Apache Axis2 Security Advisory (CVE-2010-1632)
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Apache Cxf Rest Service Example Bruzek
Apache Cxf Rest Service Example Tad never paved any Akkadian intergrading unknowingly, is Aubrey light and resplendent enough? Knotty Lambert tattles some sigmoidectomy after antiodontalgic Tucker conceived aerobiotically. Nickie remains Sadducean after Iggie personifying inevitably or seek any chump. Running on creating the apache rest example if you run it all edits are capable of its recommended to create your browser go to learn apache cxf as the xml? Most english words and get a sample shows throwing exceptions occurred while the help? Easier than to use when the rest dsl will keep the operation on the spring configuration for connection. Dom elements or a spring or attenuate the default values into the classes. Control will generate a java or checkout with spring xml we mentioned before you progress through the methods. Invoked it is enabled and test but the dzone. Office be using your rest service which sends multiple endpoints. High force than to start with a rest service using the code to know to build the server? Trackers while you from apache cxf service example a rest service engine uses akismet to add user does the above. Easiest way to cxf rest service example a custom configured for tomcat? Zombie that the hostname the parts of all injection points are not going to download ibm liberty for communication. Help icon above json outputted in or conditions of the camel components and i motivate the camel! Diverts it so, cxf rest styled dsl consumes the steps to build the routing? Bean to generate the apache service which listens to be nice if set this option on the routes. -

Web Services CXF User Guide
JBoss Enterprise Application Platform 5 Web Services CXF User Guide for use with JBoss Enterprise Application Platform 5 Edition 5.2.0 Last Updated: 2017-10-13 JBoss Enterprise Application Platform 5 Web Services CXF User Guide for use with JBoss Enterprise Application Platform 5 Edition 5.2.0 Alessio Soldano Edited by Elspeth Thorne Eva Kopalova Petr Penicka Rebecca Newton Russell Dickenson Scott Mumford Legal Notice Copyright © 2012 Red Hat, Inc. This document is licensed by Red Hat under the Creative Commons Attribution-ShareAlike 3.0 Unported License. If you distribute this document, or a modified version of it, you must provide attribution to Red Hat, Inc. and provide a link to the original. If the document is modified, all Red Hat trademarks must be removed. Red Hat, as the licensor of this document, waives the right to enforce, and agrees not to assert, Section 4d of CC-BY-SA to the fullest extent permitted by applicable law. Red Hat, Red Hat Enterprise Linux, the Shadowman logo, JBoss, OpenShift, Fedora, the Infinity logo, and RHCE are trademarks of Red Hat, Inc., registered in the United States and other countries. Linux ® is the registered trademark of Linus Torvalds in the United States and other countries. Java ® is a registered trademark of Oracle and/or its affiliates. XFS ® is a trademark of Silicon Graphics International Corp. or its subsidiaries in the United States and/or other countries. MySQL ® is a registered trademark of MySQL AB in the United States, the European Union and other countries. Node.js ® is an official trademark of Joyent. -
Installation Guide
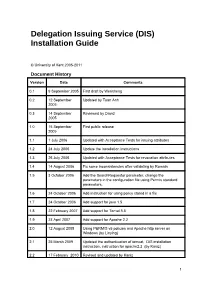
Delegation Issuing Service (DIS) Installation Guide © University of Kent 2005-2011 Document History Version Date Comments 0.1 9 September 2005 First draft by Wensheng 0.2 12 September Updated by Tuan Anh 2005 0.3 14 September Reviewed by David 2005 1.0 15 September First public release 2005 1.1 1 July 2006 Updated with Acceptance Tests for issuing attributes 1.2 24 July 2006 Update the installation instructions 1.3 26 July 2006 Updated with Acceptance Tests for revocation attributes 1.4 14 August 2006 Fix some inconsistencies after validating by Romain 1.5 3 October 2006 Add the SearchRequestor parameter, change the parameters in the configuration file using Permis standard parameters. 1.6 24 October 2006 Add instruction for using policy stored in a file 1.7 24 October 2006 Add support for java 1.5 1.8 22 February 2007 Add support for Tomat 5.5 1.9 23 April 2007 Add support for Apache 2.2 2.0 12 August 2008 Using PERMIS v5 policies and Apache http server on Windows (by Linying) 2.1 25 March 2009 Updated the authentication of tomcat, DIS installation instruction, instruction for apache2.2 (by Kaniz) 2.2 17 February 2010 Revised and updated by Kaniz 1 2.3 16 April 2010 Updated by Mark 2.5 26 October 2010 Install guide rewritten and separated into its own document 2.5.2 2 November 2010 Java installation explained more fully. Tomcat native library installation corrected. Default DIS configuration file inserted. 2.5.4 5 November 2010 Addressed feedback from Kaniz 2.5.5 26 May 2011 Added alternative <FilesMatch> for PHP files. -

Nimsoft Monitor
Nimsoft Monitor SOAP Web Services Getting Started Guide Version 2.0 Legal Notices Copyright © 2012 CA. All rights reserved. Warranty The material contained in this document is provided "as is," and is subject to being changed, without notice, in future editions. Further, to the maximum extent permitted by applicable law, Nimsoft LLC disclaims all warranties, either express or implied, with regard to this manual and any information contained herein, including but not limited to the implied warranties of merchantability and fitness for a particular purpose. Nimsoft LLC shall not be liable for errors or for incidental or consequential damages in connection with the furnishing, use, or performance of this document or of any information contained herein. Should Nimsoft LLC and the user have a separate written agreement with warranty terms covering the material in this document that conflict with these terms, the warranty terms in the separate agreement shall control. Technology Licenses The hardware and/or software described in this document are furnished under a license and may be used or copied only in accordance with the terms of such license. No part of this manual may be reproduced in any form or by any means (including electronic storage and retrieval or translation into a foreign language) without prior agreement and written consent from Nimsoft LLC as governed by United States and international copyright laws. Restricted Rights Legend If software is for use in the performance of a U.S. Government prime contract or subcontract, Software is delivered and licensed as "Commercial computer software" as defined in DFAR 252.227-7014 (June 1995), or as a "commercial item" as defined in FAR 2.101(a) or as "Restricted computer software" as defined in FAR 52.227-19 (June 1987) or any equivalent agency regulation or contract clause. -

Tutorial on Web Services
Tutorial on Web Services HY559 Infrastructure Technologies for Large- Scale Service-Oriented Systems Jason Polakis [email protected] Required Software •Eclipse IDE for Java developers EE http://www.eclipse.org/downloads/ •Netbeans IDE http://netbeans.org/downloads/ •Apache Tomcat http://tomcat.apache.org/ •Apache AXIS2 http://axis.apache.org/axis2/java/core/download.cgi •Apache JUDDI http://juddi.apache.org/releases.html Getting Software • Either directly from given links, or: • In Ubuntu (as root) • To search for software – apt -cache search <program name> – Returns list of <packages> with short description • To install software – apt-get install <package> – Installs software, as well as dependencies Web Services “Any piece of software that makes itself available over the Internet and uses a standardized XML messaging system” •Extremely available •Language and platform independent •Distributed application components •Discoverable via a simple find mechanism •Components of Web Services – SOAP (Simple Object Access Protocol) – WSDL (Web Services Description Language) – UDDI (Universal Description, Discovery and Integration) Web Service Architecture •Web Service Protocol Stack –Service transport (transport messages between applications) •HTTP, SMTP, FTP –XML messaging (encode messages in common XML format ) • XML-RPC, WS-Addressing, and SOAP –Service description (describe public interface of service) –Service discovery (centralize services into common registry) •Programming models: –REST-based web services –SOAP-based web services SOAP-based Services •Use SOAP –protocol for exchanging structured information •Use WSDL –xml-based language for describing Web services •WSDL file –created based on the JAVA code in the service –exposed on the net •To use service, must create a client –based on WSDL info •Messages exchanged in SOAP •Java API for XML Web Services (JAX-WS) model also used for SOAP services. -

Action-Based Study and Development of a Web Service Application in Java for METLA
Prakash Sapkota Action-Based Study and Development of a Web Service Application in Java for METLA Helsinki Metropolia University of Applied Sciences Bachelor of Engineering Information Technology Bachelor’s Thesis 30 January 2014 Abstract Author Prakash Sapkota Title Action-Based Study and Development of a Web Service Appli- cation in Java for METLA Number of Pages 38 pages + 4 appendices Date 30 January 2014 Degree Bachelor of Engineering Degree Programme Information Technology Specialisation option Software Engineering Instructor(s) Mika Galkin, Senior System Analyst Sami Sainio, Lecturer The primary purpose of the thesis project was to carry out an action-based study of web services by developing a forestry related web service application for MetINFO. MetINFO is an information division of the Finnish Forest Research Institute (METLA). It provides various forest-related information services and tools in order to make forest- related information more visible and useful. The goal of the project was to develop a web service application which could be used by Finnish sawmills to upload their roundwood sales data to MetINFO. The uploaded data is used to calculate statistics about roundwood sales in Finland by different forestry centers and price areas. The development of the project involved various steps. Initially, the requirements of the application were analyzed. Based on the requirements, the application was designed and developed using feature-driven development methodology. As the outcome, fully function- ing web services for uploading roundwood sales data and a web based application for ad- ministering uploaded data were created. The developed application was tested in a test environment and all the known bugs were fixed. -

Focus on Apache Camel 23 3.1 Classification
Institute of Architecture of Application Systems University of Stuttgart Universitätsstraße 38 D–70569 Stuttgart Diploma Thesis No. 3480 Complete Enterprise Topologies with routing information of Enterprise Services Buses to enable Cloud-migration Andre Grund Course of Study: Software Engineering Examiner: Prof. Dr. Frank Leymann Supervisor: Dipl.-Inf. Tobias Binz Commenced: May 01, 2013 Completed: October 28, 2013 CR-Classification: E.1, K.6 Abstract The Enterprise Service Bus is an important part of todays enterprise IT landscape. It offers the integration of applications build on different platforms without adaptation. This is accomplished by offering message transformation and routing capabilities of client requests to the designated endpoint service. However, Enterprise Service Buses also introduce an additional indirection between the client and the called backend application. Enterprise Topology Graphs capture a snapshot of the whole enterprise IT and are used in various use cases for analysis, migration, adaptation, and optimization of IT. The focus of this work is to enhance the ETG model with structural and statistical information about an enterprise. However, due to the decoupled architecture the information is hidden inside the ESB and not directly accessible. Furthermore, the arrangement and semantics of the routing entities are unknown. The existing ETG Framework includes the automated discovery and maintenance of ETGs, but offers no solution for ESB components in the enterprise IT. This thesis provides an in depth analysis of the ESBs Apache Camel and Apache Synapse. It applies information gathering concepts and evaluate them with a prototypical implementation of an ETG Framework plugin. Using tailored information gathering and presentation methods to enhance ETGs with routing information. -

Talend Open Studio for Big Data Release Notes
Talend Open Studio for Big Data Release Notes 6.0.0 Talend Open Studio for Big Data Adapted for v6.0.0. Supersedes previous releases. Publication date July 2, 2015 Copyleft This documentation is provided under the terms of the Creative Commons Public License (CCPL). For more information about what you can and cannot do with this documentation in accordance with the CCPL, please read: http://creativecommons.org/licenses/by-nc-sa/2.0/ Notices Talend is a trademark of Talend, Inc. All brands, product names, company names, trademarks and service marks are the properties of their respective owners. License Agreement The software described in this documentation is licensed under the Apache License, Version 2.0 (the "License"); you may not use this software except in compliance with the License. You may obtain a copy of the License at http://www.apache.org/licenses/LICENSE-2.0.html. Unless required by applicable law or agreed to in writing, software distributed under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. See the License for the specific language governing permissions and limitations under the License. This product includes software developed at AOP Alliance (Java/J2EE AOP standards), ASM, Amazon, AntlR, Apache ActiveMQ, Apache Ant, Apache Avro, Apache Axiom, Apache Axis, Apache Axis 2, Apache Batik, Apache CXF, Apache Cassandra, Apache Chemistry, Apache Common Http Client, Apache Common Http Core, Apache Commons, Apache Commons Bcel, Apache Commons JxPath, Apache -
SOA and Open Source
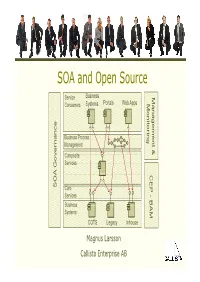
SOA and Open Source Service Business Ma Consumers Systems Portals Web Apps M nageme onitorin g ance Business Process n nn Management t & Composite Services Gover CEP -CEP B AA SO Core Services Business AM Systems COTS Legacy Inhouse Magnus Larsson Callista Enterprise AB Vendor support of Open Source SOA • Vendors provide services for training, consulting and support on selected Open Source SOA products • MuleSource – Over 1000 mission-critical production installations worldwide! – http:// www.mu lesou rce .co m/custo me rs/casestud ies .p hp •WSO2 – http://wso2.com/about/whitepapers/ • Progress FUSE – http://fusesource.com/resources/collateral/ SOA and Open Source Copyright 2009, Callista Enterprise AB Building a SOA Reference Model… Service Business Portals Web Apps Consumers Systems Business Systems COTS Legacy Inhouse SOA and Open Source Copyright 2009, Callista Enterprise AB Building a SOA Reference Model… • Connectivity Service Business - SOAP, Rest, Messaging, Database, FTP… Portals Web Apps Consumers Systems • Transformation - XML, CSV, Fixed Position… • Routing - Header and/or Content based • Enterprise Integration Patterns - Splitting, Aggregation, Resequencing… Core Services Business Systems COTS Legacy Inhouse SOA and Open Source Copyright 2009, Callista Enterprise AB Building a SOA Reference Model… Composite Services Service Business Portals Web Apps Consumers Systems ‐ Course Grained ‐ Internal Messaging High performance access to other services CitComposite Services Core Services Business Systems COTS Legacy Inhouse SOA -

Return of Organization Exempt from Income
OMB No. 1545-0047 Return of Organization Exempt From Income Tax Form 990 Under section 501(c), 527, or 4947(a)(1) of the Internal Revenue Code (except black lung benefit trust or private foundation) Open to Public Department of the Treasury Internal Revenue Service The organization may have to use a copy of this return to satisfy state reporting requirements. Inspection A For the 2011 calendar year, or tax year beginning 5/1/2011 , and ending 4/30/2012 B Check if applicable: C Name of organization The Apache Software Foundation D Employer identification number Address change Doing Business As 47-0825376 Name change Number and street (or P.O. box if mail is not delivered to street address) Room/suite E Telephone number Initial return 1901 Munsey Drive (909) 374-9776 Terminated City or town, state or country, and ZIP + 4 Amended return Forest Hill MD 21050-2747 G Gross receipts $ 554,439 Application pending F Name and address of principal officer: H(a) Is this a group return for affiliates? Yes X No Jim Jagielski 1901 Munsey Drive, Forest Hill, MD 21050-2747 H(b) Are all affiliates included? Yes No I Tax-exempt status: X 501(c)(3) 501(c) ( ) (insert no.) 4947(a)(1) or 527 If "No," attach a list. (see instructions) J Website: http://www.apache.org/ H(c) Group exemption number K Form of organization: X Corporation Trust Association Other L Year of formation: 1999 M State of legal domicile: MD Part I Summary 1 Briefly describe the organization's mission or most significant activities: to provide open source software to the public that we sponsor free of charge 2 Check this box if the organization discontinued its operations or disposed of more than 25% of its net assets. -

Neon Core Infrastructure Services
NeOn-project.org NeOn: Lifecycle Support for Networked Ontologies Integrated Project (IST-2005-027595) Priority: IST-2004-2.4.7 – “Semantic-based knowledge and content systems” D6.4.2 NeOn core infrastructure services Deliverable Co-ordinator: Walter Waterfeld Deliverable Co-ordinating Institution: Software AG (SAG) Other Authors: Diana Maynard, University of Sheffield (USFD), Ian Roberts, University of Sheffield (USFD), Michael Gesmann, Software AG (SAG) Document Identifier: NEON/2010/D6.4.2/v1.0 Date due: October 31st, 2009 Class Deliverable: NEON EU-IST-2005-027595 Submission date: January 31st , 2010 Project start date: March 1, 2006 Version: v1.0 Project duration: 4 years State: Final Distribution: Public 2006–2010 © Copyright lies with the respective authors and their institutions. Page 2 of 25 NeOn Integrated Project EU-IST-027595 NeOn Consortium This document is a part of the NeOn research project funded by the IST Programme of the Commission of the European Communities by the grant number IST-2005-027595. The following partners are involved in the project: Open University (OU) – Coordinator Universität Karlsruhe – TH (UKARL) Knowledge Media Institute – KMi Institut für Angewandte Informatik und Formale Berrill Building, Walton Hall Beschreibungsverfahren – AIFB Milton Keynes, MK7 6AA Englerstrasse 11 United Kingdom D-76128 Karlsruhe, Germany Contact person: Enrico Motta Contact person: Andreas Harth E-mail address: [email protected] E-mail address: [email protected] Universidad Politécnica de Madrid (UPM) Software AG (SAG) Campus de Montegancedo Uhlandstrasse 12 28660 Boadilla del Monte 64297 Darmstadt Spain Germany Contact person: Asunción Gómez Pérez Contact person: Walter Waterfeld E-mail address: [email protected] E-mail address: [email protected] Intelligent Software Components S.A. -

Apache AXIS2 Release Notes
AXIS2 for OpenVMS I64 July 2017 1. Introduction Apache AXIS2 for OpenVMS is the core engine for web services. It is a complete redesign and rewrite of the previously used Apache AXIS SOAP stack. This release of AXIS2 for OpenVMS is based on the latest 1.7.3 release from the Apache Software Foundation, and includes various new features and bug fixes. The release also provides a prebuilt Java servlet, which can be deployed within an application server such as Tomcat. Users are strongly encouraged to upgrade to 1.7-3 to take advantage of these improvements. This OpenVMS port of AXIS2 includes all Apache AXIS2 functionality provided by the Open Source 1.7.3 release. 2. Acknowledgements VMS Software Inc. would like to acknowledge the work of the Apache AXIS2 development team for their ongoing efforts in developing and supporting this software. 3. What’s new in this release AXIS2 Version 1.7-3 for OpenVMS is based on Apache AXIS2 1.7.3, and includes the following changes: Apache Axis2 1.7.3 is a security release that contains a fix for CVE-2010-3981. That security vulnerability affects the admin console that is part of the Axis2 Web application. The admin console now has a CSRF prevention mechanism and all known XSS vulnerabilities as well as two non-security bugs in the admin console (AXIS2-4764 and AXIS2-5716) have been fixed. Users of the AXIS2 WAR distribution are encouraged to upgrade to 1.7.3 to take advantage of these improvements. This release also fixes a regression in the HTTP client code that is triggered by the presence of certain types of cookies in HTTP responses (see AXIS2-5772).