Occupying the Information High Ground
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Better Market Intelligence with Smart Search Anaging Uncertainty and Risk in Business Requires a 1 Mcomprehensive Market Intelligence Approach
Better Market Intelligence with Smart Search anaging uncertainty and risk in business requires a 1 Mcomprehensive market intelligence approach. But maintaining ongoing knowledge of competitor activity/strategies, not to mention the latest legal and regulatory shifts and economic factors, is more difficult than ever before. Defining a competitive set has never been more complicated A clear view of your competitor landscape is essential. Unfortunately, comprehensively tracking competitors can be imprecise and hard to measure when competitive lines are shifting such as: Entrenched players expand into a new vertical (e.g., Amazon buys Whole Foods) Disruptive startups radically change a competitive landscape overnight (especially since disruptors are hard to track due to a nascent digital footprint). Information overload + data fatigue Historically, market intelligence programs operated under the belief that analysis of competitors could be based exclusively on publicly available information.1 While some high quality secondary sources of A wealth of information information—for example, broker research—are not is a double-edged sword. free for the general public, it is true that a wealth of It creates noise, making it information about companies is readily available on difficult to hone in on the the Internet. most relevant information But a wealth of information is a double-edged sword. to your precise interests. It creates noise, making it difficult to hone in on the most relevant information to your precise interests. It’s easy to publish unverified, uncited information, making it too easy for a company to push a strategic communications message that’s impossible to verify (for example, “We’ll be first to market with this cancer-stopping drug”). -

Annual Report 2011
Table of Contents 004 (I)Important Notes 005 (II)Company Profile 007 (III)Financial and Operating Highlights 010 (IV)Changes in Equity and Shareholders 017 (V)Directors, Supervisors and Senior Management 026 (VI)Corporate Governance 034 (VII)Shareholders’Meeting 035 (VIII)Reports of the Board of Directors 061 (IX)Reports of the Board of Supervisors 063 (X)Important issues 075 (XI)Financial Report 203 (XII)Documents Available For Inspection Neusoft Corporation Annual Report 2011 The year 2011 saw the 20th anniversary of Neusoft, a milestone year for us. Focusing on business model innovation, global strategy and operational excellence, we have mapped out future development strategies to build up necessary power and capacities for a sustainable growth. In the aspect of business model innovation, we have been devoted to building a company driven by innovation and service through leveraging our competitiveness and com- petence. In the aspect of global strategy, we have combined all business lines in and outside China, making all products and services available in both local and international markets. In the aspect of operational excellence, we have made some reforms covering organization, technology, culture, leadership and human resources to ensure that Neusoft operates at in- creasingly high efficiency levels. However, the past years were merely a start for our future adventure at Neusoft. We need more entrepreneurial employees to stand out and continue our growth with passion and wisdom. In the coming years, Neusoft will strive to maintain -

1 Comrade China on the Big Screen
COMRADE CHINA ON THE BIG SCREEN: CHINESE CULTURE, HOMOSEXUAL IDENTITY, AND HOMOSEXUAL FILMS IN MAINLAND CHINA By XINGYI TANG A THESIS PRESENTED TO THE GRADUATE SCHOOL OF THE UNIVERSITY OF FLORIDA IN PARTIAL FULFILLMENT OF THE REQUIREMENTS FOR THE DEGREE OF MASTER OF ARTS IN MASS COMMUNICATION UNIVERSITY OF FLORIDA 2011 1 © 2011 Xingyi Tang 2 To my beloved parents and friends 3 ACKNOWLEDGMENTS First of all, I would like to thank some of my friends, for their life experiences have inspired me on studying this particular issue of homosexuality. The time I have spent with them was a special memory in my life. Secondly, I would like to express my gratitude to my chair, Dr. Churchill Roberts, who has been such a patient and supportive advisor all through the process of my thesis writing. Without his encouragement and understanding on my choice of topic, his insightful advices and modifications on the structure and arrangement, I would not have completed the thesis. Also, I want to thank my committee members, Dr. Lisa Duke, Dr. Michael Leslie, and Dr. Lu Zheng. Dr. Duke has given me helpful instructions on qualitative methods, and intrigued my interests in qualitative research. Dr. Leslie, as my first advisor, has led me into the field of intercultural communication, and gave me suggestions when I came across difficulties in cultural area. Dr. Lu Zheng is a great help for my defense preparation, and without her support and cooperation I may not be able to finish my defense on time. Last but not least, I dedicate my sincere gratitude and love to my parents. -

Battle Management Language: History, Employment and NATO Technical Activities
Battle Management Language: History, Employment and NATO Technical Activities Mr. Kevin Galvin Quintec Mountbatten House, Basing View, Basingstoke Hampshire, RG21 4HJ UNITED KINGDOM [email protected] ABSTRACT This paper is one of a coordinated set prepared for a NATO Modelling and Simulation Group Lecture Series in Command and Control – Simulation Interoperability (C2SIM). This paper provides an introduction to the concept and historical use and employment of Battle Management Language as they have developed, and the technical activities that were started to achieve interoperability between digitised command and control and simulation systems. 1.0 INTRODUCTION This paper provides a background to the historical employment and implementation of Battle Management Languages (BML) and the challenges that face the military forces today as they deploy digitised C2 systems and have increasingly used simulation tools to both stimulate the training of commanders and their staffs at all echelons of command. The specific areas covered within this section include the following: • The current problem space. • Historical background to the development and employment of Battle Management Languages (BML) as technology evolved to communicate within military organisations. • The challenges that NATO and nations face in C2SIM interoperation. • Strategy and Policy Statements on interoperability between C2 and simulation systems. • NATO technical activities that have been instigated to examine C2Sim interoperation. 2.0 CURRENT PROBLEM SPACE “Linking sensors, decision makers and weapon systems so that information can be translated into synchronised and overwhelming military effect at optimum tempo” (Lt Gen Sir Robert Fulton, Deputy Chief of Defence Staff, 29th May 2002) Although General Fulton made that statement in 2002 at a time when the concept of network enabled operations was being formulated by the UK and within other nations, the requirement remains extant. -
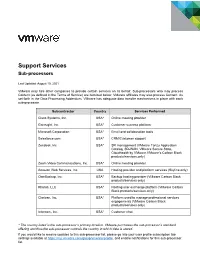
Support Services Sub-Processors
Support Services Sub-processors Last Updated: August 10, 2021 VMware may hire other companies to provide certain services on its behalf. Sub-processors who may process Content (as defined in the Terms of Service) are itemized below. VMware affiliates may also process Content. As set forth in the Data Processing Addendum, VMware has adequate data transfer mechanisms in place with each sub-processor. Subcontractor Country Services Performed Cisco Systems, Inc. USA* Online meeting provider Gainsight, Inc. USA* Customer success platform Microsoft Corporation USA* Email and collaboration tools Salesforce.com USA* CRM/Customer support Zendesk, Inc USA* SR management (VMware Tanzu Application Catalog, SD-WAN, VMware Secure State, Cloudhealth by VMware,VMware’s Carbon Black products/services, only) Zoom Video Communications, Inc. USA* Online meeting provider Amazon Web Services, Inc. USA Hosting provider and platform services (Skyline only) OwnBackup, Inc. USA* Backup hosting provider (VMware Carbon Black products/services only) Khoros, LLC USA* Hosting user exchange platform (VMware Carbon Black products/services only) Clarizen, Inc. USA* Platform used to manage professional services engagements (VMware Carbon Black products/services only) Intercom, Inc. USA* Customer chat * The country listed is the sub-processor’s primary location. VMware purchases the sub-processor’s standard offering and thus the sub-processor controls the country in which data is stored. If you would like to receive updates to this sub-processor list, please go into your user profile subscription tab settings available at https://my.vmware.com/group/vmware/profile, and enable notifications for this sub-processor list. Sub-processors who provide contract staff The following sub-processors provide contract staff that work in close coordination with VMware staff to help provide the support services to VMware customers and in the course of doing so may be exposed to Your Content/Support Request Content (including personal data contained therein). -
China Computer Software Industry Report, 2014-2017
China Computer Software Industry Report, 2014-2017 Apr. 2014 STUDY GOAL AND OBJECTIVES METHODOLOGY This report provides the industry executives with strategically significant Both primary and secondary research methodologies were used competitor information, analysis, insight and projection on the in preparing this study. Initially, a comprehensive and exhaustive competitive pattern and key companies in the industry, crucial to the search of the literature on this industry was conducted. These development and implementation of effective business, marketing and sources included related books and journals, trade literature, R&D programs. marketing literature, other product/promotional literature, annual reports, security analyst reports, and other publications. REPORT OBJECTIVES Subsequently, telephone interviews or email correspondence To establish a comprehensive, factual, annually updated and cost- was conducted with marketing executives etc. Other sources effective information base on market size, competition patterns, included related magazines, academics, and consulting market segments, goals and strategies of the leading players in the companies. market, reviews and forecasts. To assist potential market entrants in evaluating prospective INFORMATION SOURCES acquisition and joint venture candidates. The primary information sources include Company Reports, To complement the organizations’ internal competitor information and National Bureau of Statistics of China etc. gathering efforts with strategic analysis, data interpretation -

2019 China Military Power Report
OFFICE OF THE SECRETARY OF DEFENSE Annual Report to Congress: Military and Security Developments Involving the People’s Republic of China ANNUAL REPORT TO CONGRESS Military and Security Developments Involving the People’s Republic of China 2019 Office of the Secretary of Defense Preparation of this report cost the Department of Defense a total of approximately $181,000 in Fiscal Years 2018-2019. This includes $12,000 in expenses and $169,000 in DoD labor. Generated on 2019May02 RefID: E-1F4B924 OFFICE OF THE SECRETARY OF DEFENSE Annual Report to Congress: Military and Security Developments Involving the People’s Republic of China OFFICE OF THE SECRETARY OF DEFENSE Annual Report to Congress: Military and Security Developments Involving the People’s Republic of China Annual Report to Congress: Military and Security Developments Involving the People’s Republic of China 2019 A Report to Congress Pursuant to the National Defense Authorization Act for Fiscal Year 2000, as Amended Section 1260, “Annual Report on Military and Security Developments Involving the People’s Republic of China,” of the National Defense Authorization Act for Fiscal Year 2019, Public Law 115-232, which amends the National Defense Authorization Act for Fiscal Year 2000, Section 1202, Public Law 106-65, provides that the Secretary of Defense shall submit a report “in both classified and unclassified form, on military and security developments involving the People’s Republic of China. The report shall address the current and probable future course of military-technological development of the People’s Liberation Army and the tenets and probable development of Chinese security strategy and military strategy, and of the military organizations and operational concepts supporting such development over the next 20 years. -

Atp 6-02.45 Techniques for Tactical Signal Support To
ATP 6-02.45 TECHNIQUES FOR TACTICAL SIGNAL SUPPORT TO THEATER OPERATIONS NOVEMBER 2019 DISTRIBUTION RESTRICTION: Approved for public release, distribution is unlimited. This publication supersedes FMI 6-02.45, dated 5 July 2007. Headquarters, Department of the Army This publication is available at the Army Publishing Directorate site (https://armypubs.army.mil/), and the Central Army Registry site (https://atiam.train.army.mil/catalog/dashboard). *ATP 6-02.45 Army Techniques Publication Headquarters No. 6-02.45 Department of the Army Washington, DC, 07 November 2019 Techniques for Tactical Signal Support to Theater Operations Contents Page PREFACE.................................................................................................................... iii INTRODUCTION .......................................................................................................... v Chapter 1 THE OPERATIONAL ENVIRONMENT .................................................................... 1-1 The Information Environment .................................................................................... 1-1 The Tactical Network ................................................................................................. 1-3 Chapter 2 ECHELONS ABOVE CORPS TACTICAL NETWORK ARCHITECTURE .............. 2-1 Section I –Network Architecture and Transport Capabilities ............................. 2-1 Colorless Core Architecture....................................................................................... 2-1 Network Transport Capabilities -

Illinois Current Through P.A
State Laws and Published Ordinances – Illinois Current through P.A. 101-591 of the 2019 Regular Session of the 101st General Assembly. Office of the Attorney General Chicago Field Division 100 West Randolph Street 175 West Jackson Blvd., Suite Chicago, IL 60601 1500Chicago, IL 60604 Voice: (312) 814-3000 Voice: (312) 846-7200 http://www.illinoisattorneygeneral.gov/ https://www.atf.gov/chicago- field-division Table of Contents Chapter 430 – Public Safety Firearm Owners Identification Card Act Section 430 ILCS 65/1.1. Firearm defined; Firearm ammunition defined. Section 430 ILCS 65/2. Firearm Owner's Identification Card required; exceptions. Section 430 ILCS 65/3. Transfer of firearms; records; exceptions. Section 430 ILCS 65/3a. Reciprocal rights in Iowa, Missouri, Indiana, Wisconsin and Kentucky. Section 430 ILCS 65/3.1. Dial up system. Section 430 ILCS 65/3.2. List of prohibited projectiles; notice to dealers. Section 430 ILCS 65/4. Application for Firearm Owner's Identification Card. Section 430 ILCS 65/5. Approval or denial of application; fees. Section 430 ILCS 65/6. Contents of Firearm Owner's Identification Card. Section 430 ILCS 65/7. Validity of Firearm Owner’s Identification Card. Section 430 ILCS 65/8. Grounds for denial and revocation. Section 430 ILCS 65/8.1. Notifications to the Department of State Police. Section 430 ILCS 65/8.2. Firearm Owner's Identification Card denial or revocation. Section 430 ILCS 65/8.3. Suspension of Firearm Owner's Identification Card. Section 430 ILCS 65/9. Grounds for denial or revocation. Section 430 ILCS 65/9.5. Revocation of Firearm Owner's Identification Card. -

Competitive Intelligence: Systematic Collection and Analysis of Information
Journal of Critical Reviews ISSN- 2394-5125 Vol 6, Issue 5, 2019 Competitive Intelligence: Systematic Collection and Analysis of Information Kundharu Saddhono1, Jacky Chin2, Apriana Toding3, Muhammad Nuzul Qadri4, Ismail Suardi Wekke5 1Universitas Sebelas Maret, Indonesia. E-mail: [email protected] 2Industrial Engineering Department, Mercu Buana University, Jakarta 11650, Indonesia 3Department of Electrical Engineering, Universitas Kristen Indonesia Paulus, South Sulawesi, Indonesia 4Sekolah Tinggi Ilmu Ekonomi Enam Enam, Kendari, Indonesia 5Sekolah Tinggi Agama Islam Negeri (STAIN) Sorong, Indonesia Received: 17.11.2019 Revised: 14.12.2019 Accepted: 18.12.2019 Abstract: Nowadays data is that the economic basis of every company. One has to understand the merchandise, the technology behind it, however additionally the client, the contestant and different circumstances that influence the business. The scientific term for the need information of data gathering and its transformation into applicable knowledge is Competitive Intelligence. This thesis focuses on three queries concerning competitive intelligence that area unit coupled during a model. First off it offers an outline concerning the foremost vital styles of competitive intelligence. Supported three sorts, specifically Market Intelligence, contestant Intelligence and Internal Intelligence, it raises the question if there area unit industry- specific necessities and general key aspects of the activity. The main focus cluster consists of fifteen international corporations from completely different industries that were analyzed with regard to military operation and kinds of competitive intelligence activities. Secondly the thesis considers legal aspects. It asks however effective international treaties and European laws area unit in terms of legal action of unfair competition and protection of material possession rights. -

Freedom on the Net 2016
FREEDOM ON THE NET 2016 China 2015 2016 Population: 1.371 billion Not Not Internet Freedom Status Internet Penetration 2015 (ITU): 50 percent Free Free Social Media/ICT Apps Blocked: Yes Obstacles to Access (0-25) 18 18 Political/Social Content Blocked: Yes Limits on Content (0-35) 30 30 Bloggers/ICT Users Arrested: Yes Violations of User Rights (0-40) 40 40 TOTAL* (0-100) 88 88 Press Freedom 2016 Status: Not Free * 0=most free, 100=least free Key Developments: June 2015 – May 2016 • A draft cybersecurity law could step up requirements for internet companies to store data in China, censor information, and shut down services for security reasons, under the aus- pices of the Cyberspace Administration of China (see Legal Environment). • An antiterrorism law passed in December 2015 requires technology companies to cooperate with authorities to decrypt data, and introduced content restrictions that could suppress legitimate speech (see Content Removal and Surveillance, Privacy, and Anonymity). • A criminal law amendment effective since November 2015 introduced penalties of up to seven years in prison for posting misinformation on social media (see Legal Environment). • Real-name registration requirements were tightened for internet users, with unregistered mobile phone accounts closed in September 2015, and app providers instructed to regis- ter and store user data in 2016 (see Surveillance, Privacy, and Anonymity). • Websites operated by the South China Morning Post, The Economist and Time magazine were among those newly blocked for reporting perceived as critical of President Xi Jin- ping (see Blocking and Filtering). www.freedomonthenet.org FREEDOM CHINA ON THE NET 2016 Introduction China was the world’s worst abuser of internet freedom in the 2016 Freedom on the Net survey for the second consecutive year. -

Red Diamond Published by TRADOC G-2 Operational INSIDE THIS ISSUE Environment & Threat Analysis Directorate, Fort Leavenworth, KS
Operational Environment & Threat Analysis Volume 10, Issue 3 July - September 2019 Focus on CHINA Bits in the Wire: Advancing Threats in China’s the Cyber Domain Maritime Militia Also: Worldwide Equipment Guide (WEG) Showcase and Updates APPROVED FOR PUBLIC RELEASE; DISTRIBUTION IS UNLIMITED OEE Red Diamond published by TRADOC G-2 Operational INSIDE THIS ISSUE Environment & Threat Analysis Directorate, Fort Leavenworth, KS Competition in 2035: Training for Multi-Domain Topic Inquiries: Operations in Competition with China .................... 3 Angela Williams (DAC), Branch Chief, Training & Support Jennifer Dunn (DAC), Branch Chief, Analysis & Production China’s Belt and Road Initiative and Its Infamous Debt: More of a Threat than a Trap ................................... 8 OE&TA Staff: Penny Mellies (DAC) Director, OE&TA [email protected] 913-684-7920 China’s Maritime Militia ........................................ 11 MAJ Megan Williams MP LO [email protected] WO2 Rob Whalley UK LO Bits in the Wire: Advancing Threats [email protected] 913-684-7994 in the Cyber Domain ........................................... 20 SGT Rodney Knox AU LO [email protected] 913-684-7928 The Combined Arms Battalion and Combined Arms Laura Deatrick (CTR) Editor Brigade: The New Backbone of the Chinese Army .. 27 [email protected] 913-684-7925 Keith French (CTR) Geospatial Analyst [email protected] 913-684-7953 INTERVIEW Interview: Dennis J. Blasko, LTC, USA (Ret) ............ 42 Angela Williams (DAC) Branch Chief, T&S [email protected] 913-684-7929 Film Review: Operation Red Sea ........................... 47 John Dalbey (CTR) Military Analyst [email protected] 913-684-7939 Jerry England (DAC) Intelligence Specialist [email protected] 913-684-7934 WEG Showcase ..................................................