large enterprise businesses to thoroughly protect against the latest malware and advanced threats—including stopping known and unknown exploit attacks. Key Benefits Blocks zero-hour malware Easy management Reduces the chances of data exfiltration and saves Simplifies endpoint security management and identifies on IT resources by protecting against zero-hour vulnerable endpoints. Streamlines endpoint security malware that traditional security solutions can miss. deployment and maximizes IT management resources. Saves legacy systems Scalable threat prevention Protects unsupported programs by armoring Deploys protection for every endpoint and scales as vulnerabilities against exploits. your company grows. Increases productivity Detects unprotected systems Maintains end-user productivity by preserving Discovers all endpoints and installed software on your system performance and keeping staff on revenue- network. Systems without Malwarebytes that are positive projects. vulnerable to cyber attacks can be easily secured. Core Technologies and Technical Features Anti-Malware Proactive anti-malware/anti-spyware scanning Three system scan modes (Quick, Flash, Full) engine Enables selection of the most efficient system scan Detects and eliminates zero-hour and known based on endpoint security requirements and available viruses, Trojans, worms, rootkits, adware, and system resources. spyware in real time to ensure data security and network integrity. Extends its protection to Windows Server operating systems. | Santa Clara, CA | malwarebytes.com | [email protected] | 1.800.520.2796 Advanced threat prevention Malicious website blocking Advanced malware remediation Prevents access to known malicious IP addresses Employs delete-on-reboot to remove persistent or so that end users are proactively protected from deeply embedded malware. -
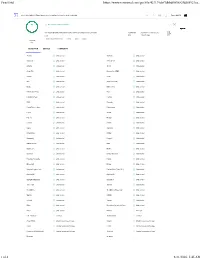
Virustotal Scan on 2020.08.21 for Pbidesktopsetup 2
VirusTotal https://www.virustotal.com/gui/file/423139def3dbbdf0f5682fdd88921ea... 423139def3dbbdf0f5682fdd88921eaface84ff48ef2e2a8d20e4341ca4a4364 Patch My PC No engines detected this file 423139def3dbbdf0f5682fdd88921eaface84ff48ef2e2a8d20e4341ca4a4364 269.49 MB 2020-08-21 11:39:09 UTC setup Size 1 minute ago invalid-rich-pe-linker-version overlay peexe signed Community Score DETECTION DETAILS COMMUNITY Acronis Undetected Ad-Aware Undetected AegisLab Undetected AhnLab-V3 Undetected Alibaba Undetected ALYac Undetected Antiy-AVL Undetected SecureAge APEX Undetected Arcabit Undetected Avast Undetected AVG Undetected Avira (no cloud) Undetected Baidu Undetected BitDefender Undetected BitDefenderTheta Undetected Bkav Undetected CAT-QuickHeal Undetected ClamAV Undetected CMC Undetected Comodo Undetected CrowdStrike Falcon Undetected Cybereason Undetected Cyren Undetected eScan Undetected F-Secure Undetected FireEye Undetected Fortinet Undetected GData Undetected Ikarus Undetected Jiangmin Undetected K7AntiVirus Undetected K7GW Undetected Kaspersky Undetected Kingsoft Undetected Malwarebytes Undetected MAX Undetected MaxSecure Undetected McAfee Undetected Microsoft Undetected NANO-Antivirus Undetected Palo Alto Networks Undetected Panda Undetected Qihoo-360 Undetected Rising Undetected Sangfor Engine Zero Undetected SentinelOne (Static ML) Undetected Sophos AV Undetected Sophos ML Undetected SUPERAntiSpyware Undetected Symantec Undetected TACHYON Undetected Tencent Undetected TrendMicro Undetected TrendMicro-HouseCall Undetected VBA32 Undetected -

Antivirus Software Before It Can Detect Them
Computer virus A computer virus is a computer program that can copy itself and infect a computer without the permission or knowledge of the owner. The term "virus" is also commonly but erroneously used to refer to other types of malware, adware, and spyware programs that do not have the reproductive ability. A true virus can only spread from one computer to another (in some form of executable code) when its host is taken to the target computer; for instance because a user sent it over a network or the Internet, or carried it on a removable medium such as a floppy disk, CD, DVD, or USB drive. Viruses can increase their chances of spreading to other computers by infecting files on a network file system or a file system that is accessed by another computer.[1][2] The term "computer virus" is sometimes used as a catch-all phrase to include all types of malware. Malware includes computer viruses, worms, trojan horses, most rootkits, spyware, dishonest adware, crimeware, and other malicious and unwanted software), including true viruses. Viruses are sometimes confused with computer worms and Trojan horses, which are technically different. A worm can exploit security vulnerabilities to spread itself to other computers without needing to be transferred as part of a host, and a Trojan horse is a program that appears harmless but has a hidden agenda. Worms and Trojans, like viruses, may cause harm to either a computer system's hosted data, functional performance, or networking throughput, when they are executed. Some viruses and other malware have symptoms noticeable to the computer user, but many are surreptitious. -

MSI Afterburner V4.6.4
MSI Afterburner v4.6.4 MSI Afterburner is ultimate graphics card utility, co-developed by MSI and RivaTuner teams. Please visit https://msi.com/page/afterburner to get more information about the product and download new versions SYSTEM REQUIREMENTS: ...................................................................................................................................... 3 FEATURES: ............................................................................................................................................................. 3 KNOWN LIMITATIONS:........................................................................................................................................... 4 REVISION HISTORY: ................................................................................................................................................ 5 VERSION 4.6.4 .............................................................................................................................................................. 5 VERSION 4.6.3 (PUBLISHED ON 03.03.2021) .................................................................................................................... 5 VERSION 4.6.2 (PUBLISHED ON 29.10.2019) .................................................................................................................... 6 VERSION 4.6.1 (PUBLISHED ON 21.04.2019) .................................................................................................................... 7 VERSION 4.6.0 (PUBLISHED ON